The Growing Importance of Security Assurance (And What It Means to Be Good at Compliance Operations)

Living through a global pandemic has made life tough for every human on the planet—some far more than others. We saw unprecedented losses in lives, jobs, and education in the past year. In the realm of security assurance, information security, compliance professionals, and audit executives faced challenges in 2020 they’ve never encountered in their careers.
Top issues that impacted security assurance in 2020
In March 2020, millions of workers were sent to work from home by their employers who didn’t have a plan for how to maintain cybersecurity and data privacy under a radically different work environment. When workers’ use of technology and devices shifted, security and privacy controls that were set up for physical offices suddenly became irrelevant. CISOs, IT security, and compliance professionals were challenged with questions like:
How do we identify all the new assets tapping into our corporate network and data? What’s the right mix of policy and training for employees to think carefully about security, versus security controls that block new devices?
In 2020, we saw cyber attackers refine their methods to take advantage of the COVID-19 pandemic and the adoption of new technologies used for remote work. In fact, online crimes reported to the FBI’s Internet Crime Complaint Center (IC3) have nearly quadrupled since the beginning of the COVID-19 pandemic. By end of 2020, a failure to figure out how to support remote work without exposing sensitive information led to nearly 25% of organizations paying unexpected costs to address cybersecurity breaches and malware infections.
In 2020, information security, compliance, and audit professionals had more external threats to address, new internal uncertainties to resolve, and in many cases, fewer resources to do the work. While these teams had to step up to promptly address new threats due to the COVID-19 crisis (e.g., establish secure connections for newly remote workforces, monitor spiking threat levels, prevent new network threats that target workers), they still had to stay on top of core compliance duties they’ve always had. Audits, regulatory filings, and ensuring compliance with statutory and contractual obligations—those tasks still need to be done. And there’s the fact that employees will still try new software and IT systems anyway, with and without proper governance.
After making the shift to mass remote work this year, many organizations became highly sensitized to the security and privacy risks posed by remote-work supportive technologies (e.g., tele-conferencing systems). Companies have realized that when SaaS providers don’t have solid security controls within and around their systems, attackers can penetrate the SaaS providers’ IT systems and then use the vendor to launch an attack against them.
As more organizations are gaining a deeper understanding of technology risks posed by their vendors, they’ve shifted from a “trust and verify” model to a zero trust model when dealing with IT vendors. In this context, zero trust means that viewing third-party software vendors and business service providers as potential attack vectors—and only trusting a third party with your organization’s sensitive information after qualified auditors have had the opportunity to audit the third-party’s security controls and verify their security and compliance posture.
One of the biggest examples of this shift to a zero trust approach to B2B relationships comes from the Department of Defense. In the past few years, the loss and theft of government data became increasingly costly. In the fall of 2020, the DOD rolled out a new cybersecurity requirement for all DOD contractors and suppliers called the Cybersecurity Maturity Model Certification (CMMC). Instead of accepting companies’ self-assessment on security questions as valid, the DOD will only conduct business with contractors who have passed third-party audits for the appropriate CMMC level going forward.
At this time you should expect prospective customers to view your business as potentially dangerous until proven otherwise. Some sophisticated organizations have even put risk- and security-related provisions into their contracts with vendors, including the right to audit the vendor’s security and privacy controls and guarantees on sub-contractors.
We saw this trend bear out in the data. Research by Coalfire in 2020 found that for the majority of organizations, growing compliance obligations are now consuming 40% or more of IT security budgets. And 58% of companies view compliance as a material barrier to entering new markets. Here at Hyperproof, we found a similar pattern in our own survey in 2019: organizations are spending too much time demonstrating compliance and maintaining their compliance posture.
The work ahead for security assurance professionals
Whenever there is a major event (e.g., COVID-19) or a major shift in people’s technology usage patterns, cyber attackers will exploit the circumstances. With this in mind, we expect remote workers to continue to be the focus of cybercriminals in 2021. As businesses adopt new technology in their quest to compete and innovate, and more work gets done over the Internet, the risk of data exposure will continue to grow.
Meanwhile, we expect regulators to be quite active in enforcing data privacy regulations. In fact, this trend is already here as evidenced by the 300 fines EU data protection agencies handed out for GDPR violations (as of December 2020). The Information Commissioner’s Office (ICO)—the independent regulatory office in charge of upholding information rights in the interest of the public and the GDPR enforcement body in the UK—has slapped seven and eight figure fines on corporations such as TicketMaster and Marriott International for failing to keep their customers’ personal data safe.
