Guide
Getting to Know the ISO 27001 Standard
Practical Guidance for achieving ISO 27001 certification

Overview of ISO 27001 and key benefits
ISO/IEC 27001 is an information security standard designed and regulated by the International Organization for Standardization, and while it isn’t a legally mandated framework, it is the price of admission for many B2B businesses and is key to securing contracts with large companies, government organizations, and companies in security-conscious industries.
ISO 27001 defines what an information security management system (ISMS) is, what is required to be included within an ISMS, and how management should implement, monitor, and maintain an ISMS. It is notable for being an all-encompassing framework for protecting all types of digital information, including employee data, financial data, customer data, corporate IP, and third-party entrusted information. ISO 27001 also comes with a control set for organizations to implement to address their information security risk, known as Annex A of ISO 27001.
To obtain an ISO 27001 certification, an organization must hire an accredited certification body to perform an independent assessment verifying that the organization’s ISMS conforms to the requirements of the ISO 27001 standard. An issued certificate is valid for a three-year term, during which time surveillance audits must be completed. The ISO certificate is meant to communicate that the ISMS is actively implemented and continues to operate effectively.
Here is what makes ISO 27001 certification compelling and desirable: a business that is ISO 27001 certified has invested significant time and resources in understanding risks, protecting information assets and increasing business resilience, and their clients and partners can be certain they’re doing business with an organization that takes security seriously.

An ISO 27001 certification can help reduce audit fatigue by eliminating or reducing the need for spot audits from customers and business partners. Many companies annually audit their customers and business partners as part of their risk management process. As a vendor, you may be bombarded with a high volume of time consuming audits coming from multiple sources. An ISO 27001 certification is a great solution for this, as companies will often accept your certification in place of conducting a separate audit.
The certification can also help you protect your reputation in the event of a data breach. When customer data is accessed or stolen, reputations suffer. However, showing that your business is compliant with one of the most stringent security standards can help you demonstrate your good faith efforts to protect their data and privacy. Lastly, if your business is ISO 27001 compliant, it’s highly likely that you’re compliant with other security standards, including legally mandated ones. Maintaining an ISO 27001 certificate can help you ensure you’re compliant in other standards and regulations on a continual basis.
In this guide, we will break down the core requirements of ISO 27001 in simple terms, provide practical tips on becoming certification ready in a highly efficient way, and showcase how compliance operations software can help you jumpstart your ISO 27001 effort.
Because this guide describes the ISO 27001 core requirements in detail, you can use it as a reference to understand what controls you already have within your organization and identify the additional controls you’ll need to create and implement to fully meet this standard.
How to become ISO 27001 certified: the key steps
Becoming ISO 27001 certified isn’t quick or easy; the length of time it takes varies from organization to organization and depends on a lot of different factors. Conservatively, businesses should plan on spending at least a year to become compliant and certified.
The preparation process

Here are the key activities your organization will need to undertake to be ready for an external auditor to conduct the formal audit needed to achieve a certification.
- Determine which areas of your business will be within the scope of your ISMS. Each business is unique and houses different types and amounts of data, so before building out your ISO 27001 compliance program, you need to know exactly what information you need to protect.
- Develop a project plan. It’s important to treat your ISO 27001 initiative as a project that needs to be managed diligently. Planning involves several key pieces, including getting leadership commitment, understanding the needs and expectations of all parties that have a stake in Information security and determining the boundaries of your ISMS. These requirements are outlined in Clause 4 and 5 of ISO 27001. Getting leadership commitment early in the process is key because your leadership team will need to be aware of ISO 27001 requirements and commit to performing certain key activities, such as setting security objectives and ensuring that information security management system requirements are integrated into your organization’s processes.
- Define an information risk assessment process and use that process to identify, analyze and evaluate information security risks. ISO 27001 requires each organization to define an information risk assessment process that contains risk acceptance criteria and criteria for performing information security risk assessments. Each organization also needs to ensure that their risk assessment process is set up to produce consistent and comparable results. Once the risk assessment process is created, your organization will need to use it to identify risks associated with the loss of confidentiality, integrity and availability for information within the scope of the ISMS and track those risks somewhere (ideally in a centralized risk register).
