What is Cyber Risk?

The discouraging numbers continue to grow as the latest high-profile breaches make headlines. Another corporate giant crumbles with the embarrassment of exposing countless names and emails of trusting customers. Ransomware is exploding, with experts predicting an attack every 11 seconds in 2021. 61% of all tech companies surveyed in the 2021 IT Compliance Benchmark Survey experienced a security breach or privacy violation in the last three years. Today, companies in every industry are asking themselves, “Will we be next?”
Today’s technology is undoubtedly making business processes faster, more mobile, and more efficient. Advancements like cloud migration, 3rd-party vendors, and mobile devices surely boost convenience. But they also increase cyber risk exposure.
So, what exactly is cyber risk, and how can your organization protect itself while continuing to innovate in the digital age? This article will explore cyber risk and how your organization can effectively manage it while continuing to enjoy the benefits of advancing technology.
Cyber risk
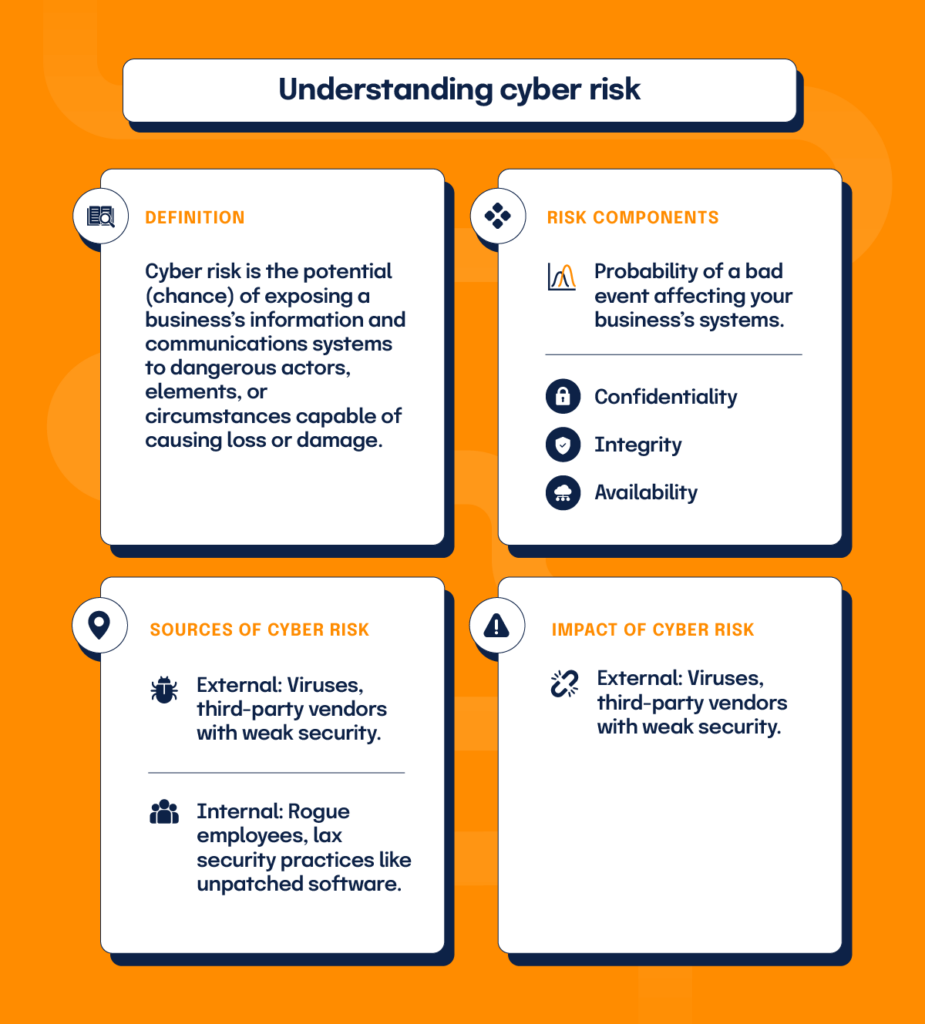
Cyber risk can be understood as the potential (chance) of exposing a business’s information and communications systems to dangerous actors, elements, or circumstances capable of causing loss or damage. Risk implies a degree of probability or the chance of an event occurring. Cyber risk is based on the probability of a bad event happening to your business’s information systems, leading to the loss of confidentiality, integrity, and availability of information.
