HIPAA Business Associate Agreement: What SaaS Companies Need to Know
Are you a SaaS company or cloud service provider (CSP) who works with or wants to work with businesses that handle electronically protected health information (ePHI)?
If the answer is yes, your company is held to the same compliance guidelines as your customers under HIPAA Privacy and Security Breach Notification Rules. That’s right—if your company processes protected health information (PHI) on behalf of clients, regulators view you as an extension of their business. You will need to enter into a HIPAA-compliant business associate agreement (BAA) with your customer and must maintain compliance with all applicable HIPPA rules.
If you’re like many SaaS companies or cloud service providers today, you may be a little foggy on HIPAA business associate agreements and your compliance responsibilities under current HIPAA rules. Not to worry—we’ve got you covered. In this article, we’ll dive into the concept of business associate agreements and help you understand how to stay compliant when partnering with companies that handle PHI.
What is HIPAA? Learn about the requirements in our guide.
What is a business associate?
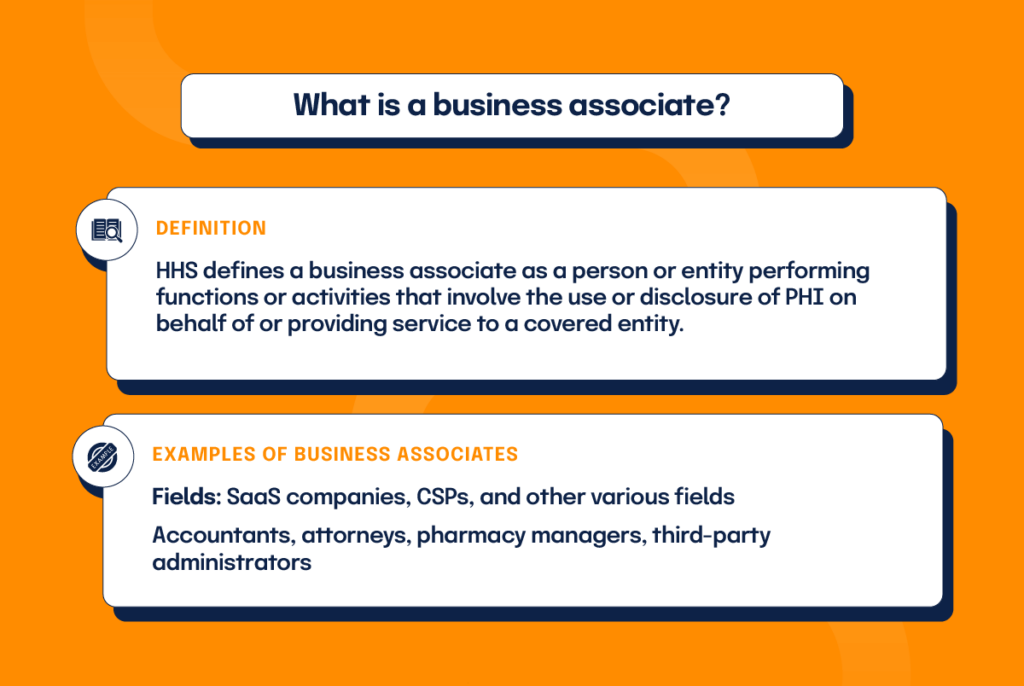
Health and Human Services (HHS) defines a business associate as a person or entity performing functions or activities that involve the use or disclosure of PHI on behalf of or providing service to a covered entity. In other words, if your company performs work involving the handling or disclosure of PHI for a customer who falls under HIPAA regulations, you are considered their business associate (BA). Typical functions performed by business associates include payment processing or activities concerning some aspect of healthcare operations.
In addition to SAAS companies or cloud service providers, business associates come from various fields. For example, accountants, attorneys, pharmacy managers, healthcare clearinghouses, and third-party administrators pulled in to assist with billing or claims processing can all be considered business associates, provided their work involves access to PHI.
