Transforming Your IT Risk Management from Reactive to Proactive in 7 Steps
As a seasoned IT risk management professional, you already know that staying on top of security is a constant battle. You probably also know that managing IT risks proactively and consistently is incredibly difficult to do. In Hyperproof’s 2022 IT Compliance Benchmark Survey (completed by 1,014 IT security assurance/compliance professionals), we found that 60% of global tech companies are still managing IT risks in an ad-hoc way, in siloed departments, with disparate processes and multiple disconnected tools.
What’s more, three in five respondents said that they spend 40 percent or more of their time at work on low-level administrative tasks when it comes to managing IT risks and compliance. In the survey, we specifically asked people, “When it comes to preparing for and executing audits, what tasks do you find to be tedious/take longer than you’d like?”
Turns out that compliance professionals find two types of activities to be especially tedious: evidence collection and management, and working with internal stakeholders who need to assist in the audit prep process.
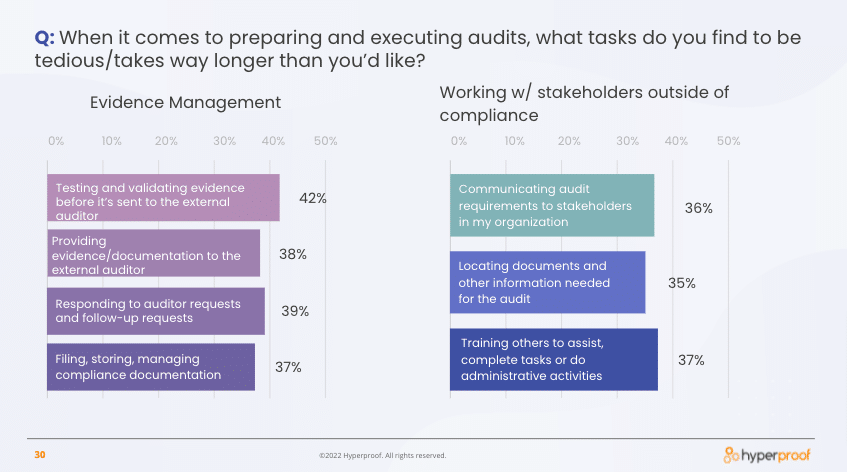
When compliance professionals spend so much of their time just trying to prepare for the upcoming audit, it’s difficult to enough time to focus on improving the organization’s capabilities around managing risks.
All of this ultimately results in unwanted risk exposure: 63% of all surveyed said their organization has experienced a data breach that led to a compromise of regulated data in the past 24 months.
If these statistics resonate with you, and if you want to get a better handle on your information security compliance program, we’re here to help. In this article, we’ll tell you about an operating model and methodology we’re calling “Compliance Operations” (or “ComOps” for short) you can use to get things into better shape. Related: Cybersecurity Best Practices
What is compliance operations?

Compliance Operations is an operating model and a methodology that recognizes that managing information security compliance and security assurance programs consistently and on a day-to-day basis is a critical component of effective IT risk management. It operates on the understanding that cyber risks can change by the minute, regulatory volatility isn’t going away, and zero trust is now the default security (and B2B purchase) model. As such, compliance and security assurance professionals need to apply more rigor and discipline to their day-to-day activities. The Compliance Operations methodology provides a way for organizations to manage IT risks in a more disciplined, proactive manner and efficiently prove to their customers that they can keep sensitive customer data safe.
Want to become an expert in compliance operations methodology?

Seven compliance operations principles
1. Break down information silos across IT risk management processes
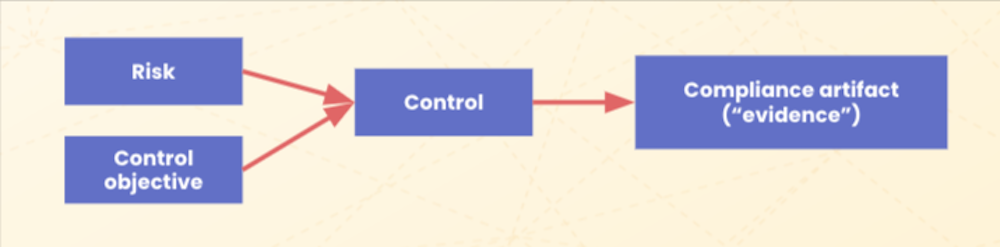
Connecting disparate information silos across the IT risk management processes– so risks, security requirements, and the state of existing internal controls are well understood — has to be the first step if an organization wants to manage IT risks in an agile, proactive way. All of your company’s risks, control objectives and requirements, controls, and compliance artifacts can be documented in Hyperproof and these information objects can be mapped.
2. Establish shared responsibility for security and compliance
If an organization wants to be consistent at mitigating risks, their information security compliance teams and business stakeholders need to share responsibility for maintaining security and compliance. This is a departure from what we see today, where many business process owners/stakeholders view compliance as something that happens off to the side.
Business process owners from HR, Finance, Engineering, and IT are operating IT systems and processes that can affect data security, integrity, and privacy. These business stakeholders and operators purchase new technology in order to improve their own productivity and to deliver better customer experiences. When new technology is purchased or when a new business process is created, new risks to information may be introduced. It’s important for the infosec compliance team to understand their business, why these business processes exist, what tools are used in these business processes, and why things are done a certain way — so they can understand the security and compliance implications.
Compliance and business stakeholders (and product engineers) should work together to ensure that IT systems are configured and used in ways that advance business objectives and adhere to internal security and regulatory standards. It’s important that the compliance team knows when business process and technology changes happen. The compliance team should document what the “proper” processes are so that what’s happening can be reviewed against the established standard. They should make this data available to the business process owners. The business process owner is accountable to ensure that the right processes or procedures are followed as they are operating their systems through the course of normal business.
3. Break down work into small increments and work iteratively
Compliance work can feel really intimidating if you think about everything that needs to be done all at once. But if you take a pragmatic and incremental approach, the work becomes much more manageable. A pragmatic approach is one that starts with your organization’s business needs in mind. For instance, what are the most critical risks within your business that need to be mitigated? Which risks need better mitigation controls? What’s the next audit that’s coming up? Is there a new security regulation or standard your business has to become compliant with in the coming months in order to do business with certain customer segments?
Knowing your current state and your business priorities, you can start to set realistic, achievable milestones and identify the most important set of tasks that need to be completed in the near term.
If you take a disciplined approach to setting incremental goals in service of improving your security and compliance posture over time, it becomes much easier to figure out the workloads and resources required to meet your objectives and allocate tasks to individuals within, and outside of, the security and compliance function.
Rather than reacting to the demands from other stakeholders, you choose to look ahead and figure out who needs to do what, and by when. For instance, what’s the cadence for internal and external audit activities? When do controls need to be implemented, reviewed, and tested? Who’s responsible for critical tasks and how do we monitor that? And finally, how can we quickly see if there’s a potential issue, like a control not being tested on schedule or if we failed to remediate a key finding?
4. Define a process for collecting and reviewing evidence

