What You Missed at Gartner Security and Risk 2025: Adapting Security Strategy for an AI-Driven Future
Industry leaders and analysts gathered for Gartner Security & Risk 2025 from June 9-11 in National Harbor, MD. This year’s conference arrived as organizations worldwide grapple with artificial intelligence adoption, while 88% now report having GenAI capabilities in production. The timing was particularly relevant, with growing concerns about quantum computing threats and the need for comprehensive identity and access management strategies.
Hyperproof held a theater session with Blackstone, where we talked through strategies on achieving and then improving DORA compliance for financial services. In a separate session, we held a private CISO roundtable based on our findings from Hyperproof’s Summer 2025 IT Risk and Compliance Benchmark Report, where attendees related our findings to their experiences as CISOs. One of the most magical moments of the conference was when an industry attendee at the roundtable spoke about the challenges of working with the TSA for pipeline security, and the person sitting next to them was from the TSA and gave the regulator’s perspective on security; they found common ground, despite not having met before.
Conference sessions painted a picture of an industry at an inflection point. Speakers consistently emphasized that cybersecurity professionals must adopt adaptive strategies that account for AI’s probabilistic nature and the increasing velocity of threat detection and response.
Security teams are struggling to balance competing demands: enabling business innovation while maintaining protective controls, preparing for quantum computing threats while managing immediate AI risks, and scaling security expertise across distributed decision-making structures. Research presented throughout the conference suggested these challenges require fundamental shifts in how organizations approach risk management, threat intelligence, and technology adoption planning.
AI security strategies and investment priorities
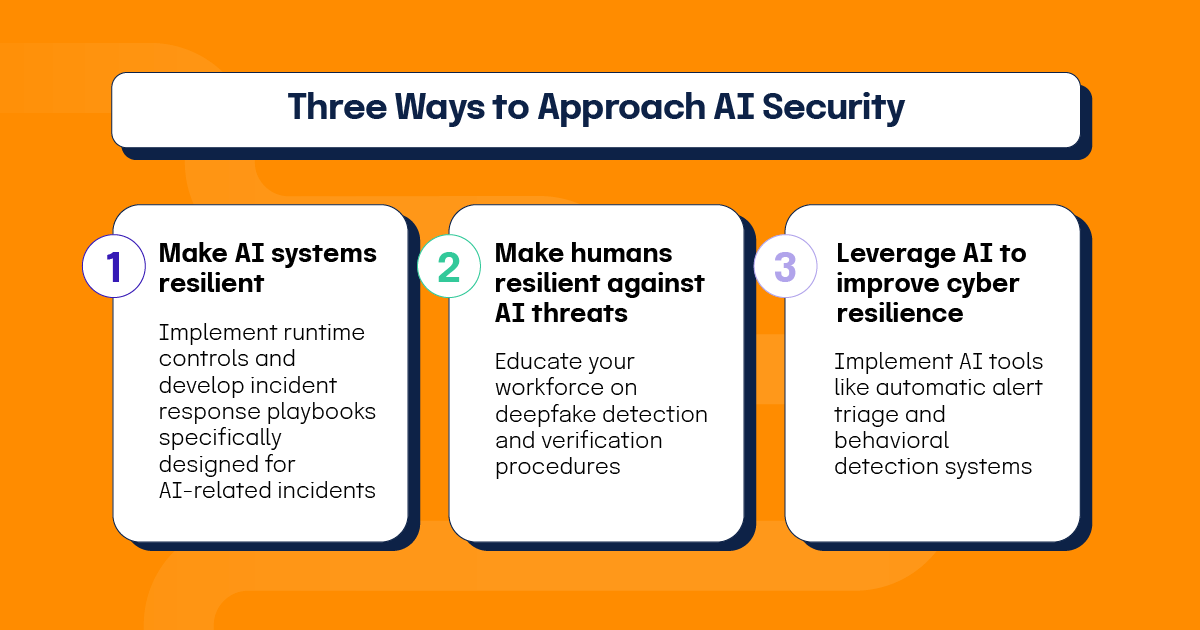
Conference presentations outlined a comprehensive framework for approaching AI security through three distinct perspectives: making AI systems resilient, making humans resilient against AI threats, and leveraging AI to improve overall cyber resilience. Speakers emphasized that AI’s probabilistic nature requires security teams to abandon deterministic thinking and accept unpredictability as part of AI’s value proposition.