Cloud service providers as business associates
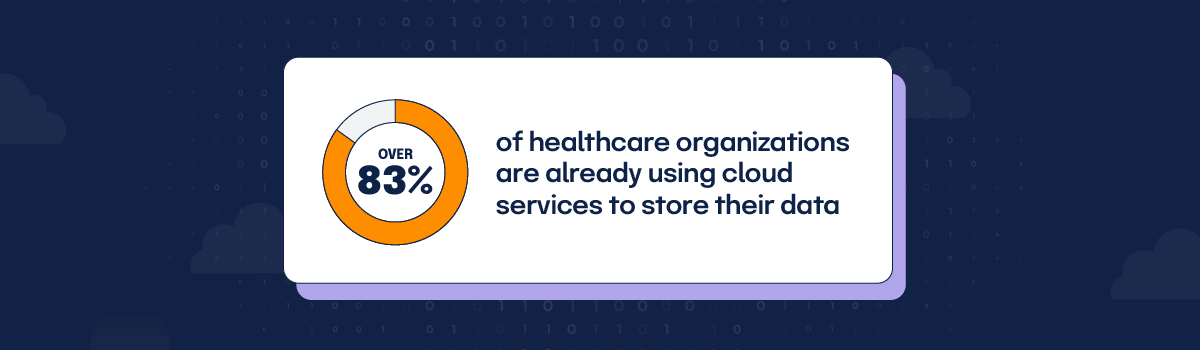
How widespread are cloud services in the healthcare industry today? Consider this—over 83% of healthcare organizations are already using cloud services to store their data, according to a recent HIMSS Analytics survey. When one of these healthcare entities engages a cloud service provider to create, receive, maintain, or transmit ePHI on its behalf, the cloud provider becomes a business associate under HIPAA Rules.
By law, the covered entity must have a written, HIPAA-compliant BAA in place with the cloud provider to ensure PHI protection. As business associates, cloud service providers are contractually obligated to meet all BAA terms in addition to maintaining strict compliance with all applicable HIPAA requirements.
What if a cloud service provider stores only encrypted data, doesn’t have a key, and can’t view the ePHI—are they still considered a business associate and fully responsible under HIPAA Rules?
Yes–lacking the ability to view PHI doesn’t remove business associate status or compliance responsibilities under HIPAA law.
Security rule considerations (and how to satisfy them)
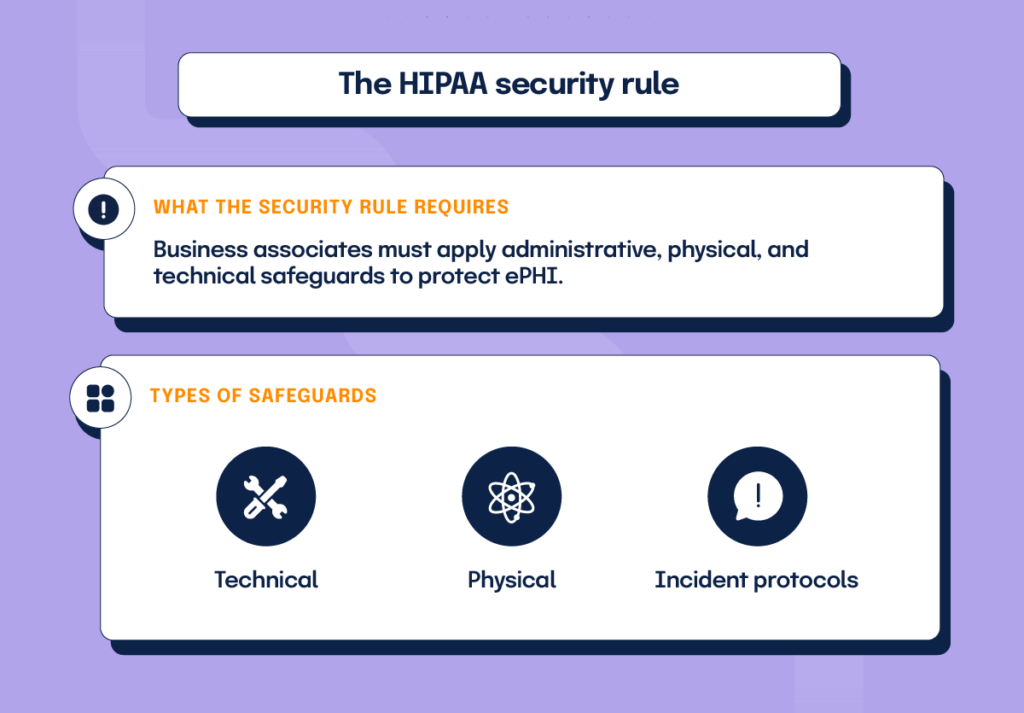
The HIPAA security rule “requires [all covered entities to apply] appropriate administrative, physical, and technological safeguards to ensure the confidentiality, integrity, and security of all ePHI”. As business associates of covered entities, cloud service providers are responsible under the Security Rule to establish security standards for safeguarding information systems containing PHI.
