How to Implement the NIST Cybersecurity Framework (CSF) to Foster a Culture of Cybersecurity

Editor’s note: this piece on the NIST cybersecurity framework was originally published in February 2020 and has been updated in May 2024 with new information.
Data breaches and developing cyber threats are routinely making headlines, and cybersecurity has become a top concern for organizations of all sizes and industries. Cyberattacks have become more frequent, sophisticated, and damaging than ever before, making it critical for organizations to develop a strong culture of cybersecurity to protect their assets and maintain trust with their customers.
However, building a culture of cybersecurity can be a complex and challenging task, especially for organizations that need more knowledge and resources or for those that have diverse or misaligned teams. This is where the NIST Cybersecurity Framework can be an invaluable tool for organizations looking to improve their security posture and more efficiently manage risk and compliance.
In this article, we’ll discuss how to implement NIST CSF — a tool security leaders can use to foster a definitive, organization-wide understanding of what an organization’s governance considers an acceptable level of risk.
Related: Guide to NIST 800-53
How does the NIST Cybersecurity Framework (CSF) support a culture of cybersecurity?
It is not unusual for an organization to have a disconnect between the C-suite and the technical implementation staff regarding risk tolerance. To make things worse, the organization is often unaware it has this problem. Unless the entire organization is aligned concerning its risk tolerance level, it’s difficult for security executives to secure budgets that are realistic to the risk associated with the company’s size, industry, or business model.
However, with a definitive, universal understanding of what an organization’s governance considers an acceptable level of risk in place, it becomes simple for security leaders — like you — to acquire the resources needed to improve cyber resilience.
Whether you work for a three-year-old company or a hundred-year-old company, the NIST Cybersecurity Framework is a tool you can leverage to assess enterprise-wide risks and foster internal dialogues to align your whole organization on its risk tolerance objectives. This, in turn, will help your team set better security priorities and secure the budget needed to mitigate IT risks adequately.
Related: Cybersecurity Measures and Internal Controls Needed to Adapt for Remote Work Environments
A breakdown of the 6 risk management framework (RMF) steps
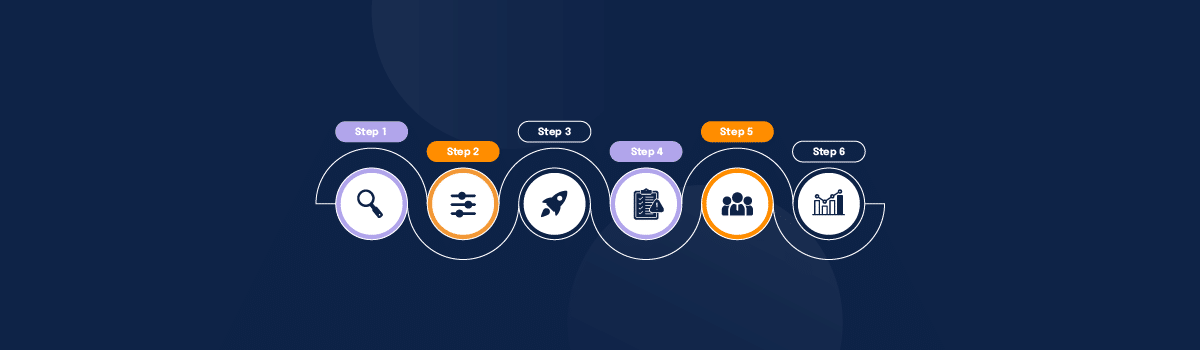
The NIST Framework for managing cybersecurity risks through the various levels of an organization is quite complex and full of various levels and steps. This section will cover the 6 RMF steps identified by the NIST to manage cybersecurity risks effectively.
1. Identify information systems
The first step in the process involves identifying and categorizing the different types of systems within the organization. Everything must be accounted for, including information types, information systems, and assets, in addition to the specific responsibilities and roles of the individuals who manage them. Finally, you’ll also want to log what each system’s intended use is and how each system connects to others.
2. Select specific security controls
The next step in the process is to select which security controls you’d like implemented and used as technical safeguards for your identified systems. These critical controls will protect your systems’ integrity, confidentiality, and information. These controls must be selected on the basis that they are effective in their application.