- Design and implement controls to treat security risks identified during your risk assessment process. During this stage, you’ll need to determine which controls are needed to sufficiently address the risks you’ve identified. You’ll need to refer to ISO 27001 Annex A as your control baseline and ensure that no necessary controls are overlooked. You should assign individuals or teams to manage the risks, ensuring that they’re onboard with the proposed controls and are accepting of the residual information security risks. Keep in mind that your entire control set as well as your control selection process need to be documented, as documentation is a requirement of ISO Clause 7.5 and your auditors will ask to see this documentation as a part of their assessment.
- Conduct an internal audit. How can you be sure that your ISMS is effectively implemented and maintained? The key is to conduct your own internal audit of your ISMS and control activities at regular intervals. ISO 27001 Clause 9 contains a number of requirements on how an internal audit ought to be conducted (ISO calls this “performance evaluation”). In ISO language, if you find that the ISMS isn’t conforming to ISO standard, or if it’s not effectively implemented or maintained, that finding is a “nonconformity”. Again, you must retain evidence of the audit process and audit results.
- Address the nonconformities found during the internal audit and take corrective action. ISO 27001 Clause 10 requires your organization’s management team to review the results of internal audits and react to “nonconformities” that were discovered. A treatment might involve taking an action to control and correct the nonconformity or making a more significant change to the ISMS. Again, your organization needs to retain documentation of the nature of issues, any subsequent actions taken, and the results of any corrective actions.
The ISO 27001 audit process
Once you’ve stepped through these phases, you’ll schedule the certification assessment with a qualified assessor.
An ISO 27001 audit occurs in two stages:
An ISO 27001 certificate will only be issued if all major and minor nonconformities have been corrected and remediation activities were performed for all major nonconformities. You will need to provide acceptable corrective action plans (CAPs) for each nonconformity.
An ISO 27001 certificate is valid for three years. In year 2 and 3, your organization will need to go through surveillance audits (or mini-audits). After three years, you’ll need to complete full-scale audits (Stage 1 and 2) in order to receive a new certificate.
Working with an accredited certification body is critical, because non-accredited certification bodies may not be subject to regular performance, quality, and competence monitoring by a national accreditation body, such as the ANSI-ASQ National Accreditation Board (ANAB). We recommend that you use ANAB’s directory to confirm that a certification body has a valid ANAB accreditation certificate.
Determining the ISO 27001 scope

Before you proceed further on the journey, you need to determine which areas of your business will be within the scope of your Information Security Management System (ISMS). Each business is unique and houses different types and amounts of data, so before building out your ISO 27001 compliance program, you need to know exactly what information you need to protect.
Information security should be about doing business more securely, not simply ticking boxes. You want to understand the internal and external issues that affect the intended outcome of the information security management system and what the people invested in your ISMS want and need from ISO 27001 compliance. The first control domains in ISO 27001—4.1 and 4.2—outlines your ISMS’ scope, which we’ll discuss more in the next section.
Once you’ve determined the relevant issues and interested parties, you have the building blocks to address clauses 4.3a-c: recording the scope of your ISMS. This is a crucial first step, because it will tell you exactly what you need to spend time on and what isn’t necessary for your business.
Getting to know ISO 27001 core requirements
Clause 4. Context of Organization
The first requirements you will encounter when reading ISO 27001 are in Clause 4. Context of the Organization.
Clause 4.1 is about relevant internal and external issues. Because ISO 27001 doesn’t offer a lot of information about what exactly constitutes an internal or external issue, this can be a tricky first step for businesses that are totally new to compliance.
Some examples of internal issues might include things such as internally stored or managed information assets, personnel issues such as high turnover rates or difficulty recruiting qualified individuals, or current compliance processes that are causing issues.
Clause 4.2 has to do with the “interested parties,” and their requirements. These interested parties do include customers and partners, but they also include employees, management, suppliers, and regulators. Anyone who has a say or an interest in your data security should be considered here. Once you’ve identified all of the stakeholders, you can identify which of those parties has the most influence on your security posture and begin to pare down that list to the most inclusive and realistic list of requirements.
Clause 4.3 requires the establishment of the scope of your eventual ISMS and states that you must consider the issues and interested parties you identified and the interfaces and dependencies between those issues and interested parties while developing this scope.
Finally, clause 4.4 requires the establishment, implementation, and maintenance and improvement of an ISMS. Ultimately, the evidence you use to prove compliance with this clause will be the culmination of the rest of the controls that you will develop, which will all be informed by clauses 4.1 through 4.3.
