Ransomware 101: How to Keep Your Business Safe From the Latest Trend in Cybercrime
Ransomware. Even the name has a sinister ring, leaving no doubt as to its malicious intentions. Yes, that’s right—ransomware is here and well-equipped to silently kidnap your businesses’ data and demand a small fortune for its return. Many organizations today believe ransomware isn’t an imminent threat—maybe they feel like they’re too small a target or have sufficient defenses in place.
However, the events of July 2nd, 2021, should serve as a wake-up call for all businesses. Kaseya, a Florida-based provider of Remote Management Monitoring software, experienced the most significant ransomware attack to date. REvil, a hardcore ransomware gang, exploited a zero-day vulnerability in Kaseya’s VSA remote management service, took control of their infrastructure, and pushed a malicious software update out to their customers.
The end result? Up to 1,500 organizations using Kaseya’s software were infected, and REvil demanded a $70 million ransom for the universal decrypter key needed to unlock the data.
The impact of ransomware attacks can be far-reaching; the cascading effects of the Kaseya attack impacted schools, businesses, and public administration offices around the globe. The Kaseya attack is disturbing for another reason as Katy-Jan Bobseine, former terrorism intelligence officer and current Director of Homeland Security Studies MS Program at Endicott College, explains: “What stands out about Kaseya is the extreme breach of trust, because many smaller companies rely on businesses like Kaseya for security services so, it’s like what are these companies supposed to do when even their security provider can be hacked?”
Kaseya is just the latest high-profile example of a dangerous trend where hackers exploit network vulnerabilities to compromise the manufacturer of a popular software product and then infect their customers. Ransomware is every organization’s problem today, regardless of size or industry needs to address it. All businesses must learn how to prevent becoming the next victim and see the dreaded words, “Your Files Are Encrypted,” flashing across the screen. In this article, you will learn about ransomware and what you can do to keep your organization safe from this potentially devastating type of malware.
What is ransomware?
Ransomware is a malware variant designed to secretly infiltrate computer systems, infect and encrypt files, then hold the data hostage until a ransom is paid in untraceable currency. This type of malware attempts to spread throughout connected systems or shared devices within the victim’s network. Encrypted files stay locked down until payment is rendered, but sadly paying is no guarantee of recovery, as 92% of organizations who pay the ransom never receive all their data back. Organizations hesitating to comply with the hacker’s steep financial demands often face the threat of their sensitive data being exposed on the internet.
Ransomware typically follows a similar delivery pattern initiated by a user tricked into clicking on a malicious link that downloads an infected file from an external website. The user unknowingly executes the ransomware file, which covertly takes advantage of system vulnerabilities to spread across the network. The ransomware encrypts all files, displaying a message on network devices demanding payment in exchange for a decryption key.
How will you know you’ve become the latest unsuspecting victim?
Ransomware encrypts files by adding a telltale extension to identify itself such as .ttt, .cryptolocker, or .petya. In addition, you will be greeted with a message like, “Your Files Are Now Encrypted,” followed closely by an open file with instructions for making the ransom payment.
Hackers typically use four infection vectors to deliver ransomware which include:
1. Third-parties and managed service providers
Kaseya is now the latest example of the type of breach where a hacker infects the provider of a widely used product, their downline of customers, and then potentially all of their customers’ customers. Threat actors exploit established third-party provider relationships by infiltrating trusted pathways to silently spread ransomware across numerous unsuspecting customer networks.
2. Internet-facing vulnerabilities and misconfigurations
Vulnerabilities on internet-facing devices such as servers, browsers, plug-ins, and document readers are often choice targets for hackers seeking undetected system access. Devices or security features not correctly configured or left enabled can provide easy points of entry. For example, the Server Message Block (SMB) feature, when loosely configured, can be readily compromised and used to spread ransomware across network systems.
3. Phishing
Hackers constantly bombard companies with emails spoofing trusted sources in hopes of duping a careless employee into clicking a link or opening a disguised email. Their tactics have become highly sophisticated, cleverly mimicking trusted sources to trick their way past human defenses.
4. Precursor malware infections
Threat actors take advantage of every opportunity to infiltrate a network, including the use of existing system malware infections to launch ransomware attacks. Hackers will identify an unresolved “precursor” system compromise and build upon it to launch ransomware throughout the target network. Ransomware is often the final step in a system compromise attack where hackers look to exploit existing system vulnerabilities over time.
