A Step-by-Step Guide to Getting a SOC 2® Report

Ensuring the security of your customers’ and partners’ data is paramount in today’s digital environment. That’s why Service Organization Control 2 (SOC 2®) compliance has emerged as a widely recognized cybersecurity audit framework. SOC 2® reporting has been adopted by more businesses to demonstrate their commitment to strong cybersecurity practices. Let’s explore what a SOC 2® report can look like. We’ll also find out how to get a SOC 2® report and how SOC 2® automation tools can streamline the reporting process.
Why do I need a SOC 2® report?
Getting SOC 2® certified enhances your company’s credibility and trustworthiness. SOC 2® compliance also positions you competitively in the market to fast track deal making and attract new customers. If your company provides services involving storing, processing, or transmitting customer data, you may require a SOC 2® report.
Typically, your clients or prospects will request a SOC 2® report, especially in industries such as finance, healthcare, or technology, where data security and privacy are critical. Customers in these sectors may require SOC 2® reports as part of their compliance efforts to ensure that their vendors meet industry standards and regulations.
Companies may also require SOC 2® reports when they want to outsource critical services, like cloud storage, to another organization. In this case, a SOC 2® report provides assurance that you (the vendor) have effective controls in place to protect company data.
SOC 2® reports are designed to provide assurance about the effectiveness of a service provider’s controls in five categories: security, availability, processing integrity, confidentiality, and privacy. Depending on the current state of your security and compliance program, preparing to pass a SOC 2® audit can take anywhere between a few months to more than a year.
Where can I find a SOC 2® report example?
While you can easily find a SOC 2® report example online, you might find the report hard to decipher if you don’t understand its basic components first. Any sample SOC 2® report will likely contain the following sections:

- Section 1: Assertion of the management
- Section 2: Independent service auditor’s report
- Section 3: Description of your system
- Section 4: Applicable trust service categories, criteria, related controls, tests of controls and results of tests
- Section 5: Organization information not covered by service auditor’s report
We will go through all these sections in detail below.
For reference, here is an example of the beginning of a SOC 2® report:
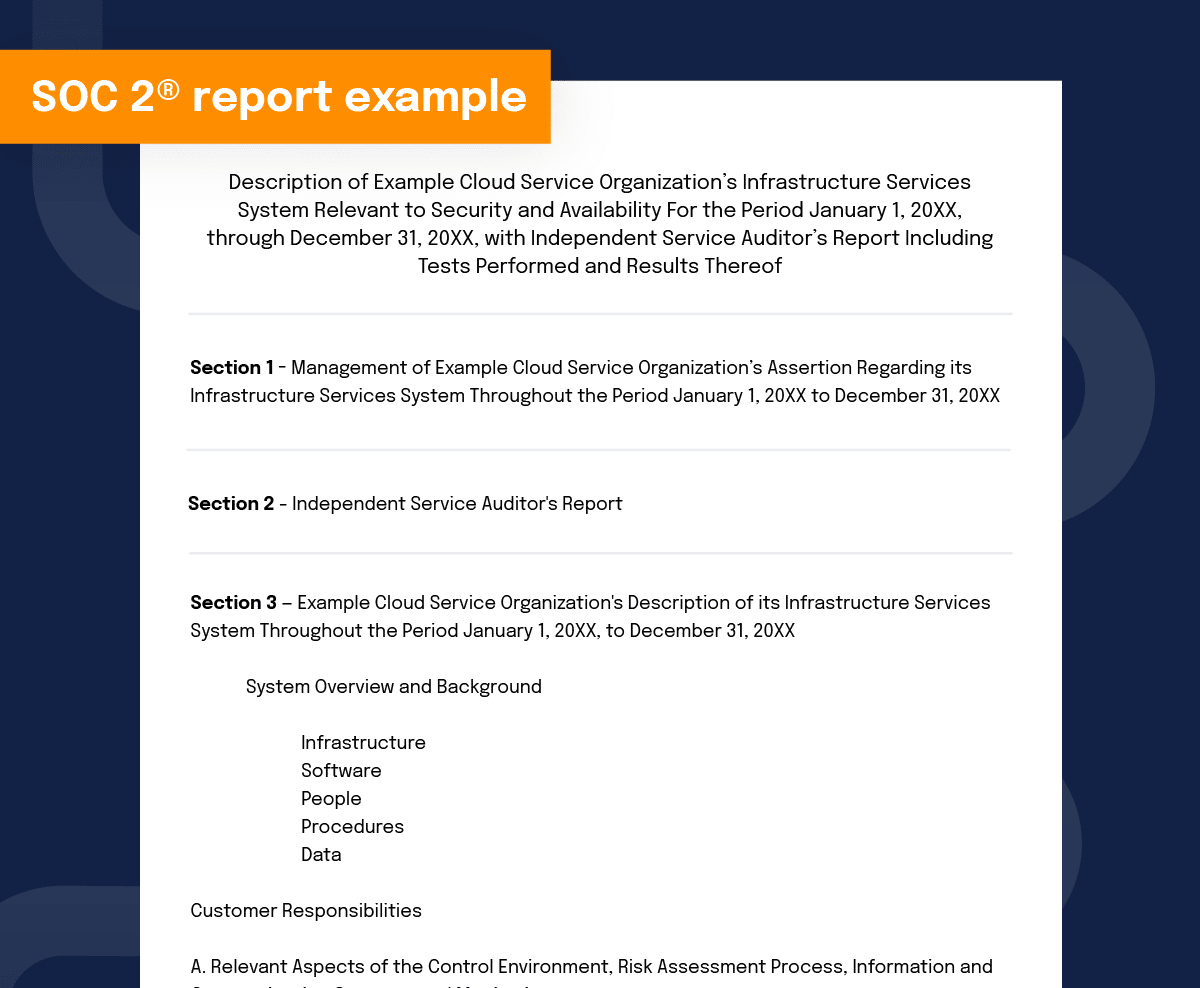
Now let’s examine what’s contained within each section of a SOC 2® report.
