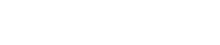The Largest Framework Library on the Market
As your company’s needs change, your compliance needs evolve. Hyperproof’s extensive risk management and compliance frameworks library of over 120 framework templates with requirements and controls can be fully customized to your organization. Explore all supported compliance frameworks in our library to find the right fit for your industry and maturity.
Need cloud-specific guidance? Our overview of cloud compliance frameworks breaks down what to implement and why it matters.

Americans with Disabilities Act (ADA) and Web Content Accessibility Guidelines (WCAG) v2.2

APRA CPS 234

Australian Government Information Security Manual (ISM) for IRAP and ASD by ACSC

Adobe Common Controls Framework (CCF) v4

AWS Well-Architected Framework

Bank Secrecy Act Compliance Program (BSA)

Belgium Cyber Fundamentals

Brazilian General Data Protection Law (LGPD)

BSI Cloud Computing Compliance Controls Catalog (C5)

C4 CryptoCurrency Security Standard (CCSS)

CA Browser Forum Network Security Controls v1.3

Canadian OSFI B-13

Canadian Personal Information Protection and Electronic Documents Act (PIPEDA)

China Cybersecurity Law – Personal information (PI) security specification

Cisco Cloud Controls Framework (CCF)

CMS Acceptable Risk Safeguards 5.0x and Information Systems Security and Privacy Policy (IS2P2) v3.0

CMS Minimum Acceptable Risk Safeguards for Exchanges (MARS-E) Harmonized Security Privacy Framework v2.2

Cybersecurity Maturity Model Certification (CMMC v1.02)

Control Objectives for Information and Related Technologies (COBIT) 2019

Cyber Risk Institute (CRI) Profile

Cyber Risk Institute Profile 2.0 (CRI)

Cybersecurity Capability Maturity Model (C2M2)

Digital Services Act (DSA)

Department of Homeland Security (DHS) 4300A – Sensitive Systems Handbook

Digital Operational Resilience Act (DORA)

Classified Protection of Cybersecurity (DJCP) or Multi-Level Protection Scheme (MLPS)

EASA Part-IS

EU AI Act

EU – US Data Privacy Framework (DPF)

EU Cyber Resilience Act

ETSI EN 319 401 V2.2.1

Spanish National Security Scheme (ENS) 2022

Family Educational Rights and Privacy Act of 1974 (FERPA) with PTAC Guidance

Federal Bureau of Investigations (FBI) CJIS Security Policy
FDA Electronic Records; Electronic Signatures (21 CFR Part 11)

FFIEC Cybersecurity Assessment Tool (CAT)

France ASIP HDS – HDH Certification – v1.1

French ANSSI SecNumCloud v3.2

Gramm-Leach-Bliley Act (GLBA) and FTC Safeguard Rule

Hyperproof Common Control Framework (CCF)

IATF 16949

Israeli Protection of Privacy Law and Regulations

Italian ACN

IBM Cloud Framework for Financial Services

IEC 62443 4-1

IEC 62443 4-2

ISO 14001:2015

ISO 17025:2017

ISO 20000

ISO 21434

ISO 22301:2019

ISO 26262

ISO 27001:2019

ISO 27002:2022

ISO 27017:2015

ISO 27018:2019

ISO 27701:2019

ISO 27799:2016

ISO 28000:2022

ISO 42001 AI Management System

ISO 45001:2018

ISO 9001:2015

ITSG-33 Government of Canada Controls Catalogue

International Traffic in Arms Regulations (ITAR) Compliance Program Guidelines
Japanese Information System Security Management and Assessment Program (ISMAP)

Korean Personal Information & Information Security Management System (ISMS-P)

MAS Technology Risk Management Guidelines (TRM)

Microsoft SSPA v.10

Microsoft Supplier Privacy & Assurance Standards (SSPA DPR v7)

NERC Critical Infrastructure Protection (CIP)

NIS2

NIST SP 800-161

NIST 800-171 Rev2

NIST 800-171 Rev3

NIST SP 800-218

NIST SP 800-82

NIST SP 800-53 Rev5

NIST SP 800-53 Rev5 Selectable Baseline

NISTIR 8374 Ransomware Risk Management

NY Department of Financial Services (NYDFS) Part 500 Cybersecurity Requirements for Financial Services

OWASP Application Security Verification Standard (ASVS) v4.0.3

Payment Card Industry Data Security Standard (PCI DSS) 3.2.1 (Retired framework available for reference)

Payment Card Industry Data Security Standard (PCI DSS) 4.0.1

SASB ESG

Saudi Arabia Essential Cybersecurity Controls (ECC) 2018

SEC 17 CFR Part 240 15c: Rules Relating to Over-the-Counter Markets (§§ 240.15c-2 and 240.1c-3)

SEC 17 CFR PART 240 17a: Preservation of Records and Reports of Stabilizing Activities (§§ 240.17a-1 – 240.17f-2)

Secure Controls Framework (SCF)

Secure Control Framework v. December 2024

Sarbanes–Oxley Act (SOX)

GovRAMP

SWIFT CSCF

Task Force on Climate-Related Financial Disclosures (TCFD)

Trusted Information Security Assessment Exchange (TISAX)

Texas Risk and Authorization Management Program (TX-RAMP)

UK Cyber Essentials: Requirements for IT infrastructure

WebTrust Principles and Criteria
Ready to see
Hyperproof in action?