Automated Controls Testing Starter Kit
Access Controls
DESCRIPTION
Ensure that employees and contractors get access to company systems in a controlled manner (e.g., -password policies are enforced). Password policies are used to enforce a set of best practices around password security for every user.
TESTING SCENARIO
Ensure that the password policy in key systems conforms to the larger company policy. The test would check to see whether there is a minimum password length. It could also check whether required special characters are enabled or not.
EXAMPLE TEST CASES:
If [minimum character length] is less than {8}, then the test fails.
If [required symbols] is {false} and [required special characters] is {false}, then the test fails.
If [password expiration] is more than {90 days}, then the test fails.
FOLLOW UP TASK
Create a task to alert the key system’s administrator to use the system’s password policy to conform to the larger company password policy.
EVIDENCE FILE
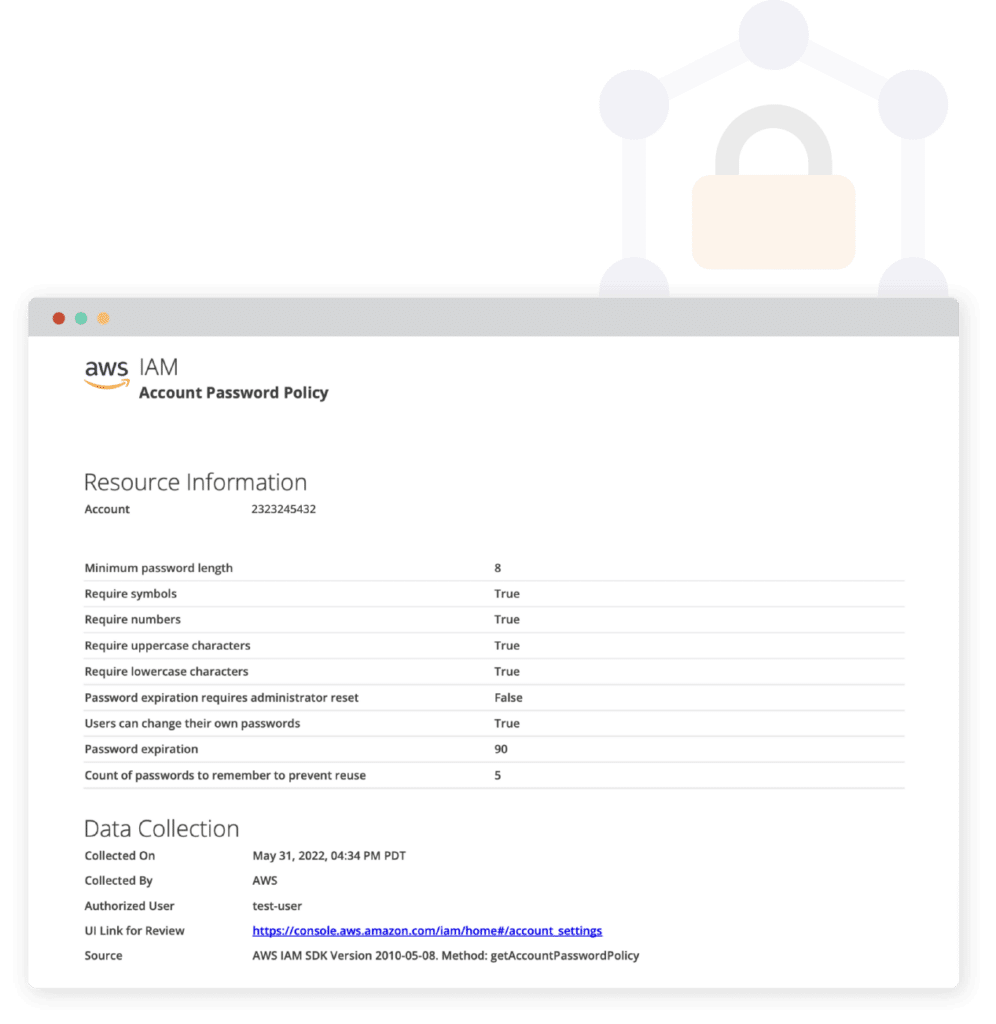
