Many Businesses Have GRC Software, Yet Most Still Struggle to Manage IT Risks Consistently
Even if you haven’t used any Governance, Risk and Compliance (GRC) software yourself, you’re likely familiar with this category of software. As regulations proliferated and the risk landscape became more volatile in the past decade, many organizations found themselves struggling to keep up with regulations and wrestling with how to best protect their organizations from emerging threats.
Recent surveys have found that today’s enterprises are spending more resources on meeting compliance obligations than ever before. GRC software is a broad category of software that helps companies catalog, assess, and mitigate business-specific risks, communicate risks to employees, ensure compliance with policies and regulations, and helps users plan and implement audit programs and tasks.
In Hyperproof’s 2021 IT Compliance Benchmark survey, we found that GRC software adoption among tech companies has reached mainstream status. However, the majority — 65% of all survey respondents — still manage IT risks with an ad-hoc, reactive approach, with siloed processes and disconnected tools. Many survey respondents also reflected that getting through day-to-day risk management and compliance tasks is a slog: one in two survey respondents said they spend at least 50% or more of their total time at work on low-level, administrative tasks.
What’s more, taking an ad-hoc approach isn’t all that effective at mitigating risks: 61% of all survey respondents said that their organization has experienced a data breach or a data privacy violation in the last three years.
In this article, we’ll share the results of the study, which provides new clues on why existing GRC tools haven’t solved some of the biggest IT risk management and compliance challenges businesses face today. We’ll also provide three practical steps any business can take to start managing IT risks in a more consistent and effective manner.
What it takes to manage IT risks consistently
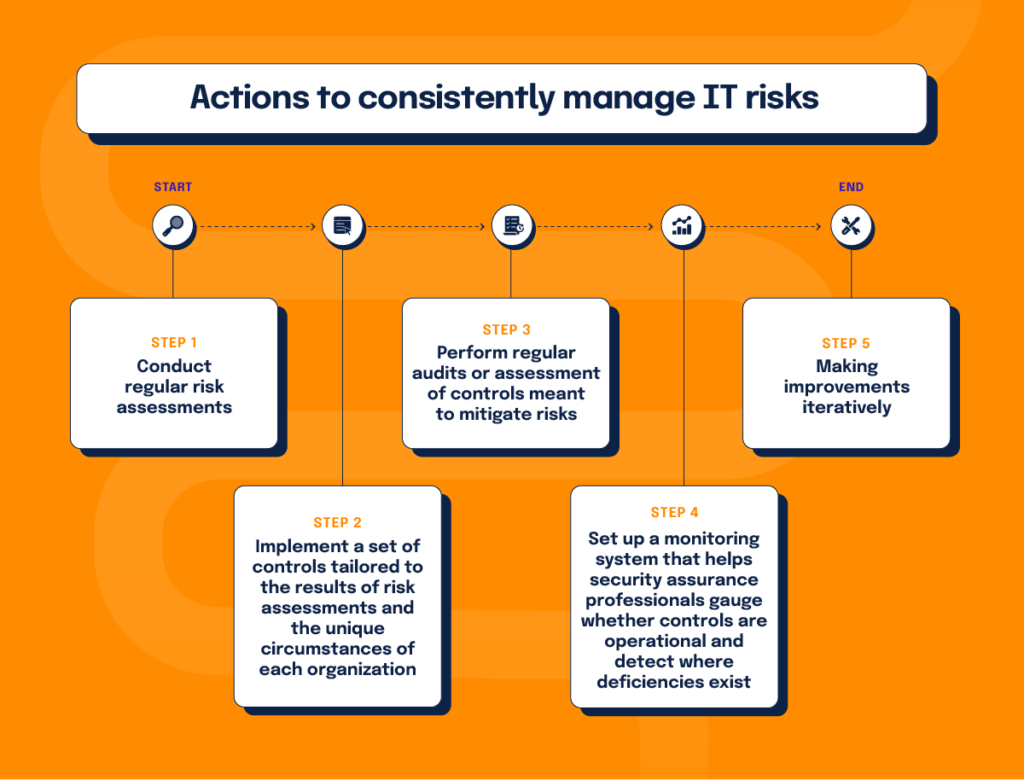
Governance, Risk and Compliance experts at organizations like NIST and ISO and ISACA generally agree that a rigorous approach to risk management requires organizations to take the following actions:
- Conduct regular risk assessments. The ability to accurately identify and assess risks facing an organization is the starting point of any effective risk management program.
