Guide
2023 Proposed Changes to NIST CSF
What You Need to Know about NIST CSF 2.0

Editorial note: this piece was published in November of 2023 before NIST 2.0 debuted. To get a recap of the changes to NIST CSF 2.0 that were published February 26, 2024, check out our blog post, NIST CSF 2.0: Everything You Need to Know About the Update.
Introduction
In January 2023, the National Institute of Standards and Technology (NIST) announced its intent to make new revisions to its NIST Cybersecurity Framework (CSF) document, with an emphasis on cyberdefense inclusivity across all economic sectors. Responding to industry requests on relevant issues, version 2.0 focuses on international collaboration, broadening the scope of industries that can use the CSF, and one entirely new Function.
The new CSF sees protocols surrounding increasing international collaboration in cybersecurity efforts while still retaining the level of detail within the existing standards and guidelines to ensure the framework is scalable and useful for as many organizations as possible.
Keep reading to review the updates and their implications for your business.
When will NIST CSF 2.0 be implemented?
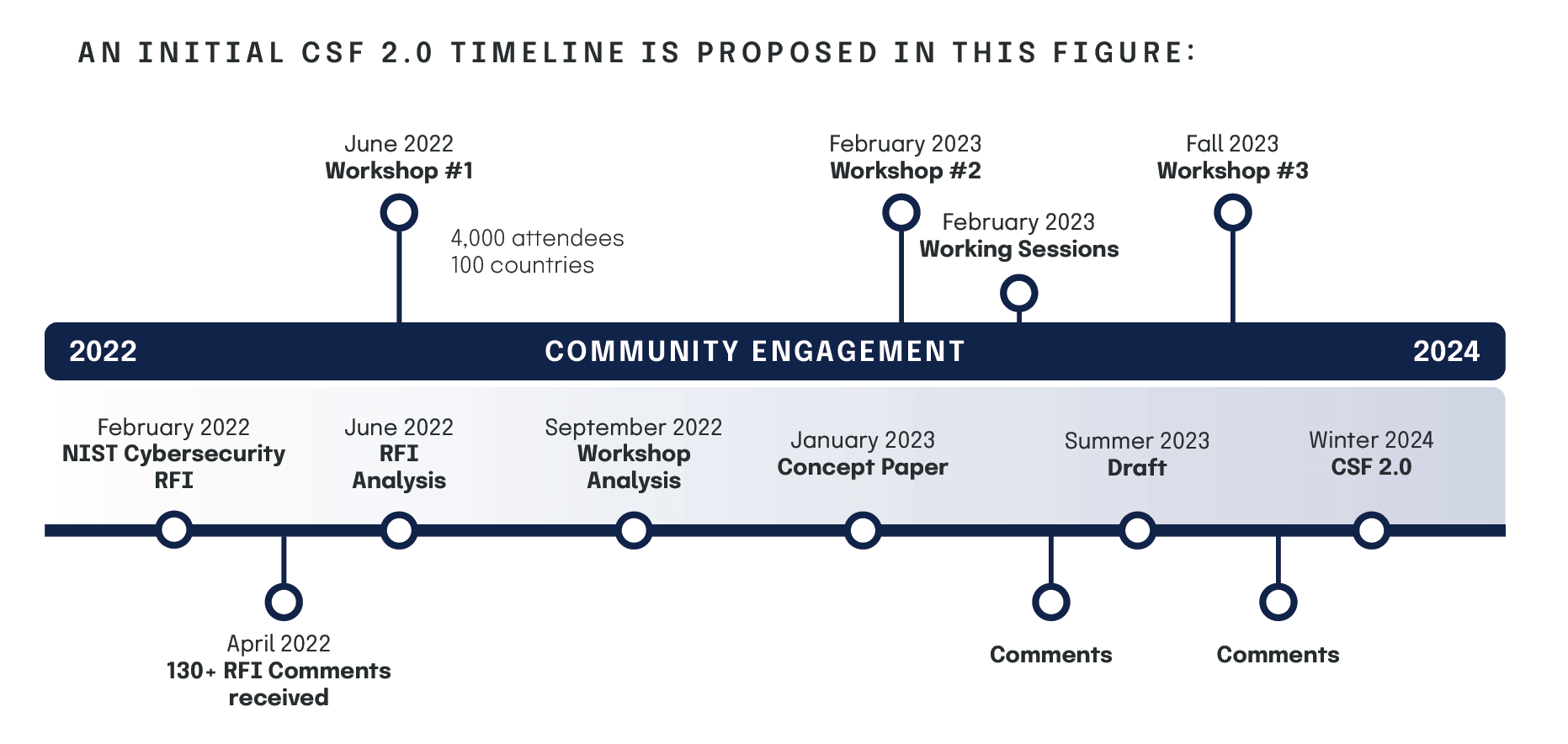
An initial CSF 2.0 timeline is proposed in this figure:
What is NIST CSF?
