Use Audit Trails to Improve Security, Maintain Compliance, and Streamline Processes
You may have heard of the term “audit trail” before. Setting up audit trails is an important compliance activity all organizations need to take to maintain customer trust, protect their reputation and stay in compliance with laws, regulations, and compliance frameworks. The purposes of audit trails include reducing the risk of fraud, preventing material errors in companies’ financial statements, preventing unauthorized users from accessing company resources, helping companies detect intrusion attempts into their assets, and determining how security incidents occurred.
In this article, we’ll cover what an audit trail is, why you need to maintain audit trails, how audit trails can be set up effectively, and how audit trails play a role in compliance.

What is an audit trail?
Audit trails keep a record of a sequence of events and actions in chronological order. Audit trails can be set up on systems and application processes. The audit trails log how systems are functioning alongside what users are doing within those systems. When audit trails are used in conjunction with appropriate tools and procedures, they can detect security violations, whether valuable records (e.g. financial data in a company, a patient’s medical information) have been tampered with, system performance problems, and flaws in applications.
Audit trails are often required for regulatory compliance. Publicly traded companies are required to maintain audit trails on their financial reporting systems under the Sarbanes Oxley Act (SOX). Further, HIPAA (Health Insurance Portability and Accountability Act of 1996) has set out medical record keeping requirements for protecting health information privacy; healthcare organizations must maintain audit logs in order to meet these requirements.
All in all, audit trails can be quite useful for analyzing and reporting on operational and managerial processes.
The National Institute of Standards and Technology (NIST), a government agency within the U.S. Department of Commerce defines a security audit trail as the following:
“A set of records that collectively provide documentary evidence of processing used to aid in tracing from the original transactions forward to related records and reports, and/or backwards from records and reports to their component source transactions.”
The National Institute of Standards and Technology

What purposes do audit trails serve?
Audit trails serve several purposes; they help organizations improve security, maintain compliance and streamline their audit preparation processes.
Audit trails and security
Audit trails can benefit security teams in the following ways:
- Deter bad behavior such as misuse of systems and internal fraud. When employees and contractors know that their activities are logged, it can deter people from misusing their privileged access to key systems containing sensitive information. Audit trails can also identify internal fraud by keeping track of different users and how they’re interacting with a company’s data.
- Improve incident response. Analysis of audit trails can help security teams reconstruct events after a problem has occurred, and learn from those events to improve their responses to future security incidents.
- Intrusion detection. Audit trails can help security staff identify moments when intruders are attempting to penetrate into systems and do harm.
Audit trail and compliance
Audit trails are a legal requirement for many industries and company types. Here are the industries where audit trails are required for ongoing compliance.
Audit trail compliance requirements for publicly traded companies
Audit trails help finance teams in companies of all industries stay in compliance with their legal obligations. As we mentioned earlier, all publicly traded companies need to keep audit trails and review them on a regular basis. By law, their books (financial statements) must be audited once a year at a minimum by independent, third-party public accounting firms.
Audit trail compliance requirements for healthcare companies
Healthcare organizations must abide by HIPAA guidelines, putting in place rigorous security measures to protect patient health and identifying information. To meet HIPAA’s requirement around when and how patient health information can be disclosed, healthcare organizations need to set up audit trails that track who has access to a patient’s medical information, when that secure data was accessed, who accessed it, and for what purpose.
Audit trail compliance requirements for federal government contractors
The U.S. government requires all federal agencies to protect federal information in conformance with a security standard titled NIST SP 800-53, Security and Privacy Controls for Information Systems and Organizations. This document contains a collection of hundreds of specific measures that can be used to protect an organization’s operation and data and the personal privacy of individuals. NIST SP 800-53 has 20 control families including one on “audit and accountability.” This control family contains a number of specific guidelines that government agencies need to follow regarding how to set up audit trail policies and procedures, log events in support of the audit function, conduct audit record reviews, and more.
If your organization is contracting with a federal agency or wants to bid for a contract, you’ll need to ensure that your own security safeguards are meeting the agency’s security requirements, including requirements around setting up audit trails.
Maintaining audit trails will streamline audit processes
Although it takes time to decide what audit trails to implement and set up, once they are in place, they can help you streamline your audit preparation process. External auditors are looking to test control processes system admins had set up over your key systems (ie., CRM, Financial Reporting) and see whether they operate consistently over time and in fact conform to your company’s established policies and procedures. When system and user activities are properly tracked, it’s easy to send this information to your auditor to verify. The audit process can be completed more quickly.
