How to Avoid Control Deficiencies That Can Impact Your Audit Results
Maintaining effective internal controls that operate consistently is an important component of any good compliance program. When internal controls and other security safeguards fail, they can expose an organization to risk. Not only can control failures negatively impact your audit results, they can lead to costly data breaches, business disruptions, reputational damage and revenue loss. Fortunately, many control failures are entirely avoidable.
In this article, we’ll discuss at a high level what controls are designed to do. Then, we’ll dive into the common reasons controls become deficient, how they can impact your audit results, and the actions you can take to prevent these control deficiencies in your compliance program.
What are internal controls designed to do?
Before we dive into the common reasons that internal controls become deficient, it’s important to spend a moment on what internal controls are designed to do, and what could happen when controls don’t work as intended.
Internal controls are designed to help reduce risk by avoiding, detecting, or correcting the things that introduce or create risk. While it is not really practical for an organization to eliminate all risks, a good control environment can help maintain a risk posture that is acceptable to the specific circumstances of the organization. For example, security controls are safeguards designed to avoid, detect, or minimize security risks to physical property, digital information (e.g., sensitive customer data or a company’s intellectual property), computer systems, mobile devices, servers, and other assets.
Security controls could fall into one of the following categories:
- Physical controls: doors, locks, security cameras
- Procedure controls: incident response processes, management oversight, security awareness and training, background checks for personnel who handle critical systems
- Technical controls: user authentication (login) and logical access controls, antivirus software, firealls
- Legal and regulatory controls: policies, standards, etc.
Security controls can also be classified according to the time that they act, relative to a security incident:
- Before the event: preventative controls are intended to stop an incident from occurring, e.g. by locking out unauthorized users
- During the event: detective controls are intended to identify and characterize an incident in progress, e.g. by sounding the intruder alarm and alerting the appropriate personnel such as system administrators, security guards or police
After the event: corrective controls are intended to limit the extent of damage caused by an incident, e.g. restoring a system to normal working status as fast as possible
Common reasons internal controls become deficient
1. People change roles, leave your organization, or simply get too busy
One common reason why a control stops operating is that the person responsible for performing a control stops performing that control. This could happen because someone gets too busy, switches roles within an organization, leaves the organization altogether, or takes a leave of absence.
How this could happen:
- Software updates and patches. You don’t have a centralized patch management function. Instead, multiple people deploy patches for different systems. If an IT manager forgets and goes on a leave-of-absence, the patches that they were responsible for deploying do not get deployed. Failure to patch software can lead to serious consequences, such as an entire website going down.
- Coordinating penetration testing. An individual is responsible for coordinating penetration testing with a 3rd party provider once a year. The individual leaves the company and forgets to transition coordination of penetration testing to someone else before they leave.
- Updating a security policy. There are many cybersecurity frameworks that say security personnel in your organization have to review your security policy annually. Since it’s a once-a-year task, it’s not top of mind. Your head of security has put a task to review the security policy on his calendar, but he ends up leaving the company 12 days before he’s supposed to perform it. Unfortunately, no one else was sure about when the security policy ought to be reviewed, or remembered to take over this task.
How to avoid this pitfall
A good way to avoid a control failure related to non-performance is to have visibility into the controls that are not being performed in a timely manner. This includes knowing who is responsible for operating each control, when they are supposed to perform the control process, and having a mechanism for being notified when the control process did not operate when it was supposed to.
Additionally, it’s important to build in redundancies or multiple controls to safeguard the critical assets if the primary control fails. Specifically, if a control fails, it is good to have a “backup” control that can mitigate the risk that the original control was designed for.
Last but not least, it’s important to train all control operators on what it means to operate a control properly, and why it’s important that they perform their control processes on time. You can also reinforce desired behavior from these process owners and control operators by incorporating compliance results into your variable pay plan.
