It sounds official — like it might be the subject of the next action-packed, government espionage, Jason Bourne-style thriller. Or maybe put it before the name of a racy city and have your next hit crime series. A history of mysterious aliases like “official use only,” “law enforcement sensitive,” and “sensitive but unclassified” only adds to the intrigue.
So, what exactly is CUI, and why should your company care? Hint alert — obtaining a government contract could depend on how your organization addresses CUI, so for many, it’s a topic worthy of discussion.
CUI, or controlled unclassified information, didn’t have much of an established identity before 2010. It went by any number of aliases and took a back seat to the more glamorous classified category. However, should CUI fall into the wrong hands, something as serious as national security could be at risk. This article will explore CUI — what it is, why it’s so important, how CUI management is changing, and the most critical action your company can take to manage CUI today properly.
Classified vs. controlled unclassified information (CUI)

Classified info gets all the attention — and the highest level of government protection with access on a “need to know” basis. Matt Monroe, a 20-year U.S. Air Force veteran and current operations manager at Omnistruct, explains the breakdown, “There are four classified information categories in the military based on the severity of damage that the information’s release would cause. The three most sensitive — confidential, secret, and top-secret — could cause damage to exceptionally grave damage should the information be released and end up in the wrong hands.”
CUI isn’t classified, but the government feels this type of information must be controlled and not disseminated as its release could threaten national security. Fewer controls govern CUI and can pose an easier path for malicious invaders as access requires only a “lawful government purpose” rather than the much stricter “need to know” requirement for classified information. Safeguarding CUI is taken seriously but not historically viewed with the same urgency as classified.
What is CUI?