3. Implementing selected security controls
In this step in the process, the selected security controls from step two are implemented into their respective systems. Additionally, it must be described how each control is employed in its specific system of operation. These controls will be used to both posture and benchmark the success of your organization’s cybersecurity initiatives. Additionally, implemented policies should be tailored to the individual devices they’re aligned with and include the proper security documentation.
4. Assessment of implemented security controls
This step is used to benchmark the relative success of the security controls that you have in place. Thus, your security’s effectiveness is only as good as its ability to protect against threats effectively. Controls must be appropriately implemented to produce the desired outcome of the security procedures for specific devices and systems.
5. Authorization of information systems
Nearing the end of our six-step ‘cycle,’ this step requires reporting system control operational success and determining whether present risks are permissible to the organization. This step also involves the tracking of failed controls put in place. That said, organization stakeholders must grant permission for this step to occur to ensure that all organizational personnel are kept informed.
6. Monitoring security controls
The final step in fully implementing your cybersecurity management system is to continually monitor and update your systems. Thus, your system will reflect the dynamic and continuously evolving technologies and threats at any given time. Automated tools can help to increase the efficiency and effectiveness of your security systems and processes.
Learn more about NIST CSF in our ultimate guide
How the NIST cybersecurity framework can be applied

Several organizations have leveraged the Framework to create a risk heat map for their critical business function, driving organization-wide alignment on risk tolerance and prioritization. Below is the story of how Intel has utilized the Framework to achieve meaningful outcomes.
Proof positive: Intel case study
Intell used the Framework to create a risk heat map that can be used to set risk tolerance baselines, identify areas that need more detailed or technical assessments, identify areas of underinvestment and overinvestment, and assist in risk prioritization.
Intel divided its computer infrastructure into five critical business functions and piloted the Framework to perform an initial high-level risk assessment for one business function. They conducted the project in four phases:
- Set target scores: A core group of security SMEs set target scores, validated Categories, developed Subcategories, and performed an initial risk assessment and scoring. This phase helped the team validate that their approach could be a meaningful tool for prioritization and risk tolerance decisions.
- Assess current status: Separate from the core group, several individual security SMEs conducted an independent risk assessment based on the Framework. They individually scored the Categories and noted specific Subcategories where opportunities to improve existed.
- Analyze results: They used the heat map format to examine areas of concern at the subcategory level and further identify specific areas in need of improvement.
