Guide
How Hyperproof Facilitates a Strong Privacy Risk Management Program
Why Paying Attention to Data Privacy Is Critical

Introduction
Businesses today encounter numerous data privacy risks when they collect, process, and store personal data or personally identifiable information (PII). At this time, there’s a multitude of state, federal, international, and industry-specific regulations (e.g., GDPR, CCPA, SOX, GLBA, HIPAA, FERPA, etc.) setting requirements around how businesses ought to collect, store, process, utilize, and dispose of PII. Many regulations also require businesses to disclose incidents where PII was compromised within a certain timeframe. To complicate things further, what constitutes PII is expanding under the laws.
At this time, businesses that do not invest in maintaining a robust privacy program can be fined hundreds of thousands or millions of dollars for a single privacy incident and lose hard-earned customer trust. As consumers became more privacy-conscious, lawmakers have broadened their view of what constitutes as PII in need of protection and begun to enforce privacy laws more stringently. This trend is evidenced by the 300 fines EU data protection agencies handed out for GDPR violations (as of December 2020). In 2020, the Information Commissioner’s Office (ICO)—the independent regulatory office in charge of upholding information rights in the interest of the public and the GDPR enforcement body in the UK –slapped seven- and eight-figure fines on corporations such as TicketMaster and Marriott International Inc. for failing to keep their customers’ personal data safe.
10 data privacy compliance pitfalls to watch out for

To ensure data privacy compliance, companies should create operating procedures that maintain data privacy, educate their workforce, and add access control measures around personal data. Below are the ten common errors businesses make that have serious legal, financial, reputational, and business continuity consequences.
1. Collecting and storing too much personal information
Any time a company collects and stores personal data or PII they take on the responsibility to take care of the data and abide by the privacy regulations in place. To lessen data privacy risks, a business should only collect personal data that it truly needs and only store it if it needs it for future use. When not managed, copies of personal data can diffuse through an organization, so businesses should also control the practice of copying personal data.
2. Using personal data for an unauthorized purpose
When collecting personal data, companies should be transparent about what data will be collected and how it will be used. Using the data for a different, hidden purpose, whether intentional or unintentional, would represent a compliance violation.
3. Vulnerable applications and insufficient data security
Applications, including Web applications, on-premise applications, and legacy applications exposed to the Web through modern APIs, storing personal data should be secured. If not secured, the personal data is at risk to be stolen or breached.
4. Insufficient procedures around access to personal data
The use or access of personal data should be restricted to those with a true need for the data. Access to applications, systems, and even specific data records that contain personal data should be restricted. Data privacy will be maintained not just through the presence of access controls, but also healthy practices and controls around maintaining passwords and access, such as when an employee leaves the company.
5. Insufficient processes for deleting personal data
Some regulations, such as GDPR, require companies to have procedures to delete personal data upon request. Procedures that do not remove or anonymize all personal data leave a company exposed to compliance violations and potential fines.
6. Insufficient responses around personal data loss
Some regulations, such as GDPR, require companies to inform people when their personal data has been stolen or accessed by unauthorized people. Procedures that do not adequately inform people within the required amount of time leave a company exposed to compliance violations and potential fines.
7. Lack of transparency regarding data collection and use
Data privacy regulations often require clear explanations of what personal data is collected and how the personal data is used. This information needs to be publicly available and easily obtainable and usually resides in policy documents such as a privacy policy, cookie policy, and terms of use statement. Some regulations, such as GDPR, have requirements that companies must divulge all the personal data stored about a person if that person requests that information. Failure to have such policies and failure to respond to information requests in a timely manner will cause the company to fall out of compliance with the regulation.
8. Sharing of data with third parties
When collecting personal data, a company should specify how that data will be used, including with whom that data will be shared. If personal data is collected and shared with a third party, such as an advertising/marketing partner or subcontractor, without the owner’s knowledge and consent, that would constitute a compliance violation.
9. Insecure data transfers
Personal data should be secured at all times, including when it is being transported from one system to another. This is typically accomplished through secure data communication standards such as SSL.
