Next-Level Risk and Compliance Management
Hyperproof is the platform for operationalizing compliance and risk management by enabling you to automate your workflows, prepare for audits, and mitigate risk.
Trusted By







The Hyperproof Platform Advantage
60%
gain in process improvement for audit preparation
Take the guesswork out of preparing for audits with confidence that your evidence is always up-to-date and accurate.
70%
increase in productivity for compliance professionals
Get the business advantage of operationalizing risk by streamlining compliance and risk workflows so you can be proactive about risk mitigation.
90%
improvement in visibility on compliance posture
Have complete visibility into your compliance posture so you can easily communicate your security posture to stakeholders.
Compliance Management
Optimize your compliance work by mapping common controls to compliance requirements, automating evidence collection, mitigating issues, and monitoring your compliance posture, all in one place.
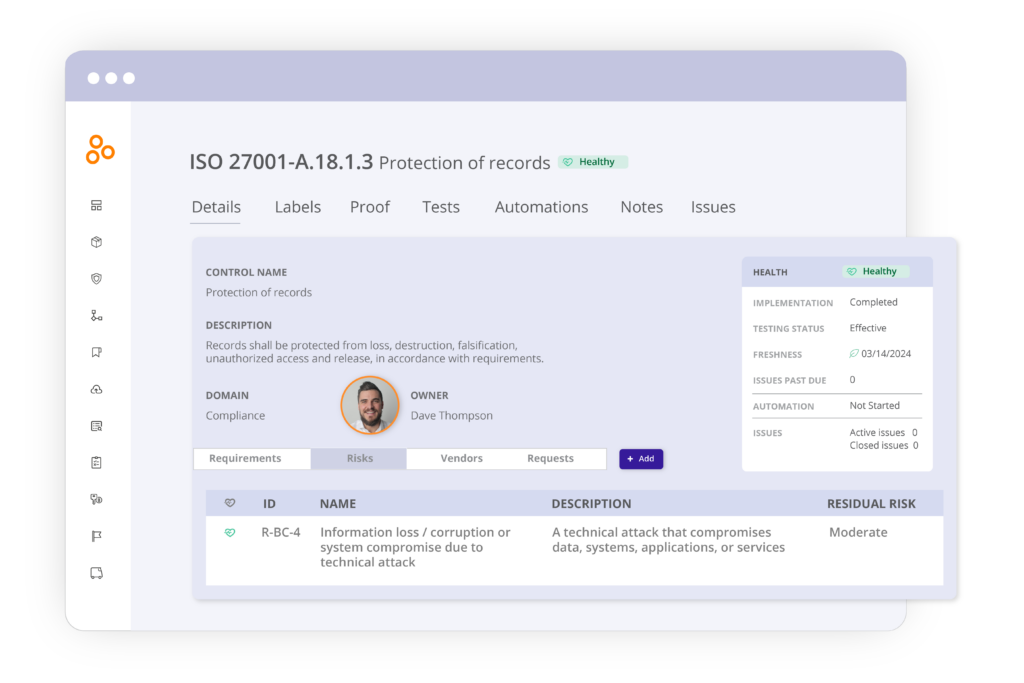
Manage controls with flexibility
Meet your organization’s needs by creating controls that fit your specific use cases and keep them up to date with easy owner assignment, task management, and control testing.

Map controls across frameworks with built-in control crosswalks
Reuse controls across multiple frameworks to satisfy requirements from multiple standards. Save time implementing new frameworks, adapting to new regulations, and managing existing frameworks as your company grows.

Automate evidence collection with Hypersyncs
Ensure your evidence is always up to date by setting up automated evidence collection using Hyperproof’s 70+ integrations and reuse evidence across multiple controls to satisfy audit requests.

Leverage integrated task management tools
Build and maintain a cohesive and uninterrupted work environment by seamlessly integrating your task management tools like Jira, Asana, and ServiceNow in one place.
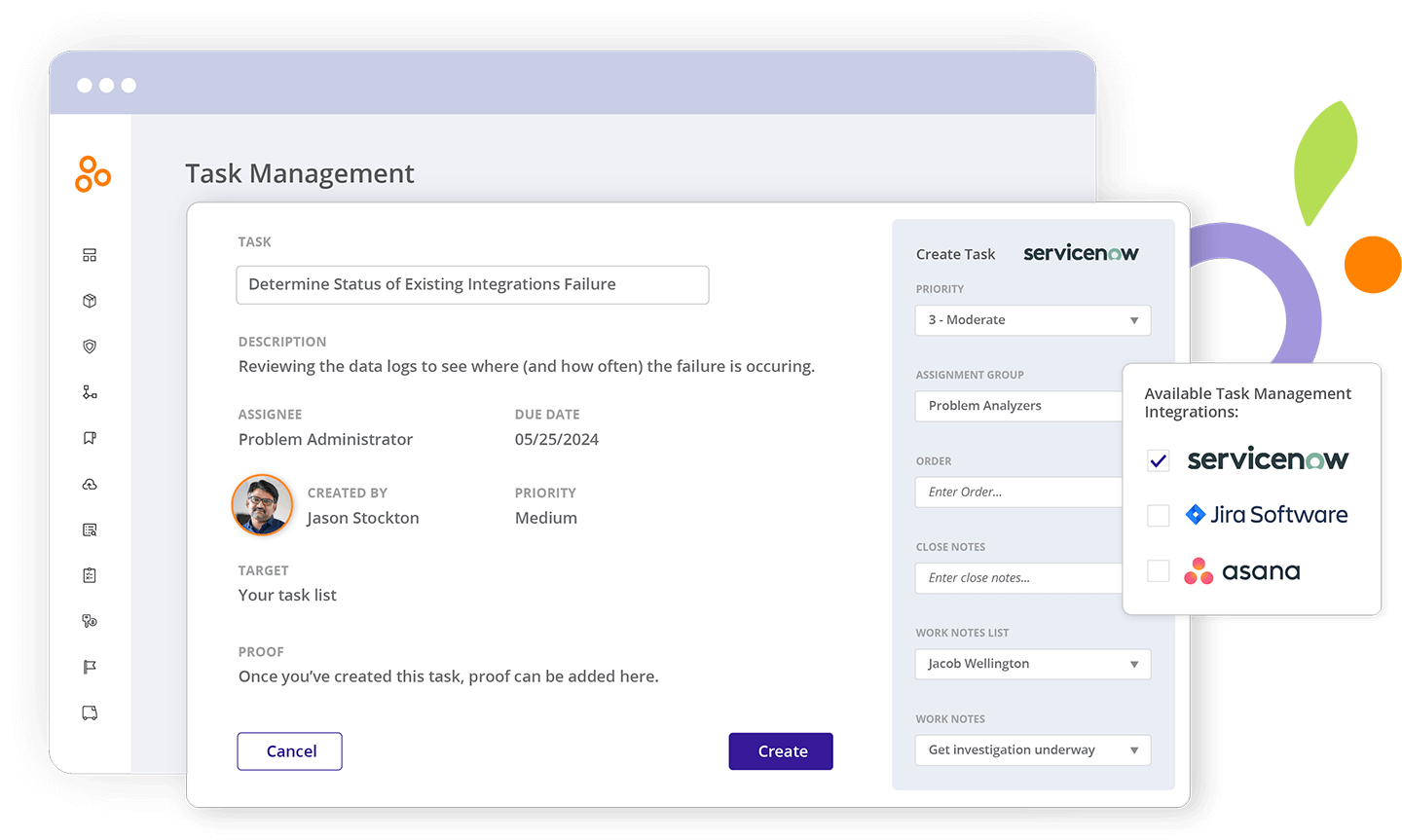
Track issues and automate risk mitigation workflows
Ensure issues are tackled immediately by easily assigning critical work on acceptance and remediation workflows. Draft prescriptive risk treatment plans by seamlessly integrating risk and controls.