On the other hand, if audit trails (and evidence) are missing from the controls your auditors want to test, it can negatively affect your chances of getting a clean result (a good grade on your audit).
Beyond the purposes stated above, having audit logs is a sign that you’re operating a mature organization that prioritizes compliance, control, and a streamlined audit process.

What types of organizations should maintain audit trails?
If your organization is handling any sensitive information (and what organization isn’t at this point?), you should use audit trails in one form or another. Some examples of industries and domains that use audit trails include financial and accounting, cloud computing resource usage, manufacturing product design, medical information, clinical research data, CRM records, e-commerce sales records, and much more.
Examples of how audit trails benefit organizations
As we mentioned earlier, there are a lot of benefits to maintaining solid audit trails. Let’s look at specific examples of how audit trails can help your organization.
1. Maintain a secure posture in your organization
Audit trails can help you deter bad behavior from your staff (from a security standpoint), understand how and when a security incident happened so you can prevent it in the future, and assist you in detecting intrusion attempts.
Promoting individual accountability
Audit trails can help managers maintain individual accountability. When users know that their actions are tracked by an audit trail, they’re less likely to attempt to circumvent the company’s security policy.
Gain insights on whether data was improperly modified
Audit trails can be used alongside access controls to identify and provide information about users suspected of improper modification of data (e.g., introducing errors into a database). An audit trail may record “before” and “after” versions of records. Someone can compare the actual changes made to the records and what was expected. This can help managers identify if errors were made by the user, by the application software, or by some other source.
Gain insights into non-sanctioned behaviors
Audit trails also complement logical access controls that restrict the use of system resources. Audit trails can be used to detect when someone has misused their privilege to access a particular resource. For example, let’s say each people manager has access to the personnel records of their direct reports (e.g. compensation information). An audit trail can reveal that a certain individual is downloading far more records than the average user, which could indicate the selling of personal data.
Here’s another example. An engineer is using a computer for the design of a new project. Audit trail analysis can show that an outgoing modem was used extensively by the engineer the week before he quit his job. This could be used to investigate whether proprietary files were sent to an unauthorized person.
Reconstruct events after an incident has occurred
Audit trails can help you understand how an incident happened, why normal operations were halted, and how much damage had occurred due to the problem. Audit trails can help you know whether errors were caused by human operators or the system itself. If, for instance, the integrity of a file is questioned, an analysis of the audit trail can reconstruct the series of steps taken by the system, the users, and the application. It can be very useful to know the conditions that existed at the time of, say, a system crash, in avoiding future outages.
Additionally, if a technical problem occurs (e.g. a data file becoming corrupted), audit trails can facilitate the file’s restoration (e.g. by using the record of changes made to reconstruct the file).
Intrusion detection
Intrusion detection is the process of identifying attempts to penetrate a system and gain unauthorized access. If audit trails have been set up to record appropriate information, they can be analyzed to help someone detect intrusions after the fact. For instance, an audit trail may detect changes in a system’s performance indicative of a virus or malware or that unauthorized access was attempted (or was successful).
Monitoring critical systems
Audit trails may also be used to monitor the status of processes within systems and applications deemed critical to a company’s business or mission. This is often referred to as real-time auditing or monitoring. An analysis of the audit trail may be able to confirm that the system operated normally (e.g. that an error resulted from a human error as opposed to a system-originated error). System performance logs can complement audit trails to show significant or sudden changes in the use of system resources — a security red flag.
2. Fraud prevention and detection
Audit trails provide a critical tool in fraud detection. When audit trails are created for every transaction within a system, they provide information proving the legitimacy of transactions. One example in the finance arena is making sure all business payments have a supporting document such as purchase orders and approved invoices. A bank reconciliation, conducted by someone other than the check writers and signers, comprises part of an audit trail. The presence of an audit trail also reduces the chances of employees committing fraud without detection.
3. Be well-prepared for audits (to meet compliance requirements)
Publicly-held companies must undergo an independent, third-party SOX audit every year. Many privately held and public companies also need to go through IT compliance audits on an annual basis to maintain security standards and certifications (e.g. SOC 2, ISO 27001, FedRAMP, PCI) they need to provide customers the assurance they’re trustworthy from a security point of view.
