Cybersecurity is a high-stakes race for many organizations today, and whoever discovers the vulnerability first wins. That’s right, cyber defense teams are racing the clock to identify and patch system flaws before they can be exploited by opportunistic threat actors. Even nation states aren’t exempt as Ukraine was hit with two significant cyber attacks–the Viaset satellite misconfiguration exploit and the Whispergate malware attack–prior to the Russian invasion on February 24th, 2022.
Today, system vulnerabilities are inevitable as organizations digitize operations with advancing technology and cloud adoption. Even the best defenses expose cracks, and modern security teams have their hands full, attempting to identify and mitigate potential areas of weakness. Vulnerability management is undoubtedly challenging, yet it’s become a critical component of security and compliance for modern organizations.
Charles Denyer, Austin-based cybersecurity and national security expert, explains,
Vulnerability management has a challenge in itself because there’s not always a general consensus as to what it is. If you ask ten different IT people what vulnerability management is, you’re likely to get ten different definitions. However, if your organization truly does all the necessary things–identifying, classifying, prioritizing, remediating, and continuously monitoring vulnerabilities–those are all the critical factors for cybersecurity.
In this article, you will learn about vulnerability management, its importance for corporate security and compliance, the components and steps of an effective vulnerability management process, and the current tools available to help your team effectively manage vulnerabilities across your network.
What is vulnerability management?
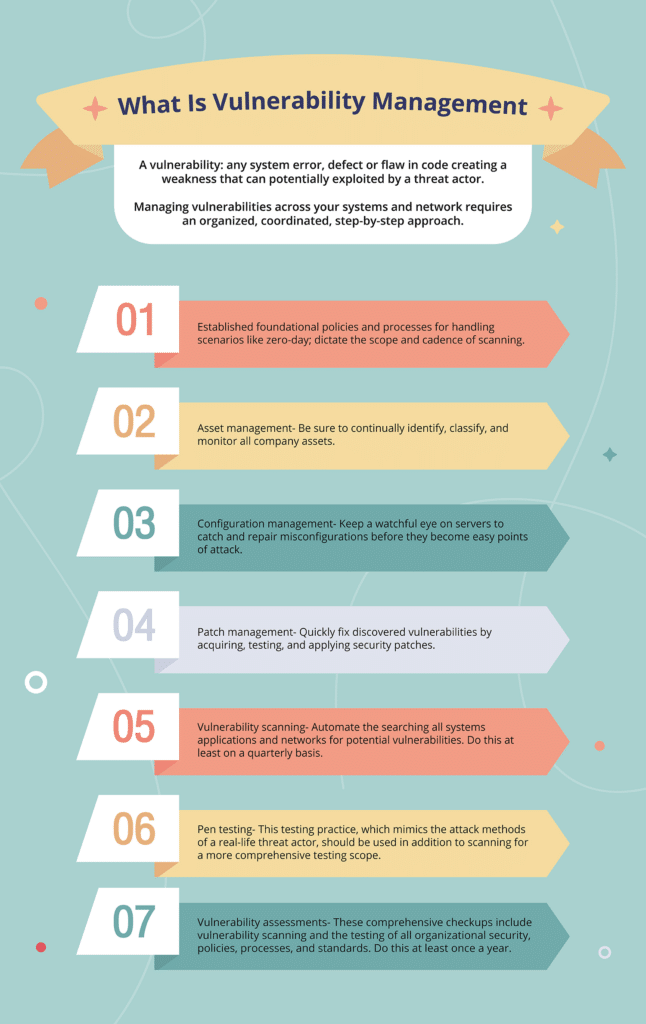
Let’s start by defining a vulnerability: any system error, defect, or flaw in code creating a weakness that can potentially be exploited by a threat actor. These software or system weaknesses are potentially dangerous as they can become pathways for attackers to enter and compromise a network.
Managing vulnerabilities involves multiple steps which includes identifying, evaluating, correcting (or accepting), monitoring, and reporting on discovered system vulnerabilities. Vulnerability management is most successful when used in conjunction with other security tactics to find and prioritize threats, shrink potential attack surfaces, and minimize the risk of harm to systems and networks.
Managing your network’s vulnerabilities doesn’t just boost security–it also helps ensure the safeguarding of sensitive customer data and privacy rights, which is the focus of many infosec compliance standards and regulations. Identifying potential vulnerabilities is a critical first step in securing systems, protecting your customer’s private information, and maintaining regulatory compliance with infosec compliance standards such as SOC 2, ISO 27001, and PCI DSS, which list vulnerability management as a key domain.