Clause 5. Leadership
Control family 5 addresses your business’s leadership and management. Senior management’s support of your company’s culture of compliance is critical to its success, so much so that ISO has dedicated three clauses and 17 sub-clauses to ensuring your business is hitting every part of leadership involvement needed to make a compliance program successful.
5.1 Leadership and Commitment: These requirements comprise almost half of control family 5, and they lay out the steps that leadership needs to take to ensure compliance is a company-wide priority. For example, the leadership needs to establish information security objectives, make the resources needed for ISMS creating and maintenance available, and promote continual improvement. Finally, 5.1.h dictates that leadership must “support other relevant management roles to demonstrate their leadership as it applies to their areas of responsibility.” Depending on the size of your company and what kinds of information security and compliance staff you have, this might include your Chief Information Security Officer, IT Director, HR Director, and more.
One of the most difficult parts of proving compliance with clause 5.1 is collecting evidence. While you might see evidence every day of your CISO or CEO providing support to other managers or promoting continual improvement of your information security program, how do you document that? Part of your ISMS’ function will be to find and collect this kind of evidence so that you can show during your audit that your senior leadership is taking these responsibilities seriously.
5.2 Policy: This clause requires that leadership establish an information security policy, ensure that it’s tailored to your organization, and that it includes some key features, like information security objectives and a commitment to continual improvement of the ISMS. Leadership also has to make the policy available to interested parties when it’s necessary and communicate the policy throughout the organization.
The final leadership responsibilities, stated in clause 5.3, are assigning responsibility and authority for 1) ensuring the ISMS conforms to the information security standard they’ve developed and 2) reporting on the performance of the ISMS.
Clause 6. Planning
This control family broadly addresses what your business needs to plan in terms of recognizing and addressing risks and opportunities. Clause 6 is broken down into four smaller sections:
6.1.1: General risk planning: This clause covers identifying risks and opportunities to 1) make sure your ISMS can achieve its intended outcome, 2) reduce or prevent undesired effects, and 3) ensure your ISMS is continually improving. This section also requires planning specific actions to address the risks and opportunities determined above as well as defining and implementing a process for assessing information security risks.
In short, your business needs a documented process for identifying, assessing, and treating information security risks that are integrated into your ISMS.
6.1.2: Information security risk assessment: This clause covers, in more detail, ISO 27001’s requirements for an information security risk assessment process that meets some specific criteria, such as including risk acceptance and assessment criteria and producing consistent, valid, and comparable results.
It also includes requirements for applying this risk assessment process to identify the risks to your business in the face of a possible loss of confidentiality, integrity, and availability, assessing the consequences and the likelihood of those risks, and using the process to evaluate the risks and see how they compare to the risk acceptance and assessment criteria you developed earlier.
Essentially, this section requires you to develop a process to identify and evaluate risks to your information that produces consistent and actionable results.
6.1.3: Information security risk treatment: Once you’ve developed a process for identifying and evaluating risk, clause 6.1.3 requires that you develop a process for risk treatment. Ultimately, this process will help you determine whether your organization will tolerate the risk, take steps to terminate it, or transfer the risk to another party; how to implement the treatment option you choose; and how to develop a risk treatment plan. Finally, this risk treatment plan and any residual information security risks that come along with it have to be approved by the risk owner.
6.2: Information security objectives and how to plan to achieve them: The final clause in the Planning control family lays out requirements for information security objectives that your business must develop. Among other things, these objectives have to be consistent with your company’s information security policy, measurable, communicated, and updated when needed.
To meet ISO 27001 standard, your business also must determine what resources will be required to meet the objectives, who will be responsible for each objective, when they will be completed, and how the results will be evaluated. You’ll also have to maintain documentation on all the information security objectives.
The Planning control family requires a lot of work, because even in an organization that has some of these elements in place, they usually aren’t as thoroughly documented as ISO 27001 requires. But that documentation is critical for these risk assessment and treatment plans to work. People have to be able to access and carry out these plans consistently, and that can’t happen if they aren’t documented and readily available.
Clause 7. Support
Control family 7 is all about the different types of support that your ISMS will need for proper maintenance and improvement, and it covers five types of support:
7.1 Resources: To introduce the requirements in this section, ISO 27001 states that businesses must, “Determine & provide the resources for the establishment, implementation, maintenance & continual improvement of the ISMS.” Below, the standard goes into more detail about what kind of resources must be provided and what you need to establish surrounding each of these resources.