Risks can originate anywhere–externally from viruses or third-party vendors with weak security posture or internally from rogue employee sabotage or the failure of lax security practices such as not regularly patching software.
What are the biggest cyber risks?
Today’s most prominent and worrisome risks are the threat of cyber attacks. Hackers work around the clock, assisted by automated bot armies seeking any vulnerability they can exploit. A minor weakness in an organization’s defense is all that’s necessary to allow a network invasion.
The majority of cyber-attacks are designed to access organizational data, which introduces a significant cyber risk today—data breaches. How would you feel knowing all your business’s sensitive information, including customers’ personal data, could be accessed by an invader with malicious intentions? Pretty unsettling, right?
Exposing sensitive customer data also puts enterprises at risk of violating data privacy and cybersecurity regulations.
Cyber risk examples
Data is most vulnerable during process or transport, which offers a prime opportunity for attack. The famous Capital One breach provides an example, as it resulted from problems with Capital One’s cloud migration plan.
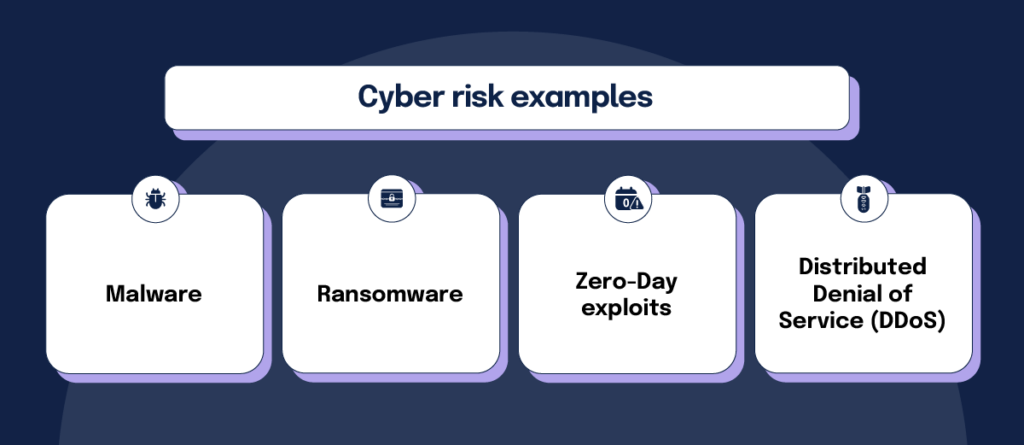
Cyber-attacks come in many forms and run the gamut of creativity. Malware, and its popular cousin ransomware, constantly search for systems to infect and control. Threat actors steal passwords and trick insiders with elaborate social engineering schemes to gain system access. Zero-Day Exploits are designed to attack software applications with hidden security flaws, while Distributed Denial of Service (DDoS) attacks overload systems, causing shut-downs.
When a cyber-attack is successful, all sorts of problems can result, including file deletion, theft of sensitive information for financial gain, or denial of network access.
Impact of cyber risk
Keep in mind that cyber risks can significantly impact your organization. All cyber risks come with a degree of likelihood and consequence, and enterprises need to be familiar with these risks’ potential tangible and intangible impacts.
Cyber risk’s tangible impacts are usually the simplest to spot and often result in financial setbacks to the enterprise. Many cyber risks create business disruption, slowing production and reducing revenue. More money can be lost in incident mitigation expenses, legal fees, and regulatory violation fines.
The intangible impacts of cyber risk can be challenging to quantify and often can only be noticed over time. When a business becomes the victim of a successful cyber-attack, customer trust is inevitably damaged. When customers lose faith, brands weaken, current and future business is lost, and valuable market share is forfeited.
Are you ready to conduct an information security risk assessment? Learn everything you need to know to be effective.
Conducting an Information Security Risk Assessment: a Primer ›

Managing risks is challenging

Why is managing cyber risk so critical today? Managing cyber risk presents a uniquely challenging problem with high stakes for today’s enterprises. Umesh Padval, long-time security industry enthusiast, investor, and current venture partner at Thomvest Ventures, explains, “Managing cyber risk is an asymmetric problem that looks like it will be with us for a long time. This problem isn’t going away–it’s only going to accelerate. For organizations to plug every hole and secure every device, it’s an almost impossible task, but threat actors need only one weakness across the enterprise for success.”
It hardly seems fair, right?