For example, both PCI DSS and HIPAA require paperwork documenting the creation and implementation of a vulnerability management program. Regularly scanning your network and web applications for vulnerabilities is recommended to satisfy the following SOC 2 requirements listed in AICPA criteria guidelines:
- CC7.1 – To meet its objectives, the entity uses detection and monitoring procedures to identify (1) changes to configurations that result in introducing new vulnerabilities and (2) susceptibilities to newly discovered vulnerabilities.
- CC4.1 – COSO Principle 16: The entity selects, develops, and performs ongoing and/or separate evaluations to ascertain whether the components of internal control are present and functioning.
- CC4.2 – COSO Principle 17: The entity evaluates and communicates internal control deficiencies promptly to those parties responsible for taking corrective action, including senior management and the board of directors, as appropriate.
What are the necessary components for a successful vulnerability management program?

Managing vulnerabilities across your systems and network requires an organized, coordinated, step-by-step approach. Your team must include the following vulnerability management process components to help identify, assess, prevent, and correct vulnerabilities in your network:
Established foundational guidelines- Start your vulnerability management initiative by creating policies and processes for handling scenarios like zero-day and dictating the scope and cadence of scanning.
Asset management- Be sure to continually identify, classify, and monitor all company assets. Keep accurate and current inventories to allow the efficient scanning of all assets for maximum protection.
Configuration management- Misconfigured servers provide prime targets for attackers, so keep a watchful eye to catch and repair misconfigurations before they become easy points of attack.
Patch management- Rapidly discovering and fixing vulnerabilities by acquiring, testing, and applying security patches is critical to the success of your vulnerability management program. Patching vulnerabilities before they get exploited by threat actors should be atop every organization’s list of security priorities.
Vulnerability scanning- Scanning is the automated practice of searching all systems, applications, and networks for potential vulnerabilities. Both internal and external scans should be run at least quarterly, and the results compared to develop an accurate picture of your risk landscape. Authenticated scans, which include deeper searches for missing patches and misconfiguration issues, should be run more frequently on higher-value assets. Unauthenticated scans, which discover less serious surface issues like open ports or operating systems, can be run less frequently on external assets of lesser importance.
Penetration testing- This testing practice, which mimics the attack methods of a real-life threat actor, should be used in addition to scanning for a more comprehensive testing scope. Pen tests help reduce the number of false positive alerts and should be performed at least annually, including physical and social engineering elements.
Vulnerability assessments- These comprehensive checkups include vulnerability scanning and the testing of all organizational security, policies, processes, and standards. Ideally, these assessments should occur continuously or at least annually.
Keep metric reports- It’s critical to keep immaculate records of all vulnerability management incidents and activities, closely tracking them to see if the actual vulnerability management activities match your established policies and processes. Record-keeping should operate on a risk-based basis, with higher risk vulnerabilities closely tracked to ensure they don’t slip through the cracks.
Five steps of the vulnerability management process

1. Discovering vulnerabilities- Searching for and identifying vulnerabilities across vast systems and networks can prove challenging for even the most dedicated teams. Vulnerability scanning, the process of using automated searching tools to test all network devices, including laptops, servers, databases, and firewalls, for potential vulnerabilities, plays a large role during discovery. The entire process consists of four steps:
- Conducting tests on available networks
- Identifying open ports and running systems
- Using remote logins to collect additional system data
- Comparing and correlating results with a database of known threats to quickly identify vulnerabilities.
Running scans can disrupt system functions, so it’s critical to properly configure scans and run them during times of lower bandwidth. Adaptive scanning methods such as testing new systems immediately upon joining a network can be used to simplify the scanning process.
Vulnerability management solutions can engage other means, such as pen testing and accessing endpoint agents to gather vulnerability information without scanning systems. All system vulnerability data gathered should be compiled into metric reports and dashboards for faster analysis.
2. Assessing vulnerabilities- Once a system vulnerability is discovered, it’s time to see what you’re dealing with in terms of severity and risk. When you understand the potential risk associated with each vulnerability, you can grade and address threats following your organization’s Risk Management Strategy. Tools like the Common Vulnerability Scoring System (CVSS) can provide a rating system for vulnerabilities.
What should be considered when rating a vulnerability?
