What Is the FedRAMP Incident Response Control Family?
Incident response is a critical piece of any enterprise cybersecurity strategy and is also a key component to achieving FedRAMP compliance. FedRAMP, the US government-wide program for ensuring the security of cloud applications and services used by government agencies, is made up of a number of security controls based on NIST SP 800-53.
For the most common FedRAMP level, FedRAMP Moderate, there are 325 controls categorized into 18 families. One of those 18 families is incident response.
Hyperproof is currently on its own FedRAMP Moderate journey, and with incident response being such an important element of cybersecurity to get right, Thomas Wilcox, CISSP, Sr. Director, Security & Compliance at Hyperproof, and Kayne McGladrey, CISSP, Field CISO, recently discussed incident response best practices related to FedRAMP.
Listen in to their conversation here and continue reading for more of their insights.
FedRAMP controls: a look at incident response
The FedRAMP Moderate incident response (IR) control family is designed to help cloud service providers (CSPs) implement a comprehensive incident response program to better protect federal government data and systems from security incidents.
The IR family includes nine top-level controls:
1. IR-1 Policy and Procedures
IR-1 Policy and Procedures: This control requires CSPs to develop, document, and disseminate an incident response policy and procedures.
2. IR-2 Incident Response Training
This control requires CSPs to provide incident response training to system users consistent with assigned roles and responsibilities.
3. IR-3 Incident Response Testing
This control requires CSPs to perform incident response testing annually. Testing should involve all aspects of the incident response plan, including communication, coordination, and response procedures.
4. IR-4 Incident Handling
This control requires CSPs to implement proper handling capability for incidents consistent with the response plan, coordinate handling activities with contingency planning, and incorporate lessons learned.
5. IR-5 Incident Monitoring
This control requires CSPs to track and document incidents, including maintaining records and status of incidents and other information necessary for forensics.
6. IR-6 Incident Reporting
This control requires CSPs to communicate suspected incidents and incident information to affected parties and the incident response team.
7. IR-7 Incident Response Assistance
This control requires CSPs to provide an incident support resource that advises and assists users in handling and reporting incidents.
8. IR-8 Incident Response Plan
This control requires CSPs to develop and maintain an incident response plan. The plan should be tailored to the specific system and organization.
9. IR-9 Information Spillage Response
This control requires CSPs to communicate the classification or impact level of information spills, the security capabilities of the system, the nature of the contaminated storage media, and the access authorizations of all individuals with access to the contaminated system.
Depending on your organization’s security maturity and other frameworks you comply with, you likely are already implementing several or all, of these controls. For FedRAMP in particular, there are several areas to consider when building or expanding on incident response at your organization.
Building a FedRAMP Moderate incident response plan
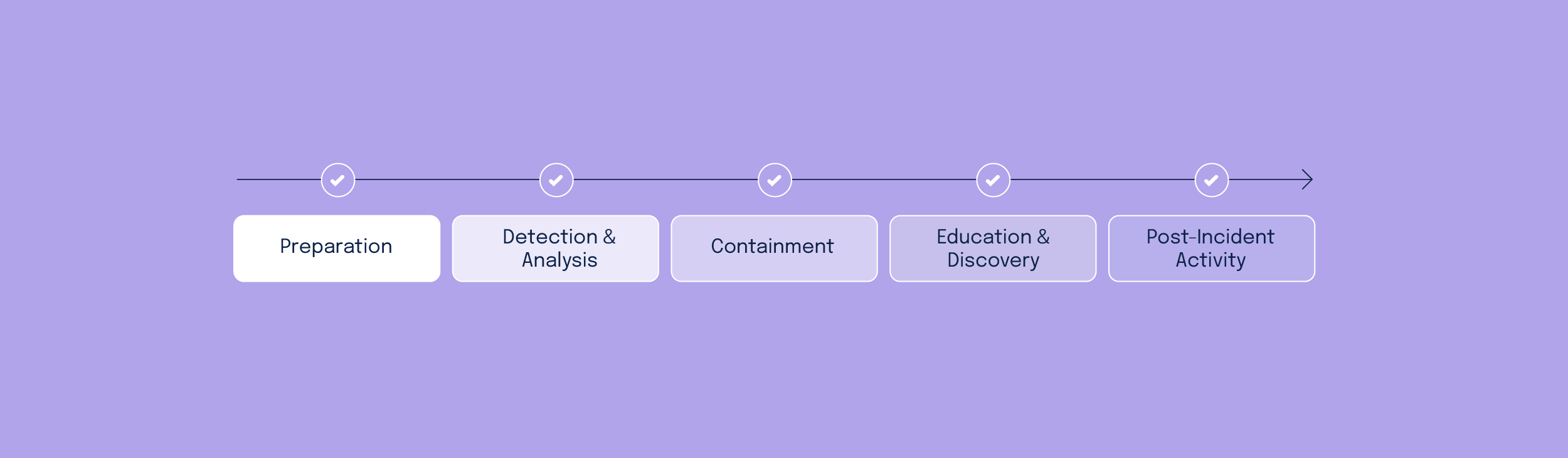
SPs can implement the FedRAMP Moderate incident response control family by following the guidance in NIST SP 800-61, Revision 2, Computer Security Incident Handling Guide. As outlined in NIST SP 800-61, the incident response process has several phases:
- Preparation
- Detection and analysis
- Containment
- Eradication and discovery
- Post-incident activity