10. Not evolving your data privacy policy as your business changes
To ensure compliance with applicable data privacy regulations, businesses ought to revisit their data privacy policies and operating procedures whenever they make new business decisions, such as selling through a new channel, bringing on new third parties, launching a new product, purchasing new systems, or opening new offices in new states or countries.
Additionally, businesses need to think through the privacy implications when they roll out new operating procedures in times of disruptions. One example includes bringing employees safely back into physical workplaces in the midst of COVID-19 pandemic. A company should be aware that they are collecting personal data when they take body temperature readings to ensure an employee doesn’t have COVID-19 or ask employees about their personal activities as part of a contact tracing program.
What we’ve learned from GDPR enforcements
Upon a review of the biggest GDPR violations from 2020, regulators found privacy infractions were most often caused by the following practices:

For instance, H&M’s GDPR violation that resulted in a 35.3 Million Euro fine involved the “monitoring of several hundred employees”. After employees returned from sick leave, company management required employees to attend what they called Welcome Back meetings. The company recorded these meetings where employees talked about their health conditions and made the recordings accessible to over 50 company managers. The company violated GDPR’s principle of data minimization (e.g., collecting only the minimal amount of data you need for a specific purpose) and they didn’t have strict access controls on who could access confidential, employee health data.
To abide by data privacy regulations consistently, businesses need to maintain a robust data privacy compliance program on a continuous basis.
How Hyperproof can help businesses maintain strong privacy programs
1. Implement a privacy framework
At this time, privacy-conscious companies have begun to implement data privacy frameworks/standards such as the NIST Privacy Framework and ISO 27701 to apply greater rigor to their privacy risk management program.
The NIST Privacy Framework is a voluntary tool intended to help organizations identify and manage privacy risk to build innovative products and services while protecting individuals’ privacy. This privacy framework is intentionally regulations-agnostic, but it is crosswalked to the California Consumer Privacy Act (CCPA), EU’s GDPR, Brazil’s LGPD, ISO/IEC 27701 and to NIST’s flagship cybersecurity standard – NIST SP 800-53. By implementing the NIST Privacy framework, you’re choosing to look at all of your business processes with a privacy lens. You’re choosing to implement a set of privacy protection activities that allow you to effectively manage privacy risks arising from data processing. This type of focused effort will improve your organization’s capability in privacy risk management, and allow you to stay in compliance with multiple data privacy laws more easily.

ISO 27701 provides detailed guidelines for building, managing, and updating systems to keep private information secure on a continuous basis. ISO 27701 maps so closely to the requirements in GDPR that some groups in the privacy compliance space speculate enforcement agencies will eventually adopt it as a certification standard for GDPR.
With Hyperproof’s compliance operations software platform, it’s easy to implement the privacy framework of your choice and iteratively improve upon your baseline. Hyperproof provides a central location to document and manage all of your privacy controls, map controls to applicable data privacy regulations, and collect proof to attest that privacy compliance activities are performed in a timely manner. You can implement one set of privacy controls for your entire organization and map those controls to the requirements of various regulations, such as GDPR or CCPA.