SOC 2® Section 1: Assertion of the management
As the service organization, your company is tasked with producing Section 1. It’s a formal statement regarding your company’s responsibilities and the effectiveness of its controls. Section 1 briefly describes your product, services, structure, and it summarizes your IT systems, teams, and controls.
SOC 2® Section 2: Independent service auditor’s report
This section is written by an independent auditor to state their opinion about the effectiveness of your organization’s controls based on the criteria specified in the report. Essentially, Section 2 states whether you passed or failed the audit. This section of the SOC 2® report can include information like:
1. Opinion statement
This is probably what you’ll want to read first. It’s the auditor’s professional opinion on whether your organization’s controls are suitably designed and operating effectively to achieve the control objectives specified in the report. This opinion is based on the auditor’s assessment and testing of the controls.
2. Scope of audit
Audit scope includes the services, systems, and controls evaluated, as well as the period covered by the assessment (see section below, SOC 2® Type 1 vs Type 2).
3. Audit methodology
This may include details about the procedures, tests, and techniques employed during the audit process.
4. Criteria for evaluation
The evaluation criteria can include industry standards, regulatory requirements, contractual obligations, or the Trust Services Criteria (TSC) related to security, availability, processing integrity, confidentiality, and privacy.
5. Independence and objectivity
The auditor affirms their independence and objectivity in conducting the audit, emphasizing their impartiality and adherence to professional standards and ethics.
Basis for opinion
The auditor states their assessment of the design and operating effectiveness of the controls, the evidence obtained during the audit, and any limitations or constraints encountered.
Qualifications or exceptions
If applicable, the auditor may disclose any qualifications, exceptions, or areas of concern identified during the audit. This could include control deficiencies, non-compliance with criteria, or other issues that may impact the overall opinion.
Assurance level
Finally, the auditor’s report provides assurance to stakeholders regarding the reliability of the service organization’s controls and the accuracy of the information presented in the SOC 2® report.
SOC 2® Section 3: Organization’s descriptions of its systems
This section is usually the longest part of the report. Section 3 provides stakeholders with a comprehensive understanding of the service organization’s system, processes, controls, and risk management practices.
