The Importance of Endpoint Security
Are your organization’s endpoints secure?
That’s the question keeping more than a few CISO’s up at night—and with good reason. In 2019, according to the IDC, 70% of successful breaches originated on the endpoint.
Today’s business is mobile, with people becoming the new perimeter. As organizations expand and more employees work remotely, the number of vulnerable endpoints grows. Centralized solutions no longer protect networks, and organizations must embrace multi-layered endpoint security solutions or face a greater risk exposure to costly breaches.
In this article, we will discuss endpoint security and why it’s critical to your organization’s overall security in today’s threat environment.
What threats does your enterprise face?

Threats to your business’ information security come in many forms today, and advanced hackers are constantly changing their methods and exploiting unpatched software or lax employees. Endpoints in particular can provide easy targets for malware botnets. Ransomware can hold data hostage or blackmail the owner, while spyware quietly gathers passwords. New advanced file-less malware, estimated to make up 50% of malware attacks in 2019, quietly infiltrates through various channels, making detection difficult. Social engineering ploys, such as spear phishing and whaling, constantly test employees by attempting to extract information.
In 2020, with the global pandemic forcing many employees to work remotely, organizations must protect more endpoints than ever. Attackers know humans, who are now often working outside of the controlled environment that office computers and networks provide, are security’s weakest link. Forced outside the corporate structure, humans are more susceptible to lapses in judgment, creating opportunities for attack.
What is endpoint security?
Endpoint security is a multi-layered initiative focused on blocking threats and securing network endpoints. Endpoint solutions operate from centralized software with installs on each device. Endpoint platforms mirror larger systems with firewalls, access control, and vulnerability assessment to neutralize threats.
All endpoint security solutions should provide data classification and loss prevention, insider threat monitoring, network and privileged user access control, anti-malware, email gateways, and Endpoint Detection Response (EDR).
Additionally, encryption and application control play a significant role in endpoint security. Encryption is essential to ensuring data protection in communication. Application control prevents risky endpoint application usage—something humans are prone to.
Why endpoint security is important

Effective endpoint security is a must for modern enterprises—locking all doors on your corporate house isn’t a matter of choice anymore. Data is the lifeblood of business, and protecting it is paramount to organizational success.
With the shift towards mobility, security must now occur at all points within a network. Centralized security systems prove ineffective in today’s dispersed landscape. Jose-Miguel Maldonado, VP Business Ops & Security at Rubica, explains, “People are outside the corporate security structure and today’s attacks are extremely sophisticated. Traditional solutions like on-premise firewalls and anti-virus just aren’t enough anymore”.
As organizations grow, so do the endpoints and the cost of protection. However, the cost of not securing your network can be far greater in terms of data loss, regulatory fines, and reputational damage.
On-premise endpoint security
This option is based on securing all network endpoints from a solution hosted and maintained on in-house servers. All costs fall on the user—this includes the space, electricity, cooling, and staff. On-premise software usually requires a large initial investment and can involve lengthy installation. For these reasons, it may not be the best choice for budget-conscious organizations seeking faster solutions.
Cloud-based endpoint security
This option involves securing all network endpoints from a solution hosted and maintained on cloud vendor servers. Often referred to as “endpoint protection,” this solution provides a cost-effective, agile option that can be up and running in minutes. Cloud-based solutions offer numerous advantages, starting with access to vendor databases and monitoring that provides rapid threat response. Additionally, for a reasonable monthly fee, users get automatic data backups, quicker patching even for remote devices, and remote system control.
Types of endpoint security

