5 Strategies For Hiring & Retaining Cybersecurity Talent
As the CISO, Head of Security, or CTO of your organization, you probably already know how difficult it can be to hire high-caliber cybersecurity talent. At this moment, organizations of all sizes and industries are increasingly concerned with cybersecurity risks and how security failures may result in compliance violations, reputational damage, and economic fallout. According to Hyperproof’s 2022 IT Compliance Benchmark Survey, 62% of survey respondents had plans to increase spending on IT security and compliance in 2020; 66% of respondents had plans to make new hires to support the compliance function.
There’s plenty of recent data pointing to a shortage of cybersecurity talent worldwide. For instance, here are the findings in the State of Cybersecurity 2019 report by ISACA, which polled 1,576 security professionals. The high-level findings included the following:
- 69% said their teams are significantly (21%) or somewhat (48%) understaffed;
- 58% said their enterprises have unfilled cybersecurity roles;
- 32% said it takes six months or longer to fill those positions – up from 26% reported in the same survey the previous year; and
- 82% cited better financial incentives, such as salaries and bonuses, as reasons for leaving an employer.
All of these data points naturally leads to this question, what should organizations do to attract experienced cybersecurity professionals to their organization? And how can organizations retain their existing high performers?
In this article, I’ll share a few key talent acquisitions and employee retention strategies relevant for experienced, technical professionals. I’ll also share some new salary trend data on popular cybersecurity job titles from PayScale to help you establish appropriate compensation ranges for your cybersecurity positions.
In this article, I’ll discuss:
- How to get compensation right
- Painting the full picture of the opportunity for candidates
- Helping your team minimize energy-sapping, administrative work around compliance
- Improving your team’s ability to respond rapidly to risks through technology
- Continuing to educate your leadership team on the importance of cyber risk mitigation
My perspective on this topic is grounded in my experience in a previous role at PayScale, a leading compensation management software company. While I was at the firm, I worked closely with in-house economists and researchers to conduct over a dozen studies that all rotated around a set of central questions: Why and when do employees make career moves? What are the common elements of great workplaces? How do organizations consistently attract, motivate, and retain high performers? I also spoke frequently with HR and Recruiting leaders from companies of all sizes and industries across the U.S. to hear their perspectives on these topics.
5 tips for recruiting cybersecurity talent
1. How to set the appropriate salary range
Getting compensation right requires you to have a pulse on the market. That means getting fresh, granular data on base pay and bonus pay for your cybersecurity job titles. Keep in mind that data always needs to be grounded in context. And before consulting data, the first step is to make sure your compensation strategy is aligned to your talent strategy and overall business strategy. For instance, before setting pay ranges, you want to make these decisions first:
- Who are you competing against for talent? Are they companies of a similar size or industry, or are they larger companies or companies from other industries? The answer may vary by role, department, and office location.
- How competitive do you want to be relative to other companies who are looking to hire from the same talent pool? For instance, do you want to pay at the top of the range or be somewhere closer to the 50th percentile? You will need to consider your overall financial situation and may consider targeting a higher percentile for roles you deem critical to your company and a lower percentile for roles you deem less critical to the company. Additionally, certain skills are important but difficult to find and should command a salary premium.
- How much do you want to use cash as an incentive for attracting talent vs. other levers such as flexible work hours/locations, career growth potential, L&D opportunities, or great healthcare benefits? What do your ideal employees value the most?
Once you have a definitive compensation strategy, you’re ready to look at salary data. Keep in mind that when you’re hiring niche talent, you need to be clear on which skills and experiences you need and have accurate compensation data so you can make competitive offers quickly. As the truism goes, time kills all deals. Thus, having your compensation strategy ready will help you keep momentum during the offer stage.
Recently, I asked PayScale to gather the salary information of a variety of different cybersecurity job titles. PayScale administers the largest real-time salary survey in the world with more than 150,000 new survey records added every month (see methodology). People completed a salary profile on PayScale’s highly popular website to find out how their pay stacks up against others in similar positions. The data PayScale collects is strongly correlated with the size of the pool being considered, representing the diversity of the general workforce. For this project, PayScale pulled this data from 37,702 employee salary profiles that were completed between Jan. 1, 2017, and Jan. 1 2020 by U.S. workers.
Job titles in this dataset include computer security specialist, data security administrator, information security manager, security engineer, information security analyst, director of IT security, cyber security engineer, security architect, and variations of these titles. Below, we disclose the total cash compensation for cybersecurity professionals in 2019. Total cash compensation includes base pay and bonuses.