Start by determining the history of the specific vulnerability–how long it’s been around and if there are known exploits connected to it. How difficult is this vulnerability to exploit, and what would be the impact on the business should exploitation occur? Finally, does your team have any security controls to lessen the chances of exploitation?
3. Resolving vulnerabilities- Once identified and rated, it’s time to decide on a resolution for the vulnerability. Remediation, or fixing the flaw, is always preferable, as this removes the threat entirely. Remediations run the gamut of complexity–being as simple as a patch or as involved as replacing an entire fleet of servers. If remediation isn’t an option, then mitigation, which lessens the chance of occurrence or the impact of the exploit, is a popular second choice that can buy time until a permanent fix becomes available. Acceptance could also be an option if the vulnerability is low-risk and the cost to remediate or mitigate is more than the potential damage of the exploit. Whichever resolution you select, be sure to run future tests monitoring the effectiveness of your chosen solution.
4. Reporting vulnerabilities- Don’t forget to keep immaculate records of your organization’s vulnerability history, chosen resolutions, and outcomes. Report all impactful vulnerabilities to your customers so they know whether the vulnerability has impacted your system (and them by extension), what you’ve done to respond to the vulnerability and whether remediation steps have been taken. A recent example of such a vulnerability is Log4j which made news in December of 2021. This vulnerability affected the popular Java logging package by allowing unauthenticated application execution and is considered one of the most dangerous vulnerabilities in the last decade.
Remember to use customizable reports and convenient dashboards to keep track of metrics, as this organized approach will support learning and simplify compliance verification.
5. Audit your policies and practices- Every new client, partner, employee, technology, or workflow brings the possibility of new vulnerabilities for your business. Change is inevitable, and your vulnerability management program must be able to keep pace. Maintaining a successful vulnerability management program requires the performance of regular assessments testing the strength of your vulnerability management policies and practices through changes and over time–especially regarding patch management.
Are all your system patches timely and adequate for vulnerability resolution? How do you know if the patches your team applied last month were configured correctly and continue to maintain effectiveness in your current threat landscape? You really don’t–unless you continually conduct comprehensive assessments to empirically prove that system vulnerabilities have been remediated and no longer present a threat.
Many organizations conduct patch management audits to prove the effective functioning of their patch management program for peace of mind and regulatory compliance verification.
9 Tips to Keep in Mind for Effective Patch Management
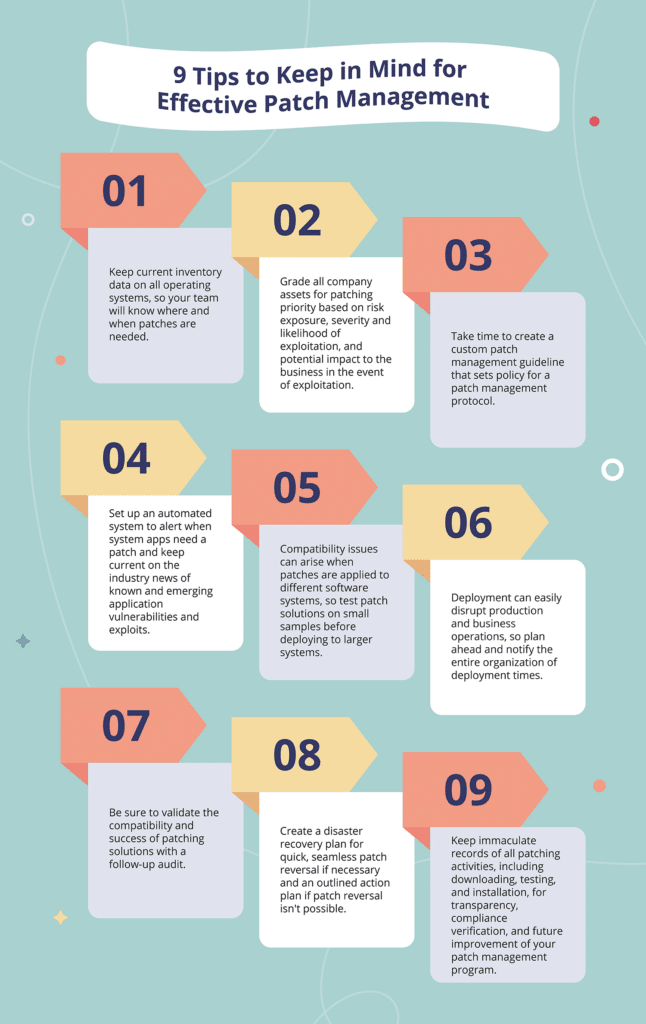
1. Keep current inventory data on all operating systems so your team will know where and when patches are needed.
2. Grade all company assets for patching priority based on risk exposure, severity and likelihood of exploitation, and potential impact to the business in the event of exploitation.