- Implement a set of controls tailored to the results of risk assessments and the unique circumstances of each organization. Meanwhile, keep regulatory requirements in mind and ensure that controls put in place help the organization stay in compliance with the regulatory requirements it is subject to.
- Perform regular audits or assessment of controls meant to mitigate risks.
- Set up a monitoring system that helps security assurance professionals gauge whether controls are operational and detect where deficiencies exist.
- Making improvements iteratively. Take a disciplined approach to uncovering deficiencies within the organization’s environment and ensure that responsible parties remediate the issues in a timely manner.
Although the risk management process is easy to articulate, doing each step well requires stakeholders to gather a significant amount of information at every stage of the process. And that information must reach the right people in time so they can act upon it in a timely manner. For instance, it’s not enough to just know what your organization’s high risk areas are. To understand how well existing risks are being managed, you also need to know whether specific risk mitigation processes and activities already exist in your organization and whether those processes are effective. To get answers for a single risk, you may need to talk to a dozen of individuals within your organization and look through three or four different systems.
In Hyperproof’s 2021 IT Compliance Benchmark study, we found that although many respondents already have GRC software in their organization, their ability to gather relevant risk and compliance information is limited. Further, organizations’ risk management workflows are often disjointed and siloed, which inhibits the flow of relevant information to the right people and keeps people from being able to prioritize risk actions appropriately.
Study results in detail
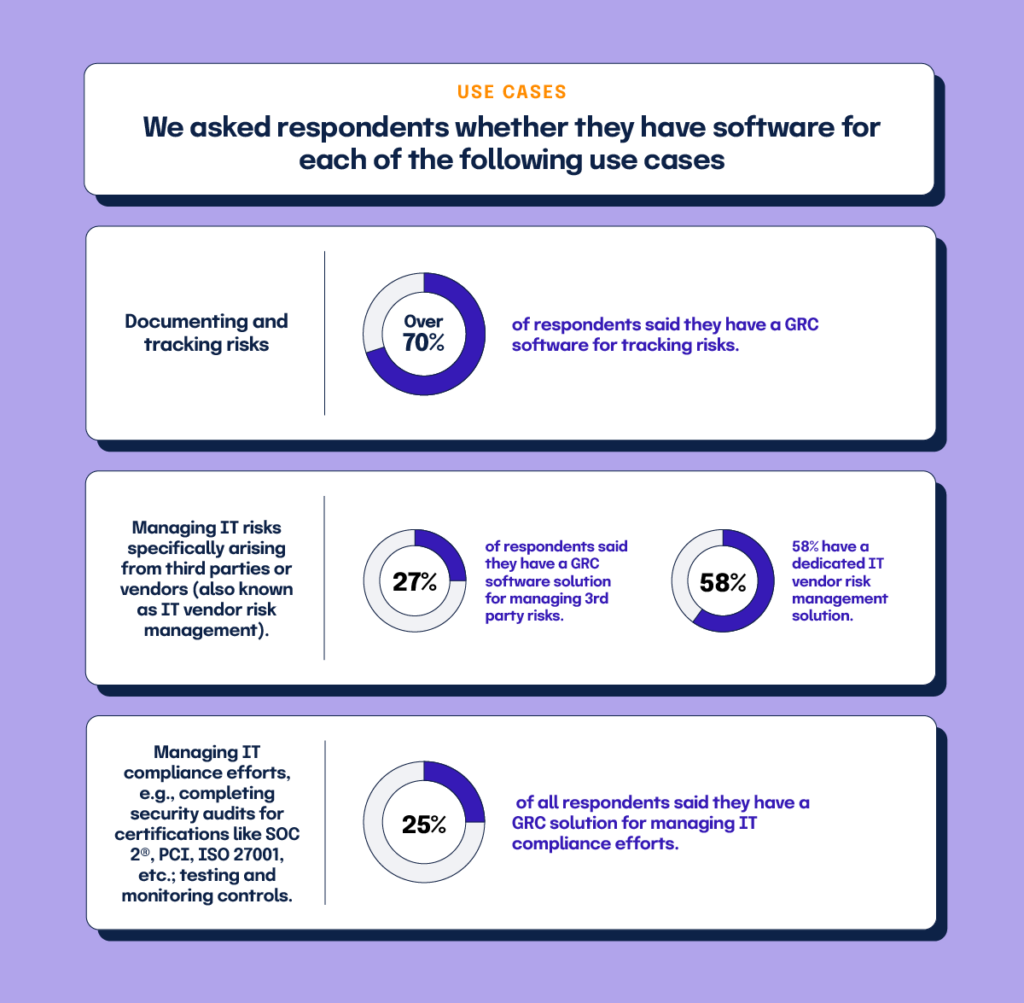
In this study, we asked respondents whether they have software for each of the following three use cases.