How serious a threat is a ransomware attack for today’s organizations? Consider these numbers: by the end of 2021, an organization will fall victim to a ransomware attack every 11 seconds, with the average ransom topping $170,000 and the average recovery cost at 1.85 million.
As the Kaseya attack demonstrated, you don’t need to be the main target to feel the pain ransomware can inflict—you merely need to be a downline customer to experience the potentially devastating impact. The days of organizations ignoring this problem are over, and those clinging to the illusion they won’t be affected by ransomware do so at their own peril. “The ransomware problem today is unprecedented in terms of scope and the tenaciousness of hackers.
There’s historically been a lack of attention to the problem for many companies, combined with a false sense of hope that it won’t happen to them. Nobody is really secure, and no industry is safe. Every organization needs to recognize the urgency, view the problem like it could happen to them tomorrow, and actively work to protect themselves from ransomware attacks,” adds Bobsein.
Given the severe consequences and growing likelihood of occurrence, all organizations should have a plan to prevent, respond to, and recover from ransomware attacks.
Ransomware prevention strategies
Successfully preventing any cybersecurity incident—including ransomware—requires building and maintaining a comprehensive knowledge of your organization’s systems, people, assets, data, and capabilities. After identifying your critical resources, it’s possible to construct and implement the safeguards to protect them. Protection is necessary, but it’s only half the battle, as your team will need robust event detection and response systems to limit the impact of a ransomware attack. Your team will also need a rapid recovery plan to restore operations in the aftermath of an incident.
Ransomware can’t be eliminated with a few simple steps, and there’s no miraculous prevention recipe. The best strategy for countering ransomware is maintaining a holistic security program emphasizing multiple activities, including identification, protection, detection, response, and recovery. Below are some best practice suggestions to help keep your business from becoming the next ransomware casualty. Organizations looking to avoid the potentially devastating effects of ransomware should remember to:
Create and sustain an effective security program
Start with a system inventory to ensure you know your most valuable data’s locations, flow, and risk level. Assess all risks and vulnerabilities across your organization through continual scanning and examination of electronic records, physical media, key systems, services, and devices.
Assist your team in selecting and implementing the most current control system for managing environmental risks. Periodically check all your system devices for proper configuration and function. Remember to continually monitor and test the effectiveness of your risk management strategy and controls, as this step is critical to keeping pace with the evolution of current threat landscapes. Be sure to make corrections as needed and document lessons learned.
Protect data with the latest methods and technology
Arm your defense team with up-to-date strategies and weaponry, starting with an eye on prevention. Look at maintaining multi-faceted defense layers across the enterprise, emphasizing identifying and blocking threats before infection. Keep all system devices and software updated and patched while employing all traditional endpoint and network safeguards like firewall, antivirus, and antispyware protection.
Innovative teams engage analytic technologies to establish baseline network activity norms so anomalous actions can be easily spotted. Multi-factor authentication (MFA) and the least privilege principle help restrict unauthorized system access. Network segmentation helps prevent lateral movement across departments should a successful breach occur. All organizations should learn and follow cloud security best practices and ensure their third-party vendors do as well.
See how you can stay safe while using AWS services

Ransomware targets specific systems and functions, so consider specific preventative actions, like securing domain controllers, restricting the use of Powershell (a scripting language in Windows), disabling Microsoft micro scripts, and disarming the Server Message Block feature. Also, consider installing an intrusion detection system (IDS), email filter, and a Domain-based Message Authentication Reporting Conformance (DMARC) feature to lower the chance of spoofed emails from trusted domains.
Enacting an “application directory allow listing” policy to block the running of any unauthorized software across your network systems can prove helpful in thwarting ransomware. Lastly, creating a cyber incident response plan using a resource like the Public Power Cyber Incident Response Playbook will ensure your team is prepared with the proper response and notification protocols in the event of an incident.
Backup all data files (and then back them up again)
Maintaining backup copies of all your organization’s data in a secure, offline location is the most important action your team can take in preventing the headache and expense of your data being encrypted and held hostage. Securely backing up all your business’s data reduces the threat posed by ransomware—attackers no longer have the necessary leverage to demand a ransom and soon realize they need to find a less prepared victim.
