Guide
Practical Checklist for Streamlining Evidence Collection

Introduction
Businesses today reach more potential customers, rely on more vendors and suppliers, and collect huge troves of data – which has given rise to a seemingly endless parade of regulations around data privacy, process integrity, and security. Each of those regulations brings its own demand for assurance that your business meets its compliance obligations; each regulation then requires the collection of evidence. This evidence collection checklist helps you streamline the evidence management process.
If you’re spending too much time on collecting evidence for audits, you’re not alone. According to Hyperproof’s 2021 IT Compliance Benchmark Survey, 1 in 2 compliance professionals said they spend at least 50% of their time on manual, repetitive work – much of it revolving around generating and preserving evidence of their organization’s security and data protection controls.
Common evidence collection challenges among businesses
Many organizations today do their best to manage evidence manually, with ad-hoc tools (e.g., spreadsheets, G-Drive, SharePoint, email, etc.) that aren’t built for security assurance and compliance projects. This leads to a host of evidence management challenges, such as:
1. Evidence isn’t collected on a regular frequency because without reminders, people forget to do the work.
2. Evidence is poorly labeled and/or it’s not linked with specific compliance requirements.
3. Evidence is stored hazardously in disparate systems (e.g., hard-drive, G-Drive, SharePoint, email threads) making them difficult to retrieve and reuse.
4. Controls – organizational procedures and processes – aren’t set up in a way that generates appropriate, sufficient, and time-stamped evidence.
5. Business unit teams don’t understand what controls they’re providing assurance for and how to generate sufficient and appropriate evidence.
What can go wrong when evidence collection challenges aren’t addressed
Business unit teams
Lost productivity and audit fatigue
When business unit teams are pulled out of their day jobs to respond to requests for evidence multiple times a year, they experience “audit fatigue” and become increasingly frustrated with the demands from the compliance team. People start to ignore the requests or provide quick but inaccurate responses simply to get the compliance team “off their backs”.
Compliance professionals
Lost productivity and declining job satisfaction
When compliance teams cannot easily retrieve and re-use evidence to satisfy multiple security/data privacy assessments, they end up starting from scratch in tracking down the evidence each time they prepare for an assessment. They’re left with little time for higher-level, strategic work.
The organization
Inconsistent information security and data privacy management and evidence collection practices across teams and business units
Without a single source of truth for evidence and information about controls, different product teams and business units cannot easily find relevant security policies and procedures other teams and business units have developed and apply it to their one teams and products. As a result, data protection and infosec efforts – and evidence of those efforts – are inconsistent between teams and business units. These inconsistencies will likely be noticed by external auditors, raise questions from auditors and possibly jeopardize audit results.
Elevated legal risk
When a compliance team doesn’t have a tool that allows them to easily “show their work” (i.e., map evidence of particular controls to requirements in data privacy regulations), it puts their organization at higher risk for violating data privacy laws that require organizations to conduct due diligence to back up the compliance representations they make.
Incomplete risk data on vendors and suppliers
When a security team assesses their vendors’ risk profile by manually sending questionnaires to their vendors and suppliers, the questionnaires might get lost, overlooked, or never retained. The security team might receive erroneous data or data in multiple formats that need an integration process to consolidate it into something meaningful.
Tips for a streamlined evidence management process
By shifting away from manual processes to compliance operations software, you can create a highly efficient and consistent evidence management process and gain the ability to reuse evidence for multiple assessments/to satisfy multiple assurance frameworks’ requirements. Regardless of the specific solution you choose, it should have several important capabilities.
1. Ability to manage multiple assurance frameworks and crosswalk controls
Controls include policies, activities, processes, procedures, and technical solutions your business has committed to putting in place in order to meet compliance requirements and mitigate risks.
The tool should be able to manage multiple assurance frameworks and specifically empower control mapping (also called crosswalks) so you can see where two or more frameworks have overlapping requirements. This allows you to tailor your evidence request so one answer can satisfy several frameworks’ demands, so you don’t overwhelm control owners in the business operating units.
