3 Tips to Radically Reduce Your Evidence Management Burden
Here at Hyperproof, we consistently hear from security compliance professionals that they’re spending an inordinate amount of time on collecting evidence for IT security and data privacy audits. When we surveyed over 1,000 security assurance and compliance professionals in December 2020, we found that 1 in 2 respondents spend at least 50% of their total time at work on low-level administrative tasks, such as locating evidence needed for audits.
Why is collecting evidence such a daunting challenge?
For more established organizations, the challenge is three-fold. One, there’s a plethora of regulations and audits the organization has to go through each year — that means there’s a massive volume of information that needs to be gathered and verified for audits. Second, larger organizations typically have hundreds of IT applications and business processes. Compliance professionals must coordinate with dozens or hundreds of people operating various IT applications within the organization and explain to system owners what the compliance team needs from them for each audit. This means they spend a lot of time going back and forth with system owners until they receive the correct information. It often takes multiple reminders for people to complete the task they’re asked to do.
Making things more complicated is the fact that many compliance teams still use ad-hoc tools such as spreadsheets, email, and cloud-based storage tools (e.g., Sharepoint, G-Drive, etc.) to manage their activities, making it difficult for them to quickly find relevant information and keep track of progress. Further, information about what needs to be provided is easily lost across the many tools the company uses.
For early-stage companies, collecting evidence is tough for a different set of reasons. When a company is still in its nascent stage of development, they may not have much in the way of processes for security and compliance. There’s a lot of work to do to define policies and procedures and set up a structure for managing their compliance program before the organization is ready to gather evidence for an audit.
Here at Hyperproof, we want to help security assurance teams eliminate routine, repetitive work associated with collecting evidence for audits and give people time back to focus on higher-value work. In this article, we’ll show you a few things you can do to set up a highly organized approach and system for evidence management that allows you to dramatically reduce the amount of time you and your team need to spend on this area.
Tip 1: Document the current state of controls, including what, whom, and when
Security and compliance are two sides of the same coin. You invest in security measures because your organization has valuable information assets that need protection. Compliance is about proving and attesting that the security measures you intended to put in place are in fact present, meet certain externally defined standards, and are functioning effectively to protect your systems and the data within these systems — so customers can trust you to handle their valuable data.
Gathering evidence for audits is a tedious and complicated exercise if your security measures (policies, procedures, technical controls, training, etc.) aren’t well documented or if they aren’t mapped back to specific security and compliance requirements.
If you want gathering evidence for security and compliance audits to become an easy task, it’s important to have good documentation of your “controls”. Controls are activities, processes, procedures, technical solutions and policies your business puts in place to ensure that specific security and compliance requirements are met and risks are mitigated. If you don’t currently have good documentation of existing controls in your business, investing energy in this area is important. Below are three sets of questions to think through to help you get to a place where controls are well-documented.
WHAT:
- What business processes are running within your organization where data security/privacy risks and concerns exist?
- What systems and software applications are people in your company using to support these business processes?
- What risk scenarios are likely to occur given how a process works and the way people in the firm are operating a particular system or piece of software?
- What controls (e.g., risk mitigation/compliance policies, procedures, protocols, technology) ought to be in place to mitigate this specific risk and ensure compliance with applicable standards/regulations your company is subject to?
- Could this control be embedded into a system and enforced automatically, or is this a procedural control that relies on involvement from certain people within the business?
WHO:
- Who is responsible for ensuring that the control is performed and operating effectively? Control owners are usually those who “own” a system and have admin privileges. This person would gather evidence of controls’ performance and send it to the compliance team to review.
WHEN:
- When: Given the nature of the risk, the way a particular business process works, and the particular systems in use, how often should the control be reviewed? How often should revisions to a policy be considered? It’s important to have a way to monitor performance of controls — especially when a control’s performance depends on a person having to remember to do something.
Want to gain efficiency in all areas of compliance and security assurance?
If a “control” is a policy that doesn’t need to change too often (e.g., an employee code of conduct document), it makes sense for someone to send the latest version of a policy to the compliance manager manually. However, other “controls” will be technical controls embedded into systems through configuration settings. Monitoring that control is about making sure a setting stays what it should be and no unauthorized changes have occured. In that case, it’s unrealistic to expect the system owner to pull that evidence manually everyday. You’ll want to see if you can get access to the system where the technical control is set up and find a way to automatically extract that evidence on a daily basis.
Once you’ve identified what controls need to be in place and what systems certain controls are embedded within, it’s much easier to determine what type of evidence you should gather to verify the design and effectiveness of each control. In this regard, it’s helpful to think about what an outside auditor would want to see as valid evidence.
Tip 2: Manage your evidence and controls in a single platform
By centralizing all of your ongoing control evaluation and evidence management efforts onto a single platform, you can start to keep a better track of what needs to be done, who’s responsible for the work, and who needs to be held accountable.
By having a single repository for evidence, you can gather evidence once and re-use for upcoming, similar audits. Having a central repository also helps to retain institutional knowledge and makes it much easier to onboard new hires and help them get up-to-speed on compliance matters. Additionally, managing things in a central place will help save you and your auditor time; you will be able to provide your auditor direct access to all document version histories, your completed work, and information on how evidence changed over time.