7.2 Competence: This clause is summed up pretty well by 7.2.a, which states that your business must, “Determine the necessary competence of the person(s) doing work that affects its information security performance.” Auditors will need to see documentation of your staff’s training, education, or experience or documentation of the actions being taken to ensure that your employees are moving towards being competent.
7.3 Awareness: This clause is straightforward; it requires that you show that your employees are aware of the information security policy and that they understand their contribution and what will happen if they don’t comply with the ISMS requirements.
7.4 Communication: The Communication clause lays out everything you need to know in regards to internal and external communication with your ISMS: What you’re communicating, when you’re communicating, who it’s being communicated to, and who is communicating it. This is a pretty simple set of requirements.
7.5 Documented information: Essentially, this clause provides guidelines for the documented information you need to have about your ISMS, and there is quite a bit of it. It refers to what information is documented as well as how it’s formatted, labeled, and the review and approval of documentation.
Clause 8. Operation
While much of ISO 27001 up to this point has focused on planning, control family 8 lays out the requirements for your ISMS’ operation and what plans, documentation, and controls you need to have in place to ensure your ISMS is operating correctly and meeting all of the requirements in ISO 27001.
8.1 Operational planning and control: This clause should be easy to demonstrate compliance so long as you’ve documented it well. In control families 6 and 7, you should have done a lot of work to develop your information security management system and document who is responsible for what parts of your ISMS. Much of the documentation for this section will be replicated from earlier clauses.
8.2 Information security risk assessment: In clause 6, you developed some detailed plans for how to assess and evaluate the risks you’re facing now and how you’ll address risks in the future — especially the risks that you don’t know about or aren’t yet facing. This clause covers what you need to document the success of your assessment process.
8.3 Information security treatment: Similarly to the previous clause, clause 8.3 lays out what you should be doing once you’ve developed an information security risk treatment plan: utilizing it and documenting the outcomes.
Clause 9. Monitoring
An ISMS is not a set-it-and-forget-it solution: threats to information security are constantly changing, and as your business practices adapt to those threats, your ISMS will also need to adapt. Control family 9 lays out detailed requirements for monitoring, auditing, and reviewing your program.
9.1 Monitoring, measurement, analysis, and evaluation: By now, your ISMS should be up and running, and you should consistently monitor how it’s working and evaluate whether or not it’s helping your company meet the information security objectives that your leadership team has set. Clause 9.1 is the first step in that monitoring.
9.2 Internal audit: This clause takes the monitoring and analysis a step further and requires that you perform internal audits on your ISMS and look not just at the outcomes, but whether it’s conforming to internal and external standards and whether you’re maintaining it properly.
9.3 Management review: This is another place where management’s involvement in this process is absolutely critical. This isn’t just a box to tick off for senior management or for your information security team; it’s a chance to make sure that your company’s ISMS is still in-line with your company’s bigger goals and whether it’s adequately meeting your business’ needs. Upper management has the birds-eye view needed to make this final review valuable.
Clause 10. Improvement
In the previous control family, ISO 27001 lays out all the requirements for auditing and analyzing your program. The next step, and one that needs to be in progress continually, is the improvement of your ISMS. Technology is changing rapidly, and executives see the effects of these changes in their business every day. To continually protect the information your business stores and processes, your ISMS needs to be evolving and improving all the time.
10.1 Nonconformity and corrective action: Even the strongest and most up-to-date ISMS will eventually encounter a nonconformity; we’ve seen that even huge companies with large security budgets are susceptible to data breaches. How you react to those nonconformities is as important as the work you put into minimizing and avoiding them.
10.2 Continual improvement: The final clause in ISO 27001 simply states that you must, “Continually improve the suitability, adequacy, and effectiveness of the ISMS.” If you’ve already implemented all of the other parts of this framework, such as the risk assessment and treatment in control family 6, the internal audits and management reviews in control family 9, and the corrective actions required in 10.1, you’re already taking significant steps towards improving your ISMS. Continue to look for other ways that you can improve things. This can be done through research, meeting and talking with other information security professionals, and by analyzing the data you’re documenting as a part of ISO 27001 compliance.