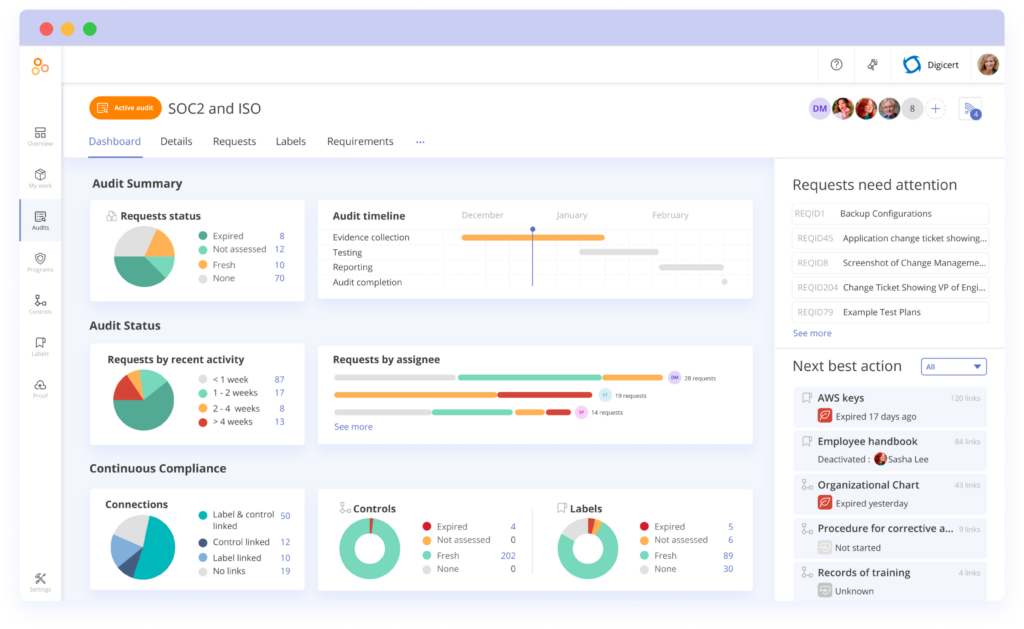
How Hyperproof can help ensure consistency
Hyperproof gives compliance managers visibility into control process performance. Hyperproof provides the ability to assign “owners” to each control, tell control operators when a piece of evidence needs to be submitted, and remind control owners to provide evidence of control performance according to a predetermined cadence.
For instance, with Hyperproof you can specify that John, an IT Security Analyst, conduct penetration testing once a quarter. Then, through Hyperproof’s dashboards, you can easily see if evidence has been provided that demonstrates penetration testing has been performed.
A compliance manager can also easily re-assign a control to someone else, if the original control performer has left your organization or is out-of-office.
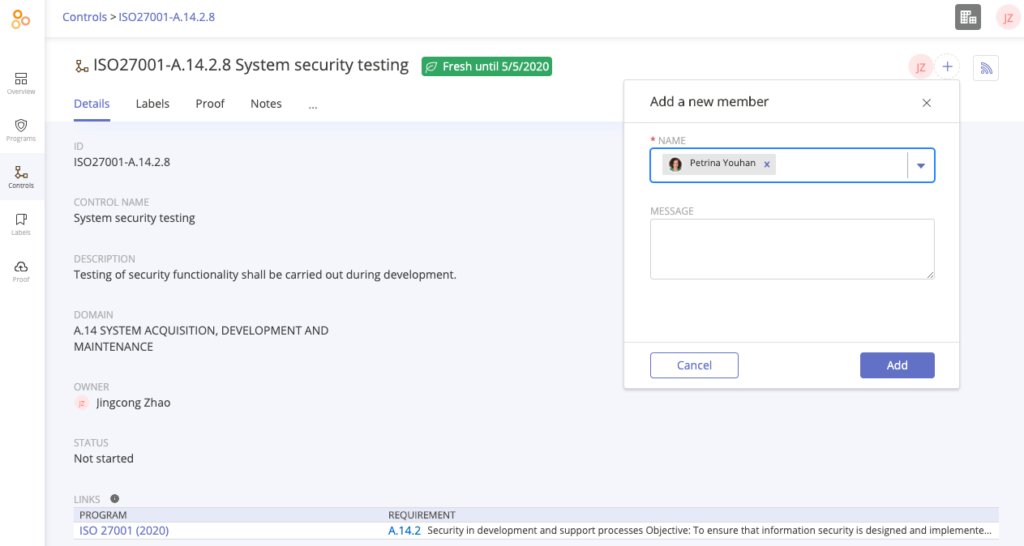
2. Your business processes or technology changed, but you have not updated the design of your controls.
This type of control deficiency happens most frequently in organizations that are growing quickly.
How this could happen
Here’s a common scenario: a couple of years ago an IT security manager created an account management control based on the technology stack at that time. The control was considered just fine in last year’s SOC 2 audit. However, at the beginning of this year, the organization implemented a new system used in performing the control, which made the control’s design out-dated. Yet, no one has remembered to update the control design.
For instance, you have an access management control for your CRM system that says, “All users who want to gain access to the company’s CRM system need to submit a request ticket through JIRA”. This control was written before your organization implemented ServiceNow as their ticketing system. In the past few months, several employees have asked your Sales Ops administrator to get access to the CRM system via a ServiceNow ticket, and your Sales Ops administrator approved the access requests through ServiceNow.
In this case, your control would be considered deficient because the language in your control was not updated to say that “ServiceNow” is an acceptable method for requesting and approving access.
How to avoid this pitfall
The best way to avoid issues like the above is to set an appropriate cadence to review each control according to the risk it represents to the organization. Then use a good project management system to remind control operators to review the controls within their domain according to that cadence.