3. Take time to create a custom patch management guideline that sets policy for a patch management protocol. This policy guideline should provide a clearly outlined action template while allowing for adaptive flexibility in situations such as when a patch is needed but not yet available.
4. Set up an automated system to alert you when system apps need a patch and keep current on the industry news of known and emerging application vulnerabilities and exploits.
5. Compatibility issues can arise when patches are applied to different software systems, so test patch solutions on small samples before deploying to larger systems.
6. Deployment can easily disrupt production and business operations, so plan ahead and notify the entire organization of deployment times. Engage automated patch deployment solutions whenever possible and only deploy after extensive testing verifies patch compatibility and safety.
7. Be sure to validate the compatibility and success of patching solutions with a follow-up audit. Identify any deployment issues needing future remediation.
8. Create a disaster recovery plan for quick, seamless patch reversal if necessary and an outlined action plan if patch reversal isn’t possible.
9. Keep immaculate records of all patching activities, including downloading, testing, and installation for transparency, compliance verification, and future improvement of your patch management program.
Utilizing vulnerability scanners & software
Vulnerability management tools are security applications that monitor network systems, test and scan for areas of vulnerability, prioritize potential threats, and recommend actions to remediate threats before they harm the system. These tools are designed to reduce risk while helping preserve the confidentiality, integrity, and availability of system information.
When searching for the best vulnerability management tool, it’s important to understand critical functions. Effective vulnerability management solutions should:
- Maintain a comprehensive inventory of organizational assets while viewing and monitoring all network devices.
- Provide real-time scanning across all attack vectors, business risk analysis for all assets, and prioritized fixes to speed remediation for identified vulnerabilities. Ideally, these tools will engage artificial intelligence and machine learning to keep pace with vast volumes of system data.
- Deliver reports tracking vulnerability data, providing analysis and context on vulnerability and mitigation trends, and offering future predictions to boost overall network security.
Vulnerability management scanning tools come in three options–paid, free, and open-source. They offer speedy solutions, taking a few hours to complete, and most employ convenient automated technology to avoid tying up manual resources. However, like any security tool, vulnerability scanners do have drawbacks. Their false positive rates are low but still greater than zero. This is where combining scanning tools with penetration testing is a great strategy to weed out false positives and free up your team’s resources for addressing real vulnerabilities.
So, what are the best vulnerability management software solutions on the market today? The answer will depend on your organization’s individual security needs and the ability of the chosen solution to analyze your network’s systems. Here are a few paid, open-source, and free options to consider:
Netsparker- This highly-rated paid option has many advanced features, including robust vulnerability mitigation techniques.
Acunetix- Another highly-rated paid option that offers a broad vulnerability scanning range over a more extensive device load.
Nikto2- This open-source offering works in minimal time but doesn’t offer countermeasures for discovered vulnerabilities.
W3AF- Another open-source option known to be user-friendly that covers many vulnerabilities and assists with penetration testing.
Nmap- This well-known free option is an excellent beginner’s tool for those new to vulnerability scanning.
Microsoft Baseline Security Analyzer- Another well-known free option that offers robust vulnerability resolution features and is an excellent fit for Windows users and budget-conscious small to midsize businesses.
Hyperproof helps you maintain robust security processes and compliance

Hyperproof’s compliance operations platform can give you immediate visibility into your enterprise risks and their impact. You’ll be able to implement security controls – including those related to vulnerability management and patching – and manage them continuously in Hyperproof. Hyperproof makes it much easier for you to validate/verify that your established security policies, practices, and procedures are consistently applied and enforced.
On vulnerability management specifically, evidence from vulnerability management software, including Tenable and Qualys, can be automatically pulled into Hyperproof for review. All evidence can be tied to specific controls (written documentation of your policies and procedures designed to mitigate risks), making it easier to show your auditors that you were properly using vulnerability management software all along and patches had been applied in a timely manner.
Want more info on how Hyperproof can help your team verify effective vulnerability management practices and maintain compliance? Visit our product page.
Monthly Newsletter
Get the Latest on Compliance Operations.