If the controls the auditor needs to assess have an audit trail, the auditor can quickly determine if the controls were operating correctly and consistently. When auditors can do their work faster, they can complete the audit sooner — so it’s better for both the auditors and the auditee organization to have a comprehensive and accessible audit trail.
Further, by adhering to audit trail requirements within the regulations your business is subject to, you can make sure you’re not hit with penalties or fines due to violating mandated requirements.

How does an audit trail work?
The reach of an audit trail can vary, and it is up to an organization’s system administrators, security personnel, and managers to determine how audit trails are designed and implemented. Because there are costs associated with setting up audit trails, organizations usually prioritize setting them up on systems that are deemed mission-critical or are storing highly sensitive data.
For instance, specific to the healthcare industry, IT security personnel at a hospital would set up an audit trail within their Electronic Medical Records (EMR) application that tracks who is accessing patients’ medical information and updating patient records, when that secure data was accessed, and what was done to the record (e.g. read, updated, deleted, etc.).
The hospital’s EMR administrator sets up this audit trail and the patient logs because the hospital must comply with HIPAA — a federal law that sets the standards for protecting patient health information and when and how it can be disclosed, outlawing disclosure without patient knowledge. An audit trail gives hospital staff visibility into how patient information is stored and accessed and allows them to fulfill the HIPAA mandate that healthcare organizations regularly review and manage how their information is stored and accessed.
According to this NIST bulletin, there are several levels of audit trails:
- System-level audit trails: If a system-level audit capability exists, the audit trail should capture, at a minimum, any attempt to log on (successful or unsuccessful), the log-on ID, the date and time of each log-on attempt, date and time of each log-off, the devices used, and the function(s) performed once logged on (e.g., the applications that the user tried, successfully or unsuccessfully, to invoke).
- Application-level audit trails: Application-level audit trails can capture information not tracked within system-level audit trails. In general, application-level audit trails monitor and log user activities, including data files opened and closed, specific actions, such as reading, editing, and deleting records or fields, and printing/downloading reporting.
- User audit trails: These can log things such as all commands directly initiated by the user, all identification and authentication attempts, and all files and resources accessed.
How to design and implement audit trails properly
An audit trail should include enough information to establish what events occurred and who (or what) caused them. In general, an event record should specify when the event occurred, the user ID associated with the event, the program or command used to kick off the event, and the result. Date and time can help determine if a user was an unauthorized intruder or the actual person specified.
Further, it is important to protect audit trail data, since the data should be available for use when you need it and it’s not useful if it contains errors. Access to audit logs should be strictly controlled, and modification of audit trail data should be guarded against via mechanisms such as the use of digital signatures. Strong encryption should be applied to preserve the confidentiality of sensitive information within audit trails. System managers and administrators, with guidance from IT security professionals, should also determine how long audit trail data will be maintained.
Additionally, audit trails are meant to be reviewed in a timely manner; otherwise, they’re of little value. Audit trails should be reviewed:
- right after a problem occurred (e.g. a software problem, a known violation of existing requirements by a user, or an unexplained system or user problem), and
- periodically based on the importance of identifying unauthorized activities.

