Segregation of Duties: What it is and Why it’s Important

Successfully managing risk across the enterprise is undoubtedly one of the stiffest challenges faced by today’s security professionals. Threats come in many forms and from varying angles, with the risk often raised or lowered by different structural scenarios or behavior patterns within your organization. One such scenario would be allowing one person or group within your organization complete control over a business process or multiple steps within that process.
What would happen if only one of your employees knew the code to deactivate the alarm system? How about if only one software designer had unchecked authority to move code to production? Or worse yet, what if one person was given the responsibility of both handling inventory and recording inventory transactions?
In all of these scenarios, the odds of a negative outcome for your business rise, thereby increasing your organization’s risk level. Giving one person or group too much control within your business’s processes opens the door for unchecked errors and possible fraud–both of which can result in financial loss, reputational damage, and compliance violations.
How can your organization protect itself from the danger of too much responsibility falling to one person and the increased organizational risk this can bring? This article will discuss segregation of duties–an internal control that’s critical in helping today’s organizations minimize risk across the enterprise.
What is segregation of duties?
Segregation of duties (SOD) is a core internal control and an essential component of an effective risk management strategy. In practice, segregation of duties in internal control means sharing the responsibilities of key business processes by distributing the discrete functions of these processes to multiple people and departments, helping to reduce the risk of possible errors and fraud.
Segregation of duties is designed to prevent unilateral actions within an organization’s workflow, which can result in damaging events that would exceed the organization’s risk tolerance. In short, no one person or group should be given control over a process or asset where they have the unchecked power to overlook errors, falsify information (remember Enron?), or attempt theft.
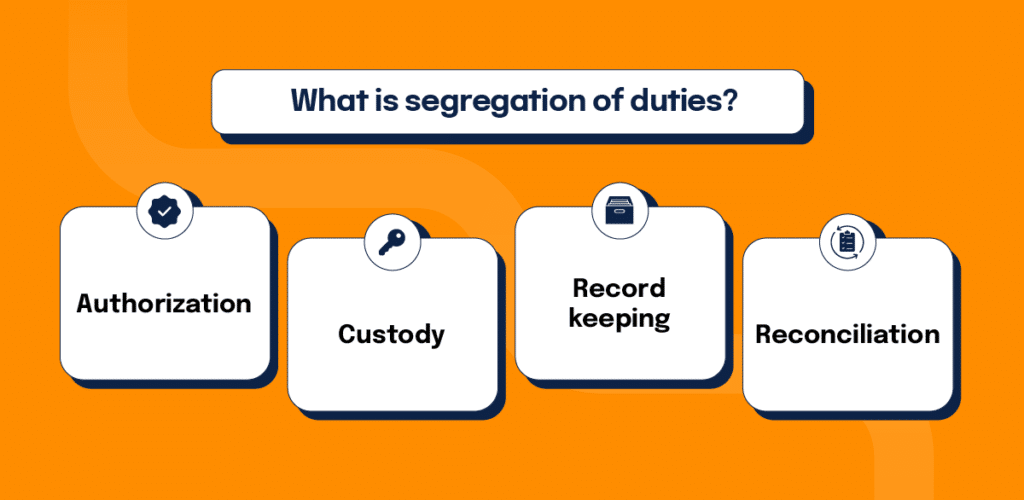
Segregation of duties breaks business-critical tasks into four separate function categories–authorization, custody, recordkeeping, and reconciliation. Ideally, no one person or department holds responsibility in multiple categories–workflow roles should be adequately separated with a system of checks and balances so all positions can regulate each other.
Why is segregation of duties so important?
Including a segregation of duties control component in your risk management strategy helps reduce risks that can be costly to your organization–whether it’s financial, damage to your brand, or the stiff penalties imposed for regulatory infractions. By segregating duties to minimize errors and potential fraud, your organization can remain at or below its desired risk threshold.
Segregation of duties is recommended across the enterprise, but it’s arguably most critical in accounting, cybersecurity, and information technology departments. Significant damage to your organization can result from errors or fraud in all three departments, and organizations failing to implement effective SOD policies in these areas do so at their peril.
Eric McGee, Senior Network Engineer and experienced cybersecurity expert at TRGDatacenters, offers his perspective:
“Segregation of duties (SOD) is one of the most impactful techniques of minimizing risks internally. With segregation of duties, the risk of erroneous or fraudulent actions is minimized as each employee involved has access control and limitations. Also, when a SOD risk management strategy is in place, it’s easy to trace which employee is culpable should a mistake or fraudulent act occur. All organizations should consider making SOD a part of their risk management strategy.”