Appendix A Controls
Annex A provides a list of security controls that are meant to be used to improve information security. All controls of Annex A need to be considered in the process of obtaining your ISO 27001 certification. Any controls in Annex A that are not implemented require justification as to why they aren’t applicable to the scope of the ISMS, so you need to ensure you’ve considered each one carefully and implemented any that are applicable to your business.
9 project management tips to help you achieve certification readiness efficiently
1. Secure executive buy-in from the beginning

To become ISO 27001 certified, your entire organization will need to accept and adapt to certain changes. To ensure that your ISMS meets the ISO 27001 standard, you’ll likely need to create new policies and processes, change some internal workflows, add certain new responsibilities to employees’ plates, implement new tools, and train people on security topics. Auditors also expect you to create detailed deliverables, including a Risk treatment plan (RTP) and a Statement of Applicability (SoA). All of this work takes time and commitment from stakeholders across an organization. As such, having senior executives who believe in the importance of this project and set the tone is crucial to its success.
2. Hire an outside expert to conduct a gap analysis if you’re not familiar with ISO 27001
A gap analysis provides a high level overview of what needs to be done to achieve certification and compares your organization’s existing information security measures against the requirements of ISO 27001. It also helps to clarify the scope of your ISMS, your internal resource requirements, and the potential timeline to achieve certification readiness. If you don’t have internal expertise on ISO 27001, getting a credible consultant with the requisite experience in ISO 27001 to conduct the gap analysis can be highly beneficial. An experienced expert can help you develop a business case and a realistic timeline to achieve certification readiness — so you can secure the necessary leadership commitment and investment.
3. Appoint a project leader
It is important to identify someone who’s dedicated to driving the project forward. The project leader will convene with senior leaders across the organization to review objectives and set information security goals. This person will develop a project plan and assign roles and responsibilities to other stakeholders. This person will also develop forums (e.g., ISO 27001 executive committee and an ISO 27001 work committee) to ensure progress is being made consistently.
4. Be careful about scoping the ISMS
Scoping is about deciding which information assets to “fence off” and protect. It’s a decision each business has to make for itself. Doing this correctly is critical because defining too-broad of a scope will add time and cost to the project, but a too-narrow scope will leave your organization vulnerable to risks that weren’t considered.
5. Establish a risk management framework that meets the requirements of ISO 27001
The assessment and management of information security risks is a key component of ISO 27001. Make sure you use a risk assessment method that’s ISO 27001 approved and approved by your senior management. According to ISO 27001, a formal risk assessment methodology needs to address four issues: 1. Baseline security criteria; 2. Risk appetite; 3. Risk scale; 4. Assessments are based on specific scenarios or covering specific assets.
6. Break down control implementation work into smaller pieces
Use a visual project management tool to keep the project on track. ISO 27001 requires organizations to apply controls to manage or reduce risks identified in their risk assessment. To keep things manageable, start by prioritizing the controls mitigating the biggest risks. Scope out the work and break it out into two- or threeweek sprints. List out the tasks you (and others) need to complete and put them on a calendar. Make it easy to track your team’s progress by putting your tasks into a compliance project management tool with good visualization capabilities.
7. Map existing controls to ISO 27001 requirements
If ISO 27001 isn’t your organization’s first security compliance program, you’ll have existing controls that can be leveraged to meet ISO 27001 requirements. For instance, if you’ve done SOC 2 Type 2, you may already have security controls that work for ISO 27001. By taking the time to evaluate existing controls and crosswalking them to ISO 27001 requirements, you’ll be able to avoid duplicative work when it’s time to test controls and collect evidence. You’ll also have a smaller set of controls to monitor and review. This type of control mapping exercise can be done manually, but it’s much easier to manage within purpose-built compliance software.
8. Document things as you go so preparing the Risk Treatment Plan (RTP) and Statement Of Applicability (SOA) take less effort
The risk treatment plan (RTP) and Statement of Applicability (SoA) are key documents required for an ISO 27001 compliance project. The RTP describes the steps taken to deal with each risk identified in the risk assessment. The SoA lists all the controls identified in ISO 27001 and outlines whether each control has been applied and why it was included.
If you consistently document the risks and the controls while the actual work is happening, you don’t need to go back and spend a lot of energy putting these two documents together.
Further, there are purpose-built compliance software such as Hyperproof that are built to help you consistently manage risks and controls — saving time in producing documents for audits.