AWS Password policy
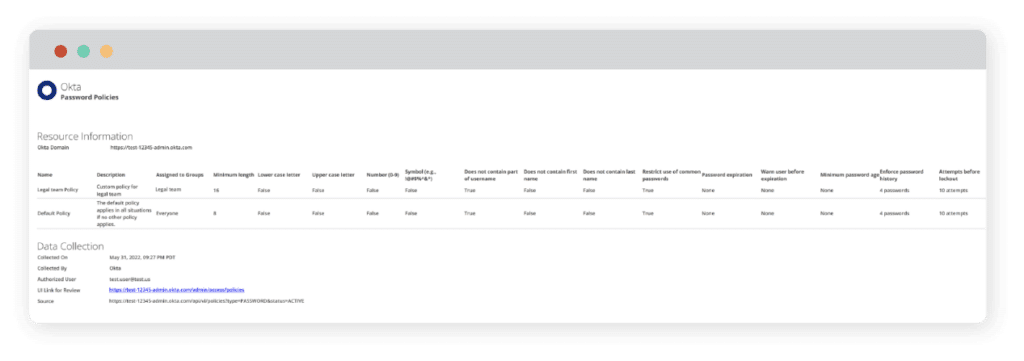
Okta Password Policies
Key Monitoring Tools Availability
DESCRIPTION
Monitoring isn’t just important for ensuring effective operations, reducing risks of outages and data breaches, and preventing malware threats. Being able to show that your systems were properly monitored over time is a must-have for passing IT audits. IT auditors want to see a paper trail showing that all monitors ran as they should and that incidents and events were identified and fixed according to established company policies and procedures.
By writing a test, you can check to see that your monitoring tools have been configured correctly and are running according to company policies and external guidelines and requirements.
TESTING SCENARIO
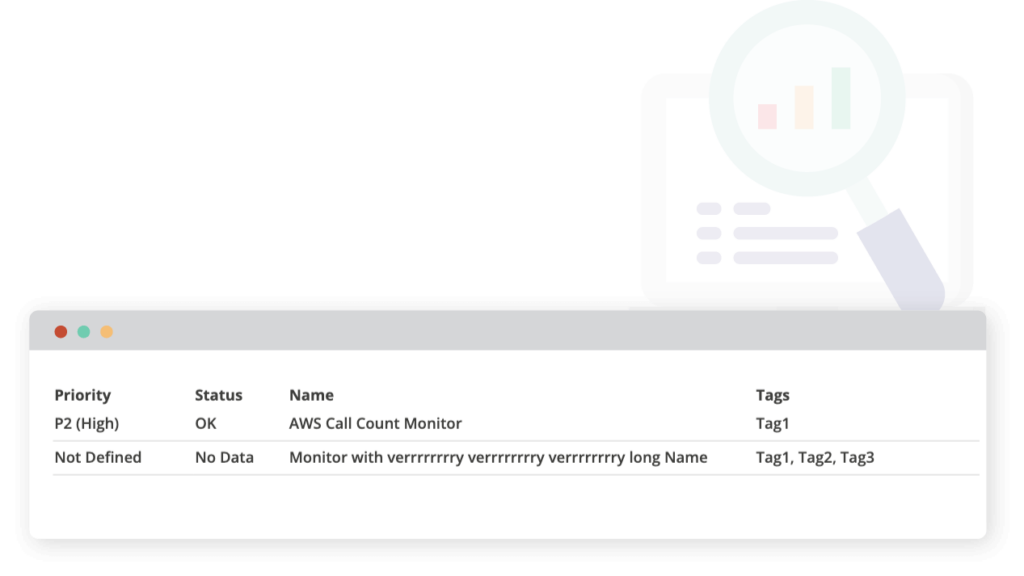
Let’s make sure that someone in Engineering is alerted anytime a new monitor in our monitoring system – DataDog- is created without a defined priority or status.