Information in this section lays the groundwork for assessing the effectiveness of the controls in subsequent sections of the report. Section 3 may include information about your:
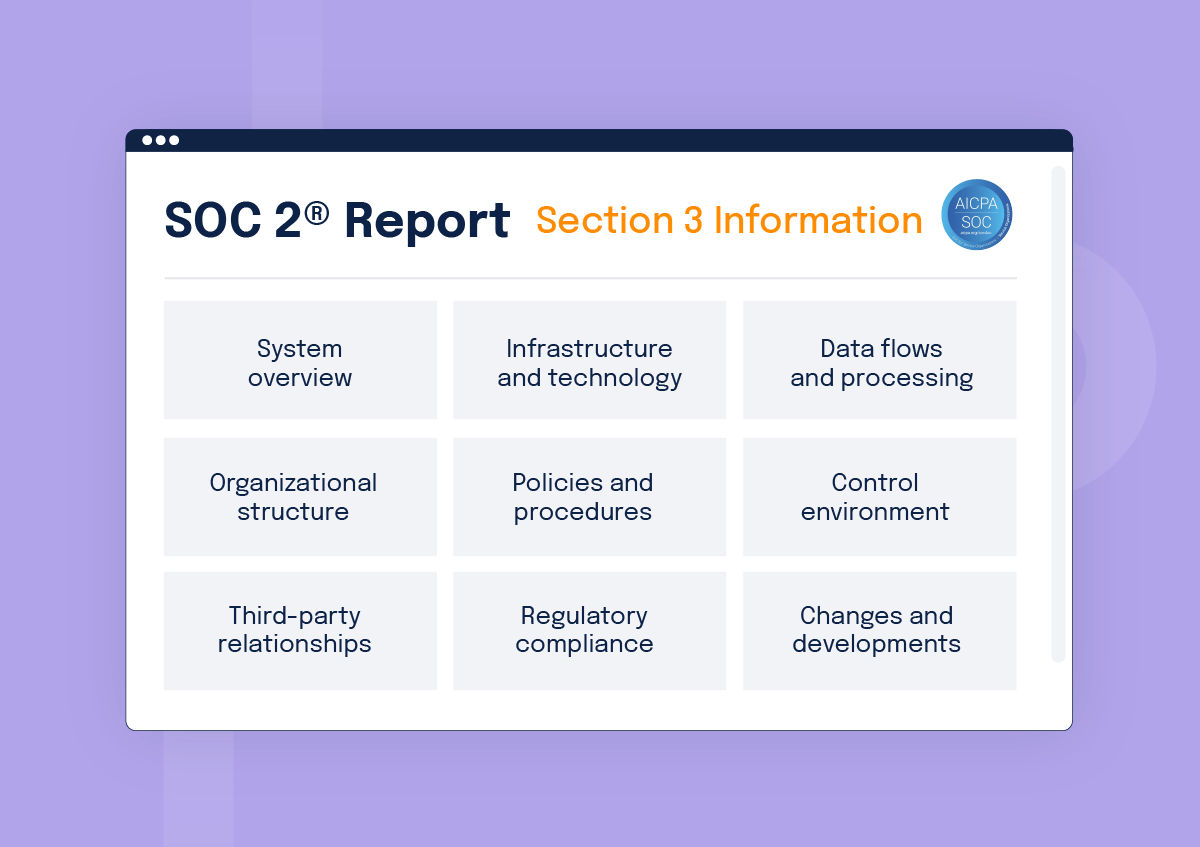
- System overview
- Infrastructure and technology
- Data flows and processing
- Organizational structure
- Policies and procedures
- Control environment
- Third-party relationships
- Regulatory compliance
- Changes and developments
SOC 2® Section 4: Applicable trust service categories, criteria, related controls, tests of controls, and results of tests
Section 4 encompasses several critical elements related to the Trust Services Criteria (TSC). Overall, SOC 2® Section 4 provides a detailed assessment of how well your organization’s controls align with the TSC. This section also provides information about the outcomes of controls testing. Section 4 is crucial for stakeholders to assess the security, compliance, and reliability of your service organization’s operations.