One thing for CSPs to keep in mind is they should also consult with their 3PAO and FedRAMP Program Management Office (PMO) for assistance in building and approval of a FedRAMP approved incident response plan. Want more help? Get the FedRAMP compliance starter guide.
Taking a step back to the bigger picture, even though FedRAMP outlines specific controls, every incident response plan should be tailored to your organization and your specific systems, team structure, and environment. Thomas Wilcox explained, “IR plans are going to be highly customized to the company.”
In Hyperproof’s case, that involves specific procedures for inspecting an application stack, how you review certain log events, and how to escalate logging, to name a few examples. “There’s a bunch of pieces that fall underneath this procedurally, and we try to — where possible — roll these things up into a single procedure,” Wilcox said. “The more you can aggregate, the better it is in terms of document-hunting you have to do in the time of incident response.”
A few further pointers: Your IR plan needs to be clearly documented (in multiple separate places in the event of a breach), communicated, and updated regularly.
Not all incidents are breaches: when to escalate events
During an incident, coordination of resources and “who’s on first” is often one of the most challenging parts of IR. As part of your FedRAMP IR plan (and in general), you want to define ahead of time your terms, who has the authority to escalate, and who decides when something will be considered a breach (usually this will be a discussion between the chief counsel, CISO, and CEO).
“Make sure that the parameters that define breach are thoroughly vetted, including who can declare one, because that’s not something you just toss around casually,” Wilcox cautioned. A good best practice, in Wilcox’s mind, is to remember that not all events are incidents and not all incidents turn into breaches. “You should ramp up to the word ‘breach.’ It shouldn’t be something you use often,” Wilcox said.
An event could be anything that is security-related, like an unusual log entry that needs further investigation. If that event is escalated to an incident, it doesn’t necessarily mean you’ve lost any data. The final stage, though, is an incident that does escalate to a breach.
Testing and determining the effectiveness of your incident response capabilities
Per FedRAMP, the IR-3 control requires CSPs to perform incident response testing annually. Testing should involve all aspects of the incident response plan, including communication, coordination, and response procedures. Annual testing does not have to be live-fire testing against your production environment. You will, however, need to conduct tabletop exercises at least annually or when your agency or the JAB requires it.
Additionally, if you do find that your organization experienced an incident, an after-action, post-mortem report following the incident is an excellent way to see what worked in real-time and what didn’t so you can take your findings and refine your IR plan for the future. An after-action report is “really a front-to-back review of the entire process that you just went through,” Wilcox said. “It helps you understand how you can improve this. And in general, it measures your capability.”
Being prepared for FedRAMP

Although incident response planning is required for FedRAMP, it is also invaluable to your company in a moment of crisis. “This is a case where doing your work ahead of time is going to pay off in spades when you actually need it,” Wilcox emphasized.
For more insight on FedRAMP and Hyperproof’s FedRAMP Moderate journey, follow along with our podcast series “Drafting Compliance” with Kayne and Tom. You can also learn more about FedRAMP in our Ultimate Guide to FedRAMP.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