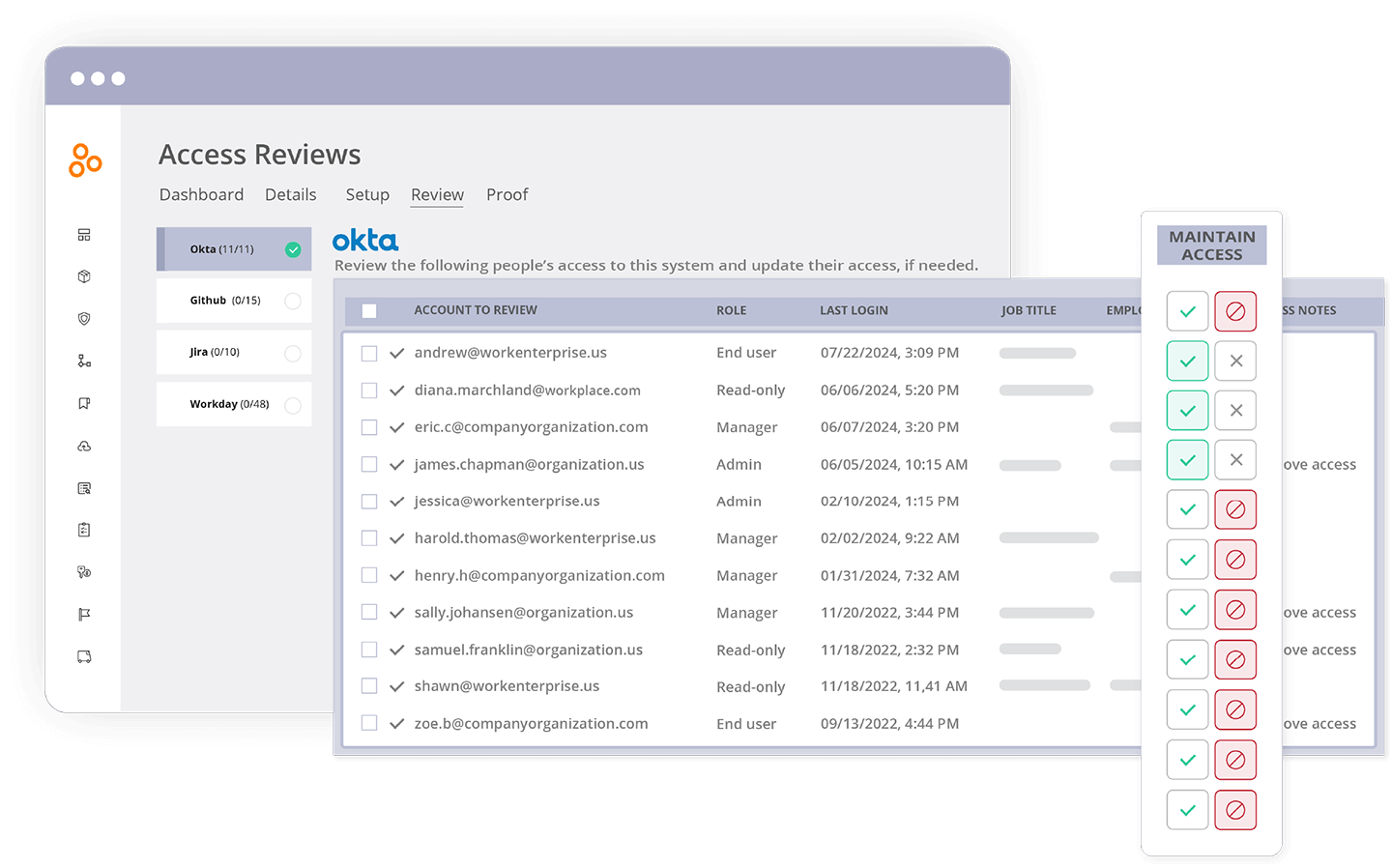
Conduct user access reviews with ease
Streamline the user access review workflow, adjust and verify access quickly, get real-time visibility into the status of access reviews, and free up valuable team resources to focus on high-impact work.