Hyperproof makes it easy to maintain audit trails (and streamlines audit prep)
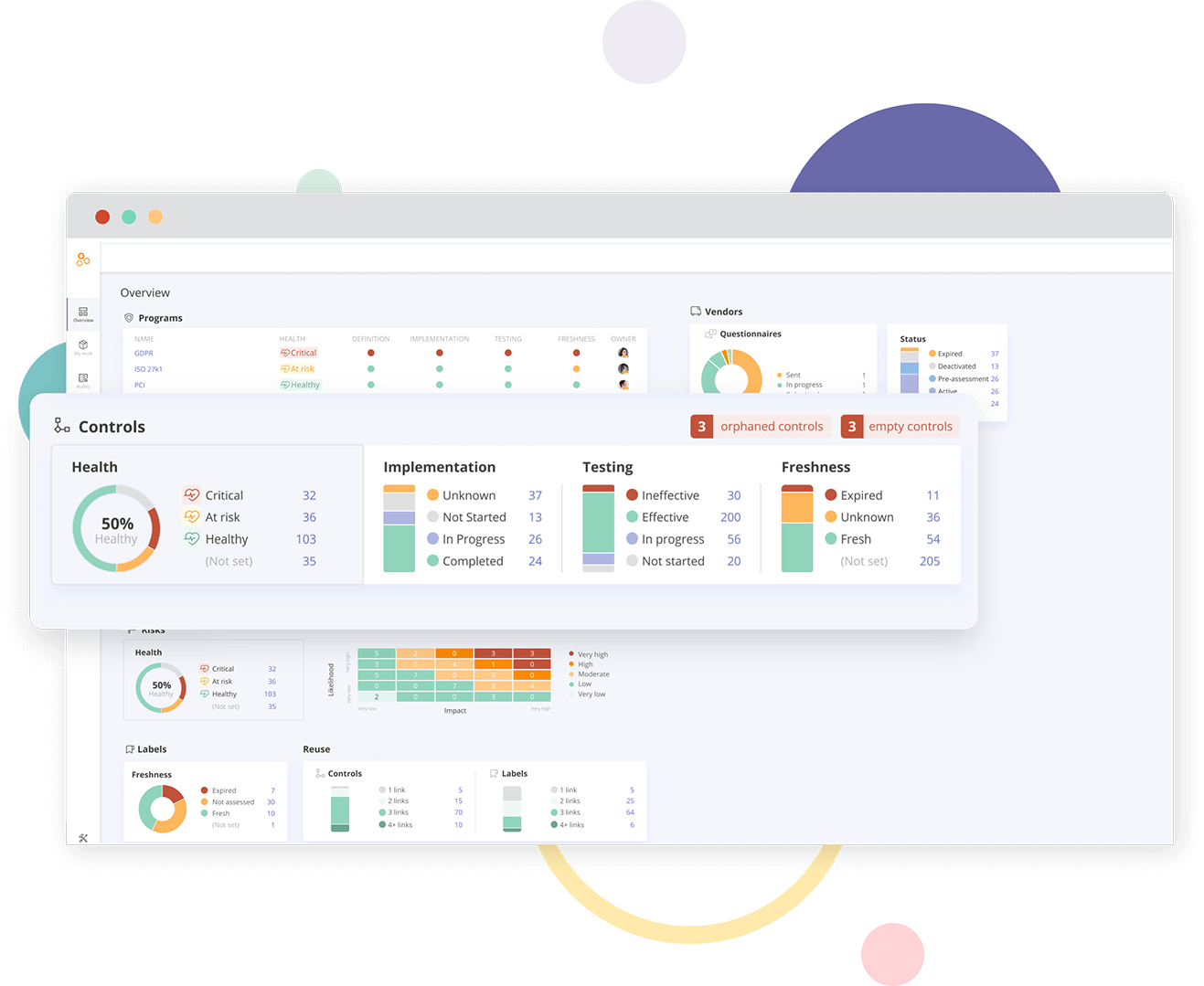
Compliance and security professionals know how tedious and time-consuming it is to pull audit trail records and system logs for their auditors to review. For certain compliance audits, there may be many systems included within the scope of that audit (e.g. ISO 27001 is an example framework that’s quite broad in its scope). Without purpose-built tools, compliance professionals must log in to each system separately and manually pull the requisite audit logs. Hyperproof seeks to drastically reduce the hassle of gathering evidence of control activities, including audit logs.
Hyperproof is built to be a single source of truth for an organization’s compliance requirements, internal controls, evidence, and risks. Hyperproof comes with a feature called Hypersync specifically to help people automate the gathering of evidence required for control testing. Hypersyncs are data connectors that automatically pull in user-defined data from many third-party cloud-based apps (e.g. CRM, HRIS, ticketing), DevOps, IT, and security tools. We built these Hypersync connectors to give compliance professionals time back to focus on reviewing audit trails, gaining insights, and improving their controls — and reduce the time that system administrators and IT pros and developers need to devote to supporting compliance requests.
With Hyperproof, compliance professionals can do a one-time setup and then automatically get compliance data from multiple systems, including records of whether system settings, encryption settings, password policies, security groups, or user access levels have changed over time and when changes occurred. This data can come into Hyperproof either on a cadence or on-demand. All compliance data comes with meta-data such as what system it comes from, the timestamp, the user who set it up, and more, so auditors trust that the information is credible (and hasn’t been modified by human operators).
To learn more about how Hyperproof can support your compliance efforts, sign up for a personal demo.
Hyperproof drastically reduces the hassle around gathering evidence of control activities, including audit logs.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?