9. Consider scheduling multiple audits simultaneously
Although different customer segments may want to see different certifications and audit reports from you, many security standards (e.g. HITRUST, SOC 2, ISO 27001, etc.) share some core requirements.
If ISO 27001 is one of multiple security audits you go through each year, see if you can convince your auditors to schedule all the audits in the same timeframe (e.g. 2 or 3 week window). We’ve talked to multiple organizations that have done this, so that the compliance team can gather and submit one set of evidence to their auditors once a year. Doing it this way is less of a burden than having multiple audits spread across the year.
How compliance operations software can help you meet the ISO 27001 standard

Hyperproof is a cloud-based compliance operations software platform that removes the heavy-lifting involved in adhering to information security standards such as ISO 27001.
Hyperproof can be your central system for planning, managing, and monitoring all compliance work and help compliance professionals drive accountability for security and compliance to stakeholders across an organization.
Hyperproof can help you become ISO 27001 certification ready and stay in compliance over time with little effort by helping you:
- Understand ISO 27001 requirements in detail
- Document your infosec risk assessment results and risk response plans
- Develop your ISMS by implementing controls, assigning roles and
responsibilities, and keeping people on track - Streamline evidence collection and management
- Know how close you are to being certification-ready
- Monitor your ISMS and make continuous improvements
By using Hyperproof to operationalize security and IT governance, organizations can create a secure environment where compliance becomes an output of people doing their jobs. The platform helps organizations gain efficiencies in compliance work, so stakeholders can focus on good operations instead of spending extra time to tick off boxes for compliance.
1. Understand the standard and the specific requirements you’ll need to meet
Hyperproof comes with an ISO 27001 starter compliance template designed to help organizations accelerate their journey to compliance. The template comes with all ISO 27001 control families and all Annex controls organized by domains (e.g., Leadership, Planning, Support Operations, etc.) – so you know what standard you have to meet to become ISO 27001 certified.
2. Document your information security risk assessment results and risk response plans
To meet the ISO 27001 standard, one of the first things your business has to do is create an information security risk assessment process to identify and evaluate risks to your information. And you need to ensure that the process meets specific guidelines, such as documenting risk acceptance and assessment criteria and producing consistent, valid, and comparable results.
By using Hyperproof’s Risk Register module, risk owners from all functions and business units can document the results of risk assessments in a consistent format and all risk treatment plans, allowing organizations’ leaders to better manage resources and prioritize risk mitigation activities.
For each risk tracked in Hyperproof, you can map it back to a control (a documented process or set of steps you intend to follow to mitigate the risk) and designate a mitigation percentage for that control. Adding this type of rigor will help company leaders fully understand the risks they’re taking on in pursuit of business objectives and the resources required to adequately mitigate certain risks.
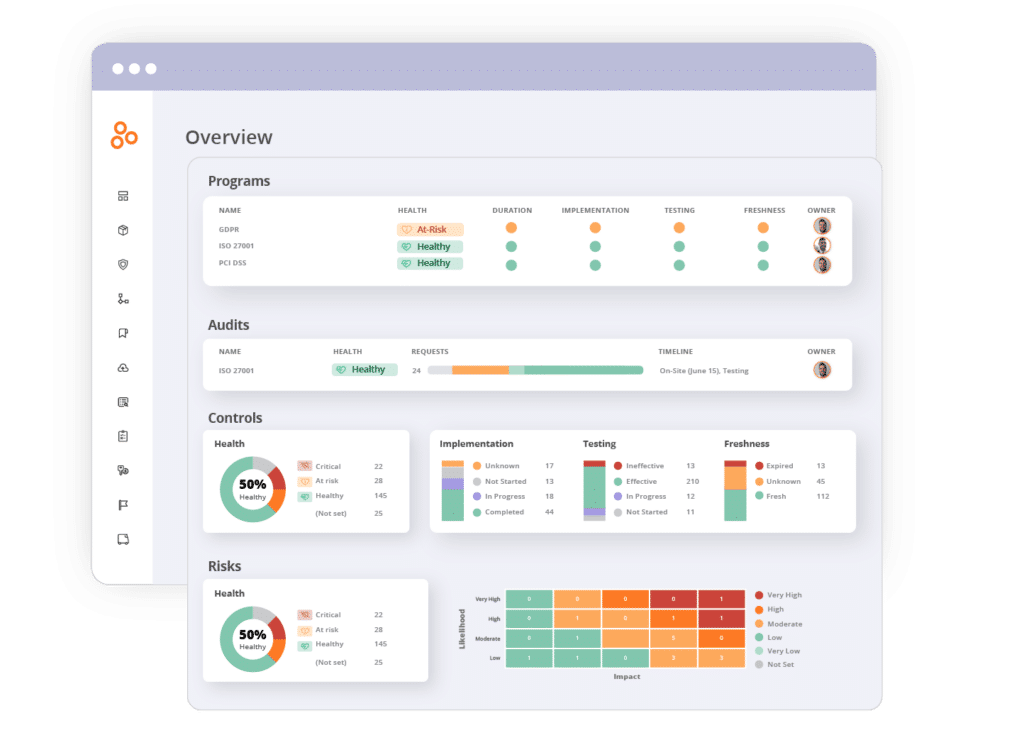
3. Develop your information security management system, document who’s responsible for what parts of your ISMS, and keep everyone on track
Many organizations choose to tackle the ISO 27001 standard not only because their customers trust its name, but also because they know this effort will push their entire organization to become better at documenting what they do from a security standpoint and more consistent at monitoring the effectiveness of their security controls.