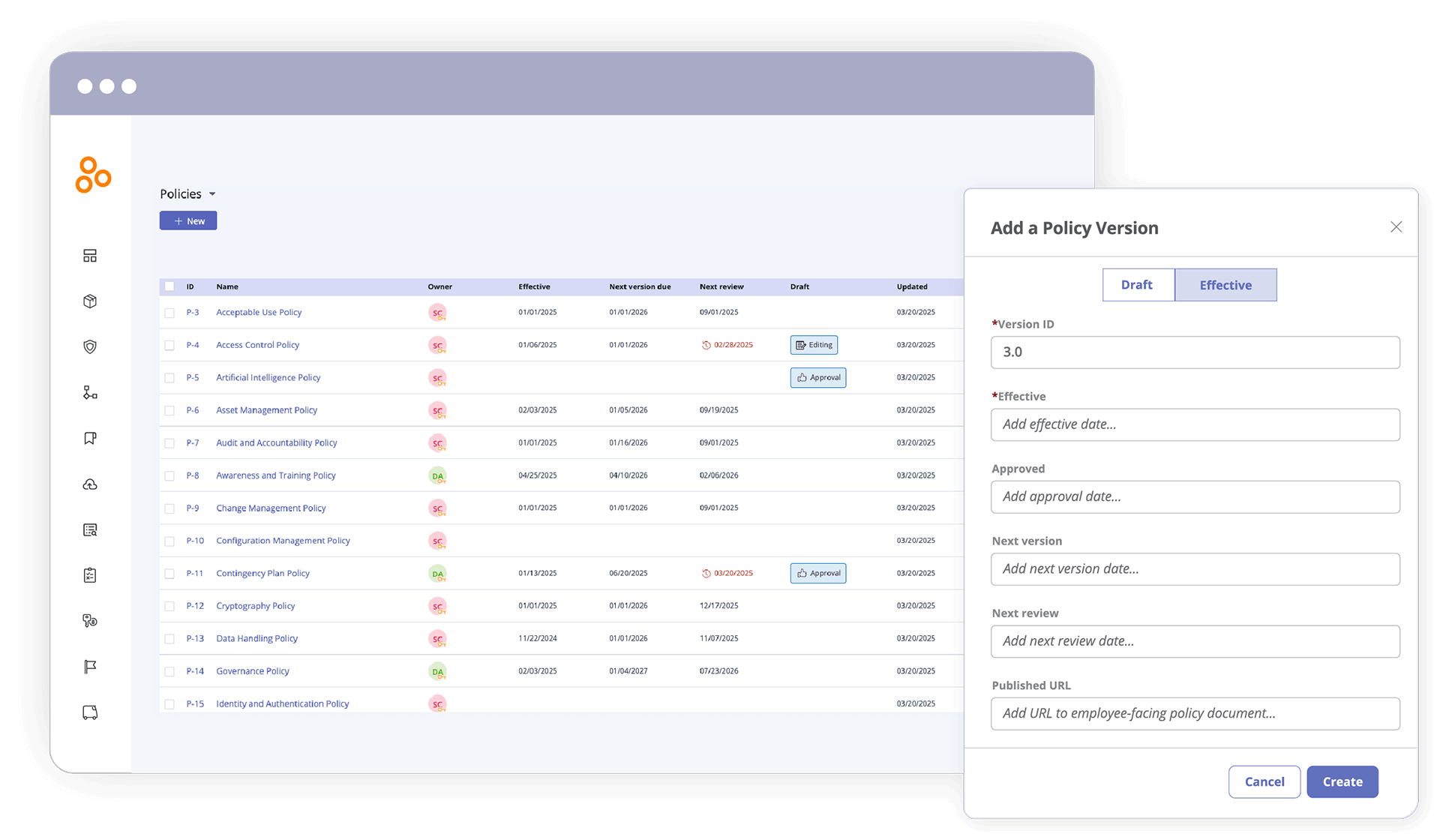
Centralize policy management
Create, store, and manage all organizational policies in one place, ensuring version control and easy access. Easily add new policies and view existing policies in a centralized place.
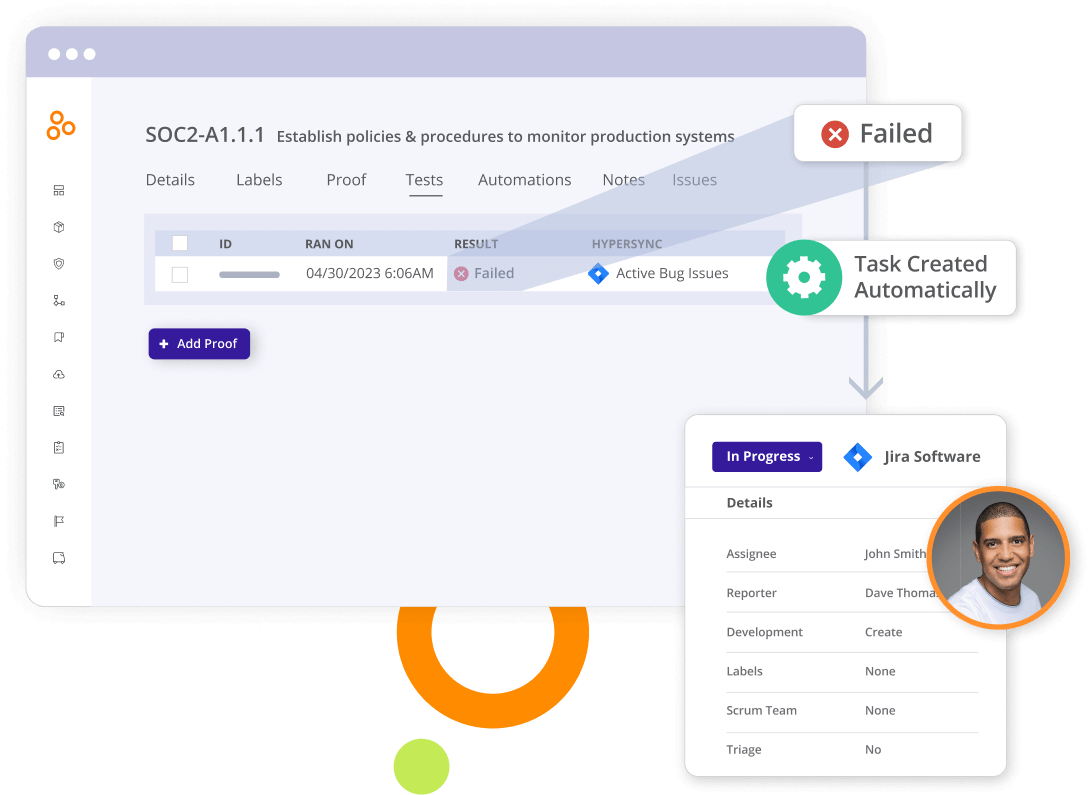
Automate controls testing and escalation
Automatically test and monitor control effectiveness and auto-create tasks based on test status. Address failed tests immediately to ensure risks are mitigated and that your controls are always up to date.