EVIDENCE FILE
Sample data from DataDog
TEST SCRIPT
If [priority] is not {defined}, then the test needs review.
FOLLOW UP TASK
Create a task for the infrastructure engineering team to review the monitor and add a priority to it.
Change Management
DESCRIPTION
In your software development process, validate that a designated approval process was followed (meaning the code has been reviewed by the right person) before it’s deployed into the production environment.
TESTING SCENARIO
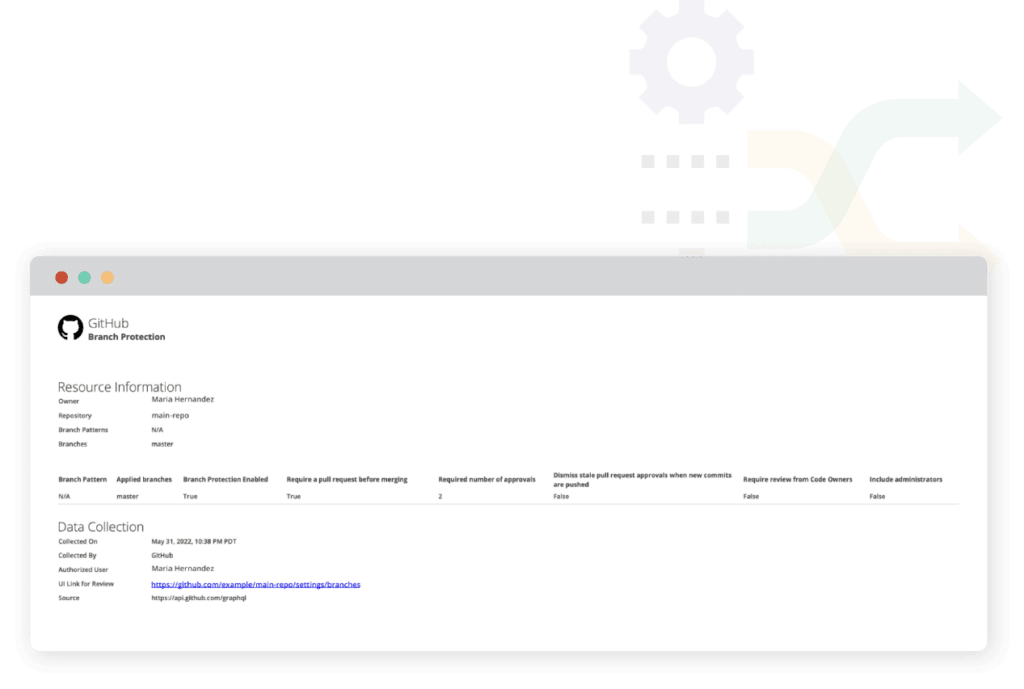
To achieve this validation, analyze branch protection settings that enforce reviews. Run a test to verify whether all Github branches have appropriate protection. Many organizations have hundreds of branches and deploy sets of rules for them based on the naming convention of the branches.
Hyperproof provides users with the flexibility to pull information based on their set up. You can either pull in all branch protection rules and check which branches they are applied to or monitor important branches like “Master” individually.