Hyperproof makes it much easier to document your information security management system and ensure that activities to monitor and improve your ISMS are happening throughout the year.
Using Hyperproof’s ISO 27001 starter template, you can work your way through the sections and document the procedures and steps (controls) you’re taking to adhere to each guideline.
You’ll be able to designate the responsible party (or team) for operating each control in Hyperproof, document what type of evidence is needed for someone to test the operating effectiveness of a control, and set review cadences for controls to ensure they’re evaluated on a timely basis based on their importance to your objectives.
Using Hyperproof’s native task management system, you can assign tasks to individuals to ensure that control activities such as periodic risk assessments, management reviews, access control reviews, and more are performed in a timely manner. Participants can either get their work done in Hyperproof or in the project management tools of their choice. Because Hyperproof integrates with third-party project management tools, all activities related to tasks are synced back to Hyperproof.
When you have an operations platform for managing ongoing compliance work, you’ll be able to ensure that your ISMS is operating correctly at all times and meeting all the requirements laid out in ISO 27001.
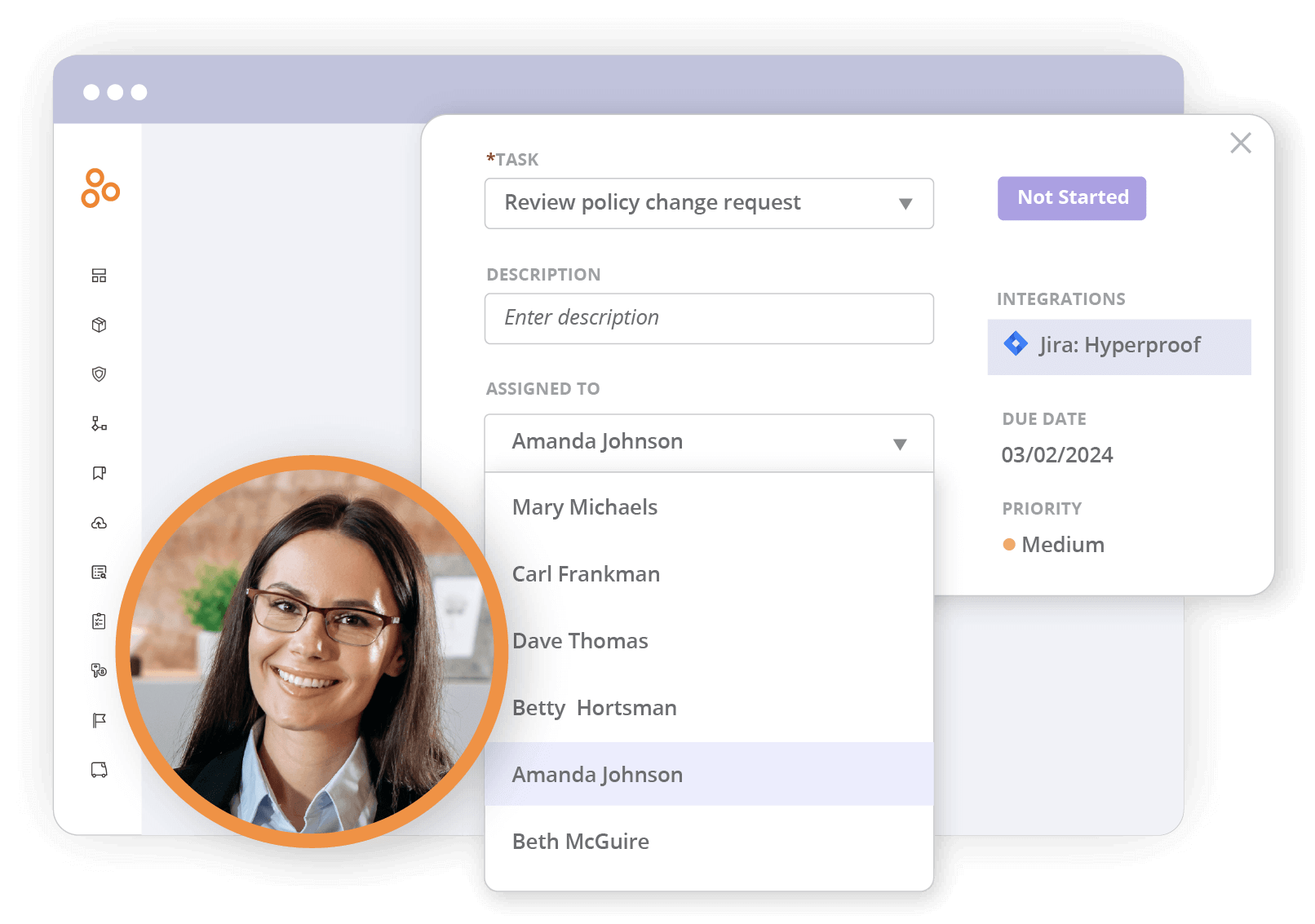
4. Conduct internal audits efficiently
You can use Hyperproof to set up an internal audit program to audit your organization’s ISMS and control activities. Within Hyperproof, all evidence of the audit process and the results can be maintained.
Instead of developing your own file system for storing all documents related to all the processes you’re running to adhere to ISO 27001, you can store all evidence in Hyperproof and link each piece of evidence to the right control and requirement.
Hyperproof provides the ability to link one evidence file to multiple requirements and controls so you don’t have to pull the same evidence files again and again if you’re preparing for multiple audits. Hyperproof also has a feature called Hypersync, which allows you to automatically extract data (e.g., backup settings, encryption settings, access groups, user lists, and more) from dozens of cloud-based apps and services on a cadence or on-demand and store them in Hyperproof.