The research suggested that by 2027, AI policies will be integrated into general technology procedures rather than maintained as separate governance frameworks. AI will become ubiquitous across business operations, necessitating that security considerations be embedded throughout organizational processes.
Current AI applications for cyber resilience already demonstrate significant value across multiple domains. CVE prioritization and remediation systems help security teams focus resources on the most important vulnerabilities. AI-led tabletop exercises provide more realistic and adaptive training scenarios. Automatic alert triage reduces analyst workload, while behavioral detection systems identify anomalous activities that rule-based systems might miss.
Making AI systems resilient requires implementing runtime controls and developing incident response playbooks specifically designed for AI-related incidents. Organizations need education programs addressing AI usage and hallucination risks, along with defenses against prompt injection, spiking, and stuffing attacks. Security fundamentals like data loss prevention (DLP), identity and access management (IAM), and policy enforcement remain important but require adaptation for AI-specific architectures and integrity challenges.
Human resilience against AI threats focuses primarily on deepfake detection and verification procedures. Biometric systems need capabilities to identify synthetic media, while multi-factor authentication becomes more important as deepfakes compromise single-factor verification methods. Business processes require hardening to include human verification for unusual requests, and video call platforms need deepfake detection capabilities.
Strategic priorities identified during the conference include recognizing that security is becoming a race of information velocity. Cybersecurity teams remain unprepared for AI agents that can operate autonomously and make decisions without human oversight. Deepfakes represent a primary attack vector that organizations must address immediately rather than treating them as a future concern.
GenAI investment patterns and technology adoption
Recent Gartner research shows that genAI investment patterns saw momentum across multiple technology categories. 55% of organizations have already invested via privacy-enhancing technologies, including homomorphic encryption, synthetic data, and confidential computing, with an additional 36% planning investments within 12-24 months. Model operations platforms with security features demonstrate similar adoption patterns, with 49% already invested and 38% planning near-term investments.
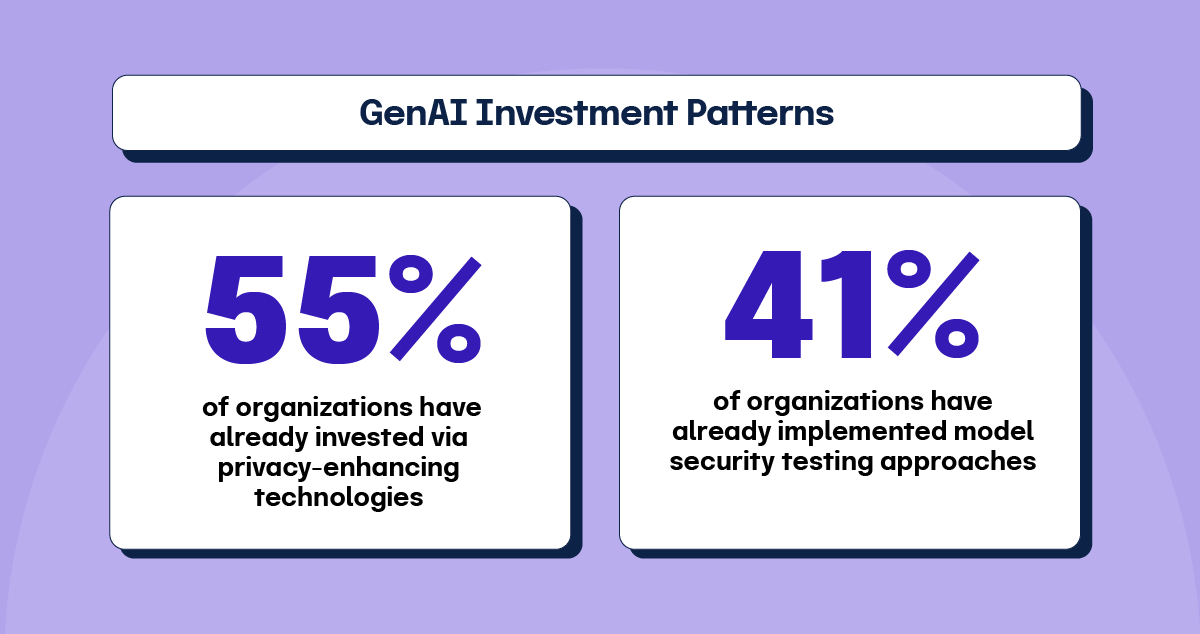
41% of organizations have already implemented model security testing approaches, including AI red-teaming exercises, with 45% planning investments. Runtime model monitoring and model risk management tools show strong adoption rates as companies recognize the need for continuous oversight of AI system behavior and performance.