Data privacy regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) hold businesses responsible not only for internal mistakes but also the data privacy and security slip-ups of their vendors. The CCPA also gives consumers private right of action to hold violating businesses responsible. Although the U.S. doesn’t have a national privacy law yet, multiple bills have been introduced in the past two years and both parties agree on the broad strokes (e.g. SAFE DATA ACT, U.S. Consumer Data Protection Act, Filter Bubble Transparency Act). The signs show the next term of Congress may pass a nation-wide data privacy and security law that rivals the GDPR.
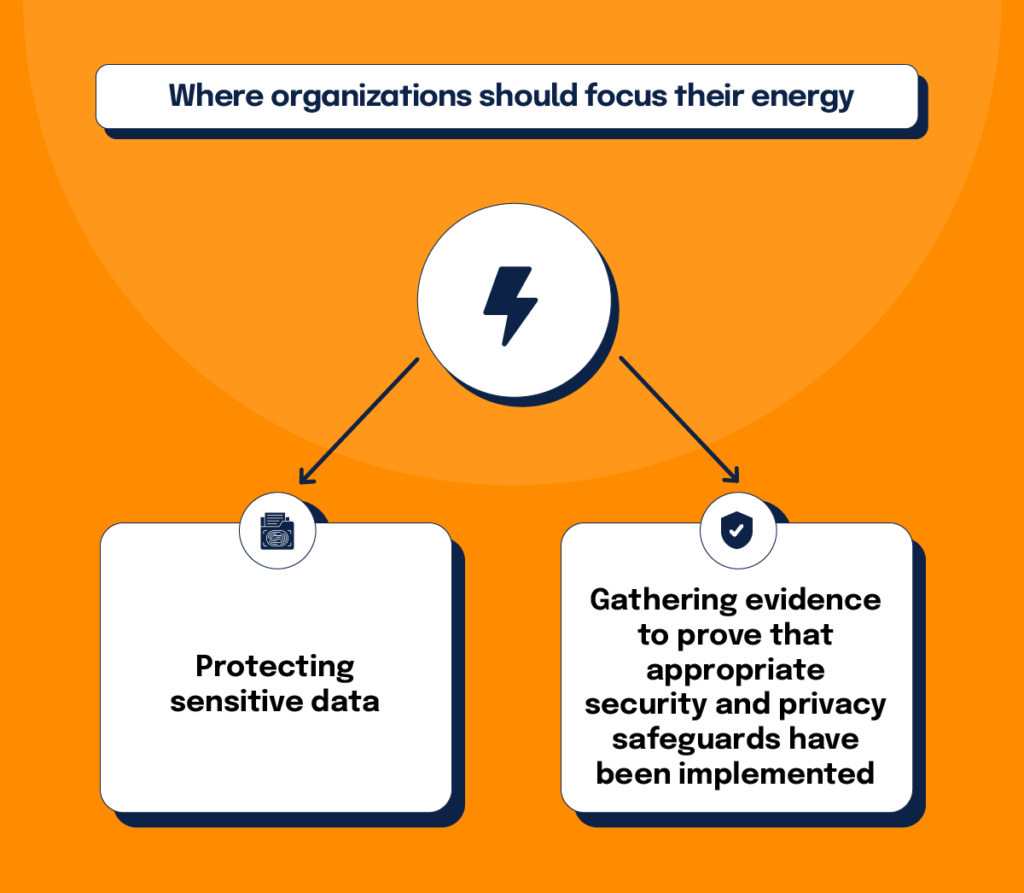
Keeping these trends in mind, organizations need to focus their energy on 1) protecting sensitive data and 2) gathering evidence to prove that appropriate security and privacy safeguards have been implemented.
As a security assurance leader, you need to be able to prove to your business leaders and customers that your organization has taken a thoughtful and diligent approach to protect the valuable data in your possession. And those data protection efforts need to cover the third parties that have access to your organization’s (and your customers’) data. Meanwhile, it would be wise to assume that security incidents are unavoidable. As such, the best defense is to take a disciplined, proactive approach to managing IT risks. That means setting up workflows and checkpoints that allow security and compliance professionals to identify issues early and respond promptly to incidents to minimize further damages.
What does taking a disciplined approach to IT risk management look like in practice?