If you want to collect a piece of proof manually from an employee in your company, Hyperproof has made it easy with our built-in integrations to popular communication and project management systems like Slack, Microsoft Teams, Jira, and Asana.
5. Take corrective action
In ISO 27001, being able to continually manage nonconformities identified from internal and external audits is key. All remediation activities can be managed within the Hyperproof platform. In fact, Hyperproof can automate certain activities such as assigning tasks to individuals or teams and reminding people to get their work done. Business stakeholders do not need to learn new tools just to do compliance work occasionally. They can receive notifications to complete tasks through the tools they are already using (e.g., Slack, Microsoft Teams, Jira), complete the tasks in those tools, and have information routed back to and reflected in Hyperproof in near real-time.
6. Monitor your ISMS and make continuous improvements
The work isn’t over once you’ve achieved your ISO 27001 certification. ISO 27001 Clause 9.1 specifically states that once your ISMS is up and running, you should consistently monitor how it’s working and evaluate whether or not it’s helping your company meet the information security objectives your leadership team has set.
To that end, you’ll need to know how you’re going to monitor, analyze, and evaluate your ISMS’s performance, determine a schedule for how often those monitoring activities will take place, determine how often the collected results will be analyzed, and make sure someone has been specifically assigned to perform monitoring activities. If results are off, then you’ll also need to figure out how controls can be improved to bring your ISMS into a healthy state.
Hyperproof can be the platform for scoping out and executing these types of monitoring and performance improvement activities on a continuous basis.
Wondering what ISO 27001 and future ISO 27001 updates mean for you? Our webinar explains what the main changes were and what your organization needs to do to transition.
Download the PDF