NIST CSF is a voluntary framework of standards, guidelines, and practices designed to help organizations better manage and reduce cyber risk of all types, including malware, password theft, phishing attacks, DDoS, traffic interception, social engineering, and others. NIST created the framework by collaborating with government and industry groups with the framework designed to complement existing organizational cybersecurity operations. NIST CSF rests on industry best practices gathered from various other documents and standards like ISO 27001 and COBIT 5.

NIST CSF is an increasingly popular framework because of its flexibility. Originally developed to address government industries and the cybersecurity risks of critical infrastructure, the CSF has been widely adopted by organizations of all sizes, sectors, and maturities who want to increase awareness around cybersecurity. Given its flexibility and adaptability, the CSF is a cost-effective way for organizations of all sizes to approach cybersecurity and foster an enterprise-wide conversation around cyber risk and compliance.
NIST CSF is a useful tool to incorporate into any organization’s risk management practice, assisting with and supporting the ongoing process of cyber risk management. Organizations can choose to use their own RMF, NIST’s RMF, another RMF, or the lightweight risk management defined in the CSF as part of the basis of control selection. If you want to use the lightweight risk management in the CSF, you can leverage it to assess risk levels (both acceptable and existing), align on risk tolerance objectives, and determine a security budget to mitigate threats.
The NIST framework for implementing critical infrastructure cybersecurity is composed of three elements: Implementation Tiers, Framework Core, and Framework Profiles.
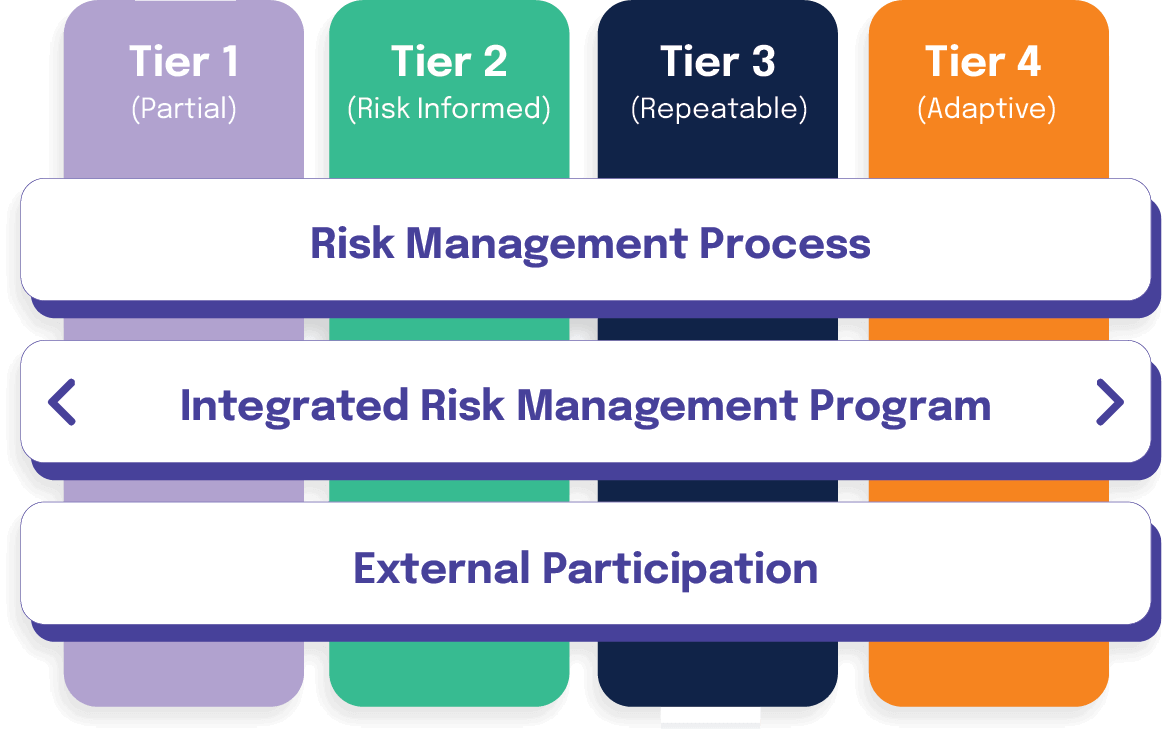
Implementation Tiers
Implementation Tiers provide context on cybersecurity risk management and guide organizations on an appropriate level of rigor for cybersecurity programs.
