Guide to
What Counts As Personal Identifiable Information
In the past few years, various states within the country have amended their cybersecurity and data privacy laws to give them more teeth. Lawmakers are expanding the definition of what counts as Personal Identifiable Information under those regulations and, as a result, have put a greater onus on businesses to get meaningful consent before acquiring consumer data and to implement security safeguards.
In this piece we’ll take a look at the different types of personal information that are covered under various data protection regulations. We’ll also highlight some key regulations in the U.S. that may impact your organization’s data handling and data security practices.
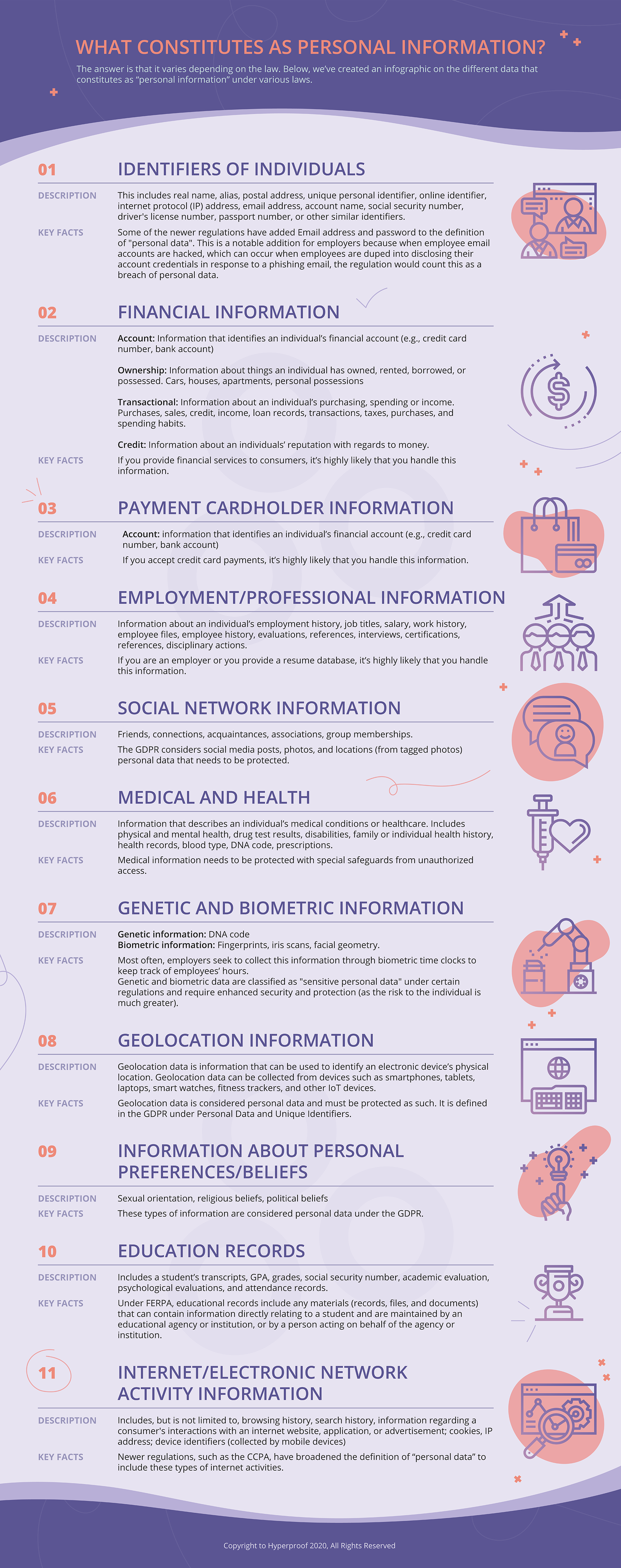
An overview of key data protection laws
As of this writing, Vermont is the latest state to amend its data breach notification law (signed into law this year).
Vermont has amended its Security Breach Notice Act
The amendments to Vermont’s Security Breach Notice Act include expanding the definition of Personally Identifiable Information (“PII”), expanding the definition of a breach to include login credentials, and narrowing the permissible circumstances under which substitute notice may be used. Notably, the amendments include:
Expanding the definition of PII to add the following data elements, when in combination with individual’s first name or initial and last name:
- individual taxpayer identification number, passport number, military identification card number or other identification number that originates from a government identification document that is commonly used to verify identity for a commercial transaction;
- unique biometric data generated from measurements or technical analysis of human body characteristics used by the owner or licensee of the data to identify or authenticate the consumer, such as a fingerprint, retina or iris image, or other unique physical representation or digital representation of biometric data;
- genetic information; and
- health records or records of a wellness program or similar program of health promotion or disease prevention, a health care professional’s medical diagnosis or treatment of the consumer or a health insurance policy number.