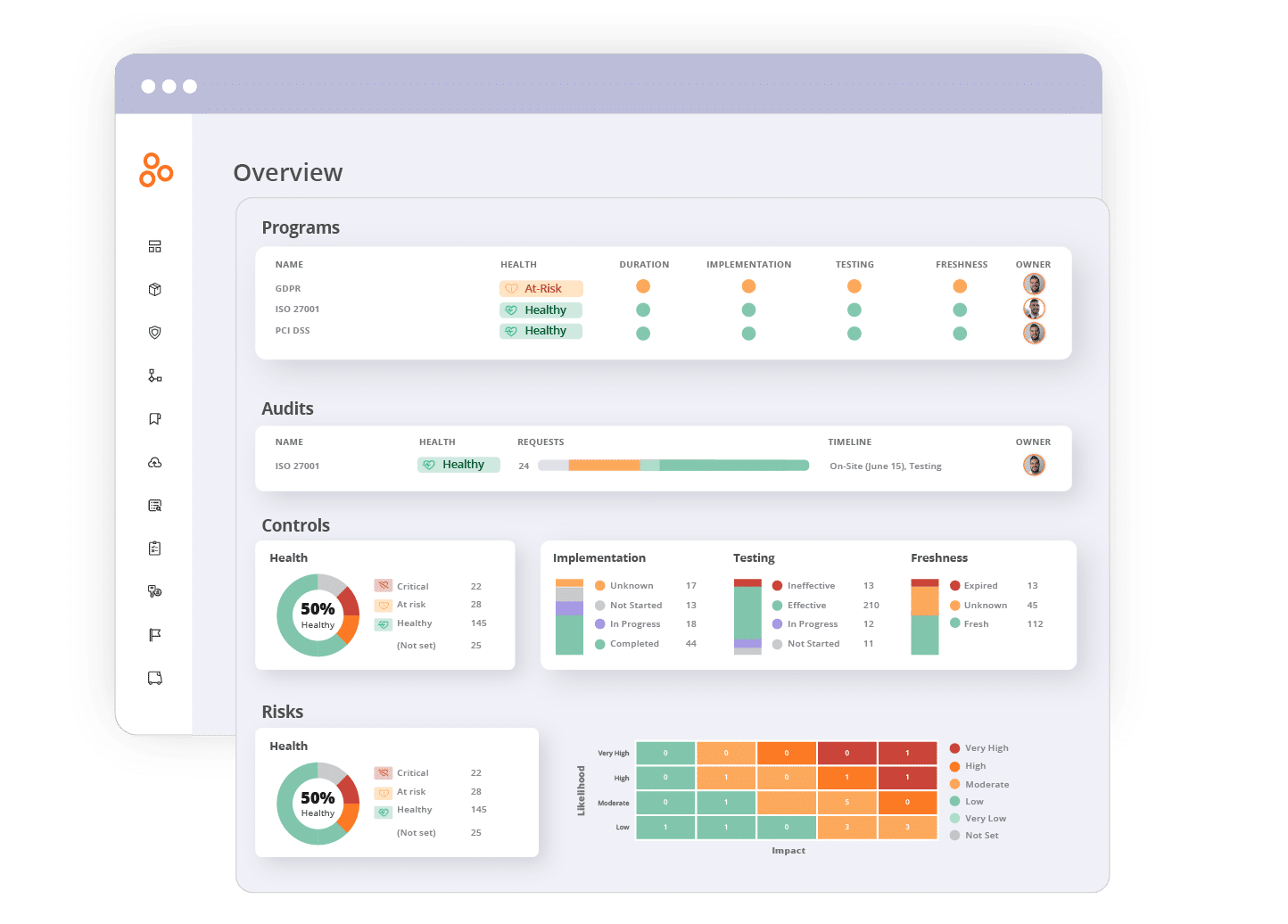
2. Assign ownership over data privacy and data security controls
Privacy incidents often happen not because people don’t know what the right solution is, but because someone didn’t implement the solution (or “control”) in a timely manner. For instance, an organization is well aware that applying software patches as soon as they become available is an important security measure and puts this requirement in writing in their security policy. But an IT manager may forget to deploy a software update or patch on a system — allowing hackers to take advantage of a vulnerability in the software and steal personal data within that application. Then, if a company fails to report the breach to the authorities and to their customers within a designated time frame, they would have violated privacy laws that require prompt disclosure of a breach.
Hyperproof helps organizations reduce human errors that can lead to privacy violations. For one, Hyperproof helps compliance and privacy professionals clearly communicate to people within and outside of their organization what their privacy responsibilities are and how they should perform those tasks. A privacy program manager can assign an owner to each control, write instructions for the control owner outlining how the control should be implemented, tested, and monitored, and the type of evidence they should provide to attest to the control’s effectiveness.
A compliance manager doesn’t have to manually remind control operators to provide proof of compliance activities anymore. The software can automatically remind people to submit fresh proof according to a pre-set cadence. When a control operator leaves the company or is out-of-office, it’s easy for a compliance manager to assign the control to someone else.