CUI is government-created or owned information that requires safeguarding or dissemination controls consistent with applicable laws, regulations, and government-wide policies. It’s also not corporate intellectual property unless created for or included in requirements related to a government contract.
Up until 2010, CUI wasn’t even CUI — it appeared under an assortment of previously mentioned names, like “for official use only” and “sensitive but unclassified.” More troubling was that no standardized guidelines existed for assessing CUI—one company could label information extremely sensitive while another could treat it as less sensitive.
In November of 2010, the Obama Administration passed Executive Order 13556, which created 10 categories for non-classified information needing control and protection due to potential vulnerability and security risk. The goal was to create a uniform system for safeguarding and disseminating CUI. The Final Rule was passed in 2016 by the National Archives Records Administration to provide implementation direction for Executive Order 13556 and to support a standardized methodology for assessing CUI.
Basic CUI vs. specified CUI
Two subsets of CUI exist — basic and specified. The Final Rule identifies the handling and dissemination controls for Basic CUI as moderate under the Federal Info Systems Modernization Act (FISMA) with info marked CUI or controlled.
Specified CUI requires more restrictive handling controls and a designating agency to apply specific dissemination controls for each information category. Examples of agency subset categories for CUI include agriculture, legal, transportation, financial, tax, and immigration.
Additional examples of CUI
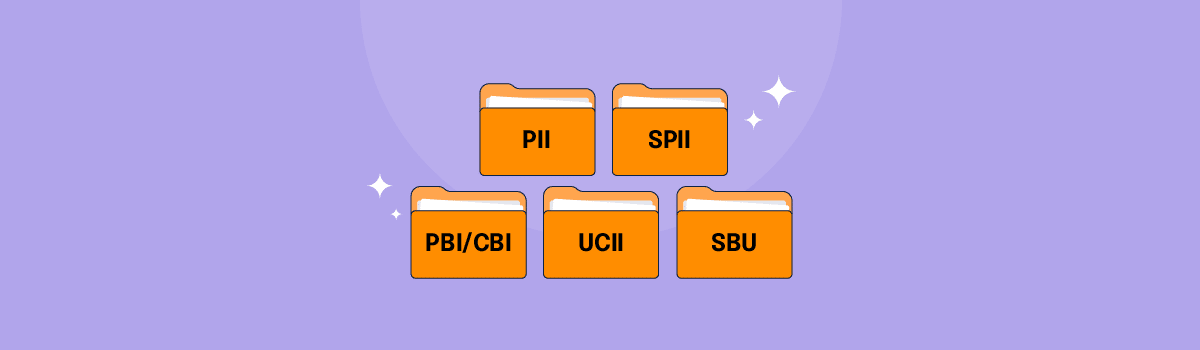
CUI can be a general term that will capture various markings to ID information that isn’t necessarily classified but still sensitive. Other examples include:
- Personally Identifiable Information (PII)
- Sensitive Personally Identifiable Information (SPII)
- Proprietary Business Information (PBI) or currently known within EPA as Confidential Business Information (CBI)
- Unclassified Controlled Technical Information (UCTI)
- Sensitive but Unclassified (SBU)
Basic requirements
For those interested in working with the government, specifically the Department of Defense (DoD), DoD Instruction 5200.48 presents a set of basic requirements for CUI in contractor relationships.
If your company wants to contract with the DoD, keep the following in mind:
- When providing info to contractors, the DoD must inform the contractor of any CUI and mark it accordingly.
- The DoD must articulate this fact in all contracts and legal documents when providing CUI.
- DoD contracts require contractors to monitor CUI and report classifications to a DoD representative.
- CUI will be classified at a “moderate” confidentiality level and follow DoDI 8500.01 and 8510.01 in all DOD systems. Non-DoD systems must provide adequate security, with requirements incorporated into all legal documents, and non-DoD entities must follow DoDI 8582.01 guidelines.
- DoD representatives and contractors will submit all unclassified DoD info for review and approval based on the Department of Defense Instruction 5230.09.
- All CUI records must follow the approved mandatory disposition authorities whenever the DoD provides CUI to or generates CUI by anyone other than the DoD.
Common mistakes with identifying CUI
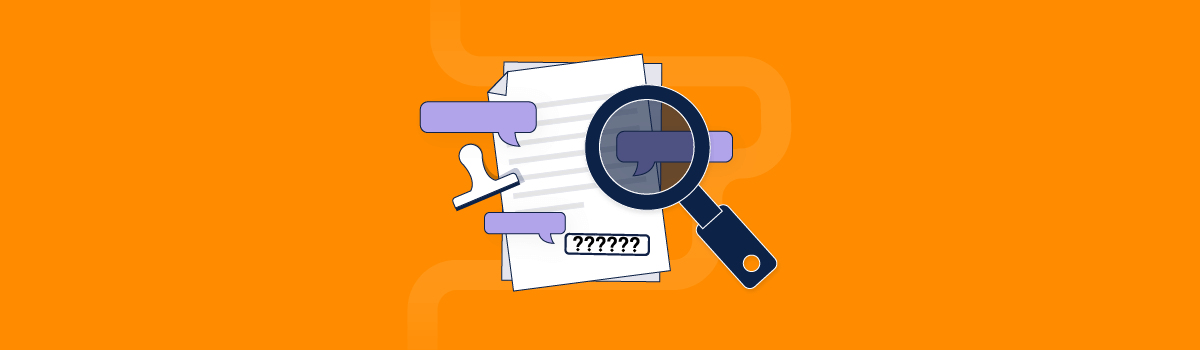
- Over-classification: Businesses might mistakenly classify all government-related information as CUI, like budgets, leading to unnecessary restrictions and inefficiencies.
- Focus on format over content: Assuming that only certain formats (e.g., reports) contain CUI, while overlooking sensitive information in emails or presentations.
- Lack of context: Not considering the context in which information is used or created. Publicly available information might become CUI when combined with other sensitive data.
How is CUI management changing?