SOC 2® Section 5: Organization information not covered by service auditor’s report
This section of the SOC 2® report provides additional context and details about your organization that are not directly assessed by the service auditor. Section 5 complements the audit findings by providing a broader view of the service organization, its business context, and risk management practices. Other content included in this section may talk about your company’s operational resilience, compliance, and trustworthiness. The information found in Section 5 can include:
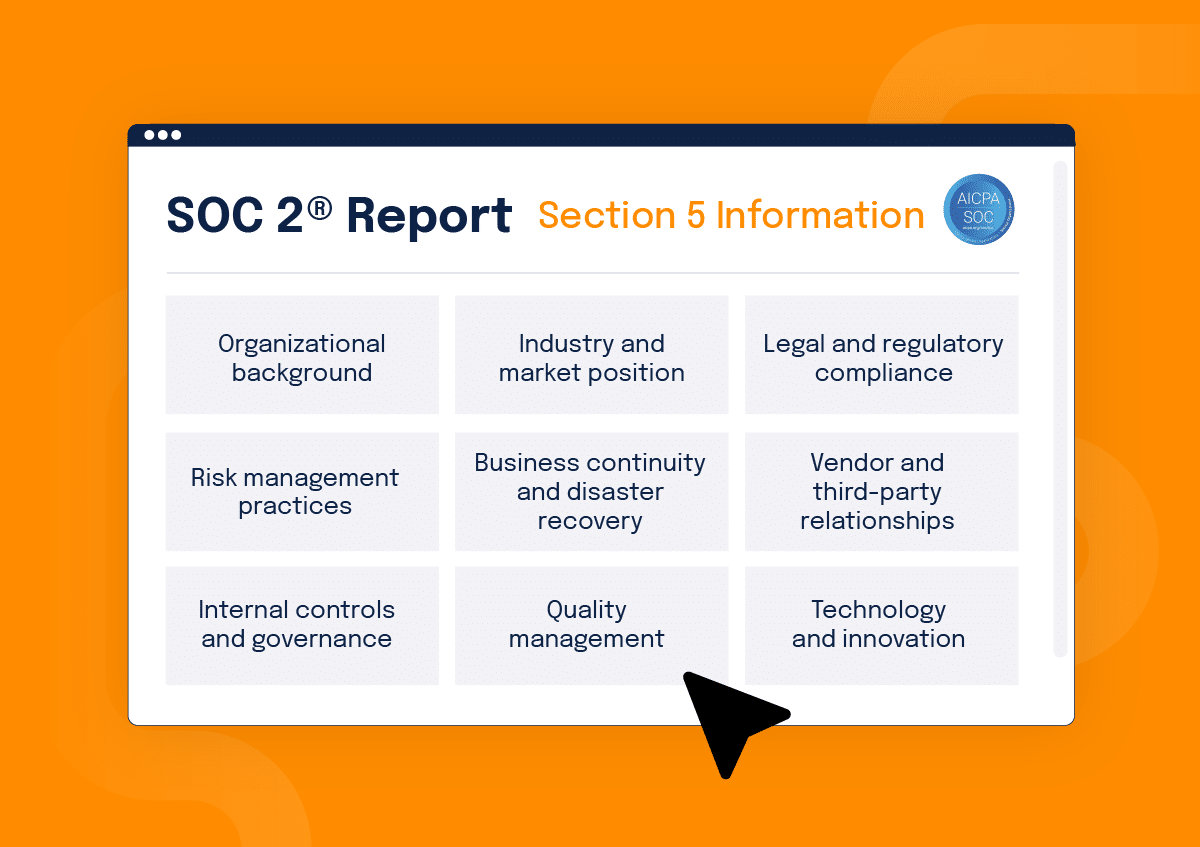
- Organizational background
- Industry and market position
- Legal and regulatory compliance
- Risk management practices
- Business continuity and disaster recovery
- Vendor and third-party relationships
- Internal controls and governance
- Quality management
- Technology and innovation
How do you get a SOC 2® report?