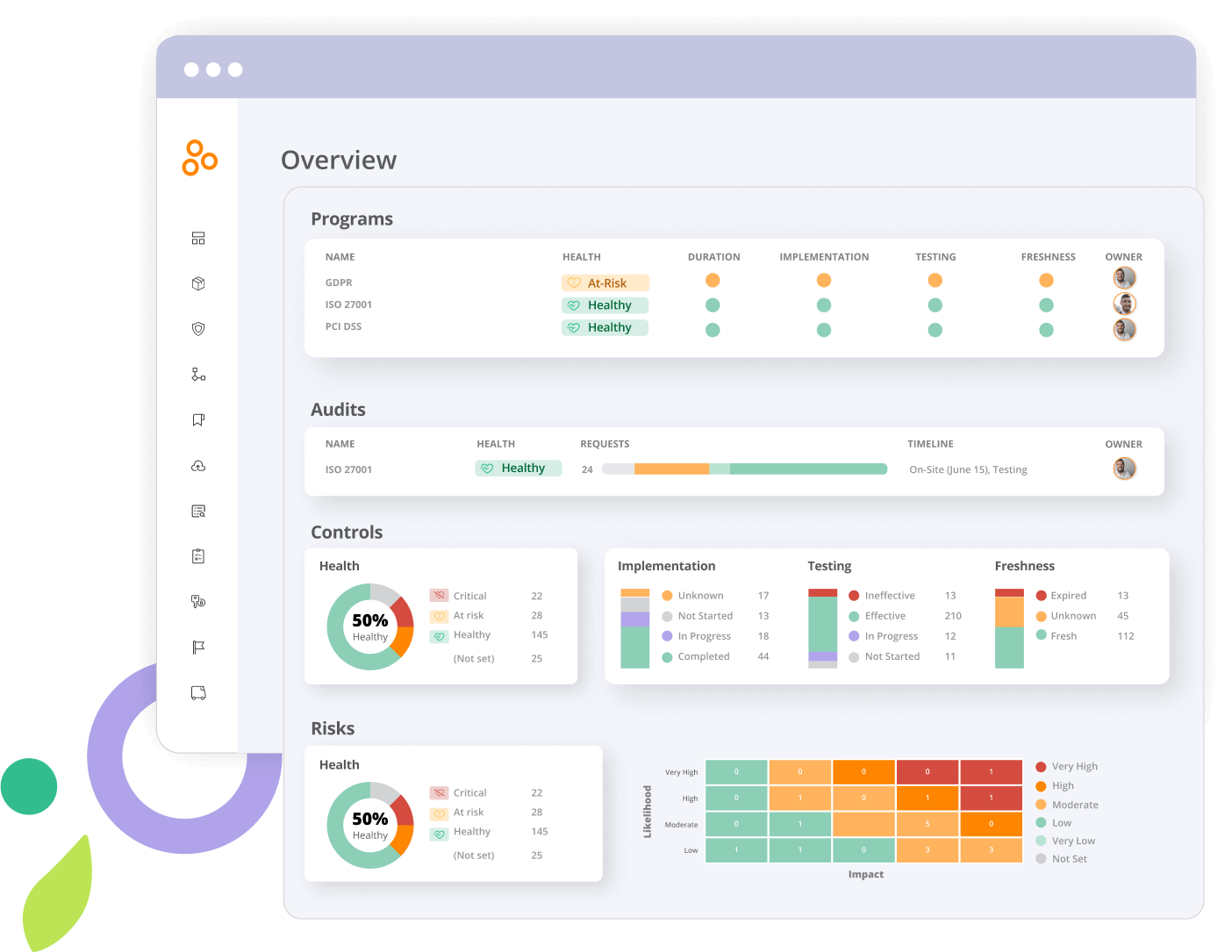
Gain risk & compliance visibility
Get the reports and dashboards you need to answer questions from stakeholders, updated in real-time to understand your compliance, risk and audit-readiness posture and action items. Export custom reports or receive reports via email.
Risk Management
Use Hyperproof to identify and prioritize risks, orchestrate and automate risk workflows, create alignment between risk management and compliance activities, and reduce time spent on monitoring risks.
Centrally manage risks
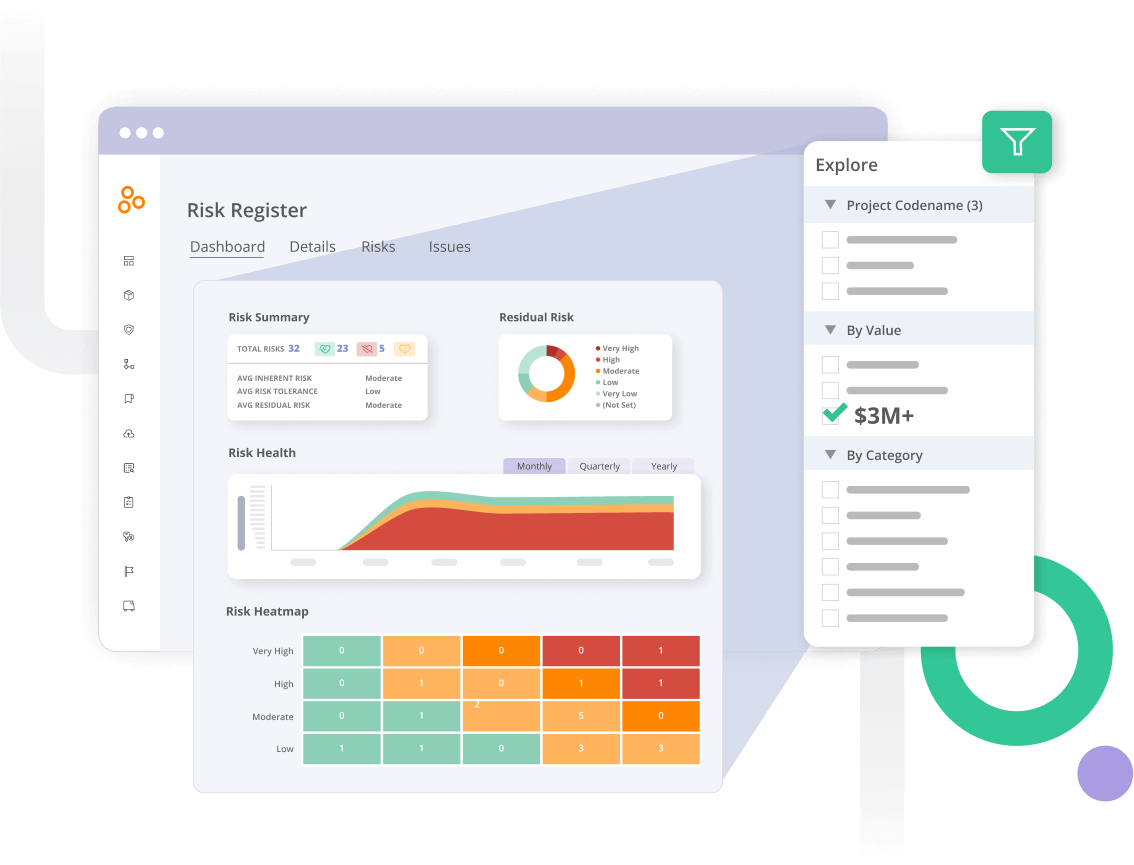
Stop working in disparate systems to track risk. Use Hyperproof to centralize risk management by collecting and tracking your risks in the Hyperproof risk register to ensure no risk is missed.