The HIPAA security rule advocates implementing technical safeguards, physical safeguards, and administrative safeguards.
- Technical safeguards would include encryption mechanisms used to make the access and use of PHI as safe as possible.
- Physical safeguards include the standards required for physical access to PHI, such as facility access control, mobile device policies, and workstation use requirements.
- Administrative safeguards pertain to the policies and procedures used in the protection of PHI, such as a risk management policy, security training, incident reporting protocol, and the use of security/privacy officers to oversee security implementation.
Each safeguard has either required or addressable specifications. All required safeguard specifications must be strictly followed. Addressable safeguards allow flexibility with implementation—you may choose not to implement or select an alternative, but you must document your decision for auditors either way.
Privacy rule considerations (and how to satisfy them)
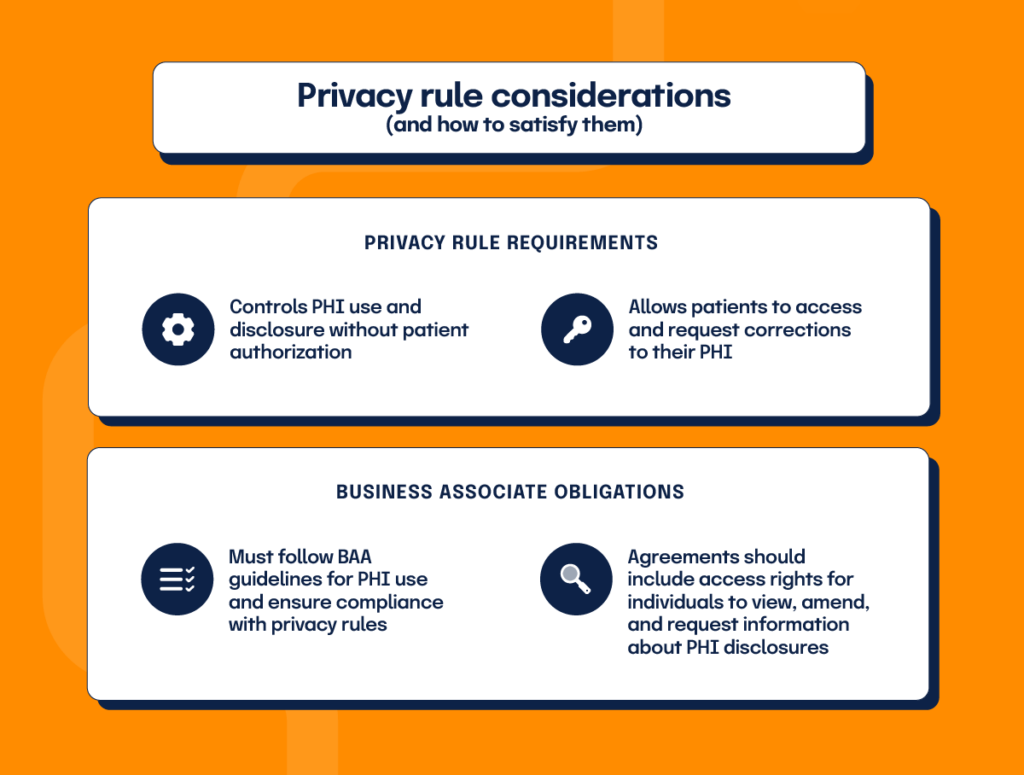
HIPAA’s privacy rule establishes standards for protecting PHI and regulates PHI’s use and disclosure without patient authorization. It also gives patients the right to obtain a copy of their health records and ask providers to make corrections to their PHI.