Runtime prompt security technology represents an emerging investment area, with 44% of organizations already implementing solutions and 47% planning investments within two years. This technology category addresses growing concerns about prompt injection attacks and AI system manipulation through malicious inputs.
Organizations must balance immediate AI security needs with longer-term strategic technology adoption goals. The conference emphasized that AI security roadmap planning requires understanding both current capability gaps and future threat scenarios that may require different security approaches. Security leaders need frameworks for evaluating new AI technologies against existing security architecture while considering integration challenges and staff training requirements.
Security leadership transformation and organizational collaboration
The traditional model of centralized security oversight faces significant challenges as technology adoption becomes more distributed across organizations. In his session on ‘Implement Collaborative Cyber Risk Management to Enable IT Democratization,’ Oscar Isaka presented research showing that centralized approaches create bottlenecks, cause business interruptions, and provide a false sense of control over rapidly changing technology environments. Business technologists outside IT are 1.8 times more likely to behave insecurely despite being increasingly empowered to make technology decisions.
Effective collaborative risk management requires clear governance structures with defined responsibilities and owner accountability. Cross-functional teams must work together using unified frameworks for risk assessment and escalation procedures, supported by modern tools like Hyperproof that increase the efficiency and consistency of these processes. Communication becomes an important component for connecting enterprise risk management (ERM), legal, compliance, audit, and security functions.
Trust and verification models emerged as practical solutions for balancing autonomy with oversight. Oscar Isaka outlined three trust levels for decision-makers: low, medium, and high. Each level corresponds to different security activities, ranging from security-led implementations to self-administered procedures with appropriate validation mechanisms.
Johnson & Johnson’s Citizen Development Portal provided a concrete example of successful implementation. Their zone-based approach divides activities into green zones for minimal-risk projects with basic cybersecurity support and amber zones for activities involving sensitive data that require pairing with IT experts. This approach has enabled over 100,000 business technologist projects while saving more than 30,000 hours without requiring additional full-time security employees.
The transformed CISO role
Research from Gartner’s Evolution of the Cybersecurity Leader study revealed that 58% of CISOs now lead their organization’s AI adoption programs. In his session “CISO’s Outlook for Cybersecurity and AI: Building AI Resilience,” Dennis Xu discussed how security leadership in business transformation initiatives is becoming more important.
Successful CISOs must rebrand cybersecurity across internal stakeholders, shifting perceptions from a barrier to a business enabler rather than focusing solely on compliance and operations. Conference presentations outlined how security leaders should tailor their messaging: board directors need strategic business outcomes, Chief Revenue Officers require revenue protection narratives, and Chief Financial Officers need clear cost-benefit analyses with measurable forecasts.