- Documenting and tracking risks at an organizational level.
The options provided were: 1) Spreadsheets, 2) Standalone risk management software, 3) Risk management module in a cloud-based GRC software, 4) Risk management module in an on-prem GRC software, 5) Custom-built software, or 6) “We don’t have a tool”.
What we found: Over 70% of respondents said they have a GRC software for tracking risks.
- Managing IT risks specifically arising from third parties or vendors (also known as IT vendor risk management).
The options provided were: 1) Spreadsheets, 2) Forms/questionnaires made in Microsoft Office/Google Suite, 3) Dedicated IT vendor risk management software, 4) GRC software solution, 5) Ticketing/task management system, or 6) “We don’t have a tool”
What we found: 27% of respondents said they have a GRC software solution for managing 3rd party risks. 58% have a dedicated IT vendor risk management solution.
- Managing IT compliance efforts, e.g., completing security audits for certifications like SOC 2®, PCI, ISO 27001, etc.; testing and monitoring controls.
The options provided were: 1) Spreadsheets, Word docs, file storage systems 2) Software purpose built for managing IT compliance operations; 3) The compliance module in a cloud-based GRC solution; 4) The compliance module in an on-prem GRC solution; 5) Custom-built software, or 6) “We don’t have a tool”.
What we found: 25% of all respondents said they have a GRC solution for managing IT compliance efforts.
Yet, 83% of all survey respondents also said that they plan to evaluate and purchase new tools in 2021 to streamline and automate their IT risk management and compliance processes. The data suggests that organizations’ existing GRC tools are not fully meeting their needs.
How well are our risks managed at present? Does anyone really know?
To gauge whether GRC tools are helping organizations manage IT risks effectively, we asked respondents a series of questions to see how well they’re executing critical IT risk management tasks and where they are struggling.
We found that about half of all respondents struggle to understand how well existing risks are being managed at the present:
- 44% of respondents said they’re not doing a good job of identifying existing controls.
- One in two respondents said they’re not doing a good job of aligning controls with risks.
- One in two respondents said they have trouble validating controls against standard controls in compliance frameworks (e.g. NIST, ISO).
- 44% of respondents said they’re not doing a good job of monitoring and testing controls meant to mitigate IT risks.
- 42% said they’re not doing a good job of capturing, tracking, and reporting control deficiencies.
- 48% said they’re not doing a good job of reviewing controls and remediating control deficiencies
Gathering relevant risk information is incredibly tedious

To better understand why certain risk management tasks are so challenging, we asked two questions:
- Do people have access to relevant risk information to make risk decisions?
- Can people get their work done efficiently? Or are some tasks so tedious that people end up skipping them?
From our survey, we found that both factors – an inability to access relevant risk information quickly and an inability to get work done efficiently – were barriers that held risk and compliance professionals back. We can infer from this data that existing GRC tools haven’t made these key tasks easy enough.