EVIDENCE FILE
GitHub Branch Protection Master
GitHub Branch Protection
EXAMPLE TEST CASES:
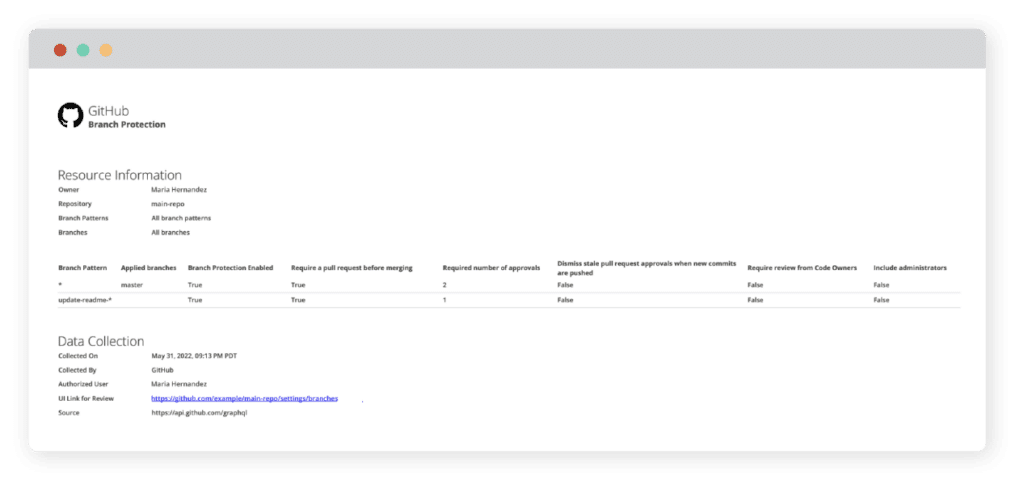
Scenario 1: When all branches are pulled in for testing
If [required number of approvals] is below {2}, then fail.
If [requires a pull request before merging] is {false}, then fail.
If [branch rule] is {none} and [branches] is not {empty}, then fail.
Scenario 2: When a single branch is pulled in
If [branch protection enabled] is {false}, then fail.
FOLLOW UP TASK
Create a task for the appropriate person in Engineering to enable branch protection in GitHub.
Vulnerability Management
DESCRIPTION
Validate that [critical] vulnerabilities are fixed in a timely manner according to the service level agreement (SLA) within our company.
TESTING SCENARIO
Ensure that when vulnerabilities are discovered, they are addressed in a timely manner. Allow users to set different rules or service level agreements (SLAs) depending on the severity level of the vulnerability. Review past vulnerabilities and remediation plans to detect whether designated remediation activities were conducted on time.
EVIDENCE FILE
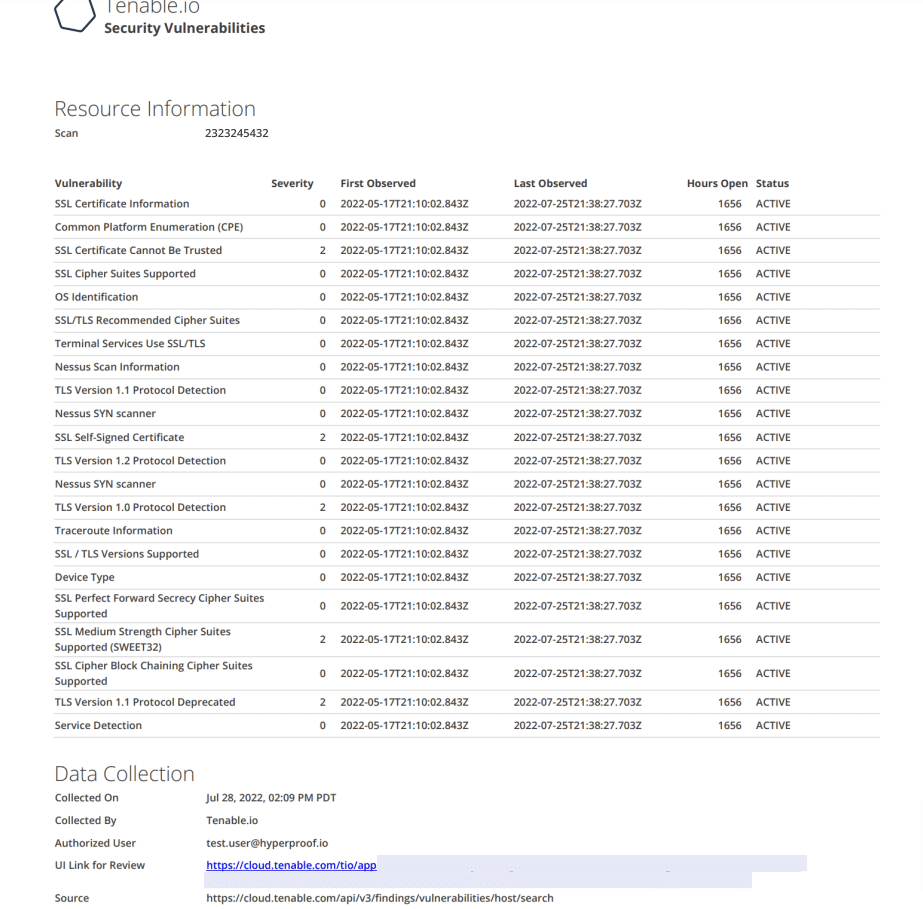
TEST SCRIPT
If [severity] is {3}
And [hours open] is greater than {24}
Then fail.