- Communicate results: They reviewed their findings and recommendations with Intel’s CISO and staff. This process fostered dialogue and helped the broader team agree on risk tolerance and prioritization.
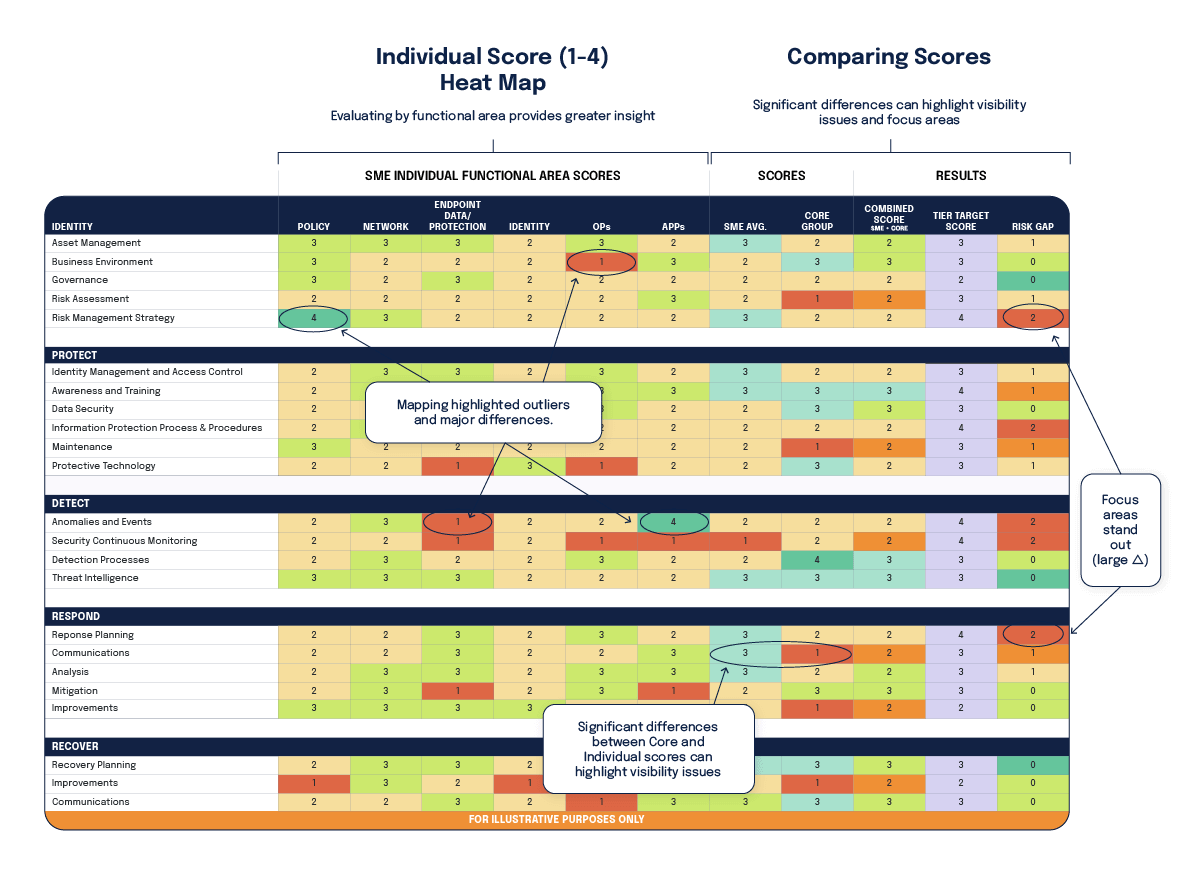
This process brought the organization several benefits. One of the most valuable was the internal dialogues it helped foster — risk conversations became grounded in a shared understanding of the threats, vulnerabilities, and impacts the organization faces, and the organization gained improved visibility into its strengths and opportunities to improve. All of this helps the organization set better security priorities and better deploy budgets and security solutions. Best of all, all of these results were achieved at a cost of under 175 FTE (full-time-employee) hours.
How to start putting the framework into practice

Suppose you’re interested in improving how your organization identifies, detects, responds to, and recovers from cyber risk. In that case, this framework is a solid tool to incorporate into your risk management practices. To maximize the benefits to your organization, you’ll need to tailor the Framework to meet your specific business processes and priorities, start where you’re comfortable, and commit to iterations with decision-makers throughout the process.
Lastly, it’s worth remembering that cyber risk management is not an end result, but an ongoing process of iteration and dialogue about risk.
If you’re interested in improving the culture around cybersecurity at your organization, sign up for a personalized demo with Hyperproof to see how we can support you throughout your entire compliance journey.
Next steps: How to implement NIST CSF with Hyperproof

The NIST CSF database represents the list of security controls and standards for federal agencies to architect and manage their information security systems. NIST established these guidelines to provide guidance for protecting agencies’ and citizens’ private data. While federal agencies are required to follow these standards, other organizations should follow the same guidelines.
Hyperproof’s compliance operations software can help organizations implement these guidelines, support ongoing control evaluation efforts, and improve the security of the organization’s information systems. Hyperproof makes complying with NIST guidelines easier by providing:
- A starter template with NIST CSF security controls.
- Tools to help you quickly collect evidence to verify the efficacy of various controls.
- A single pane of glass is included in all of your compliance efforts.
- The ability to leverage NIST CSF controls to comply with other cybersecurity and data privacy standards; the ability to map a control to multiple standards.
- A way to see your progress towards compliance, assign tasks, and prioritize work streams.
Get ahead with NIST CSF 2.0
As both cybersecurity threats and the frameworks created to help mitigate them continue to evolve, businesses must keep their security practices up to date. An important aspect of this will be navigating the upcoming changes to the NIST Cybersecurity Framework.
Want to learn more about how Hyperproof can stay NIST CSF compliant? Request your demo today.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