The Vermont law also expanded the definition of a breach to include someone’s login credentials, meaning “a consumer’s username or email-address, in combination with a password or an answer to a security question, that together permit access to an online account.”
Vermont is by no means the first state to expand the definition of PII within its cybersecurity laws. The California Data Privacy Act, which is already in effect, also puts a wide range of information under the protected category of “personal information”.
The California Consumer Privacy Act

The California Consumer Privacy Act (CCPA) requires that covered companies develop robust privacy policies that tell Californian residents whether their personal information will be sold to third parties and how they can opt-out and request to see their information, and that they provide tools to verify the identity of the requestor. Similar to the GDPR, businesses covered under the CCPA are required to honor a set of consumer rights and must have clear processes to fulfill their requests. Like the GDPR, the CCPA also creates “privacy by design”.
Under the CCPA, “personal information” includes many types of information, including:
- Identifiers: Name, alias, postal address, unique personal identifier, online identifier, Internet Protocol (IP) address, email address, account name, social security number, driver’s license number, passport number, or other similar identifiers
- Customer records information: Name, signature, social security number, physical characteristics or description, address, telephone number, passport number, driver’s license or state identification card number, insurance policy number, education, employment, employment history, bank account number, credit or debit card number, other financial information, medical information, health insurance information
- Characteristics of protected classifications under California or federal law: Race, religion, sexual orientation, gender identity, gender expression, age
- Commercial information: Records of personal property, products, or services purchased, obtained, or considered, or other purchasing or consuming histories or tendencies
- Biometric information: Hair color, eye color, fingerprints, height, retina scans, facial recognition, voice, and other biometric data
- Internet or other electronic network activity information: Browsing history, search history, and information regarding a consumer’s interaction with an Internet website, application, or advertisement
- Geolocation data
- Audio, electronic, visual, thermal, olfactory, or similar information
- Professional or employment-related information
- Education information: Information that is not “publicly available personally identifiable information” as defined in the California Family Educational Rights and Privacy Act (20 U.S.C. section 1232g, 34 C.F.R. Part 99)
- Inferences: Information that could be used to create a profile reflecting a consumer’s preferences, characters, psychological trends, predispositions, behaviors, attitudes, intelligence, abilities, and aptitudes
New York’s SHIELD Act

New York is another state that has recently amended its cybersecurity laws to provide greater consumer protection.
Passed in 2019, The Stop Hacks and Improve Electronic Data Security Act, otherwise known as the SHIELD Act, is a New York state law that provides New York state residents (consumers and employees) substantially greater privacy and data protection than before and requires businesses to “develop, implement, and maintain reasonable safeguards to protect the security, confidentiality and integrity of the private information.”
According to the bill, “private information” includes name, social security number, a driver’s license number, credit or debit card number, financial account number (with or without security code, as long as an authorized person could gain access to the account), biometric information, and username or email address with a password that permits access to an online account. The bill expands the definition of “breach of a security system” to include unauthorized access, rather than solely unauthorized acquisition of information.
The Arkansas Personal Information Protection Act
The Arkansas Personal Information Protection Act requires organizations that collect Personal Information (PI) to use reasonable security safeguards to protect such information. The law also requires that in the event such information is compromised, the organization must notify the affected individuals in a timely manner. If the breach of Personal Information (PI) affects more than 1,000 people, the organization must also disclose the breach to the state attorney general.
The law’s definition of “Personal Information” includes “An individual’s first name, or first initial and his or her last name, in combination with any one or more of the following data elements when either the name or the data element is not encrypted or redacted:
- Social Security number;
- Driver’s license number or state identification card number;
- Account number, credit card number or debit card number in combination with any required security code, access code, or password that would permit access to an individual’s financial account;
- Medical information, including any individually identifiable information, in electronic or physical form, regarding the individual’s medical history or medical treatment or diagnosis by a healthcare professional; or
- Added through an amendment in 2019: Biometric data, such as an individual’s voiceprint, handprint, fingerprint, DNA, retinal/iris scan, hand geometry, faceprint, or any other unique biological characteristic, if the characteristic is used by the owner or licensee to uniquely authenticate the individual’s identity when the individual accesses a system or an account.