Getting a SOC 2® report typically involves a detailed process that requires close coordination between the service organization seeking the report and an independent auditor. The American Institute of Certified Public Accountants (AICPA) is the governing body of the SOC framework and establishes the U.S. auditing standards that auditors use for SOC 2® examinations.
Here are the steps you need to follow to get a SOC 2® report:
1. Determine the scope
First you’ll need to define the scope of the SOC 2® audit, including your services, systems, and controls that will be assessed. Identify the relevant Trust Services Criteria (TSC) applicable to your business (e.g., security, availability, processing integrity, confidentiality, privacy).
2. Select an auditor
Choose an independent CPA (Certified Public Accountant) or audit firm experienced in conducting SOC 2® examinations. The auditor should be familiar with the Trust Services Criteria and relevant industry standards.
3. Pre-assessment preparation
Work with the auditor to prepare for the assessment. This may include documenting your control environment, policies, procedures, risk assessments, incident response plans, and other relevant documentation.
4. Onsite assessment (SOC 2® Type 1 vs. Type 2)
You’ll need to choose what type of SOC 2® report you need:
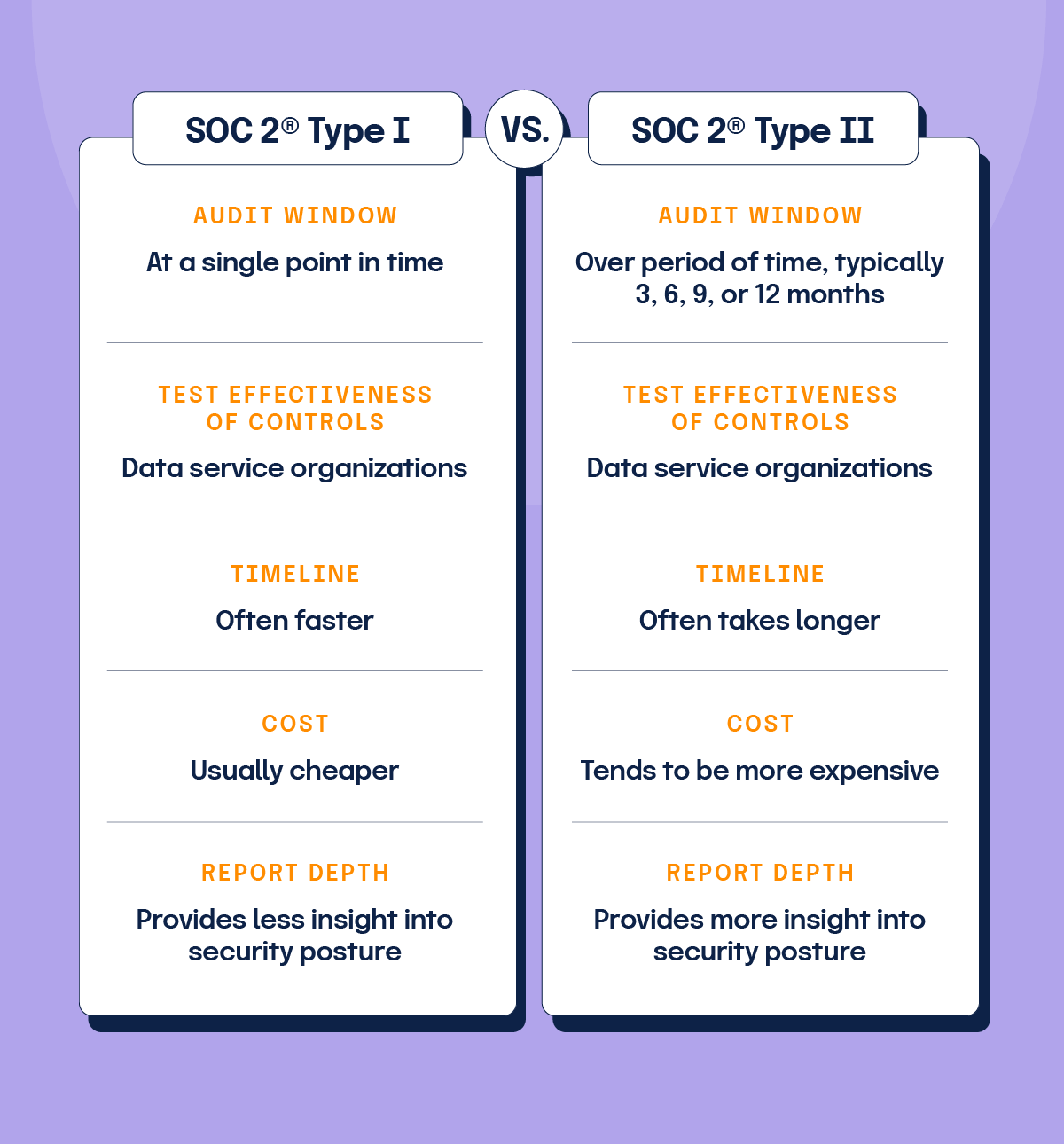
SOC 2® Type 1
This assessment evaluates the design effectiveness of your controls at a specific point in time. The auditor reviews your control environment and provides an opinion on whether the controls are suitably designed to meet the TSC.
SOC 2® Type 2
This assessment extends the evaluation over a period of time (e.g., six months to a year). a SOC 2® Type 2 report is more rigorous than a Type 1 because, in addition to evaluating the design and implementation of control processes, it also assesses that the controls were consistently performed over time. SOC 2® type 2 reporting provides customers and business partners with a greater level of confidence in the effectiveness of your control processes.
5. Auditor’s testing