Managing cyber risk today is undeniably an uphill battle for organizations—one currently favoring threat actors. Current numbers shine some light here as 35% of organizations still manage risk with an ad-hoc approach. Furthermore, only 21% of survey respondents claim to manage risk with an integrated approach using automated processes to level the playing field. Managing cyber risk today is a team sport requiring cooperation and input from all departments. It requires organizations to be rigorous in the four-step risk management process, including identification, assessment, response (prioritization and mitigation), and risk monitoring.
How to perform a cybersecurity risk assessment
Like all successful journeys, cyber risk management originates with an understanding of your current position. For today’s enterprises, this begins by creating a profile of risk through risk assessment. All internal and external risks must be identified, and the likelihood and potential impact need to be discussed with shareholders. Organizations should deploy a risk register to track their risks systemically and improve their understanding of existing threats and mitigation measures.
Featured Resource: Why You Need to Have a Risk Register and What to Track In It
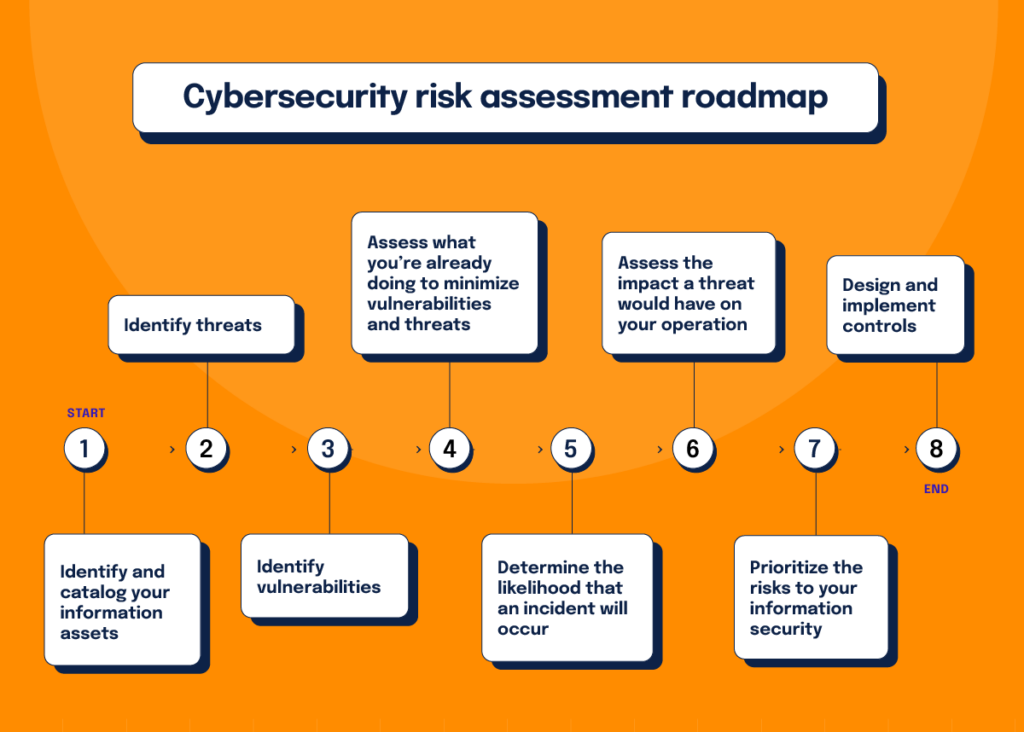
How should you conduct a risk assessment? Below are the recommended steps based on current best practices.
Identify and catalog your information assets
Before determining what safeguards measures to implement, you need to know what information needs to be protected and where the information resides. To answer that question, you’ll want to categorize your information (known as data classification) based on their sensitivity level (as dictated by legal requirements you may be subject to) as well as their strategic importance to your organization. You’ll also need to know what systems are processing sensitive information, how those systems are being used, and how data is flowing between various systems within your network.
Identify threats
As we mentioned before, threats to your business’s information come in many forms, and you’ll need to take into account many types of different threats when compiling a list of threats to which your business is most susceptible.
Identify vulnerabilities
A vulnerability is a weakness in your system or processes that might lead to an information security breach. You can find vulnerabilities through audits, penetration testing, security analyses, automated vulnerability scanning tools, or the NIST vulnerability database.