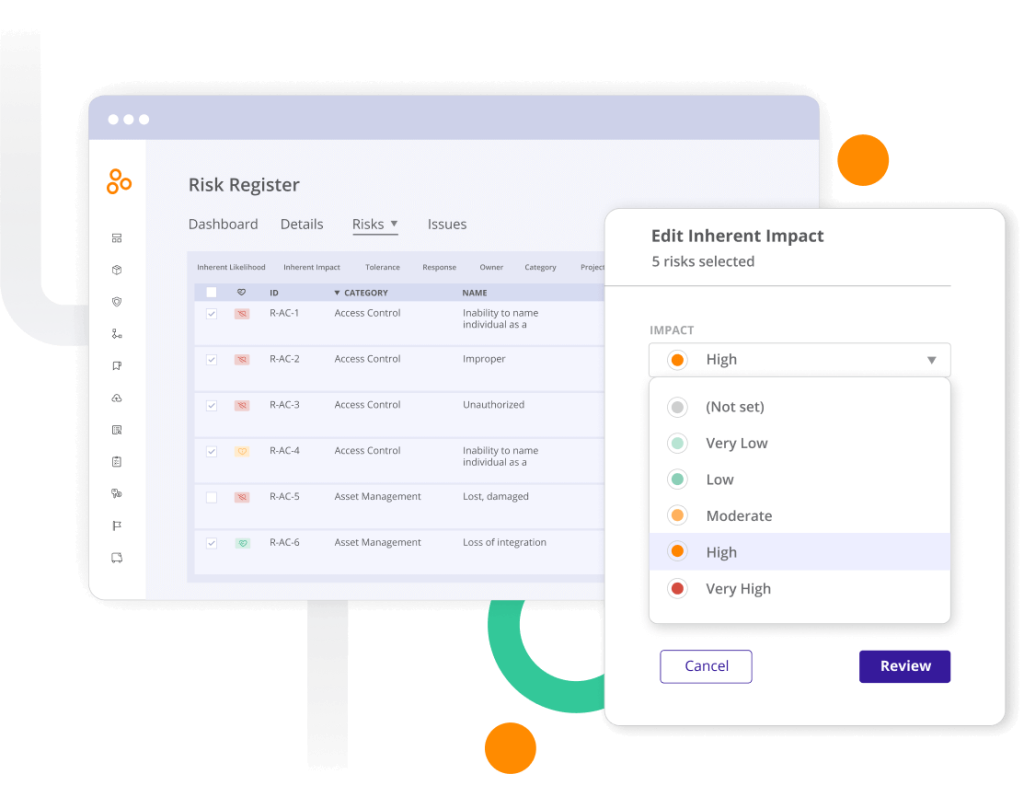
Evaluate risks based on your company landscape
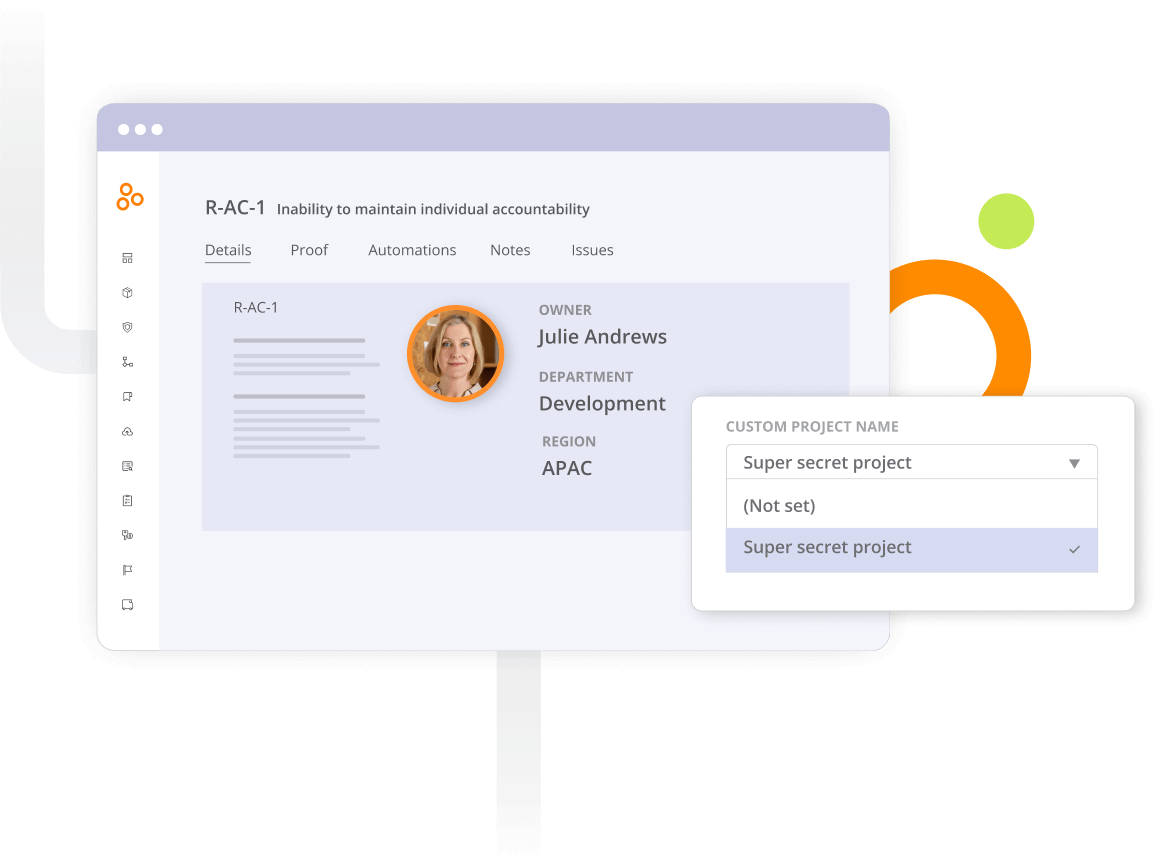
Use standard fields for evaluating each risk: tolerance, actual risk, inherent risk, likelihood and impact — all with customizable scales. Add custom fields that can function as filters on your dashboards and reports to track additional information on each risk.
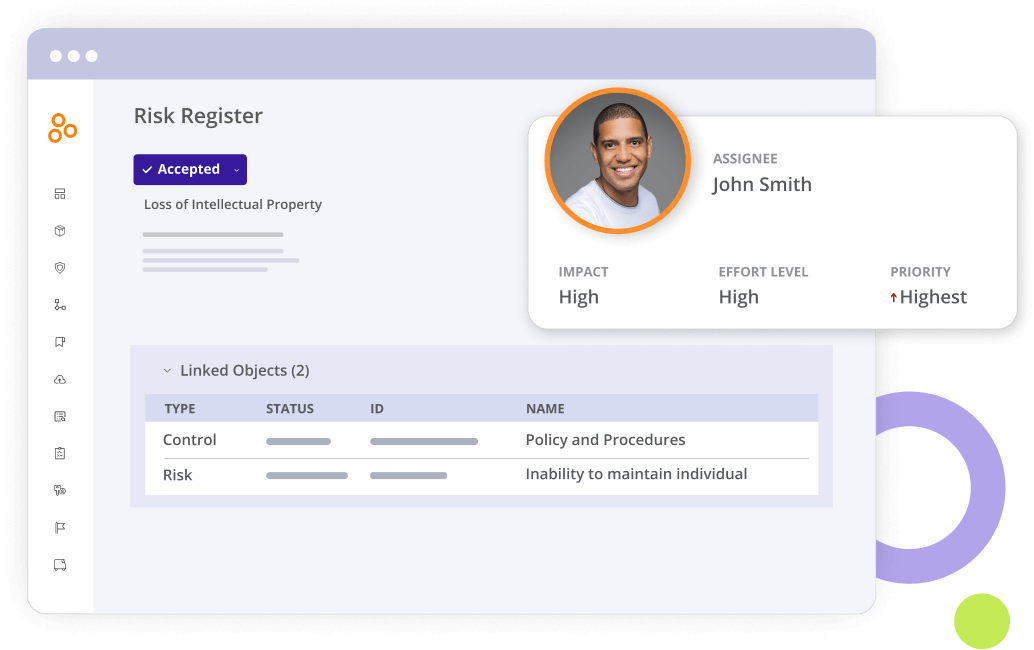
Map controls to risks
Integrate control health data with multiple risk registers so you can continuously monitor real-time risks, quickly resolve issues, and report mitigation efforts to relevant stakeholders.