FOLLOW UP TASK
Created a triggered task for a responsible developer to follow up and fix. In this case, fixing a vulnerability will typically mean making actual code changes.
Business Continuity/Data Integrity
DESCRIPTION
It is a security best practice for an organization to deploy automated data backups. Cloud infrastructure platforms like AWS and Microsoft Azure can be configured to backup data automatically on a regular cadence. Although it’s common for there to be 2 or 3 failures for every 100 back up jobs, it is beneficial to know when the number of failures exceeds your organization’s tolerance threshold, since this can be a sign of a more serious issue.
TESTING SCENARIO
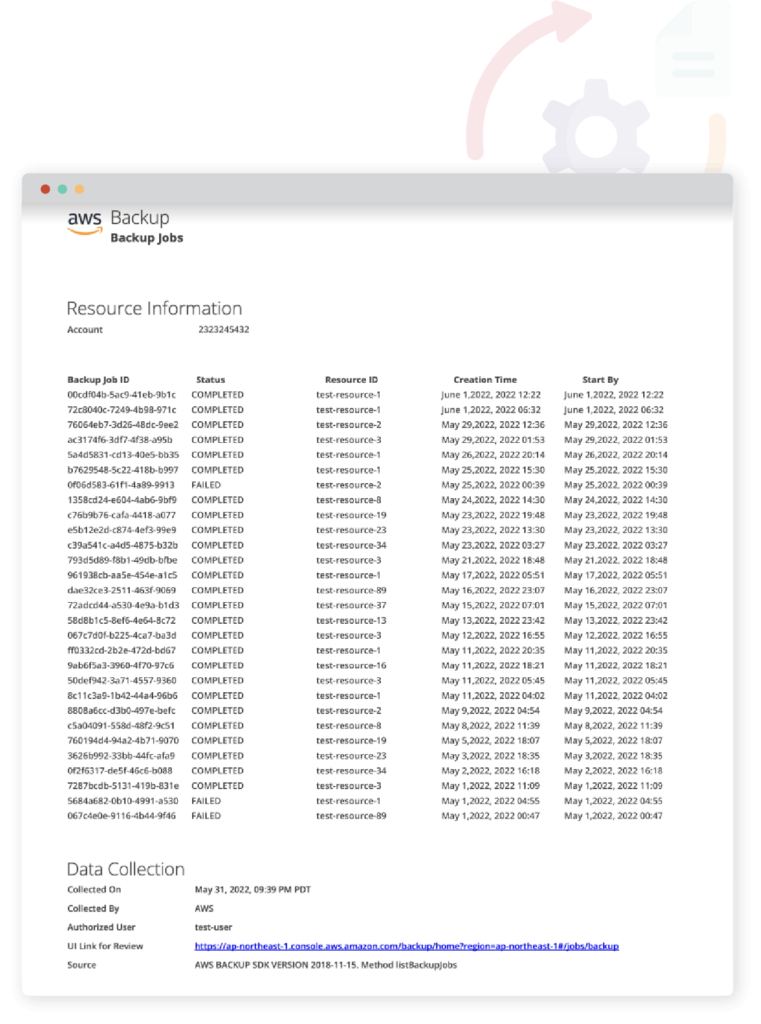
Test that there aren’t any data backup failures (or that the number of data backup failures per 100 backups is below a certain threshold). Nearly all Infrastructure as a Service platforms contain detailed reports on backup jobs that can be scanned automatically.