Assess what you’re already doing to minimize vulnerabilities and threats
Your organization may already have some policies, procedures, or technical components in place to combat threats and to prevent the loss of valuable data. By keeping track of what you’ve already done, you can determine what additional measures you will need to take to reduce threat levels even further.
Determine the likelihood that an incident will occur
Using all the information you have gathered — your assets, the threats those assets face, and the controls you have in place to address those threats — you can now categorize how likely each of the vulnerabilities you found might be exploited. Many organizations use the categories of high, medium, and low to indicate how likely a risk is to occur.
Assess the impact a threat would have on your operations
At this point, you’ll conduct a business impact analysis for each vulnerability and threat you have identified to see how disruptive it would be if the incident actually occurred. Your impact analysis should consider three questions:
- For what is the system used? What are business stakeholders able to accomplish within the system?
- How critical is this system to your organization’s mission and operations, given how it’s used?
- What’s the level of sensitivity of data within this system?
Depending on the three factors above, you can assess whether a threat would have a high, medium, or low impact on your organization. Taken together with how likely a threat event is to occur, this impact analysis will help you prioritize risks in the next step.
Prioritize the risks to your information security
Given that your organization has business objectives, security objectives, and a finite set of resources, you’ll need to work with organizational leaders to determine which risks warrant immediate treatment, which risks you can deprioritize, and which ones you are willing to accept as the cost of doing business.
Depending on the size and maturity of your business, you can either keep this exercise relatively simple by using a 2 by 2 risk matrix (with “likelihood” and “impact” being the two axes) or deploy a more advanced, risk-quantification framework such as the FAIR Model or the NIST Risk Management Framework.
Design and implement controls
Once you’ve established priorities for all risks you’ve found and detailed, then you can begin to make a plan for mitigating the most pressing threats. To determine what controls you need to develop to reduce or eliminate the risks effectively, you should involve the people who will be responsible for executing those controls. Senior management and IT security teams need to be in the room to check that the proposed controls will address risks and align with your organization’s overall risk treatment plan and business goals.
Fortunately, there’s no need to start from scratch in this realm. Organizations like NIST, ISO, and the Payment Card Industry Security Standards Council have published detailed documents containing control requirements for information security and guidance on how to implement the controls. If you’re just getting started, you may use the NIST Cybersecurity Framework, NIST SP 800-53 Rev 5, or ISO 27001 Annex A as a point of reference to establish a baseline control set for your information security program. For further guidance on how to design effective controls to mitigate risks, check out this article, The Four Signs of an Effective Compliance Program
Other keys for managing cyber risk
Cyber risk management must be treated as a strategic business function with proper resource allocation. To construct and maintain a unified, coordinated, and disciplined management solution, organizations must operate from a solid governance and accountability base. Strong governance is a must for success, starting with the precise identification and definition of all roles and responsibilities.
Leadership must oversee the alignment of risk management with other initiatives such as compliance. Security controls should be mapped back to risks and compliance requirements, so security teams can see gaps in their environment and develop a plan of action to improve their security and compliance posture.
Managing cyber risk is a dynamic and continual process, requiring an agile and doggedly persistent “bend but don’t break” mindset. Tech environments and security risks can change rapidly, so controls set up to mitigate risk need regular review and ongoing monitoring. Dashboards showing key risk indicators can help keep all team members current on real-time risk status.
Helpful risk management resources

The slope is steep for risk management teams, but there’s help available.
Structuring security and compliance programs
Using an organized approach such as the Compliance Operations methodology can help your organization improve its cyber risk management initiatives. This approach emphasizes the importance of taking a risk-based approach to security and compliance. It also discusses the importance of making consistent, incremental improvements over long planning cycles and perfect execution. Finally, it provides guidance on fostering shared responsibility for security (between the security/compliance teams and business stakeholders), standardizing compliance processes, and automating manual tasks.
Many organizations look to the support structure of security frameworks to help manage risk. Risk management frameworks provide a solid, structured base for any organization to build an effective security assurance program. These frameworks remove confusion by highlighting the business/technological domains and processes businesses need to think through when developing security and data protection controls. These frameworks also help security and compliance teams perform a swifter and more precise gap analysis between compliance requirements and current operations.