The Framework Core
The Framework Core discusses controls incorporated in cybersecurity programs, which can be tailored to an organization’s unique needs. The Framework Core consists of four elements: Functions, Categories, Subcategories, and Informative References, as shown below.
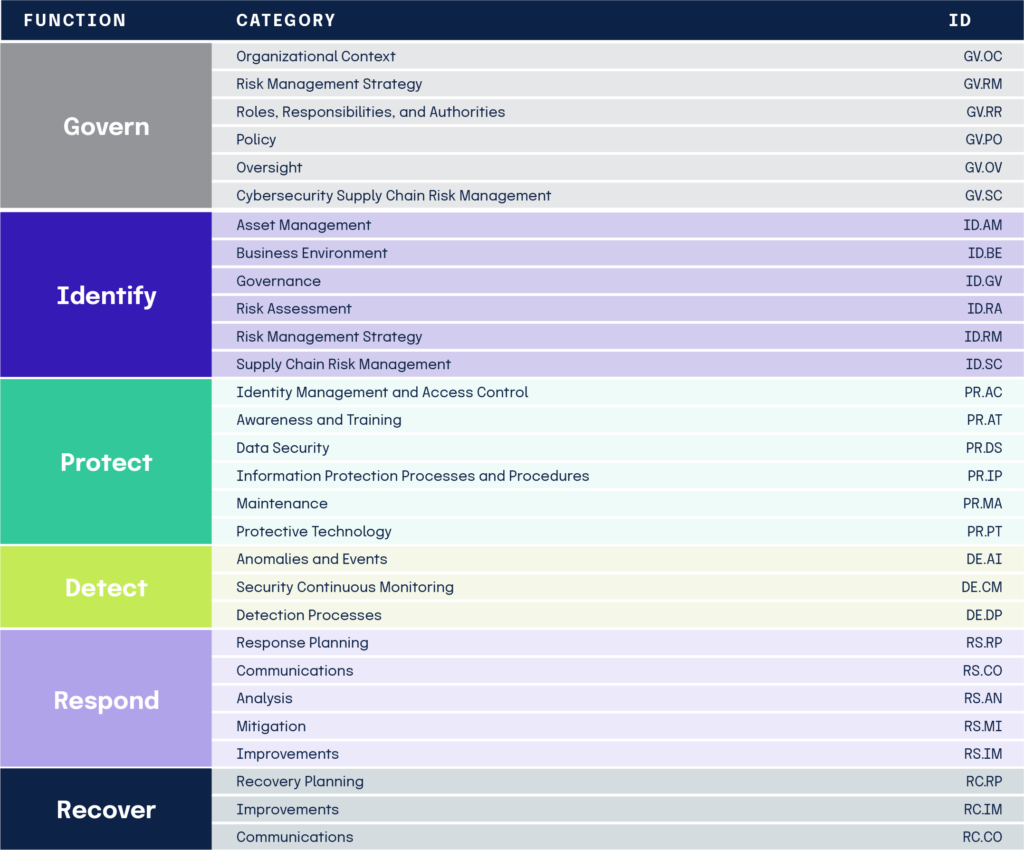
The six functions — Govern, Identify, Protect, Detect, Respond, and Recover — provide the highest level of structure for organizing basic cybersecurity activities into Categories and Subcategories. The Govern function is a new function appearing in the 2.0 update, which we will explore in more detail below. The Categories are the subdivisions of a Function into general groups of cybersecurity outcomes, closely tied to programmatic needs and particular activities. The Subcategories divide Categories into specific outcomes of technical and management activities. Think of Subcategories as outcome-driven statements that provide considerations for creating or improving a cybersecurity program.