See how risks change over time
Link mitigating controls to risks in the risk register and leverage built-in exportable dashboards and reports to see how your risk posture changes in real time.

Ready to try Hyperproof?
Vendor Management
Efficiently conduct vendor due diligence, vendor assessments, contract reviews, and vendor risk remediation activities in one place.
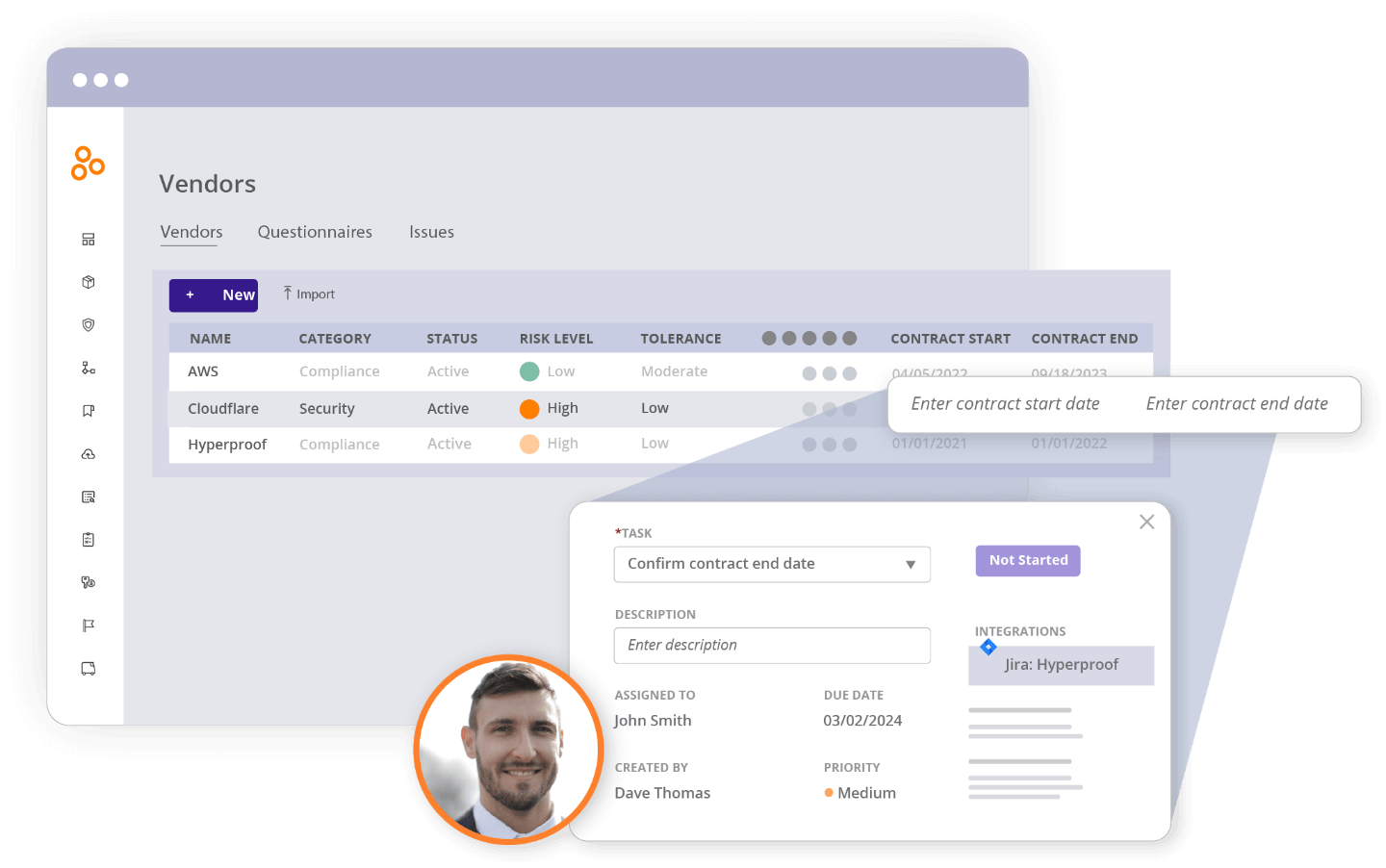
Centralize vendor management
Maintain a central source of truth for your third-party vendors. Collect a list of your vendors and track key documents and renewal dates, assess vendor risk profiles, and analyze potential risk impact with automated assessments.