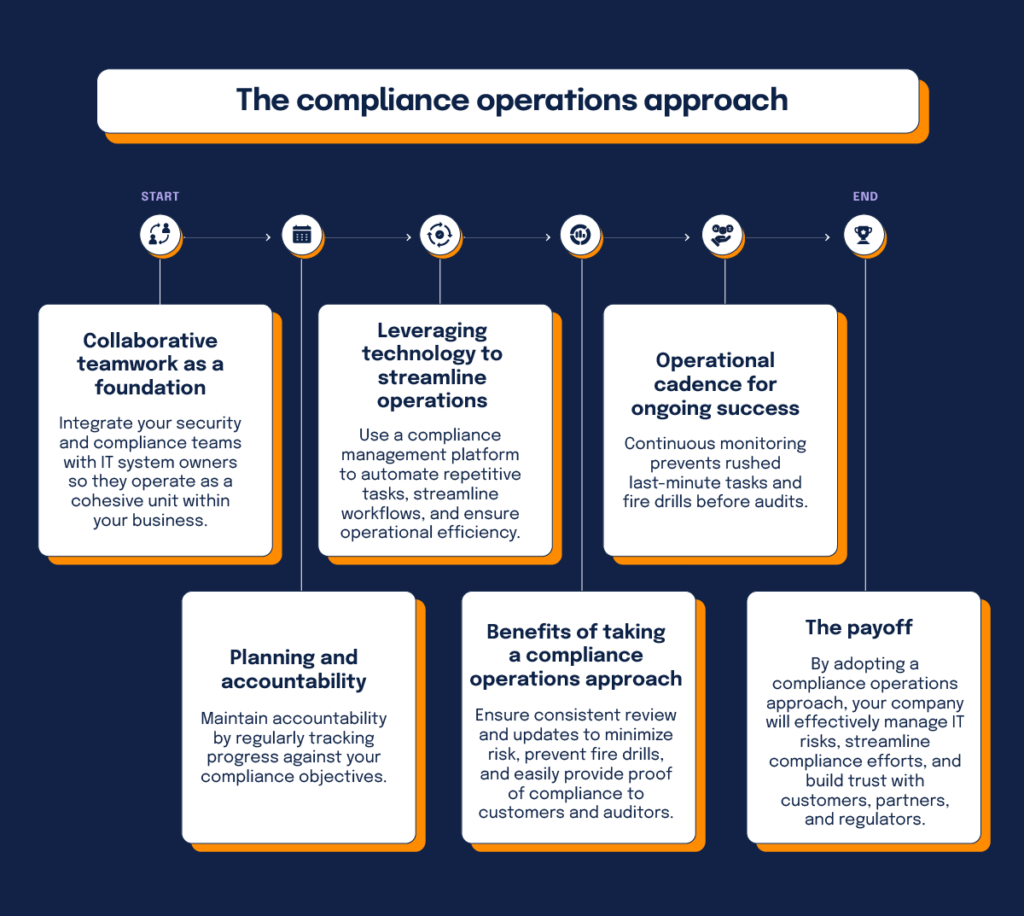
First and foremost, it means that security and compliance teams and the “owners” of key IT systems work together as an operating team, embedded within the business. Like all great operational teams, this team understands their key objectives and responsibilities and takes them seriously. The team plans out their work methodically and keeps each other accountable for getting key tasks done consistently and on time (e.g. documenting risks, aligning controls to risks, collecting evidence to reviewing controls, etc.).
To keep things on track, the team uses a technology platform to manage their day-to-day operational activities—systems that help teams plan their work and execute work in a streamlined way (including automating repetitive tasks).
Like any top operations team, security and compliance teams use up-to-date information to gauge their progress and prioritize where to focus their energy. They regularly review up-to-date information about their security assurance/ compliance activities in order to assess the efficacy of controls built to mitigate IT risks, plan remediation efforts, and identify pending tasks for upcoming audits. Here at Hyperproof, we call this mode of working Compliance Operations, because it gets security and compliance professionals into an operational cadence.
The advantages of taking an operational approach to security assurance compared to a traditional approach (e.g., rushing to check controls, collect evidence and fix controls right before an audit) are three-fold.
First, by reviewing things on a cadence, you minimize the chances of leaving an important risk-mitigation task undone.
Second, when a team reviews controls and collects evidence on an ongoing basis, no one needs to panic or go into fire-drill mode right before an audit. And finally, by keeping track of all compliance activities in a single platform, it becomes easy to prove to customers, auditors, and regulators that an organization has been operating in a secure and compliant way all along.
Ultimately, being good at security compliance operations means that you are good at managing IT risks on an ongoing basis and you can efficiently prove your security and compliance posture to customers, partners, and stakeholders. All of this will ultimately help you win and retain more customers and be more competitive as a company.
Resources for security compliance operations

Over the next few weeks, you can expect to find on our website new resources — from articles to webinars — on how you can get better at operationalizing security assurance and compliance activities. Sign up for our newsletter to stay up-to-date on when new resources become available.
Meanwhile, check out our guide on compliance operations methodology.
It’s Time to Evolve Your Approach to Security Assurance

See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?