Organizations should also maintain gold images of existing systems and backup hardware should a system rebuild become necessary. Reliable offline data backups have become mandatory links in modern ransomware defense chains. Zach Capers, the Senior Analyst for GetApp and accomplished author, explains,
“To avoid a ransomware attack’s worst outcome, you must also have a data backup and recovery strategy in place. But keep in mind that many ransomware variants also attack live backups. That means keeping an offline backup of your most critical data is necessary.”
Educate your team on best cyber hygiene practices
Employees can be your organization’s biggest asset or weakest link in combating ransomware, depending on their level of knowledge and diligence. “Despite their increasing sophistication, most ransomware attacks still stem from unpatched software, compromised passwords, and poor employee security practices. That’s why you must keep all software up-to-date, enable multi-factor authentication for all accounts, and train employees to recognize phishing and other social engineering tactics,” says Capers.
What do my employees need to know regarding adequate endpoint security?
All employees should learn the importance of limiting unauthorized and unnecessary system access. This means practicing MFA, maintaining minimum access privileges, and enforcing a strict password policy for all personnel. Employee training should emphasize disabling all unnecessary services, autoplay, Bluetooth, and file-sharing functions.
Employees should also be instructed on configuring email to block threatening files and ignore any unknown or unexpected attachments. Finally, your employees should be well-versed in using approved apps, trusted vendor lists, and the avoidance of software from websites known to share files.
Use ransomware protection software
Ransomware protection isn’t something your team should attempt without the support of certain types of software. Antivirus utility software can help foil ransomware attacks by denying unauthorized access to specific locations. Online backup utilities software sources essential up-to-date file replicas, which are crucial in checking ransomware.
There’s software specifically designed to identify and avert attacks using behavior-based detection to ground ransomware slipping past traditional antivirus defenses. There’s also software that protects files in Documents and Pictures, in local folders, and on USB drives preventing unauthorized programs from accessing files in protected zones.
The market is full of ransomware tool options, so how can you be sure which software products deserve consideration based on proven performance? The folks at PC Magazine simplified the vetting process, and here are their top ransomware protection tool choices:
- Best Multi-layered Ransomware Protection goes to Bitdefender’s “Antivirus Plus” product
- Best Dedicated Ransomware Protection goes to Checkpoint’s “ZoneAlarm Anti-Ransomware” product which also earned the honor of the overall top choice for ransomware security protection
- Best Ransomware File Recovery goes to Acronis’ “True Image” product
Ransomware response: Tips and key steps
Someday you might find that the worst has happened and you’ve received the dreaded screen alert informing you your business has been infected with ransomware, your data files no longer belong to you, and hackers demand an exorbitant ransom for their return.
Hopefully, your business will never experience this turn of events, but all isn’t lost if your team ends up facing this unpleasant reality. First, if initial mitigation isn’t an option, your team must begin an aggressive series of containment, eradication, and recovery action steps recommended by CISA, which are listed below:
- Take a system memory capture sample of infected devices, collecting relevant logs and examples of compromise indicators while being careful to preserve evidence
- Report the incident to Federal law enforcement and inquire about existing decryptors
- Research trusted sources for ransomware variants and follow steps to identify and contain the impacted systems minimizing the damage
- Formally identify all systems, accounts, and emails involved in the initial breach
- Contain any associated systems capable of providing further unauthorized access such as VPNs, remote access servers, or cloud-based assets
- Initiate server-side data encryption steps such as reviewing sessions/open file lists, properties of encrypted files, Remote Connection Manager event logs, and Windows Security event logs to gather information on file users and access events; also, run WireShark on any impacted servers to identify IP addresses involved in writing and renaming files
- Examine all detection and prevention systems (antivirus, Endpoint Detection and Response, Intrusion Prevention System) and logs to search for evidence of additional systems contributing to the attack or precursor “dropper” malware indicating other unresolved network compromises
- Conduct further analysis to identify outside-in and inside-out persistence mechanisms
- Begin system rebuild based on prioritization of critical services using backed up, preconfigured standard images
- Once the environment is cleaned and rebuilt, begin issuing password resets, patch vulnerabilities, and upgrading security software
- Based on the successful completion of the above steps, declare the ransomware containment and eradication phase complete
- Initiate system reconnection and data restoration using offline encrypted backup files while practicing caution to avoid reinfection of clean systems
- Document lessons learned from the incident to refine organizational policies and procedures for the future
- Consider sharing knowledge with CISA to benefit the community response
Recommended resources to help you counter ransomware threats and handle the potential consequences
Not sure how prepared your business is for a ransomware attack? Don’t wait until after the fact to find out— reference the Cybersecurity Framework Profile for Ransomware Risk Management published by the National Institute of Standards and Technology (NIST) and the Information Technology Laboratory (ITL) as your ransomware risk management guide. The Cybersecurity Framework Profile for Ransomware Risk Management identifies the Cybersecurity Framework Version 1.1 security objectives that support preventing, responding to, and recovering from ransomware events.