Here are the results in greater detail.
When it comes to preparing for audits, what tasks do you find to be tedious/take way longer than you’d like?
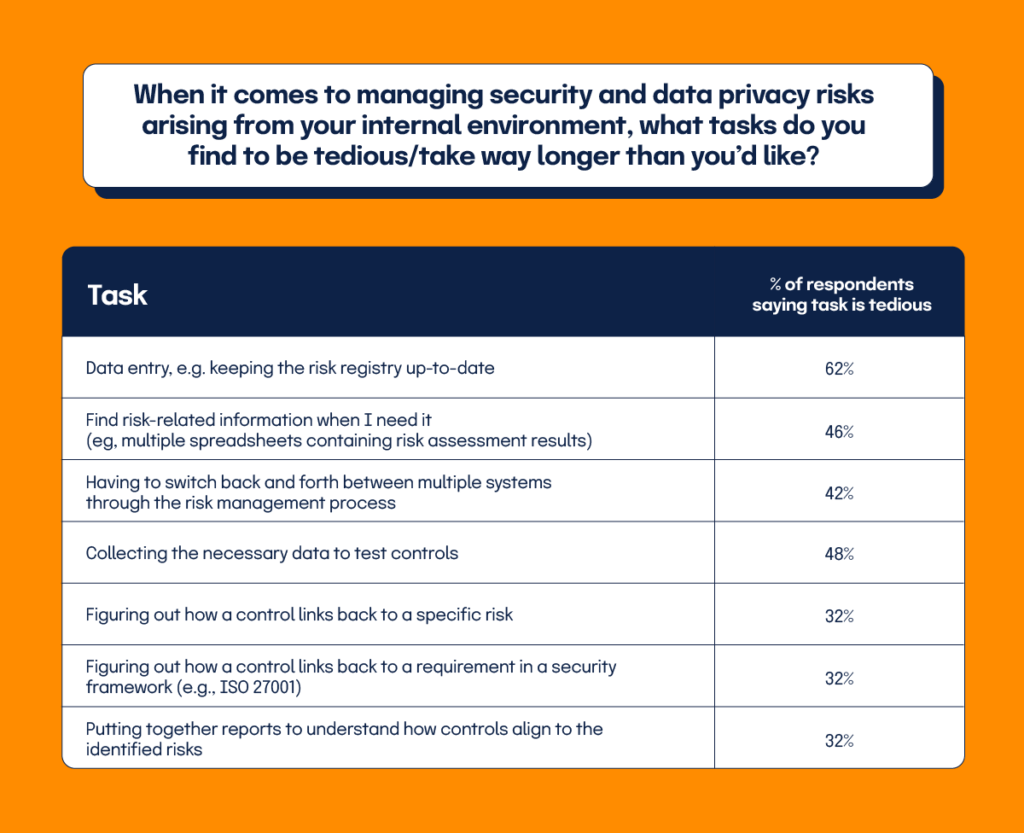
When it comes to preparing for audits, what tasks do you find to be tedious/take way longer than you’d like?