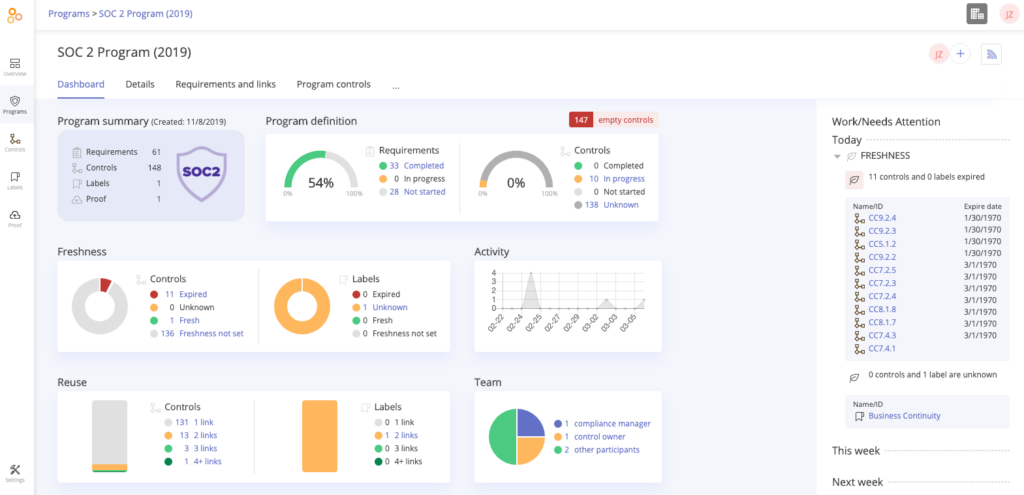
How Hyperproof can help with keeping controls up-to-date
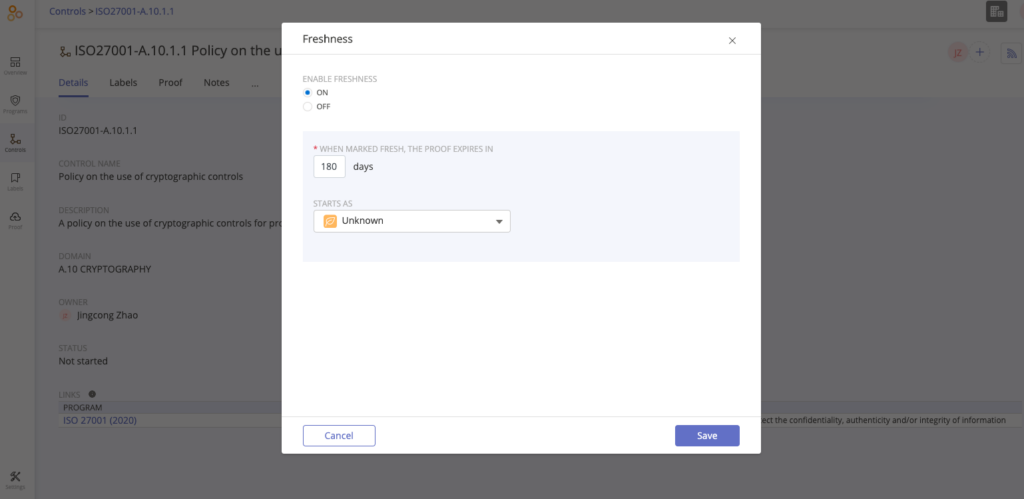
Hyperproof lets you easily view and update your control language. You can also set a “freshness” policy (a “due date”) on the evidence files needed to validate a control, so if evidence linked to a control has expired, you know it’s time to revisit that control.
3. You missed a requirement all together
Compliance control frameworks themselves can periodically change. For example, the AICPA updated the SOC2 trust service criteria last year and introduced brand new control expectations for organizations to meet. When a compliance standard gets updated your organization will have to build out new controls to keep up with the revised requirements.
Without ongoing vigilance it’s all too easy for organizations to miss these updates from assessment and certification bodies.
How to avoid this pitfall
The best way to mitigate this risk is to stay up-to-date with applicable regulations and compliance standards. It’s difficult to do this manually, but with regulatory monitoring technology, keeping up with standards become much more manageable.
On-demand webinar
To learn more about how to avoid these common control deficiencies and how Hyperproof can help, you can watch our on-demand webinar How to Avoid Common Control Deficiencies.
On the webinar, I share strategies and tactics on how to avoid these common control deficiencies and improve the quality, efficiency and consistency of your compliance program. This webinar’s content is informed by my experience leading IT security and compliance engagements at a Big 4 firm. While there, I conducted assessments of my clients’ internal control environments, to help them strengthen and streamline their risk posture.
Banner photo by Green Chameleon on Unsplash
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?