The Arkansas law applies to “any person, business or state agency (collectively, Entity) that acquires, owns, or licenses computerized data that includes PI.” It covers any organization maintaining information on Arkansas residents, regardless of whether it operates within the state.
Illinois Biometric Privacy Information Act (BPIA)

A few states, including the state of Illinois, have passed laws that impose special restrictions on businesses that collect or otherwise obtain biometric information, including fingerprints, retina scans, and facial geometric scans. Most often, employers seek to collect this information through biometric time clocks to keep track of employees’ hours.
The BPIA covers all private sector employers with employees in the state of Illinois that want to collect biometric information. The law requires employers to:
- Develop and disclose their policies for usage and retention of biometric information. Such policy must inform the subject of the specific purpose and length of term for which a biometric identifier or biometric information is being collected, stored, and used.
- Request and receive written consent from individuals before obtaining their biometric data.
- Maintain safeguards to protect biometric information in an entity’s possession; ensure that protective measures for biometric information are the same or more protective than the manner in which the entity protects other confidential and sensitive information
Additionally, under the BPIA:
- A private entity in possession of biometric information must not disclose or disseminate a person’s biometric information unless:
- The subject of biometric information consents to the disclosure
- The disclosure completes a financial transaction requested or authorized by the subject of biometric information
- The disclosure is required by state or federal law or municipal ordinance
- The disclosure is required by law enforcement
- A private entity in possession of biometric information is prohibited from selling, leasing, trading, or otherwise profiting from a person’s biometric information.
The law allows private individuals to bring suit and recover damages for violations.
GDPR – The General Data Protection Regulation (GDPR)

The General Data Protection Regulation (GDPR) was enacted in 2018 to protect the privacy rights of citizens in the European Union (EU) when it comes to their Personal Data. It gives EU residents the right to know what data is being collected and sets requirements for businesses to protect the personal data and the privacy of EU citizens for transactions that occur within EU member states.
The GDPR defines Personal Data as “any information relating to an identified or identifiable natural person (“Data Subject”); an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person”.
Implication for employers: Take inventory of all personal data in your possession
At this point, regardless of what type of business you run or what industry you’re in, it is important to recognize that there is an increasing array of data that is now considered to be “personal data” under states’ laws — and this data must be handled with care and in compliance with the laws.
Further, you don’t even need a physical presence in these states to be subject to some of these data protection regulations. Some of these laws will apply to your business as long as you have employees residing in those states (e.g. New York’s SHIELD Act).
As such, it is essential for every organization to take inventory of the types of personal data in their possession and ensure there is a legal basis for processing every piece of personal data they’ve collected.
Equally important, each organization needs to develop, implement, and maintain reasonable safeguards to protect the security, confidentiality and integrity of this private information. These safeguards need to be operational at all times. And they must extend beyond your internal systems and processes to cover all third parties that process personal data on behalf of your company.
Learn more
To learn more about what your organization can do to readily meet common data privacy legislations, check out the article Understanding Data Privacy and Why It Needs to Be a Priority for Your Business.
Additionally, to help organizations strengthen their security posture and meet regulatory requirements, Hyperproof has published a suite of articles on cybersecurity controls, best practices, and standards. Here are a few of the most popular resources on our website:
- How to Conduct an Information Security Risk Assessment
- Internal Controls and Data Security: How to Develop Controls That Meet Your Needs
- A Guide to ISO 27001 Compliance
- SOC 2 Compliance: What You Need to Know and Need to Do
- 5 Things Businesses Can Do to Minimize Cyber Losses As Geopolitical Crises Like Iran Escalate
- How to Create a Cybersecurity Incident Response Plan
- What is ISO 27001 and the Benefits of Getting Certified
Hyperproof’s compliance operations software comes with pre-built frameworks to help you implement common cybersecurity and data privacy standards (e.g., GDPR, CCPA, SOC 2, ISO 27001) — so you can improve your data protection mechanisms and business processes to readily meet data privacy and data security regulations. Hyperproof not only provides guidance when you implement these compliance standards, but also automates many compliance activities to save you time when adhering to multiple regulations and industry standards.
If you’d like to learn more about how Hyperproof can help you prepare to meet the WPA as well as existing data privacy laws, please contact us for a personalized demo.
Ready to see
Hyperproof in action?