EXAMPLE TEST CASES:
If [status] is {failed}, then the test fails.
FOLLOW UP TASK
Create a task for an engineer to log into the AWS account where the failure happened and investigate further.
EVIDENCE FILE
AWS Backups
Data Encryption/Security
DESCRIPTION
Verify that all of the firm’s confidential data is stored in an encrypted format. Ensure that access to encryption keys is restricted to authorized personnel. Ensure that data is transferred in a secure manner. These practices protect your stored data against theft, ransomware attacks, and other security risks. With proper encryption practices in place, even if an attacker gets access or to your data, they won’t be able to do anything with it unless they also have the key to unencrypt it.
TESTING SCENARIO 1
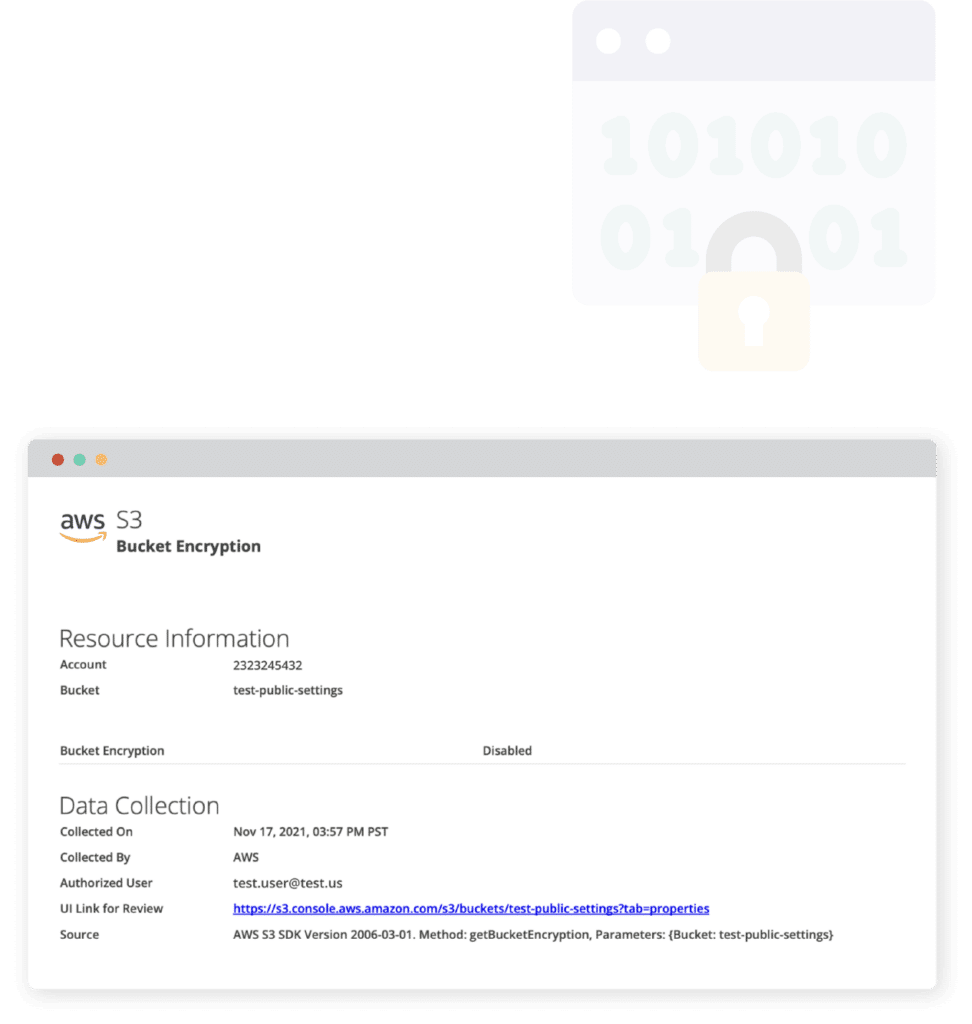
Check that all objects in a particular Amazon Web Services S3 bucket have been encrypted. If the bucket contains objects that are unencrypted, then the test would fail.