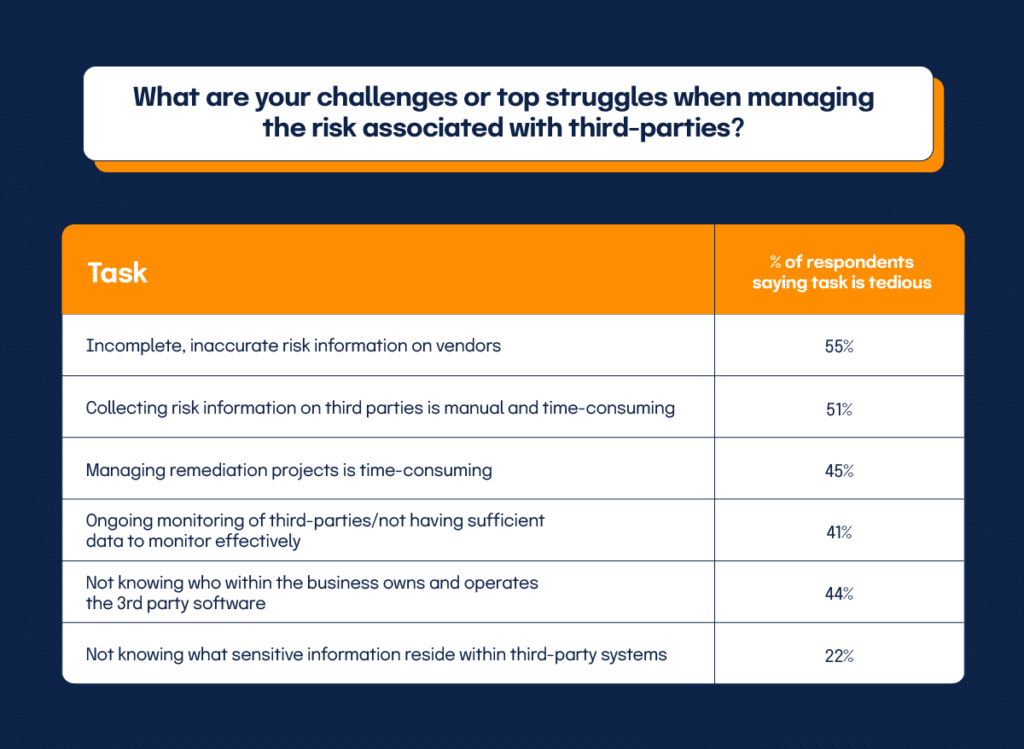
What are your challenges or top struggles when managing the risk associated with third-parties?
Further, when we asked people to estimate how much of their team’s time is spent on repetitive/administrative tasks that aren’t a good use of their time, one out of two respondents said their teams spend 50% or more of their total time on administrative tasks.
Based on the survey results, we found that the typical tech company has some sort of software built to help them with their governance, risk, and compliance effort. Yet, they still struggle to manage risks in a consistent way because their GRC software hasn’t made important tasks easy enough.
What’s the path forward?
How can you stand out from the pack and help your organization become really effective at managing risks? To achieve this, we recommend you approach this problem in three parts:
- See better
- Work faster
- Improve iteratively
See better
Recommendation: Map your risk treatment (and compliance) activities back to identified risks.
Many surveyed organizations have only a vague idea of how well their existing risks are managed because risk information resides in multiple, disparate systems and only a portion of the information is visible to risk leaders and other key decision-makers.
If you want to do better than those organizations, you’ll need to track your risks, regulatory requirements, and risk management and compliance activities in a system that allows you to easily map the risk treatment activities back to the identified risks. By doing so, you’ll be able to see where your risk management practices are strong and where you need improvement. From there, you can start to scope out the work ahead.
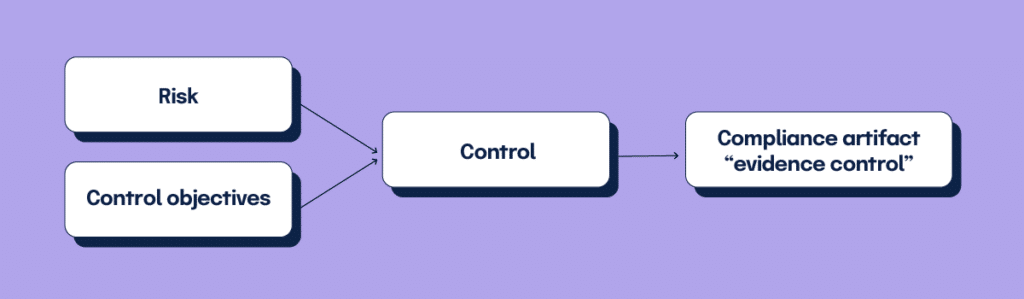
This mapping process may seem simple, but it’s quite difficult to do without a dedicated platform that serves as an enterprise-wide repository for all risks, controls, and compliance artifacts. While many GRC software platforms are intended to help with this mapping process, completing the process in some GRC software is quite cumbersome. The real purpose of using a GRC software is to help your organization effectively manage the risks that matter to your business. If it takes days or weeks just to get all of your existing processes ported into a GRC tool, the payoff is diminished.