Communication template
In addition to these components, NIST has also provided a framework for clarifying the communication roles for each level within an organization.
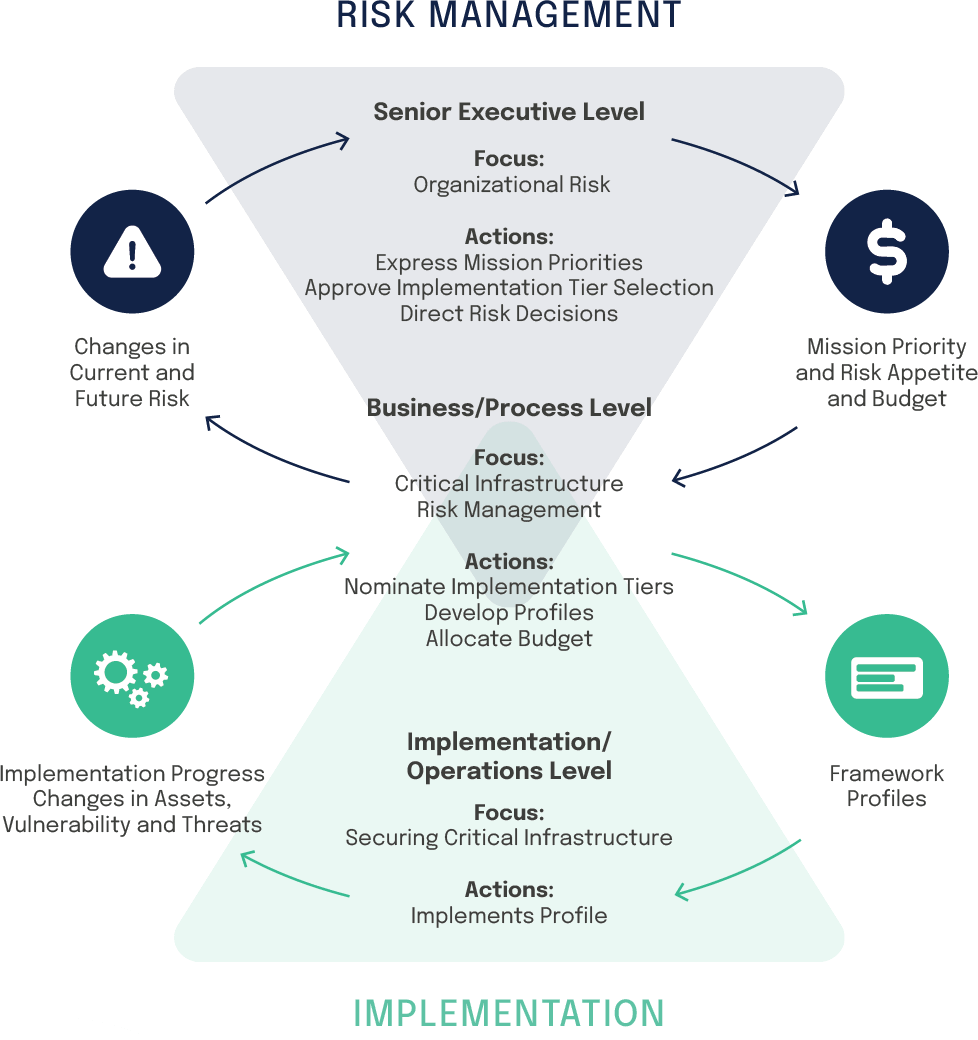
The levels are as follows:
The executive responsibilities level communicates the mission priorities, available resources, and overall risk tolerance to the business/process level.
The business/process level uses the information as inputs into the risk management process and then formulates a profile to coordinate implementation/operation activities.