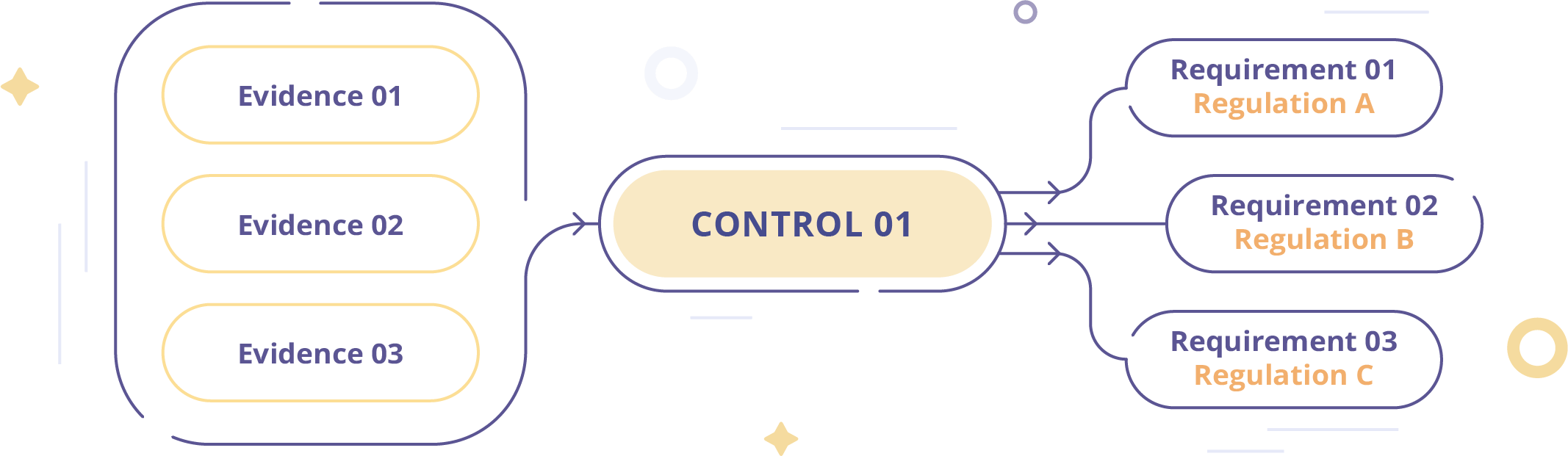
Common evidence requested across multiple data protection compliance frameworks:
2. Ability to assign owners and set review cadences for controls and evidence
You want a tool that allows you to designate individuals or teams as responsible for operating controls and collecting evidence. The ideal tool will allow you to set review cadences on controls and different types of evidence (e.g., weekly, monthly, quarterly, annually) and specify due dates so you don’t have to remind people to submit fresh evidence manually.
3. Automated alerting and escalation for any remediation work that hasn’t been completed
Having a tool that automatically alerts you when any evidence collection or remediation work hasn’t been completed can save a lot of time and ensure that your evidence stays current (and is acceptable to your auditor). For example, you might task a business unit leader with implementing a new policy or restructuring an approval process to make the controls more effective. You want a system that can send automated reminders to that unit leader about the work that they need to do or, if the work isn’t done by deadline, to escalate that alert to you and the person’s supervisor.
4. Automated evidence collection
Evidence comes in different formats. Some evidence that you’ll be asked to provide includes snapshots capturing what’s happening within a particular system or process at a particular time. This type of evidence needs to be “fresh” or collected on a regular basis (e.g., daily, weekly, monthly) for it to be considered valid by an auditor.
Evidence that needs to be fresh may include:
This information may come from cloud-based services such as AWS, Azure, GitHub, Google Cloud, or other established providers.
If your compliance management solution can automate the collection of such evidence, it goes a long way in reducing assessment fatigue. Any automatically-collected evidence should come with metadata attached so you have visibility into exactly where the evidence came from and when it was collected. Including that metadata in your evidence is crucial to demonstrating to your auditors that the evidence you’re giving them is trustworthy.
5. Ability to categorize and tag evidence for easy retrieval
You want to be able to organize your evidence (e.g., within folders or categories) so you can easily find and retrieve relevant information and quickly answer questions you’re likely to get from your customers, auditors, regulatory examiners, or other stakeholders.
6. Secure storage of evidence and the ability to customize roles and permissions
Make sure that your compliance software has adequate security controls in place to keep your sensitive
corporate/employee data safe. For instance, does it provide the ability for a compliance professional to restrict access by role? Can you configure the software so that control operators from Engineering can’t see proof that control operators from HR submitted? Can you ensure that your external auditor can only see documents you’ve directly made available to them and nothing else?
Download the PDF