SOD in risk management
Your people run your processes, and a workflow structure based on the segregation of incompatible duties is essential to keep everyone accurate and honest across departments. Let’s examine how SOD policies can help you manage risk in different areas of your organization.
SOD is a fundamental internal accounting control prohibiting single entities from possessing unchecked power to conceal financial errors or misappropriate assets in their specific role. In other words, it formalizes the division of duties accounting teams rely on to keep financial data accurate and trustworthy. Accounting segregation of duties controls require a thorough analysis of all accounting roles with the segregation of all duties deemed incompatible. For example, someone responsible for inventory custody can’t also oversee transactional recordkeeping regarding inventory.
SOD policies can also help manage risk in information technology by preventing control failures around access permission. By segregating workflow duties, your team ensures the same individual or group isn’t responsible for multiple steps in the access permission process. Imagine the possible chaos and damage if one entity possessed the power to define permission parameters and assign permission to themselves or an outside threat actor.
When it comes to risk management in Governance Risk and Compliance (GRC), effective SOD practices can help reduce innocent employee errors and catch the not-so-innocent fraudulent filings. Both can elevate compliance risk by violating regulations like the Sarbanes Oxley Act of 2002, penalizing companies for filing incorrect financial information capable of misleading investors. External auditors will often perform a segregation of duties audit to verify that these internal controls are designed and operating effectively.
The importance of creating a SOD matrix
We know SOD is a critical internal control for any risk management strategy. We also know SOD requires the separation of incompatible duties–but how should you determine which roles to segregate? And what should you do if your organizational structure divides specific roles making duty segregation impossible?
The answers can be obtained through the creation of a SOD matrix. Traditionally, SOD matrices were created by hand, but modern organizations use software tools to automatically create spreadsheets that are useful for tracking workflow duties and identifying role conflicts. Many organizations develop individual SOD matrices for each critical business process within their workflow.
To successfully segregate incompatible duties, your team must first understand the nature of all processes, roles, and tasks performed by the business. Many organizations create a visual representation of processes, helping map activities and duties to roles within their workflow. Role engineering, which defines position access rights and responsibilities and enterprise resource planning (ERP), can help clarify business roles and duties.
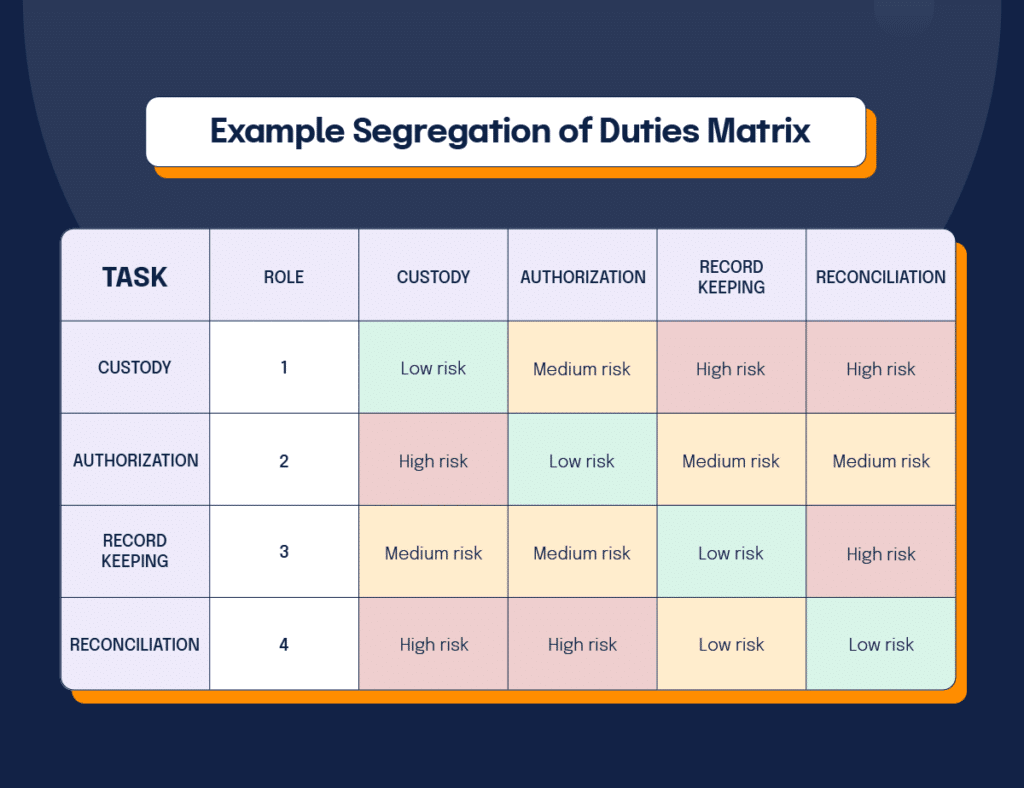
When looking to understand how to apply a SOD matrix to a business process, it’s helpful to use an example. Let’s say we want to examine a purchasing workflow for potential role and duty conflicts. We would create a spreadsheet with process (Purchasing) as the first Y axis category. The next category would be duty (Custody, Authorization, Record-keeping, Reconciliation) followed by procedure (Create requisition, Authorize requisition, Create order, Authorize order) and role (Role 1, Role 2, Role 3, Role 4).