Next, the auditor conducts various testing procedures to assess the effectiveness of your controls. This may include interviews, observations, document reviews, system demonstrations, and testing of controls in action.
6. Report preparation
After completing the assessment and testing, the auditor prepares the SOC 2® report. The report includes sections mentioned like the introduction, management’s assertion, auditor’s opinion, description of system, control objectives, control activities, tests of controls, results of tests, and conclusion.
7. Review and distribution
Thoroughly review your SOC 2® report for accuracy and completeness. Once finalized, distribute the report to stakeholders, such as customers, regulatory agencies, and business partners, as requested.
8. Continuous compliance
Maintain and enhance your control environment to address any identified deficiencies or areas for improvement. Consider periodic SOC 2® assessments (e.g., annually) to demonstrate ongoing compliance and assurance to stakeholders.
It’s crucial to work closely with your chosen auditor throughout the SOC 2® reporting process. That way you ensure a thorough assessment of your controls and the preparation of a comprehensive report that meets your stakeholders’ needs. Also, it’s important to stay up to date with any revisions to the SOC 2® framework. Then you won’t have to face any surprises that could delay your report completion.
When is SOC 2® compliance required?
Currently, SOC 2® reporting isn’t legally required. However, many B2B and SaaS businesses seek SOC 2® certification because it’s often a requirement in vendor contracts. Since it’s so widely adopted and acknowledged, many procurement and security departments require a vendor to produce a SOC 2® report before they approve any software purchase.
If your business handles any kind of customer data, a SOC 2® report shows customers and users that your data security and protection meet the highest standards. Healthcare, retail, financial services, SaaS, and cloud storage and computing companies can all benefit from SOC 2® compliance certification.