In his session “The Real Cost of Cybersecurity,” Paul Proctor outlined three recommended CISO behaviors for defending budgets:
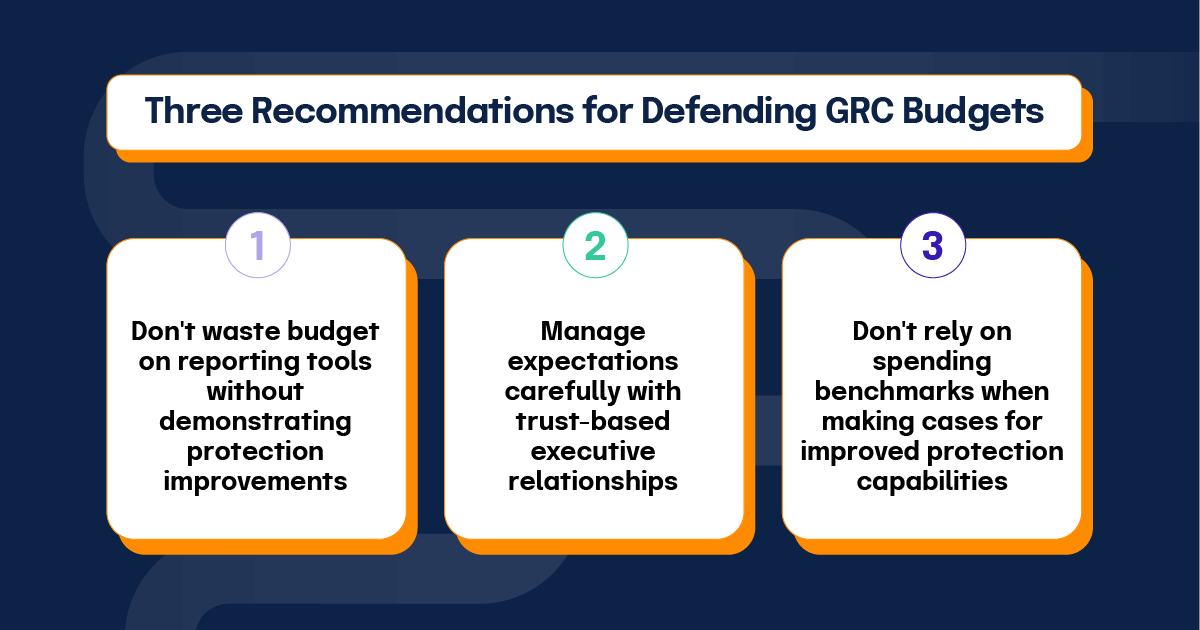
Modern CISOs need skills in developing branding messages, collaborating with marketing teams, and choosing appropriate communication channels for different audiences.
Governance framework modernization
Governance frameworks also featured heavily in leadership discussions, particularly the adoption of NIST CSF. Conference speakers suggested that mature cybersecurity governance can be achieved by using NIST CSF 2.0 to complement existing frameworks like ISO 27001, CIS Critical Security Controls, and COBIT rather than replacing them entirely.
Current CSF users should focus on category remapping, policy reassessment, and transition management. Prospective adopters were advised to consider partial implementation approaches that account for cultural shifts while taking advantage of available NIST resources. The roadmap development process should prioritize maturity assessment, supply chain integration, and privacy considerations.
Advanced threat detection and technology infrastructure adoption
Identity threat detection and response (ITDR) was a significant focus area, representing the convergence of infrastructure security and identity management. Conference presentations demonstrated how ITDR integrates with existing security tools, including security information and event management (SIEM), security orchestration, automation, and response (SOAR), network detection and response (NDR), endpoint detection and response (EDR), and extended detection and response (XDR) platforms.
Threat intelligence discussions centered on translating business requirements into actionable security capabilities. Speakers outlined a framework progressing from business input through security translation to detailed requirements. This approach ensures threat intelligence programs address organizational priorities rather than collecting information without clear business relevance.