Endpoint security engages specific practices to block threats and secure your network. Here are some to keep in mind:
- Endpoint encryption: Involves the coding and scrambling of data, making it indecipherable without a key. Encryption is the last and possibly the most important security layer because it protects the data even if it falls into the wrong hands.
- Forensic analysis: Works in conjunction with EDR by monitoring all endpoint activity and creates a digital footprint of all incidents. All information and evidence surrounding an attack—what happened, who’s responsible, and the resulting consequences—is collected and analyzed to prevent future incidents.
- IoT protection: Many IoT devices sorely lack adequate security upon installation. What can your organization do to lock down IoT devices? Start by installing an EDR system to manage, monitor, and scan for vulnerabilities. Be sure to remove outdated devices, install next-gen solutions, monitor all app and device access, encrypt communications, and segment your network to isolate problems.
- Email gateways: E-mail is the most common way for criminals to attack networks, so email gateway software is critical today. Safe emails continue through the system, while potential threats go to quarantine. All email gateways should include virus and malware blocking, content filtering, and email archiving.
- Quarantine protection: This is the practice of separating dangerous files to prevent harm to devices and networks. Rapidly isolating dangerous files is essential to endpoint security, and quarantining also allows valuable files to be cleaned rather than discarded.
Proving sufficient end-point security
If there is one thing more important than securing your endpoints, it’s providing proof. Documenting your organization’s ability to control risk and protect sensitive data offers many benefits — from avoiding regulatory fines to maintaining an attractive vendor reputation.
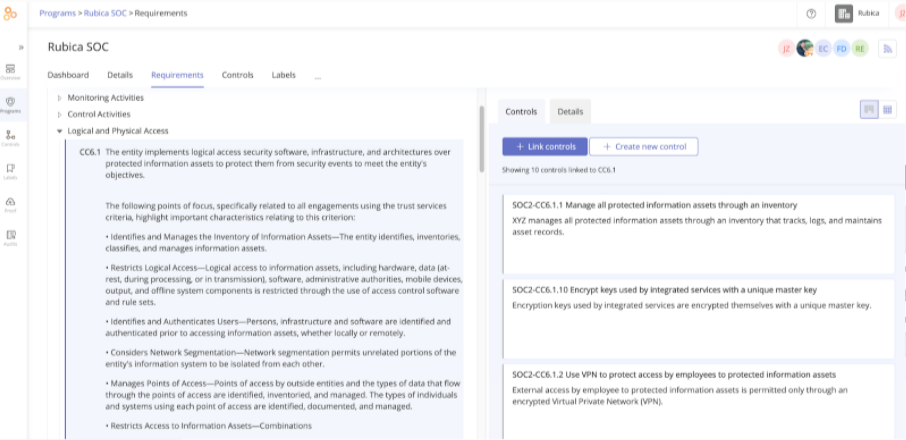
Obtaining a favorable SOC 2 report will provide documentation of sufficient endpoint security. SOC 2 reports are unique to each organization, with fluid requirements and self-designed controls. Your organization can set its criteria, but it must ensure controls are in place to meet the requirements, then effectively document success for an auditor—not always an easy feat. More related content: SOC 2 compliance: What You Need to Know and Need to Do.
Endpoint security is critical for your enterprise
In today’s mobile world, security is evolving rapidly—endpoints now form the new perimeter, and organizations must protect their data across networks. As organizations grow, so do their vulnerabilities, and securing endpoints is mandatory for all enterprises regardless of size or stature. Jose-Miguel Maldonado emphasizes this point: “Whether you’re a small or large enterprise today, you need to put the time and effort into securing your business with a strong endpoint security solution.”
Smart organizations of all sizes will fortify the new perimeter, protecting each device like it’s the key to their entire house with robust endpoint solutions. They will avoid the steep financial and reputational hit of costly breaches—and their CISO’s will sleep better at night knowing their endpoint network is secure.
Additional resource on securing endpoints
To get practical solutions for securing all devices and networks in the remote-work environment, check out this on-demand webinar “Are Your Cybersecurity and Compliance Measures ‘Remote-work’ Ready?”
About Author

Mark Knowles is a freelance content marketing writer specializing in articles, e-books, and whitepapers on cybersecurity, automation, and artificial intelligence. Mark has experience creating fresh content, engaging audiences, and establishing thought leadership for many top tech companies. He is based in the sunny state of Arizona but enjoys traveling the world and writing remotely.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?