The implementation/operations level communicates the Profile implementation progress to the business/process level.
The business/process level uses this information to perform an impact assessment. Business/process level management reports the outcomes of that impact assessment to the executive level to inform the organization’s overall risk management process and to the implementation/operations level for awareness of business impact.
Is NIST CSF right for your organization?

The framework was initially designed with government industries and critical infrastructure in mind, however, organizations of all sizes, sectors, and maturities can benefit from using this security framework. Tiers, Core, and Profiles can be customized to fit any organization’s unique needs, making NIST CSF incredibly versatile. Leveraging NIST CSF can help you:
What’s the process of updating NIST CSF?
NIST CSF is a living document that is refined and improved over time. It relies on extensive community involvement from both the public and private sectors to update, including workshops; public review and comment; RFIs; and feedback from speaking sessions.
The proposed changes to NIST CSF emerged from:
Potential significant changes: What to anticipate in NIST CSF 2.0
1. CSF 2.0’s scope would be broadened

CSF 2.0 would cover all organizations across government, industry, and academia, including (but not limited to) critical infrastructure. However, NIST is deliberate with their wording in the 2023 Concept Paper, stating, “This change is not intended to diminish the CSF’s relevance to critical infrastructure organizations, including the importance of ensuring the security and resilience of our nation’s critical infrastructure, but to embrace and enhance its broader use.” Broadening the scope of NIST CSF 2.0 is an increase in effort to ensure CSF 2.0 is helpful to all organizations, regardless of sector, type, or size to address cybersecurity challenges of all magnitudes.
Here’s what NIST intends to do to broaden the scope of the framework in detail:
Broadening the scope of the framework will help companies more easily leverage the CSF across industries. It won’t require much upfront work from cybersecurity professionals. It will make it easier for organizations not already using the CSF to adapt it.
New technology-specific mappings
CSF will remain technology- and vendor- neutral. However, to adapt to the changing technological landscape, NIST will collaborate with the community to develop technology-specific mappings to describe the relationship between security capabilities within a given tech stack and the desired outcomes described in the CSF.
If done well, this could have a moderate positive impact. CIS-CSC created quality baselines that represented a cost savings for companies that chose to use them. However, it’s unclear how NIST will implement their technology-specific mappings and the impact could be low if they do not function smoothly.
Increase international collaboration and engagement with the CSF
NIST will adopt several new strategies for increasing adoption of CSF 2.0 worldwide, including:
This is an effort to help more global companies adopt CSF 2.0 as a framework by working internationally to spread awareness. The impact on organizations already using NIST CSF will be low, and for those starting with CSF, it will be moderate.
2. CSF 2.0 aims to provide more context to existing standards and resources
NIST CSF has, historically, been a detailed and specific framework. NIST CSF 2.0 will continue to provide a common organizing structure for multiple approaches to cybersecurity, including by leveraging and connecting to, but not replacing, globally recognized standards and guidelines. The CSF provides requirements that are simple to digest, with references to much deeper resources (like NIST 800-53).
Here’s what NIST intends to do to broaden the scope of the framework in detail:
This update could enable security experts to communicate overall cybersecurity more clearly. For example, an MSSP can provide a detailed summary of security maturity to a client or a technical team can provide a quality executive summary to their leadership without getting lost in the weeds. Additionally, this will potentially be an improvement for organizations that aren’t using GRC tools to create control crosswalks to align their existing use of CSF with other standards.
Real-time updates to Informative References
Over time, some of CSF’s Informative Resources became outdated. As the source documents were updated to reflect the evolution of the framework, the updates weren’t reflected in the available documentation. To combat this, NIST will transition to online, updatable references available in the CPRT. Notably, NIST has asked the community for submissions of mappings to the CSF and to reach out to NIST to set up necessary mappings to CSF 2.0 that aren’t already in place.
This is one of the most highly-anticipated and exciting potential updates to CSF 2.0. With real-time updates, companies can rest assured that source documents are always accurate.