The X-axis would list only the specific procedures (Create requisition, Authorize requisition, Create order, Authorize order). Each user role would be rated low, medium, or high risk related to performing a particular procedure. In this purchasing example, User 1, whose primary duty is requisition creation, would rate as high risk performing requisition authorization. Ideally, each user role matches one procedure in the process workflow to minimize risk. The same approach works for finance and accounting processes. For example, an accounts receivable segregation of duties matrix might map roles like invoicing, cash application, credit memo approval, and write-off authorization across your AR team to make sure no single person can both record and collect payments or approve and process adjustments.
Conflicts arise when individual actors perform duties deemed incompatible by a SOD matrix. These high-risk conflicts occur when activities connected to conflicting duties become associated with the same role or when one actor assumes two conflicting roles, often during a profile shift. Address identified duty conflicts immediately using management tactics including process modification, activity changes, or splitting functions into disparate duties.
What can your team do when conflicts appear, but it’s impractical or costly to segregate specific duties? Compensating controls, often involving secondary authorization or third-party verification audits, can be implemented to reduce the potential vulnerability associated with the ineffective segregation of duties.
What are the risks of not implementing a SOD control today?
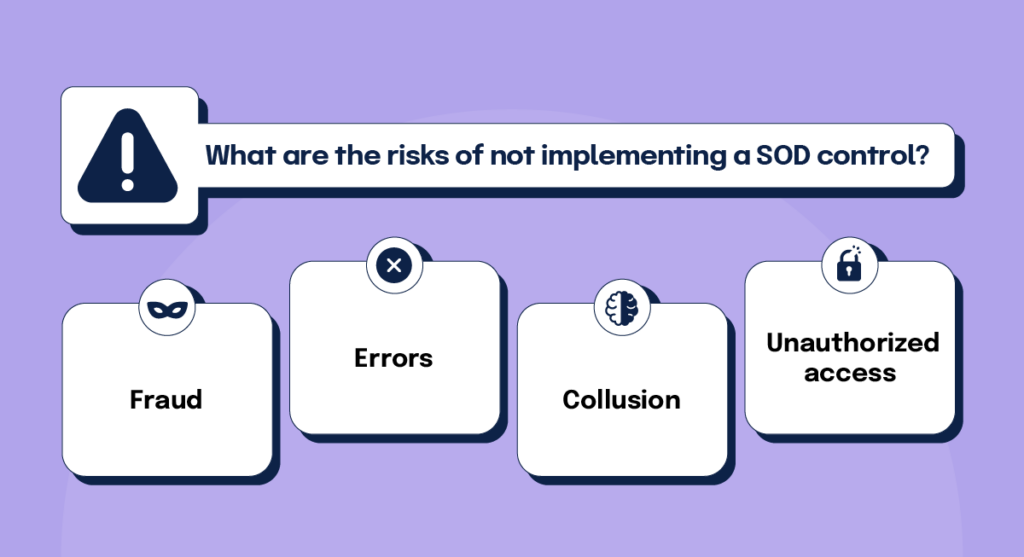
Organizations overlooking the need to implement a SOD control are risking a great deal–starting with the increased possibility of more errors going undetected and opportunities for fraud. You don’t need to look hard to see the potential damage–fraud can result in lost assets and costly reputational damage, while errors can result in compliance violations. Consider this–one violation of the Sarbanes Oxley Act can bring fines of up to one million dollars and ten years imprisonment for anyone knowingly submitting financial reports not in compliance with the regulation.
Many counter that SOD policies create more roles, increase complexity, and slow business processes. However, creating specific, segregated roles has proven its value by reducing errors, minimizing opportunities for insider wrongdoing, and boosting an organization’s overall risk posture. For modern enterprises looking to manage risk successfully, failing to implement effective segregation of duties in internal control is simply a gamble few organizations can afford to take.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?