When you look for software to help with managing IT risks, ease of use matters. If you can get past the data entry phase in minutes (e.g., import risks and existing controls into the tool), you can focus your effort on more important tasks, like understanding how well existing controls work and identifying new controls that need to be developed. A useful software solution should be intuitive to use, customizable to your workflows and help you eliminate any repetitive work or tedious work-arounds you had to deploy previously.
Recommendation: Make the work visible
Once you get an understanding of how well existing risks are managed and where you need better risk treatment plans, it’s time to define the specific work that needs to be done and who will be responsible. For instance, have you defined the cadence for internal and external audit activities? For high risk areas, what controls need to be implemented, reviewed, and tested? Who’s responsible for critical tasks and how will your team monitor that? And finally, how can relevant parties quickly see if there’s a potential issue, like a control not being tested on schedule or if someone failed to remediate a key finding?
When you understand what needs to be done, you can begin to estimate the workload and resources required to meet those objectives and design the allocation of key tasks within, and outside of, the security assurance and compliance function. Knowing the schedule, and being able to stay ahead of it, is key. Although this type of planning can be done in different ways, it’s easiest if you can plan out your project in the same system where all of your risk and compliance information is housed.
It’s Time to Evolve Your Approach to Security Assurance.

Work faster
Streamline inefficient workflows, starting with evidence collection.
The less time you can spend on low-level compliance tasks, the more time you can dedicate to strategic risk management. Start with a process that’s particularly time-intensive for you today, probably evidence collection and management. By defining a process for collecting and reviewing evidence — and automating it with technology, you can save a significant amount of time and minimize the risk of control failures.
When defining your evidence collection process, it’s important to consider the following:
- Evidence should be mapped to controls.
- What types of evidence are needed to test whether this control is functional?
- What’s the appropriate frequency for collecting that evidence?
- How long do I consider the evidence to be “fresh” or valid?
- What IT/business system does the evidence reside in?
- Who is responsible for submitting the evidence?
- Who needs to review that evidence?
By keeping all this contextual information alongside each piece of evidence in a system of record for risks, controls, and evidence, you can easily reference this information for future audits — saving time and money.
With dedicated software like Hyperproof, you can automatically collect evidence of compliance and risk mitigation activities. By keeping evidence organized (i.e., linked to relevant controls and risks) in a single platform, getting through audits becomes much easier. An auditor can see the complete document version history, understand what you’ve done, and see how evidence has changed over time. This reduces the back and forth you’d normally have with your auditor, saving everyone time and money.
Related post: Evidence Collection: A Key Pillar of an Effective Compliance Program
Improve iteratively
Cybersecurity, compliance, and risk professionals realize that their work is never done. Managing risks consistently means that we choose to work iteratively and make improvements continuously to our controls environment as our businesses grow and evolve. It means that we take action promptly when an issue is discovered.
To make iterative work possible, you need a tool that can help you track issues and manage remediation tasks in context of your risks and your compliance activities. Context is important, because when people have to switch back and forth between multiple tools, it’s too easy for a task to accidentally get dropped or forgotten.
Again, Hyperproof can help in this domain. Hyperproof comes with a native task and issues management system – all tasks can be created from existing controls or risks. Hyperproof also works seamlessly with existing project management systems including Jira and Confluence. Compliance managers can create new tasks in Hyperproof and control owners can continue to use their preferred tool of choice to complete the tasks.
Conclusion
By putting this See better, work faster, and improve iteratively framework into place and using a compliance operations platform such as Hyperproof, you can efficiently gather the relevant information you need to understand the current state of risks and security assurance activities, note what needs to happen next, assign work to stakeholders across your organization, and keep everyone moving in the same direction. By taking a more disciplined, rigorous approach to managing risks, your organization will be in a much better position to seize new opportunities and minimize the impact of turbulence.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