Updated cybersecurity and privacy reference tool
CSF 2.0 will be showcased through the NIST Cybersecurity and Privacy Reference Tool (CPRT), which provides an improved digital interface for accessing NIST cybersecurity reference data. The CPRT also provides a more flexible approach to understanding the relationships between standards, guidelines, frameworks, and technologies.
Having a digital interface to showcase CSF 2.0 would help adopters more deeply understand its relationships to other frameworks, although users have provided feedback to NIST that the tool isn’t as intuitive as they would like.
CSF 2.0 wants to reference other security frameworks more clearly
NIST has many other cybersecurity and privacy-related frameworks like the Risk Management Framework, the Privacy Framework, the National Initiative for Cybersecurity Education (NICE) Workforce Framework for Cybersecurity, and the Secure Software Development Framework, that all have relationships with the CSF. If this change is implemented, these will all remain separate frameworks, but they will be referenced as guidance either in CSF 2.0 or in companion materials like mappings. This change has been proposed because CSF 1.1 was published before the Privacy Framework.
This change will have a small positive impact on organizations using additional frameworks. However, if your organization is creating manual crosswalks in Excel, you will need to spend time redoing control assessments.
NIST wants to simplify the name of the framework
The current framework name is “Framework for Improving Critical Infrastructure Cybersecurity.” This is because NIST CSF was originally developed to address the cybersecurity risks of critical infrastructure, but the term “Cybersecurity Framework” (CSF) is now used more broadly across organizations and industries. This more commonly used and simplified name will be the official name of the framework.
Simplifying the name of the framework would make it easier for industries of all types to leverage the framework without confusion about its application. No action is needed on behalf of cybersecurity professionals.
3. CSF 2.0 aims to include updated and expanded guidance on framework implementation

A wide variety of organizations with dramatically different needs and risks use NIST CSF, and, as a result, guidance around supporting NIST CSF implementation has been piecemeal over time. NIST will provide general descriptions of the framework’s key components to help make implementation more straightforward. They will also provide detailed information like linkages and mappings to specific cybersecurity guidance from NIST and other organizations to assist with implementation guidance.
Depending on the finished product, this could have a moderate impact for consultancies deploying and configuring controls, resulting in time savings.
Updates to the CSF website
A long-awaited update: NIST will revamp the CSF website to refresh the content and enhance usability. As part of an ongoing review of the entire CSF website, NIST will remove existing outdated resources and add up-to-date resources. The site would be updated regularly during the CSF 2.0 update process. NIST is encouraging organizations to submit recently published NIST resources to include in their website’s repository, including approaches, implementation guides, case studies, mappings, and tools you use to manage the framework.
If done well, a revamp of the CSF website could provide a wealth of resources to companies looking to adopt the framework or those searching for additional framework resources. Having access to resources updated in real-time could have a profound impact on organizations using the CSF so source documentation is always updated.
A new CSF template
NIST would like to produce an optional basic template for CSF Profiles suggesting a format and areas to be considered in Profiles. While organizations can continue to use different formats for Profiles based on their specific needs, they can use templates to make the development of Profiles easier for users. NIST is encouraging the public and private sectors to share (or develop) example profiles for specific sectors, threats, and use cases for submission.
A new template would help organizations stand up NIST CSF faster and could have a moderate impact for companies looking to implement NIST CSF in a short timeline.
NIST intends to add examples for CSF Subcategories
CSF 2.0 will include notional implementation examples of concise, action-oriented processes and activities to help achieve the outcomes of the CSF Subcategories, in addition to the guidance provided in the CSF Informative References. However, it’s important to note that NIST will provide a small, limited list of examples to prevent the CSF core from getting too long-winded.
The impact of this change depends on the form of these examples. It could result in cost savings or cause organizations to reimagine or revise existing deployed controls.
4. CSF 2.0 will emphasize the importance of cyber governance with a new Govern Function
Cybersecurity governance is currently addressed in CSF 1.1 in the “Identify” Function and in the section on “How to Use the Framework.” CSF 2.0 will expand the consideration of these topics.
A new Govern Function
CSF 2.0 aims to include a new “Govern” Function to emphasize cybersecurity risk management governance outcomes. These may include:
The new Govern Function in CSF 2.0 will inform and support the other Functions. Notably, Microsoft has also suggested aligning the Govern Function in the CSF to the Govern Function in the NIST AI Risk Management Framework and the NIST Privacy Framework.