If you don’t have access to up-to-date evidence, you can’t assess whether controls you’ve implemented are functioning properly or not, which may leave a key IT system exposed. Additionally, in order to pass an independent audit, you’ll need to supply your auditors with the correct compliance artifacts.
As we mentioned earlier, we found in our 2022 IT Compliance Benchmark Survey that collecting evidence tends to be so tedious and time-consuming that it holds security assurance professionals back from tackling more strategic tasks.
By having a clearly defined process for collecting and reviewing evidence, you can save a significant amount of time, money, and frustration and minimize the risk of control failures.
When defining your evidence collection process, it’s important to consider the following:
- Evidence should be mapped to controls
- What types of evidence are needed to test whether this control is functional?
- What’s the appropriate frequency for collecting that evidence?
- How long do I consider the evidence to be “fresh” or valid?
- What IT/business system does the evidence reside in?
- Who is responsible for submitting the evidence?
- Who needs to review that evidence?
By keeping all this contextual information alongside each piece of evidence in a system of record, you can easily reference this information for future audits, saving time and money.
5. Automate processes to make them more efficient (and support a more efficient operating environment for the entire organization)
When security compliance teams spend much of their time on manual repetitive tasks, they’re left with little time to focus on other important tasks aimed at improving security and resiliency (e.g., testing controls on high risk areas, talking to business units to understand what’s changing in the business and how those changes may create new risks or amplify existing risks). Manual, repetitive tasks, such as evidence collection, controls monitoring, and reporting, should be automated.
Further, at the controls level, it’s easy to become “over-controlled” as compliance professionals try to meet different but somewhat similar framework requirements. This issue has driven the move towards unified controls frameworks. Automation and good processes can help us get there and remain there in light of new or changing requirements.
6. Have a reporting and monitoring system in place to support ongoing improvements
Security assurance/IT compliance work is an iterative process. Controls can quickly become obsolete when a change occurs in an organization, such as when an existing IT system is retired and a new one is implemented. To achieve continuous compliance, every organization needs to have a reporting and monitoring system that provides real-time insight into the status of internal controls, risks, audits, and automatic flagging of issues that need attention. For instance, one report should help you identify which controls need review because evidence isn’t fresh anymore. You should have an easy way to see which security objectives aren’t met yet because controls haven’t been implemented or tested. There should be a way to track issues and tasks so that those involved in compliance know what they need to do next.
7. Make iterative improvements
Security compliance work is never done. As your organization grows, you’ll face new compliance requirements and new risks that need to be mitigated. It’s important to look at your compliance program as a living entity and make incremental improvements on a continuous basis.
Advantages of taking an operational approach to compliance activities

The advantages of taking an operational approach, as opposed to a traditional approach (e.g., rushing to check controls, collect evidence, and fix controls right before an audit) are three-fold.
First, by reviewing things and making improvements continuously, you effectively minimize the chances of experiencing security and compliance lapses and of leaving risks unaddressed.
When your team can easily collect evidence on an ongoing basis, no one needs to scramble or go into fire-drill mode right before an audit, which helps keep your team’s stress levels down. When the team keeps track of all of their work in a single compliance operations platform, it becomes easy to prove to customers, auditors, and regulators that your organization has been operating in a secure and compliant way all along. When your organization is good at proving your compliance posture, you win and retain more business.
Put compliance operations principles into practice with a platform
While it might be possible to bring discipline and rigor to these processes using the same tools we use now, it will be close to impossible to keep it that way. This is intuitive when you look at how various business functions are operating today. Sales teams have Salesforce, HR has Workday, and Engineering has a variety of DevOp tools to efficiently execute their work. Security assurance and compliance teams also need their own platform for managing daily compliance operations — a place for making project plans, getting work done, tracking progress, and identifying areas for improvement.
Hyperproof’s compliance operations platform was built with these key principles of good operations in mind. Hyperproof is your assistant in creating a highly effective Compliance Operations function. It gives you the visibility, efficiency, and consistency you and your team need to stay on top of all your security assurance and compliance work.
To learn more about Hyperproof, sign up for a demo: https://hyperproof.io/request-a-demo/
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