Cloud service providers acting as business associates may only use and disclose PHI following their BAA and the privacy rule. Even cloud companies who lack control over PHI viewing must ensure the use of encrypted information only as permitted by the BAA and privacy rule.
Business Associate Agreements must include provisions requiring business associates to allow the covered entity access to PHI to fulfill their client obligations. The PHI must be made available, affording individuals their rights to access, amend, and receive an accounting of certain disclosures of PHI. Also, BAAs should always detail the actions required for no-view cloud service providers to meet their privacy rule obligations.
Breach notification rule considerations
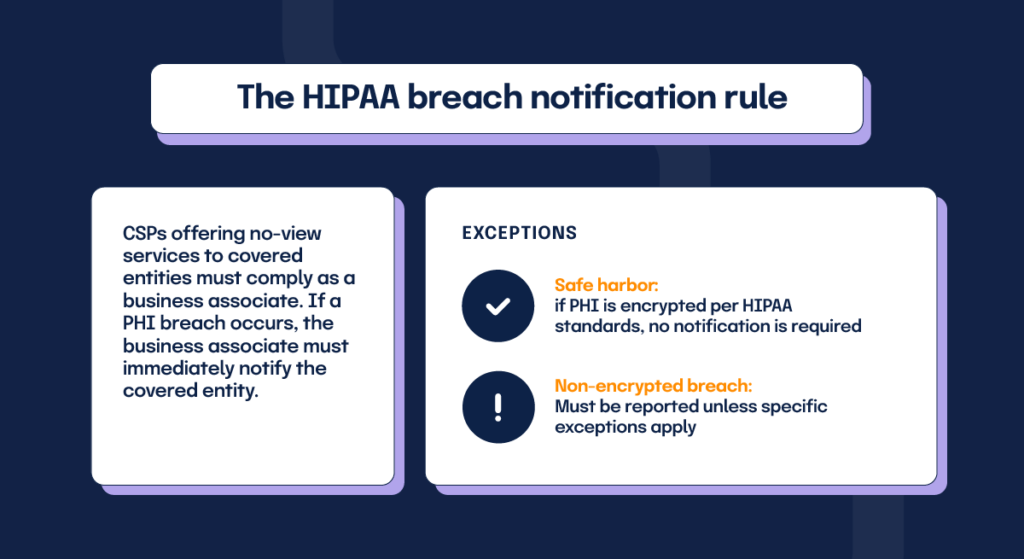
What happens when a breach occurs? The HIPAA breach notification rule requires covered entities to immediately notify appropriate parties should a breach occur. Cloud service providers offering no-view services to covered entities must comply as a business associate by notifying the covered entity of any breach involving unsecured PHI.
There are two notable exceptions to this breach notification rule. If the breach involves PHI encrypted consistent with HIPAA standards, it falls into a breach “safe harbor” zone, and the business associate isn’t required to inform the customer. If the breach involves PHI which is not encrypted to HIPAA standards, it must be reported to the customer unless one of the exceptions to the definition of breach applies.
What is a HIPAA business associate agreement (BAA)?