This Framework Profile examines five key phases—identification, protection, detection, response, and recovery— managing a ransomware incident.
It provides a helpful guide for determining how your ransomware management activities stack up against recommended best practices. Implementing the guidelines offered in the Cybersecurity Framework Profile for Ransomware Risk Management will give your organization a leg up in preventing and surviving a ransomware attack.
Download the Cybersecurity Framework Profile for Ransomware Risk Management
How Hyperproof supports ransomware prevention and response
Hyperproof’s compliance operations software makes it much easier for your organization to assess its readiness to handle many kinds of cyberattacks, including ransomware. Here at Hyperproof, we believe one of the best ways to protect your organization from all types of cyberattacks—including ransomware—is to implement a holistic security program where your security activities align with the guidelines and recommendations provided by well-recognized cybersecurity frameworks such as the NIST Cybersecurity Framework, NIST SP 800-53 or ISO 27001.
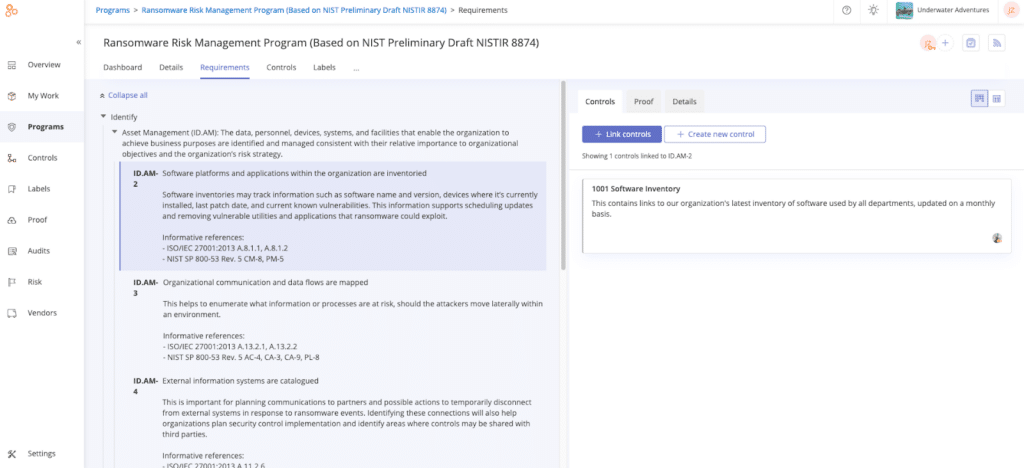
In Hyperproof, you can access the Cybersecurity Framework Profile for Ransomware Risk Management (Preliminary Draft NISTIR 8374) in a format that allows you to quickly conduct your own readiness assessment and gauge your organization’s ability to mitigate ransomware threats and react to the potential impact of events.
Hyperproof also makes it easier for organizations to directly reference additional cyber risk management frameworks like NIST Cybersecurity Framework version 1.1 or ISO27001. With Hyperproof’s built-in templates, you can see what activities each framework recommends for security and risk management, document the controls your organization already has in place, and quickly identify any existing gaps. Hyperproof’s solution platform simplifies the creation of a prioritized security roadmap and expedites remediation.
Further, Hyperproof isn’t just a useful platform for understanding your preparedness posture—it’s also a place to complete the remediation work. Hyperproof comes with project management features that allow security professionals to assign remediation tasks, track their completion, and receive automated alerts when something needs their attention. Hyperproof provides built-in dashboards and reports so stakeholders can measure progress and track how security efforts impact the organization’s risk profile.
To see how Hyperproof can help you implement a robust security program that provides protection against ransomware, book a demo today: https://hyperproof.io/request-a-demo/
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