Specific threat intelligence requirements include continuously assessing external attack surfaces for policy violations and imminent cyber threats. Organizations need capabilities to notify stakeholders within 24 hours when sensitive data, such as enterprise or customer credentials, is stolen or leaked by threat actors. Similarly, threat actor targeting requires notification within 24 hours when known adversaries conduct attacks against the organization or related industry verticals.
Detailed security intelligence requirements encompass vulnerability intelligence and threat actor profiles for groups actively exploiting organizational vulnerabilities. Organizations must search deep and dark web repositories for mentions of company keywords, credentials, and customer information while anonymously acquiring findings for validation purposes.
The conference also addressed the need for comprehensive threat actor intelligence covering adversarial operations against company infrastructure. This includes obtaining threat actor profiles specific to industry verticals and understanding the tactics, techniques, and procedures (TTPs) most relevant to organizational attack surfaces.
Infrastructure technology investment strategies
In his session “7 Essential Insights From the 2025 Cybersecurity Technology Adoption Roadmap Research,” Wayne Hankins positioned the Technology Adoption Roadmap (TAR) as a significant planning tool for organizations to benchmark technology adoption plans across security domains. The TAR helps organizations understand technology adoption timelines, risk factors, and value considerations for strategic planning.
A survey of 107 cybersecurity leaders revealed that deployment risk assessments consider implementation challenges, integration complexity, and operational disruption possibilities, while value factors analyze efficiency gains and security improvements. Infrastructure security technologies like Cybersecurity Mesh Architecture, Extended Detection and Response (XDR), and Network Detection and Response (NDR) occupy different positions based on enterprise value and deployment risk assessments.
High-value, low-risk technologies attract immediate attention for quick wins, while higher-risk technologies require pilot programs before full organizational commitment.
Implications for security leaders
Security leaders face unprecedented challenges requiring both immediate action and long-term strategic planning. The conference highlighted several predictions for cybersecurity through 2030 that organizations must consider when developing security strategies and investment priorities.
Geopolitical factors will materially shape security programs led by global Chief Information Security Officers (CISOs) by 2029. Organizations operating across multiple jurisdictions need procedures for adapting security programs to varying regulatory requirements and threat environments. This includes understanding how international tensions affect threat actor activities and targeting priorities.
By 2030, Security Operations Center (SOC) teams will experience skill erosion due to dependence on automation and artificial intelligence. Organizations must balance efficiency gains from automation with the need to maintain human expertise for complex threat analysis and incident response activities.
Privacy concerns will drive significant changes in data management practices, with 30% of organizations choosing to delete the majority of personal data rather than risk exposure by 2029. This trend requires security leaders to work closely with privacy and legal teams to develop data retention policies that balance business needs with risk reduction.
Third-party risk management will become more sophisticated, with 30% of organizations adopting business continuity and compensating controls for managing vendor relationships by 2028. Security leaders need frameworks for assessing and monitoring third-party risks that go beyond traditional security questionnaires and compliance certifications.
The Internet of Humans (IoH) represents a new threat vector that could jeopardize human life by 2029. Security leaders need to consider the security implications of technologies that directly interface with human biology and nervous systems.
Implementation success requires security leaders to adopt the role of “ringleader,” providing coordination and guidance across distributed security responsibilities. This includes annual attestation and training procedures, general coaching and advisory services, threat trend analysis for different stakeholders, and quarterly updates and newsletters to maintain awareness and engagement.
Security leaders must also prepare for the integration of post-quantum cryptography standards while managing current AI security challenges. Conference speakers suggested that advances in quantum computing will make conventional asymmetric cryptography unsafe by 2029, requiring organizations to begin planning transition procedures immediately. This dual focus requires careful resource allocation and strategic planning to address both immediate and future threats effectively.
The conference demonstrated that successful security leadership in 2025 and beyond requires abandoning traditional compliance-based approaches in favor of collaborative, adaptive strategies that enable business innovation while maintaining appropriate risk management. Organizations that master this balance will be better positioned to thrive in an increasingly complex and dynamic threat environment.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