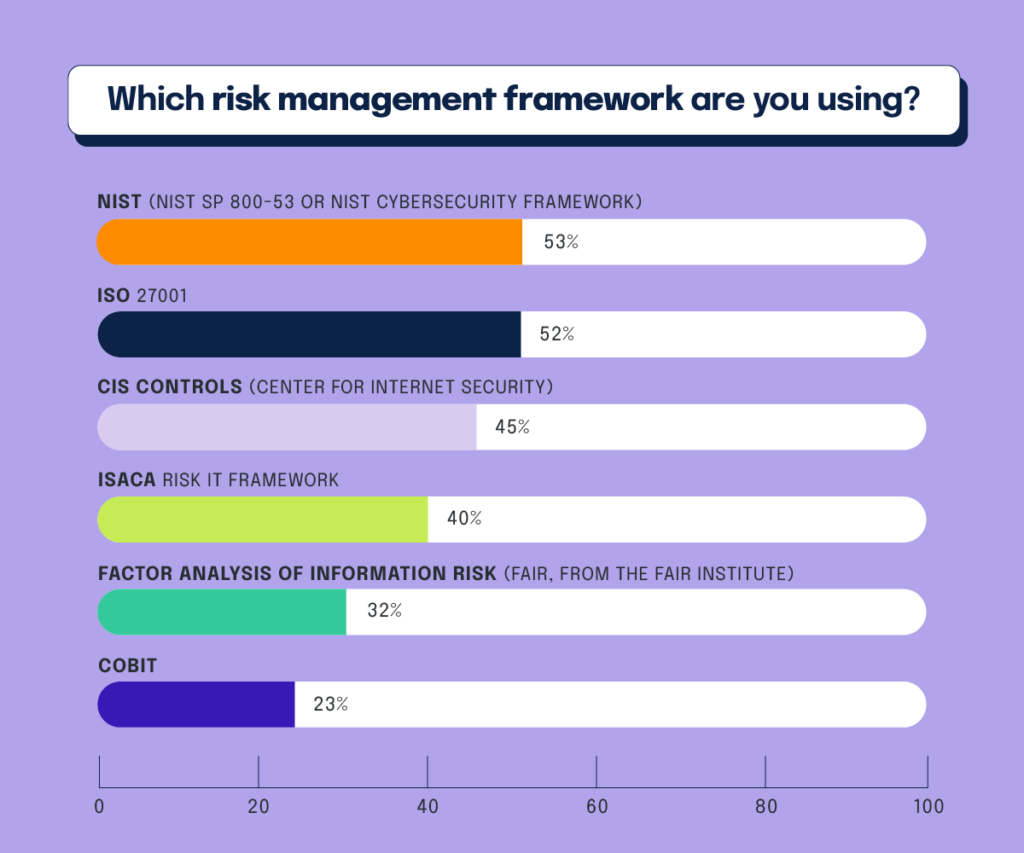
According to the 2021 IT Compliance Benchmark Survey, 93% of respondents claim their organization uses an IT risk management framework to help manage cyber risk. NIST SP 800-53 is the most popular with survey respondents, as 53% claim to favor this framework. ISO 27001 enjoys similar high status, with 52% of respondents selecting this framework as their preferred risk management guideline. CIS Controls, ISACA Risk IT, and FAIR (Factor Analysis of Information Risk) are frameworks also worthy of mention. FAIR is unique because all risk is defined in business-friendly financial terms.
Use software to streamline day-to-day risk management and compliance activities
Another way to add rigor to your risk management program is to use software tools such as Hyperproof’s compliance operations platform to stay on top of all of your risk management and compliance activities. This modern software platform can help you track all enterprise risks and streamline how internal controls are managed and compliance artifacts are gathered. Hyperproof’s solution software drives a highly effective compliance operations function with an organized, consistent, and disciplined approach featuring:
- Record keeping based on a single source of truth housing all risk and compliance requirements, activities, and evidence
- Planning of all work needed to meet security compliance requirements with timelines
- Workflow optimization is driven by automation that cuts time spent on manual tasks by up to 70%
- Monitoring and reporting with real-time analytics to keep all team members current on the state of compliance effort
- Scaling up of security and compliance programs to handle the increased volume of multiple audits
Cyber risk – closing thoughts
Cyber risk is undoubtedly here to stay, and how businesses manage it goes a long way toward determining their future success. An innovative, forward-thinking approach will prove critical as security teams strive to shrink the current advantage gap enjoyed by malicious actors. It’s time for organizations to approach cyber risk and security with a continuous improvement mindset and deploy purpose-built compliance technology to streamline day-to-day tasks.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?