TEST SCRIPT
If [bucket encryption] is {disabled}, then the test fails.
FOLLOW UP TASK
Create a task to notify the appropriate person in Engineering to review the encryption setting on this bucket.
EVIDENCE FILE
TESTING SCENARIO 2
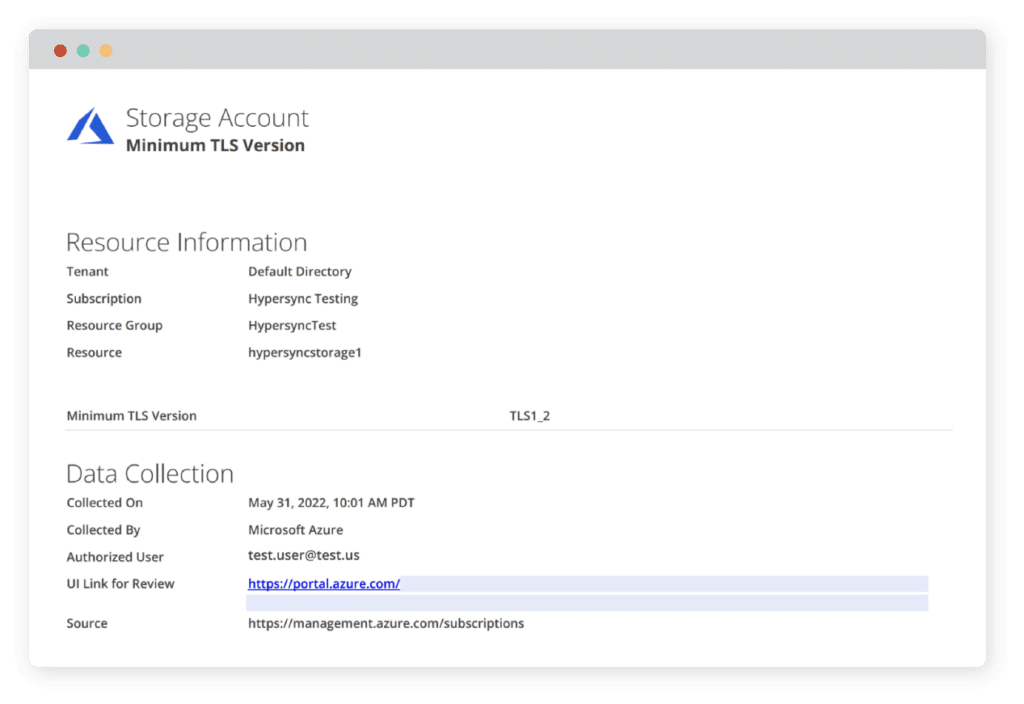
Check that data transfers are happening in a secure manner. Check whether your Azure storage account is using the appropriate minimum TLS version.
TEST SCRIPT
If [minimum TLS version] does not contain {TLS1_2}, then the test fails.
FOLLOW UP TASK
Create a ticket for the database administrator to set the minimum TLS version to TLS1_2.
EVIDENCE FILE