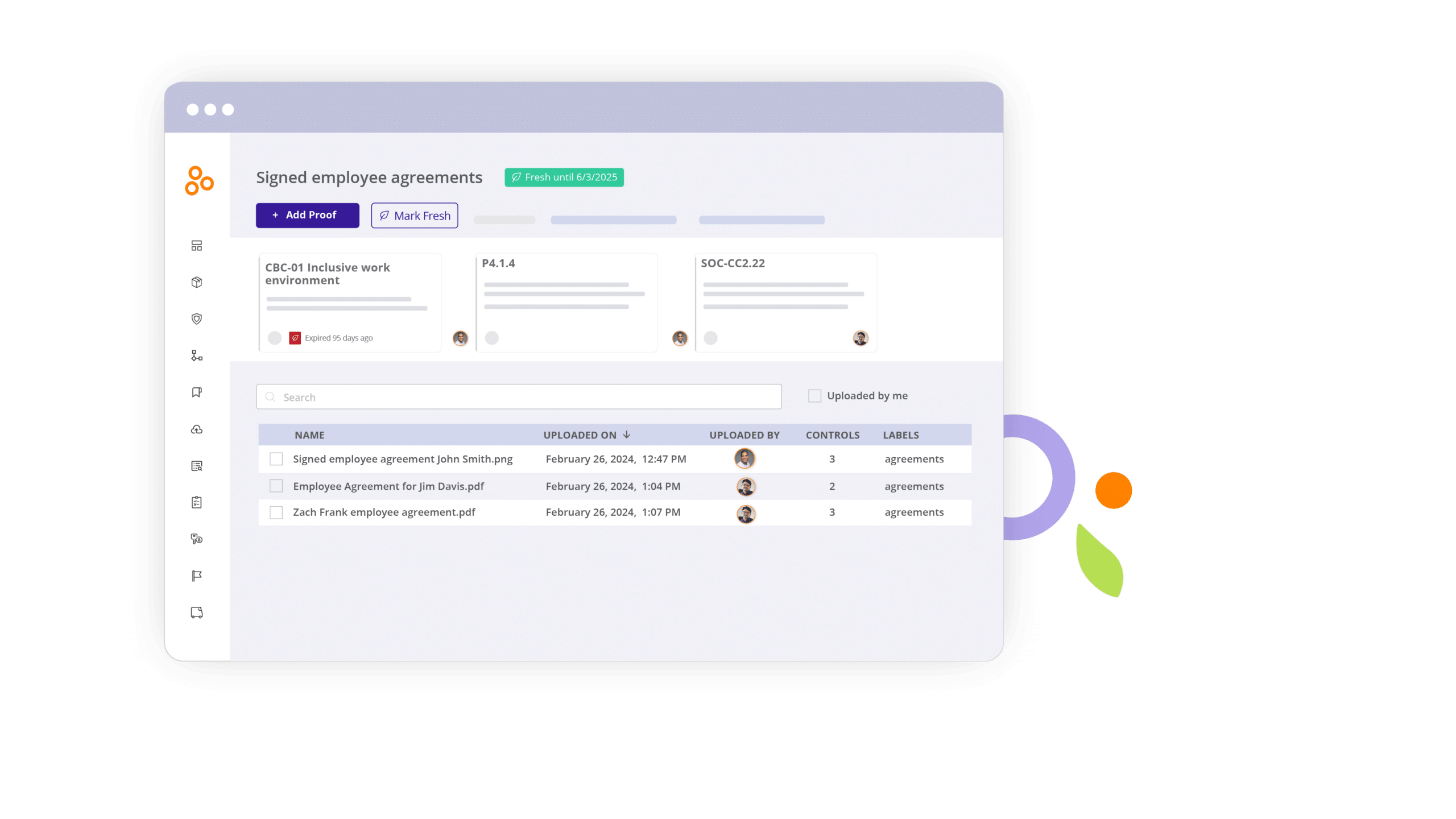
3. Monitor controls 24/7, 365 days a year
With Hyperproof, a compliance manager can set an appropriate cadence to review each control according to the risk it represents to their organization. Hyperproof takes over the job of reminding control operators to review the controls within their domain according to that cadence.
Through dashboards and drill-down reports, Hyperproof provides compliance leaders a holistic view of the performance of all controls within their organization. Compliance managers can use drill-down reports to quickly pinpoint control performance issues within specific domains, product lines, teams, and regions within their business.
Download the PDF