The importance of CUI management today is evident — especially in government-related industries. In May 2018, the senior official in charge of CUI at the time (Under Secretary of Defense for Intelligence) designated the Defense Counterintelligence Security Agency (DCSA) with DoD enterprise management of CUI. The moves’ objectives were to help foster department-wide prioritization of CUI, universal CUI assessment standards, a shared CUI data library, and CUI management training.
The Cybersecurity Maturity Model Certification (CMMC) impacts how companies must manage CUI today. Gone are the days of casual “self-attestation” for CUI compliance verification. The CMMC requires all contractors to pass rigorous third-party audits proving adherence to the new CUI regulations.
Meeting these regulations requires a significant commitment from contractors, and many of the smaller players won’t have the resources needed to meet the new DoD requirements.
One thing is for sure — all organizations will be more aware of CUI, where it is, and what measures are necessary to ensure safety and compliance.
What can your organization do to help manage CUI and stay compliant with CMMC?

What can your organization do to help manage CUI and stay compliant with CMMC? According to Monroe, two words sum it up — data classification. He emphasizes the importance of knowing what CUI is in your systems and its location. Matt feels it’s never too soon to begin classifying your data with the benefits undoubtedly worth the effort.
“Better off starting the process now, creating a classification structure and adhering to it, rather than waiting until you’re forced. As much of a drag as going through and doing data classification can be, the effort is worth it when you can deliver the proof and avoid the headaches.”
Data classification undoubtedly provides the cornerstone for any successful information security management system today. Secure and compliant organizations take time to understand their data profiles and base classifications on their specific criteria and privacy requirements. They set clear, definable goals for their classification policy, guided by solid internal ownership. Finally, they understand the importance of keeping policies simple, using automation when possible to streamline the classification process, and continually monitoring their policies to keep pace with changing environments.
Securing CUI
How can your organization best secure CUI? Start by examining the Cybersecurity Maturity Model Certification (CMMC), which addresses CUI security requirements for all DoD industry partners. This model is designed as a guideline to ensure adequate security processes and practices to protect CUI within the networks of all DoD contractors. The CMMC contains maturity levels ranging from “basic cybersecurity hygiene” to “advanced progressive,” providing users with a hierarchy of security options for CUI. Below are the five levels of the CMMC, which offer an excellent beginning guideline for protecting your CUI.
- Level 1 suggests performing basic cyber hygiene practices, such as installing anti-virus software and regularly changing passwords, to safeguard Federal Contract Information (FCI).
- Level 2 describes an “intermediate level of cyber hygiene” that begins implementing NIST SP 800-171 requirements to secure CUI.
- Level 3 raises the bar to “good cyber hygiene,” which includes implementing all NIST SP 800-171 security requirements with additional standards under a company-wide management plan.
- Level 4 establishes processes and techniques for addressing “advanced persistent threats” (APT) that bring more sophisticated expertise and resources.
- Level 5 standardizes and optimizes the processes and techniques for handling APTs and establishes a process for reviewing and measuring the effectiveness of security practices.
Remember that the first three levels of the CMMC encompass the 110 security requirements specified in NIST SP 800-171. The CMMC then goes further with each level, adding processes and practices to those specified in lower levels. It also mirrors the NIST SP 800-171 in that it assesses a company’s implementation of cybersecurity practices and institutionalization of cybersecurity processes.
Elevating CUI management: secure your federal contracts with confidence

Despite a history of playing second fiddle to the more glamorous classified ranking, CUI cannot be overlooked today, especially by compliance-conscious companies looking to secure federal government contracts.
Legislation has finally caught up with CUI, providing standardized guidelines for assessment and uniform, transparent systems like those outlined in the CUI Program to safeguard and disseminate this information. In addition, CMMC regulations have finally tightened the reins, providing the regulatory controls to ensure this unclassified yet potentially sensitive data is handled safely today.
Request a demo of Hyperproof today and unlock the potential to manage CUI effectively, securing your federal contracts with confidence and ease.
Monthly Newsletter
Get the Latest on Compliance Operations.