Ransomware Attacks are Inevitable: How to Prepare, Respond and Minimize Fallout

The aftermath of ransomware is often more devastating than the attack itself. On top of a staggering ransom, organizations can experience business disruption, impacted reputation, broken customer trust, forced layoffs, and untold remediation costs. The fallout of a breach may occur over months and years, demotivating employees, business partners, and investors alike. Company security — like diversity, work-life balance, and culture — must become a priority for organizations, with employees acting as stewards of conscientious business practices. Safeguarding your assets signals to customers your respect for their assets and goes a long way toward strengthening partnerships and driving loyalty. Implementing a bare minimum of cybersecurity won’t ward off a ransomware attack. Likely nothing will. Instead, companies should expect an attack and be prepared to respond. Prioritizing the development of a step-by-step Cybersecurity Incident Response Plan gives organizations defined actions to take during a cybersecurity incident. Fighting forward is far more effective than fighting back.
Expect a cyberattack
With cybergangs backed by governments that look to undermine and weaken other nations, there’s an unsettling realization that cyber data is the sought-after resource of future wars. In our recent webinar, Ransomware: Defending Against the Dark Arts of Modern Cyberwarfare, CISO/ThreatRecon Practice Lead at Guidacent (and U.S. Navy Veteran) Drew Blandford-Williams sees clear parallels between ransomware and combat. He says, “You have three different levels of a situation. You’re under fire, in an imminent situation where you’re going to be under fire, or you’re in a situation that could position you for something bad to happen. Drew categorizes those situations as red, yellow, or blue, adding, “Reduce the risk of a compromise from ransomware, so the bad guy is looking somewhere else.”
Ransomware is constantly evolving to meet advancements in software and infrastructure, but hackers continue to use a few tried-and-true tactics because some technology hasn’t caught up. Drew explained,
“We’re still using the same keyboards, mice, and passwords we used when we began using the internet, keeping businesses vulnerable to cyberattacks. If we don’t change how we do things, the way we are exploited isn’t going to change either.”
Email is the ultimate weak point for ransomware and cyberattacks
How do most of these elaborate schemes take place? Through email.
Phishing and email attachments are the most common methods hackers use to deploy ransomware, playing to the human drive to communicate, reply, and engage. Common ploys keep things simple and seem reasonable enough — update your account information, change your password, verify your order, and so on. Nobelium used a popular email marketing program to deploy ransomware in the disastrous SolarWinds breach. Hackers gained illegal access to over a hundred U.S. government agencies, including the U.S. Treasury, the Pentagon, and State Department. While the monetary cost to SolarWinds has been estimated in the billions, associated Fortune 500 companies reported damages averaging $12 million. In April of 2021, the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and National Security Agency (NSA) determined that the Russian Foreign Intelligence Service was behind the ransomware attack. And Chainalysis’ 2022 Crypto Crime Report estimates that 74% of revenue from ransomware in 2021 went to cybercriminals with ties to Russia.
Create a security mindset through learning and engagement
To lower your risk of falling victim to a ransomware attack, first and foremost, educate employees, executives, third parties, and other users about your organization’s systems, processes, and guidelines. Understanding the reasons why helps motivate users to adopt a security mindset.
Educate users about the following:
- How to avoid phishing and malicious email attachments
- Strategies currently in place in your organization to prevent ransomware attacks
- Software, automation, and applications used to defend your organization’s data, systems, and employees against malware
- Zero trust and its critical role in authenticating users of company information
- Security patches and their frequency and effectiveness
- The importance of using the latest versions of software and apps that feature the latest security patches
- Frameworks in place that monitor data exfiltration or other irregularities
- Procedure for reporting suspicious activity
- Response plans in place
- Backups and storage of company assets at high assurance locations and the necessary actions to reinstate data
Along with the above topics, perform periodic data recovery drills to evaluate your organization’s risk management and response to a cyber incident. Be consistent when educating users about methods to identify potential cybersecurity vulnerabilities and intrusion attempts. Keep your team in the loop about things that seem “too technical,” such as deploying Data Loss Prevention (DLP) tools to detect sensitive data exfiltration. End-users may not understand the complex technical aspects of your security measures but will appreciate being engaged candidly and encouraged to have a proactive, collaborative mindset toward company security.
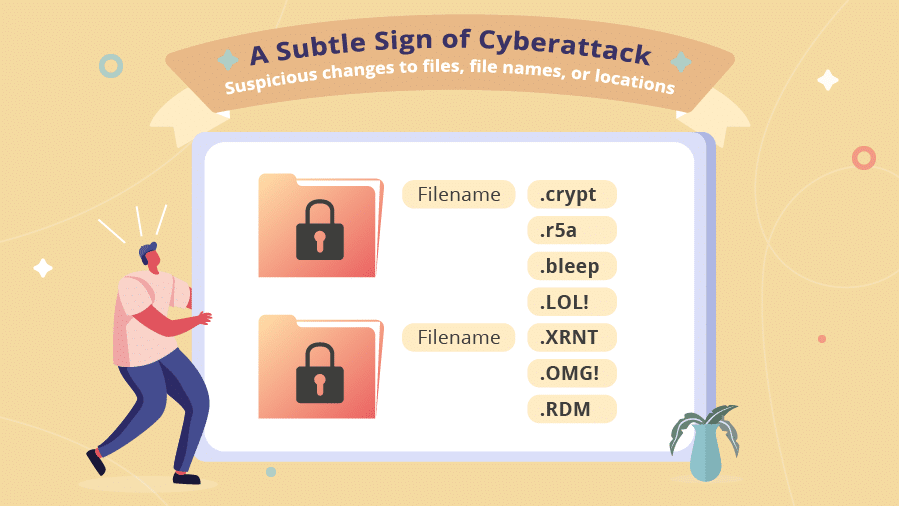
Recognize the subtle signs of cyberattack
When engaging your users, make sure they know the telltale indicators of compromise:
- Inexplicable sluggishness in a personal computer, workstation, or network activity
- Suspicious changes to files, file names, or locations. Typically, all or some of your files will have a file extension appended to the original filename, such as .crypt, .r5a, .bleep, LOL!, XRNT, .OMG!, or .RDM.
- Unauthorized extraction of data
- Unrecognized or otherwise out of place file encryption
- Messages on locked web browsers or desktops demanding payment to unlock your system
- Ransom notes in file directories (usually a .txt file)
- Failed attempts to access network shares or infrastructure
- Suddenly glitchy systems that normally behave properly
- Presence of hacking tools like MimiKatz, Process Explorer, or PC Hunter
Perform regular audits on your assets, systems, data, security, and capabilities to understand what’s normal and what’s not. Consider encrypting SMS messages, emails, databases, passwords, usernames, and additional sensitive information.
Of course, never forget the fundamentals, such as strong passwords, multi-factor authentication, network segmentation, updated systems, and practicing the principles of least privilege.
Conclusion
Convincing those that sign the checks to enhance security is no easy feat. When making your business case to the boss, come prepared with numbers, dollar figures, and percentages. But don’t gloss over the long-term after-effects. Rebuilding systems from the ground up, re-establishing company credibility, employee turnover, and starting over create far more burden than implementing consistent, comprehensive security and following best practices.
The adage rings true: better safe than sorry.
For more insights on preparing for a cyberattack, watch our webinar, Ransomware: Defending Against the Dark Arts of Modern Cyberwarfare.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