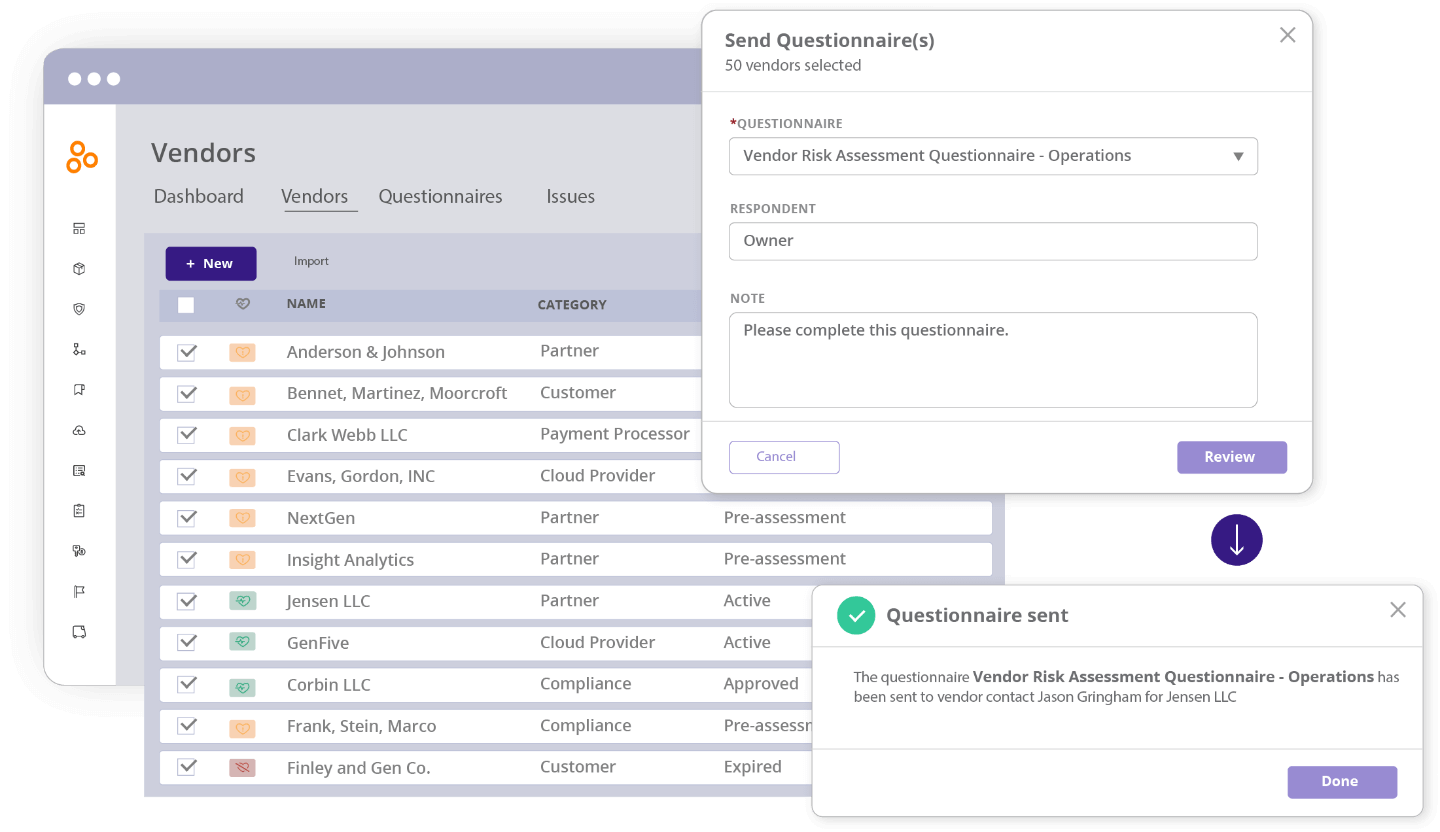
Automate security questionnaires
Create and send tailored risk and security questionnaires to your vendors and monitor questionnaire completion progress, all within one streamlined module.
Assess and reduce vendor risks
Assess vendors and measure vendor risk levels. Understand residual risk for each vendor, identify where to focus your remediation efforts, and create action plans.
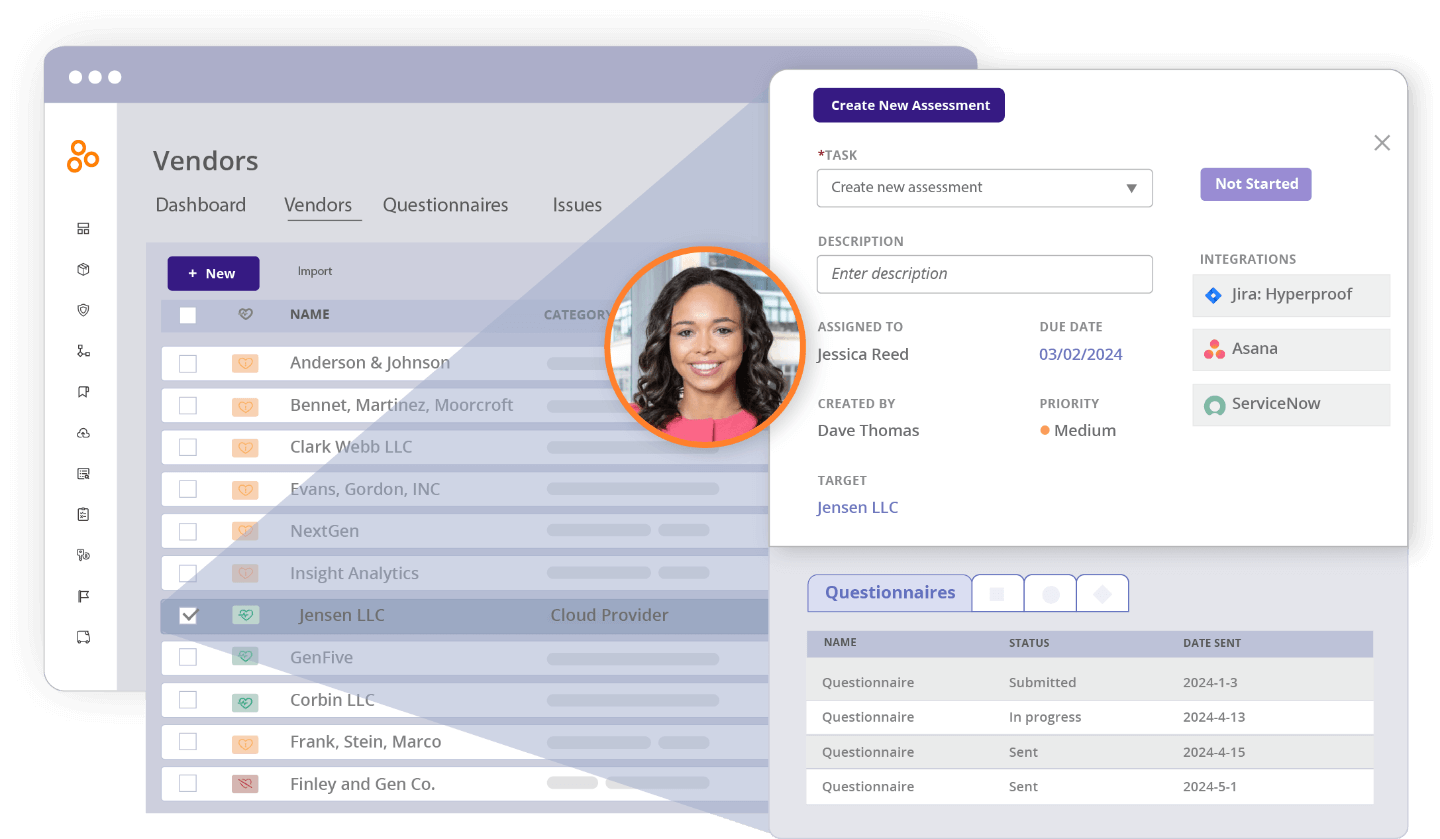
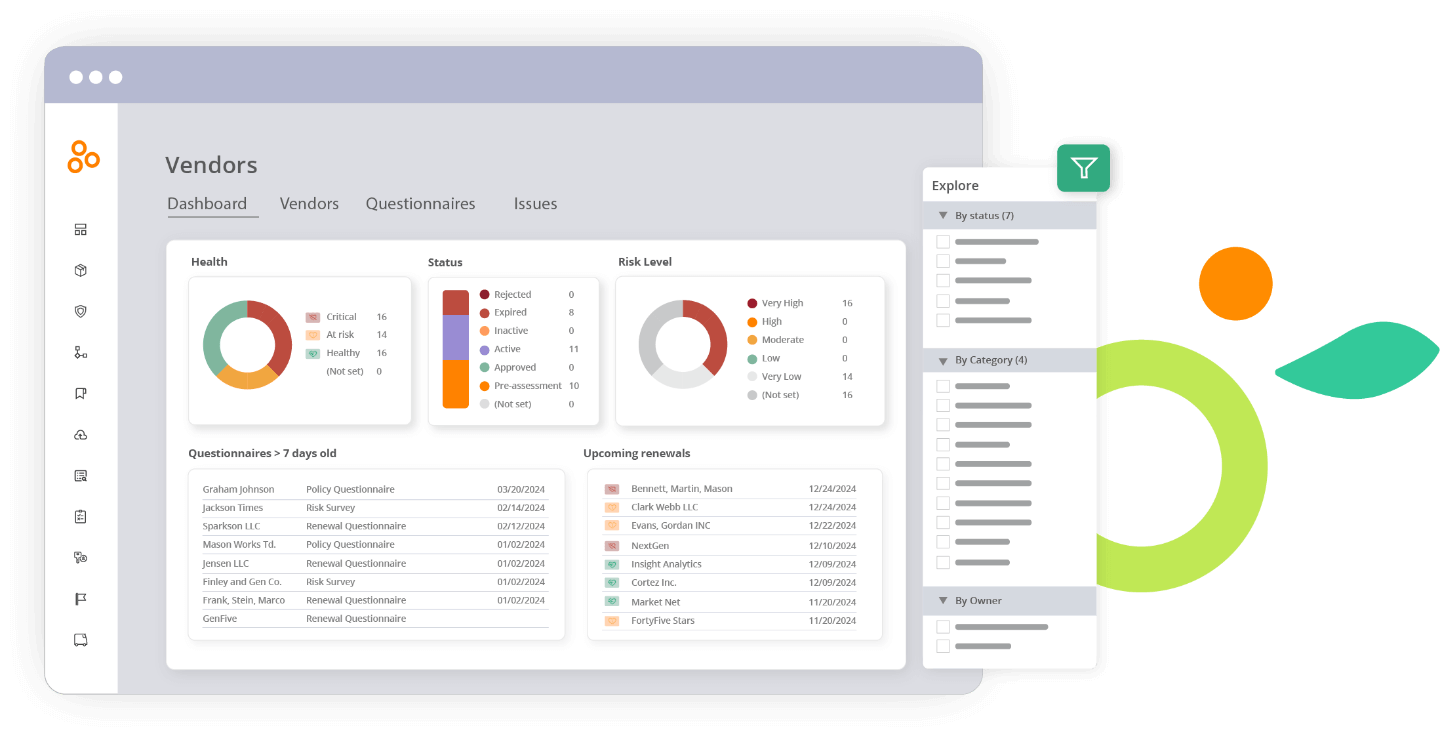
Gain visibility with the vendor dashboard
Get an overview of all of your vendors, their statuses, their risks, and the controls associated with those risks in an exportable dashboard.
Audit Management
Streamline audit preparation with Hyperproof by centralizing your work in a single place and leveraging automation to ensure your evidence is up to date to satisfy auditor requests.
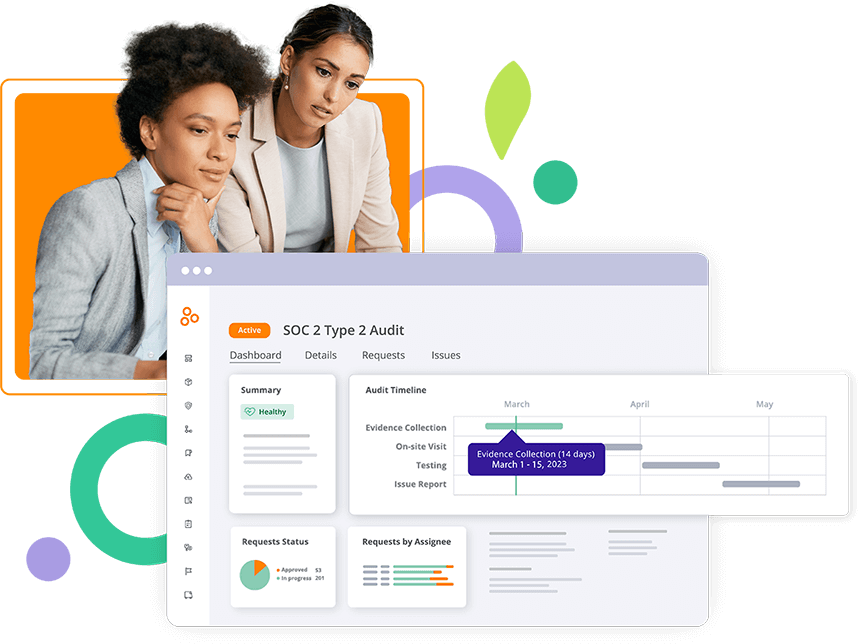
Seamless connection between controls and audit requests
Connect audit requests automatically to controls and their associated evidence, speeding up the audit readiness process and enabling you to reuse work for the next audit.
Easily collaborate with your auditors
Invite your auditor to work alongside your team in Hyperproof’s dedicated audit space to make information sharing easy while ensuring they only have access to what they need.
Know the status of your audit