Furthermore, SOC 2® requirements often overlap with other frameworks, including:
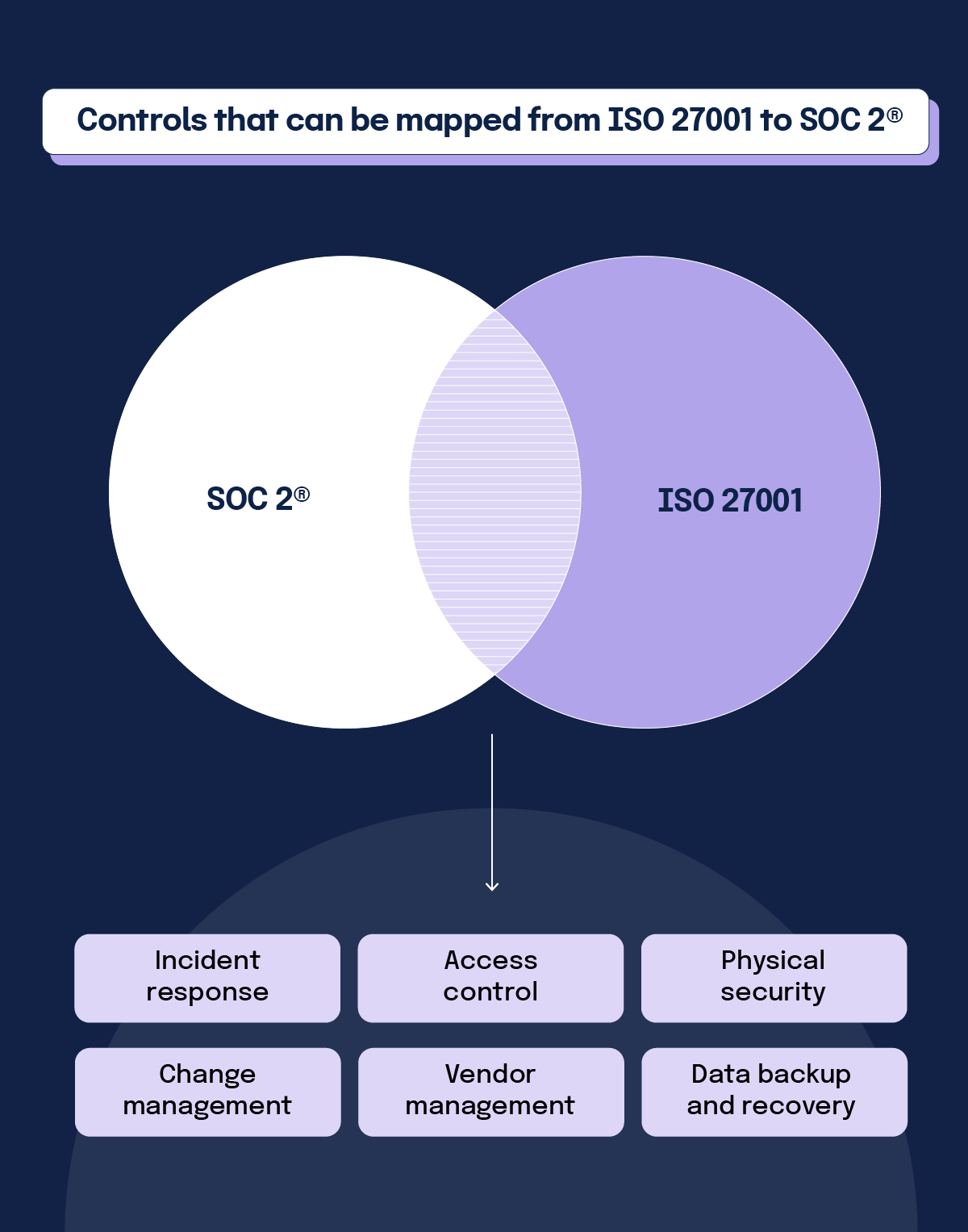
ISO 27001
According to the AICPA, SOC 2® and ISO 27001 criteria overlap by about 80% and share almost all the same controls. Companies can streamline compliance by fulfilling criteria for both standards simultaneously, which is known as common criteria mapping.
HIPAA
SOC 2® requirements often overlap with HIPAA.
PCI DSS
SOC 2® systems can overlap with PCI DSS payment processing and card holder data systems.
NIST CSF
Organizations can apply the CSF’s continuous improvement cycle to SOC 2® compliance. This helps you to review and update controls to address new threats and vulnerabilities.
Are there any SOC 2® automation tools?
As you might imagine, putting together a SOC 2® report can be a tedious process. If you try to complete a SOC 2® report manually, it will likely lead to errors and missed details. And the whole point of SOC 2® audits is to ensure that all the details are taken care of.
