Automatically Test and Monitor Controls with Hyperproof
Hyperproof enables you to mitigate critical risks, save valuable time, and gain better visibility into your risk environment by automatically testing and monitoring internal controls.
Trusted By





Make Risk Management a Competitive Advantage with Continuous Controls Monitoring
Connect risks to your controls in Hyperproof and then set up Continuous Controls Monitoring (CCM) to validate the effectiveness of those controls. CCM can also help your organization maintain a solid cyber defense posture, ensure business continuity, quality and regulatory compliance.
Key benefits include:
Reduce Time Spent on Manual Testing
Increase control testing coverage and the productivity level of compliance/internal audit teams.
Increase Accountability & Awareness
Hold employees that are operating key processes responsible for managing associated risks.
Gain Visibility Into Risk Environment
Provide company executives a greater level of assurance that highly-rated risk factors are appropriately managed.
Setting Up Continuous Controls Monitoring In Hyperproof Is Easy
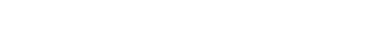
1. Identify existing controls
Before you can set up a test, you need to identify the existing controls in your organization and bring them into Hyperproof. You can quickly import controls from a spreadsheet into Hyperproof and organize them by traits such as control criticality, control domain, control owner, and more.

As someone who has to manage multiple work streams across both the compliance and security functions, I view technology as critical in helping me reduce routine work and make time to focus on the more strategic items. By setting up automated control tests in Hyperproof, I can worry less about those controls, focusing my time on managing critical controls.
Tony Dell’Ario
Senior Compliance Manager // Highspot
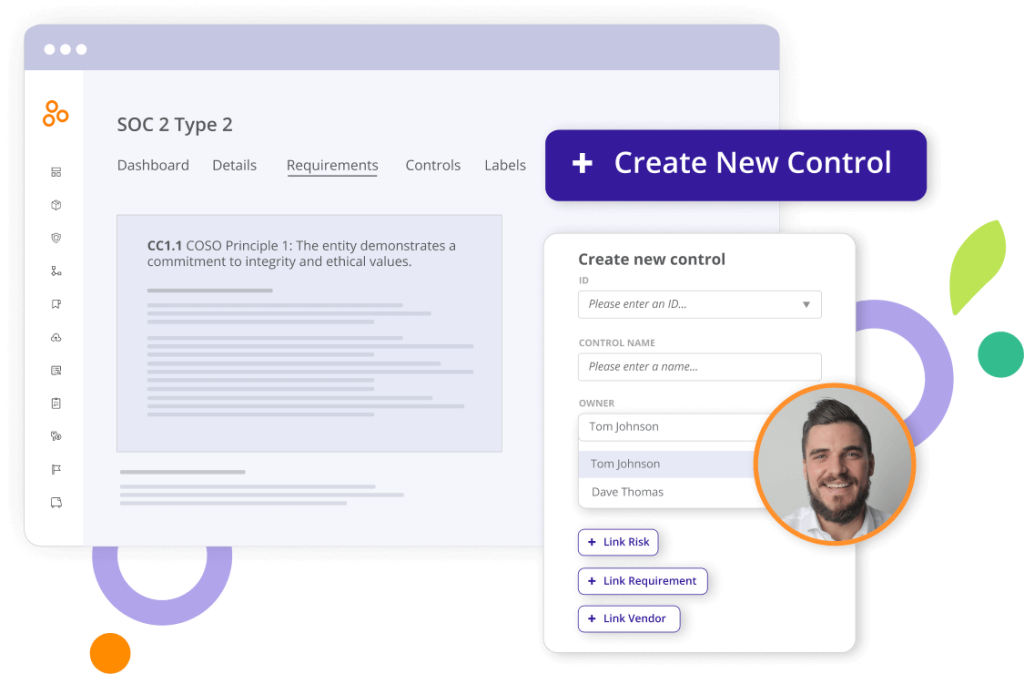
2. Select controls to automatically test and monitor
Good candidates for automated control testing and monitoring are control processes that occur at high frequency (continuously, daily, weekly, monthly, etc.) and those that generate well-structured data for testing (rows and columns of data suitable for Excel formulas).
3. Set up a test for each control
Set up a test for each control or a group of related controls at once. Hyperproof’s flexible test builder allows you to write many types of tests – it’s similar to popular Excel functions you may already know (VLOOKUP(), HLOOKUP(), or an IF() ).
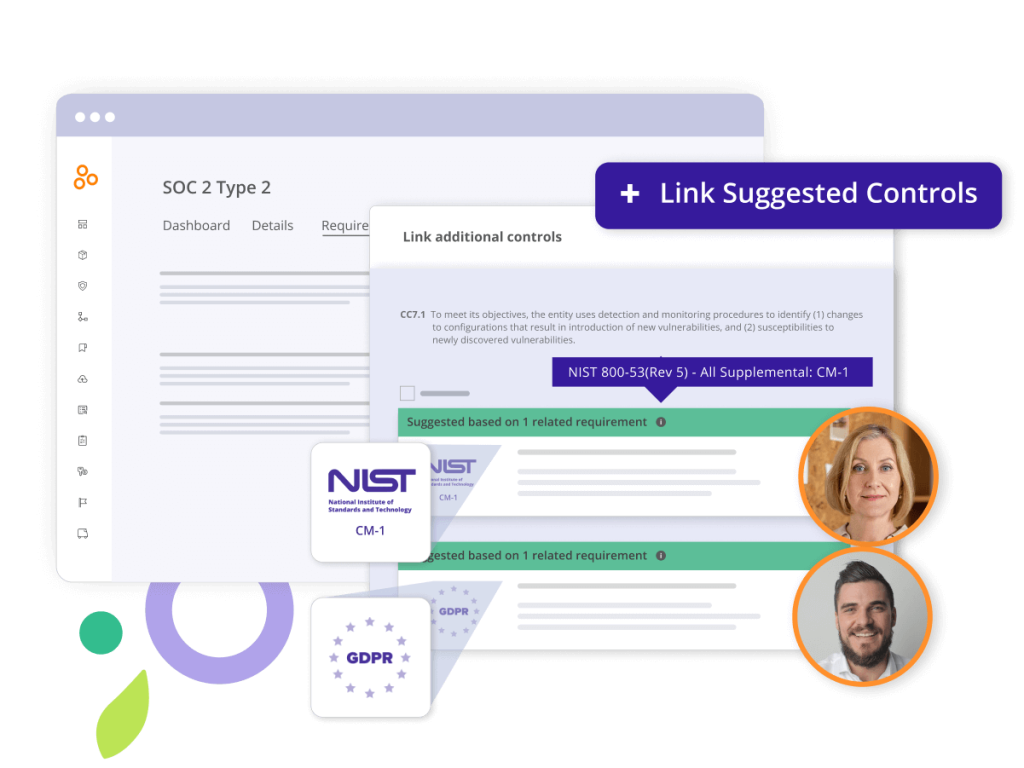
4. Determine what should happen if a test fails
Once you write a test, determine what type of response is appropriate when a test fails or the result is unexpected. For instance, you may choose to set up an automatic notification and send it to the control operator when the control test fails.
5. Build reports for easy monitoring of automated controls
Hyperproof makes it easy to build custom reports that track relevant data and processes. As a best practice, we recommend you create a report of all automated controls after initial setup to ensure these tests and test-driven notifications are working as intended.
Security Controls that Benefit from Continuous Monitoring
Related Resources:
Ready to see
Hyperproof in action?