Easily understand what requests still need to be done, what’s in progress, what’s being reviewed, and what’s completed with Hyperproof’s audit dashboard.
Enterprise-grade security to meet your complex needs
Easily control user access with robust roles and permissions and keep systems secure leveraging MFA and SSO with Azure via OpenID Connect (OIDC), JumpCloud and Okta.
Robust roles and permissions
Users across your organization can access what they need while still providing the safety and security compliance administrators need to meet data confidentiality requirements.
SSO
Hyperproof supports Single Sign On (SSO) with Azure via OpenID Connect (OIDC), and JumpCloud and Okta via SAML.
Multi-factor authentication
Secure your Hyperproof instance by requiring MFA with authenticator apps like Google Authenticator, Microsoft Authenticator, or Authy.
SOC 2® Type II compliance
Hyperproof’s takes compliance as seriously as its customers and successfully obtained a SOC 2® Type 2 report.

Your partner from the start
We aim to delight our customers with every interaction. Our customer success team offers continual support for every step along your security, risk, and compliance journey.
“Hyperproof’s team has been extremely responsive. We love to see our requests on the roadmap and implemented so quickly.”

Alex Scoble
Head of IT Security

“I’ve had a fantastic experience with Hyperproof. The implementation team was very hands-on.”

Jessica Parant
Security Compliance Specialist

Ready to see
Hyperproof in action?