A HIPAA Business Associate Agreement is a required contract between a HIPAA-covered entity and a business associate providing written, contractual assurance that the business associate will maintain a specific set of standards for the protection of PHI. This agreement defines the parameters for using and disclosing PHI based on the business associate’s working relationship and performed functions. The customer may disclose PHI only as is necessary for the business associate’s performance of contracted duties. The business associate may use or disclose PHI only as allowed by this contract and is directly liable for any violation of HIPAA rules with civil and sometimes criminal penalties resulting.
According to Health and Human Service (HHS) guidelines, a HIPAA BAA must:
- Establish the permitted and required uses and disclosures of PHI by a BA
- Provide that the BA won’t use or disclose PHI except as stated in the BAA
- Require the BA to implement required safeguards to prevent unauthorized use or disclosure of PHI
- Require BA to report breaches to the customer
- Require BA to disclose PHI to satisfy customer’s obligations regarding individual requests for PHI
- Require BA to make PHI records available to Health and Human Services
- Require BA to destroy or return all PHI upon conclusion of work contract
- Require BA to hold any of its subcontractors to the same BA requirements
- Require BA to authorize the termination of the contract by the customer if the BA violates the agreement
Instead of using a HIPAA Business Associate Agreement, can a business associate self-certify or be certified by a third-party?
No – these options aren’t permissible under HIPAA rules. Business associates are required to enter into a BAA with their customers that meet the requirements of 45 CFR 164.504(e).
What does a HIPAA Business Associate Agreement look like?

A basic BAA customarily contains five to seven sections covering different provisions of the agreement. BAAs often include the following sections:
- Definitions: This is often the first section that defines the terms used in the agreement. Examples of these terms would be business associate, covered entity, and HIPAA rules.
- Obligations, activities of BA: This section describes all requirements of the BA.
- Permitted uses and disclosures by BA: Arguably the heart of the agreement, which dives into the particulars of PHI use and disclosure by the BA.
- Provisions for the covered entity to inform BA of privacy practices, restrictions: This section discusses instances of restriction, change, or limitation for which the covered entity may need to notify the BA.
- Permissible requests by the covered entity: This section is optional but can contain examples of acceptable requests by the covered entity.
- Terms and termination: This section covers start and finish dates for agreement, termination for cause, BA obligations in the event of termination, and BA survival protocol.
- Miscellaneous: Another optional section to cover the nature of amendments or handling ambiguity in the agreement.
Penalties for business associates in violation of HIPAA rules
So, what happens when you violate a HIPAA rule as a business associate? When it comes to imposing penalties for business associate violations, the Office of Civil Rights (OCR) can choose financial penalties and/or corrective action plans. Financial penalties come in the form of fines, ranging from $114 to $57,051 per violation. Monetary punishments are tiered based on the offender’s knowledge of the violation.
In addition to these OCR-imposed fines, BA’s are also subject to lawsuits for breaching the terms of their BAA. The bottom line for cloud service providers and all companies in a BA role is clear—you will be held to the letter of HIPAA law with potentially severe penalties, so you need to take HIPAA compliance seriously.
A BAA is Necessary for HIPAA Compliance
HIPAA rules view business associates as an extension of their customers. As a BA, your company will be held to the exact security and privacy standards of your customer, and you will be penalized just as harshly when you fail to adequately protect PHI. After all, what good are HIPPA regulations if they strictly govern covered entities while allowing their business associates to use and disclose PHI without restrictions?
HIPAA compliance is a team effort today—it requires the awareness, commitment, and participation of both covered entities and business associates. A Business Associate Agreement cements this unity of purpose by providing the written assurance that every BA is aware of and actively implements the security and privacy controls required by HIPAA to protect PHI.
So, if you’re a SaaS company or cloud service provider who works with or wants to work with businesses that handle ePHI, we have some advice for you: Take the time to draft a thorough BAA with all your customers. Make sure your team understands and abides by all BAA provisions. Take the lead in following HIPPA rules and safeguarding PHI—your customers will thank you, and your business can look forward to a brighter, compliant future.
What is HIPAA compliance and how can you maintain it? Read about it in this blog.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?