Out-of-the-box SOC 2® program templates can be a great help to get successful SOC 2® reporting faster. A preconfigured SOC 2® template can be found Hyperproof’s library of over 70 frameworks. And we can tailor any SOC 2® requirements and controls to the needs of your company.
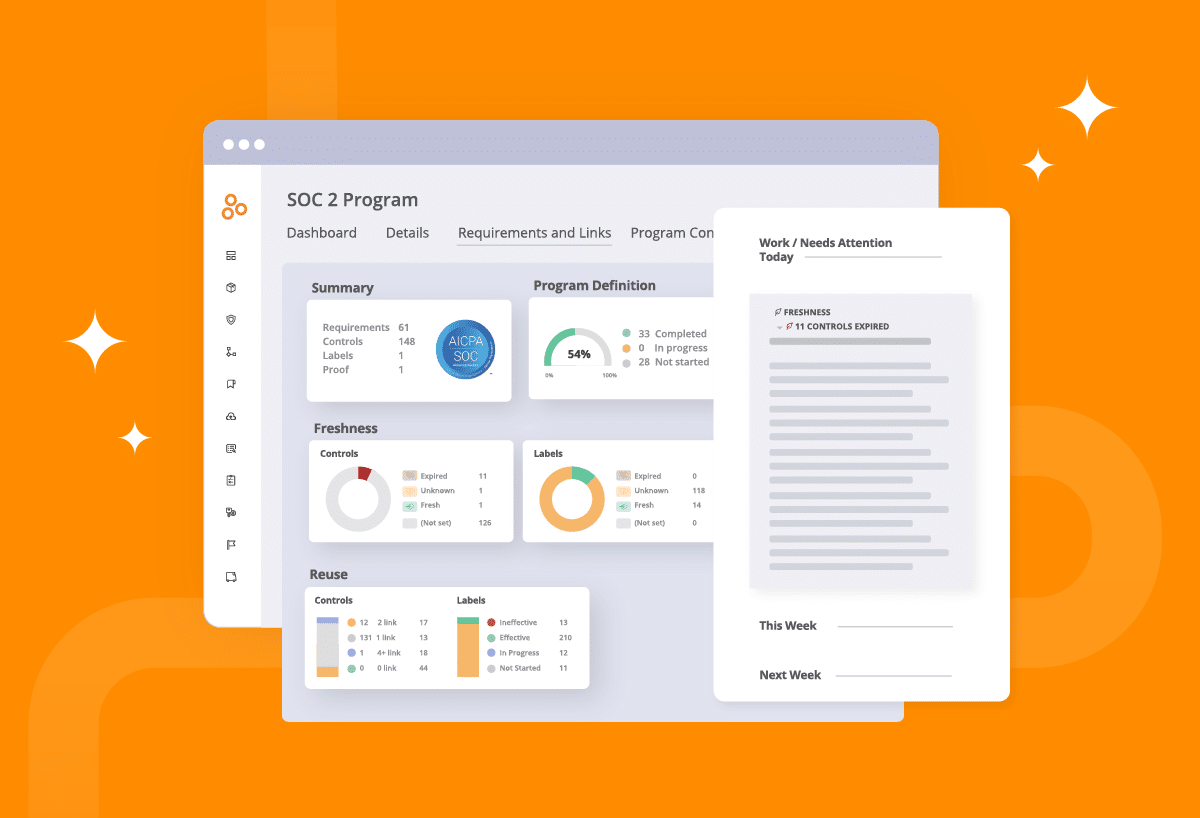
Hyperproof can also automate evidence collection for your SOC 2® audit. This helps avoid redundant work and ensures consistent documentation to fulfill auditor requests. Plus, any pertinent information used in your SOC 2® reporting can be used to comply with other reporting standards and vice versa. You can also assign tasks to collaborators, automate task assignments, and easily review workflows.
The Hyperproof SOC 2® automation tools accelerate SOC 2® reporting so you don’t have to worry about report preparation delays. Who knows? You might even get your SOC 2® report completed ahead of schedule!
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?