This is one of the most significant potential changes in the CSF 2.0. Adding to the original “Identify, Protect, Detect, Respond, Recover” is now “Govern,” and the implications are large. This new Function will not only highlight how important governance is to reducing risk but may also help with assessing risks and impacts, determining priorities and risk tolerances, understanding the roles and responsibilities of cybersecurity functions, and establishing additional policies and procedures.
5. CSF 2.0 will emphasize cybersecurity supply chain risk management
Supply change management has been a pervasive problem among cybersecurity professionals. If your business engages supply-chain partners or outsources anything, third-party risk is on your radar. The CSF 2.0 intends to respond to the increasing pressure to mitigate third-party risk by expanding supply chain coverage.
Expand supply chain coverage
CSF 2.0 would include additional C-SCRM-specific outcomes to help organizations address third-party risk. NIST has proposed a few options:
- Further integrating C-SCRM outcomes throughout the CSF Core across Functions
- Creating a new Function focused on oversight and management of C-SCRM
- Expanding C-SCRM outcomes within the current ID.SC Category in the Identify Function
Third-party risk remains a pervasive problem for cybersecurity professionals, and these updates could help those using the CSF to better address it. This might require some changes to your existing framework, so be prepared to make tweaks to your framework program if this update is included in CSF 2.0.
6. CSF 2.0 will clarify what success looks like and how to measure it

Measuring success with such a broad framework can be difficult, considering the needs of organizations using CSF are so varied. CSF 2.0 aims to provide a common taxonomy and lexicon to provide more guidance on what success looks like with CSF, regardless of what a company’s underlying risk management process is, since all organizations have the primary goal of determining how well they are managing cybersecurity risk and how to continuously improve.
This will not add any additional work or burden to cybersecurity professionals, but having more guidance on defining success would help companies more deeply understand how to leverage the framework to its fullest.
NIST will provide examples for measuring CSF success
CSF 2.0 will include examples of how organizations have used the CSF to measure success. This may include examples of ways organizations have leveraged the CSF in the past, risk management strategies, maturity models, and ways organizations have communicated how effective their programs are to stakeholders. NIST is asking organizations to share their methods to better understand what resources to include in this section.
Companies using NIST CSF will not be impacted, but having examples of how others have leveraged such a flexible framework would provide additional insight into how to best utilize the framework.
Updates to the NIST Performance Measurement Guide
It’s only natural that with improved definitions on measuring success, the flagship measurement guidance document, the NIST Performance Measurement Guide, will also need to be updated. Note that the underlying fundamentals of the cybersecurity measurement process and implementation will not be included in the CSF, but rather in NIST SP 800-55.
As the CSF evolves, so do benchmarks for measuring success. Updating the NIST Performance Measurement Guide won’t be a lift for companies using the CSF, but rather an effort from NIST to ensure the framework is as useful as possible.
Additional guidance on framework implementation tiers
CSF 2.0 will clarify the scope and applicability of Tiers to address more robust risk management processes, programs, and external communication. The update will also better describe the relationship between Tiers and maturity model concepts, but consistent with the approach described broadly to address cybersecurity measurement, CSF 2.0 will not provide a distinct maturity model to meet CSF outcomes at the Function, Category, or Subcategory level. Supplemental resources could include new guidance on how the Tiers can be used in CSF Profiles, and increased focus on resources for the community to share mappings among Tiers, risk management processes, and maturity models.
Tiers are not widely adopted and have historically been confusing to implement. This change would help clear up confusion around Tiers and maturity model concepts so that companies can better leverage them.
Ready to see how Hyperproof can help you manage NIST CSF?

Hyperproof’s compliance operations software can help organizations implement NIST CSF guidelines, support ongoing control evaluation efforts, and improve the security of an organization’s information systems. Hyperproof makes complying with NIST guidelines easier by helping you:
If you’re currently using NIST CSF 1.1 and looking for a platform to help you upgrade to 2.0 when the time is right, Hyperproof has you covered. To learn more, sign up for a personalized demo.
Download the PDF