In a compliance operations platform such as Hyperproof, you can document your controls and map the controls to the requirements within various information security standards (e.g. SOC 2, ISO 27001, NIST SP 800-53, PCI-DSS, CMMC and others) as well as the risks your organization is tracking. You can collect evidence for the control — so evidence and control are linked.
Each control comes with customizable fields to help you manage that control on an ongoing basis. For instance, you can assign controls to people to manage, note down what type of information someone needs to provide to demonstrate that a control is operational, and set a cadence to review the control. You can also set cadences on controls to review them periodically and collect evidence attesting to the effectiveness of controls on an automated basis.
Sign up for a demo of Hyperproof
Tip 3: Automate routine repetitive work
There are multiple manual workflows within the evidence collection process you can automate. Here are some key areas:
- Collecting evidence: Asking people to submit evidence is one of the most time-consuming tasks compliance managers have to do. With a Compliance Operations platform like Hyperproof, you can automatically extract evidence from certain source applications into Hyperproof. Simply go to a particular control in Hyperproof and connect Hyperproof to your source system where evidence resides (e.g., Google Drive). Once you set up the connection, Hyperproof will automatically extract evidence from that application on an automated basis.
- Reminding colleagues to submit evidence: No one likes bothering their colleagues with multiple requests for the same documents. With Hyperproof, you can set up automated workflows to remind teammates to upload new evidence so you can spend your time on higher impact tasks.
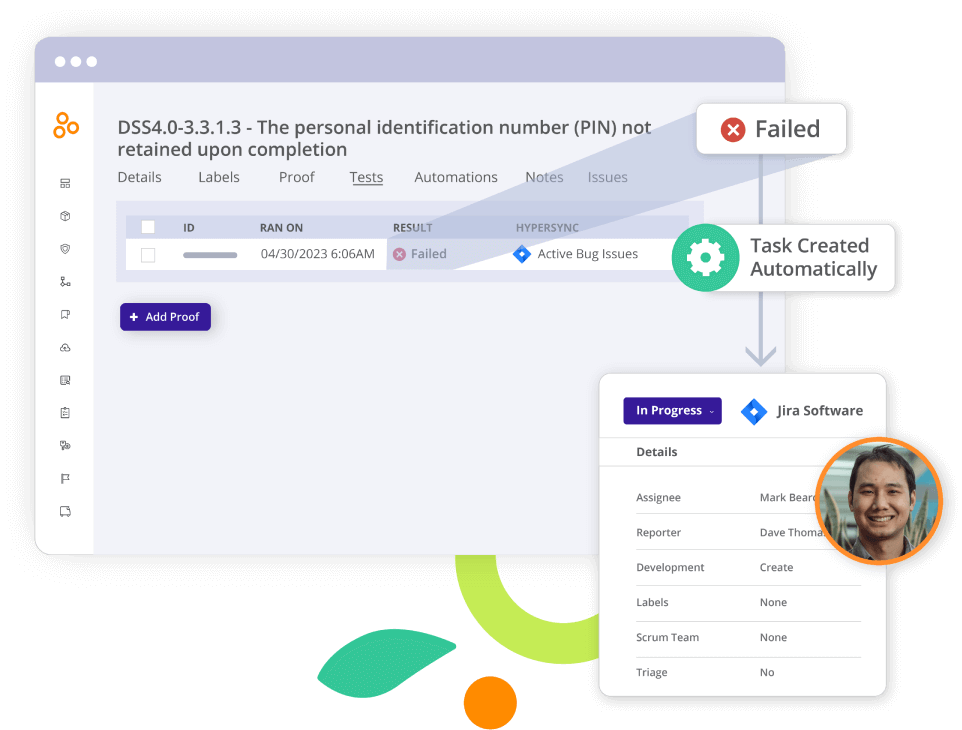
- Filing away evidence: Compliance managers traditionally had to be the ones to organize all the compliance evidence people send to them. Evidence comes from all sorts of tools such as Jira, Slack, and email — and compliance managers had to file them somewhere else. This type of organizational work can be eliminated with a platform like Hyperproof. Hyperproof integrates with project management tools like Jira as well as communications tools like Microsoft Teams and Slack so compliance managers can initiate evidence gathering requests directly on specific controls. The person who needs to submit evidence can submit information within the system they already use (e.g., Jira for instance) and that information goes back into Hyperproof automatically.
- Automate requesting evidence: With an upcoming feature in Hyperproof, compliance managers will no longer have to manually request their colleagues for evidence and keep track of due dates. Compliance managers will be able to schedule recurring tasks (weekly, monthly, etc.) that automatically remind people to complete their work. Users will be able to specify if they want a task to have a corresponding Jira issue, helping cut down on manual work further.
- Automate testing of controls. Here at Hyperprof, we plan to release features in the coming months to provide the ability to automatically test controls and gauge their effectiveness based on collected evidence extracted automatically.
See available integrations for Hyperproof
How Hyperproof can help
When you take the time to develop a solid process for collecting and managing evidence for IT security/compliance audits, and automate the process with a compliance operations platform like Hyperproof, you can expect to save hundreds or thousands of hours each year, contain the costs of compliance, and empower your security assurance team to do their best, most impactful work everyday.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?