Cyber security job salary trends
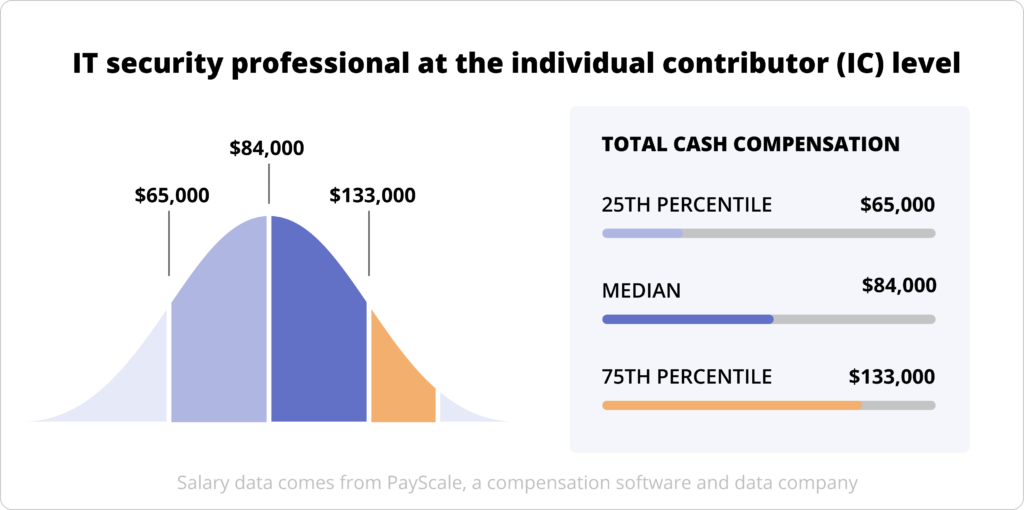
Median Pay for an IT security professional at the individual contributor (IC) level: $84,000
Salary range (25th percentile to 90th percentile): $65,000 to $133,000
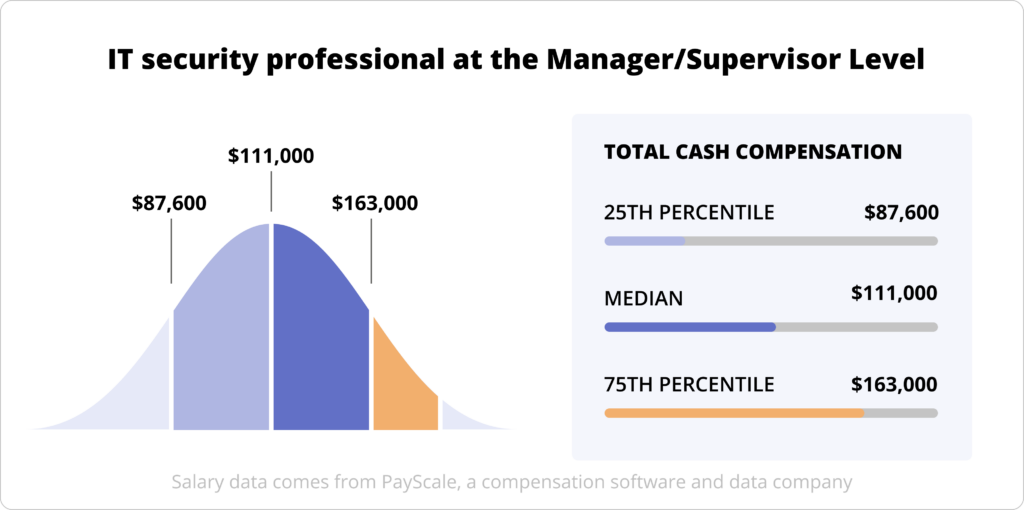
Median Pay for an IT security professional at the Manager/Supervisor Level: $111,000
The salary range for IT security professionals at the Manager/Supervisor Level (25th to 90th percentile of pay): $87,600 to $163,000
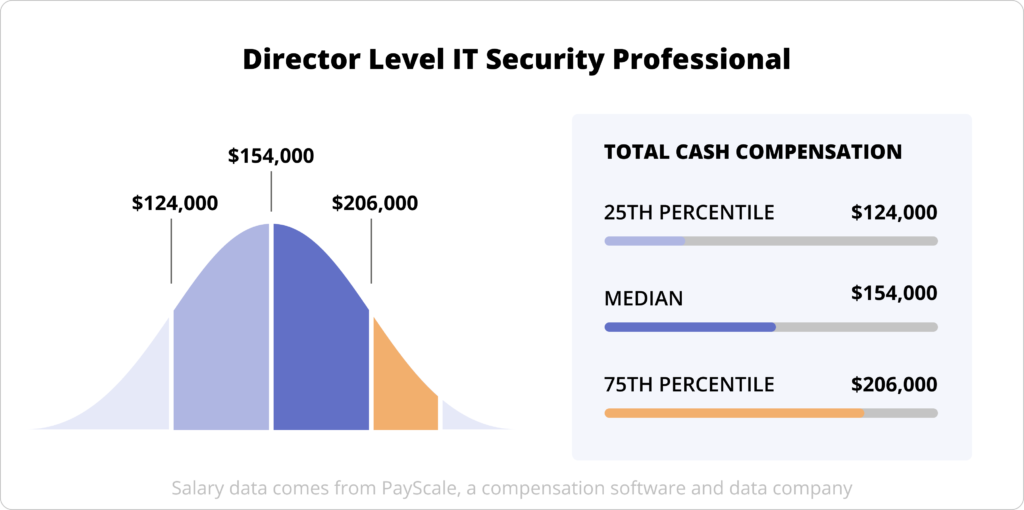
Median Pay for a Director Level IT Security Professional: $154,000
Salary Range for IT Security Professionals at the Director Level: $ $124,000 to $206,000
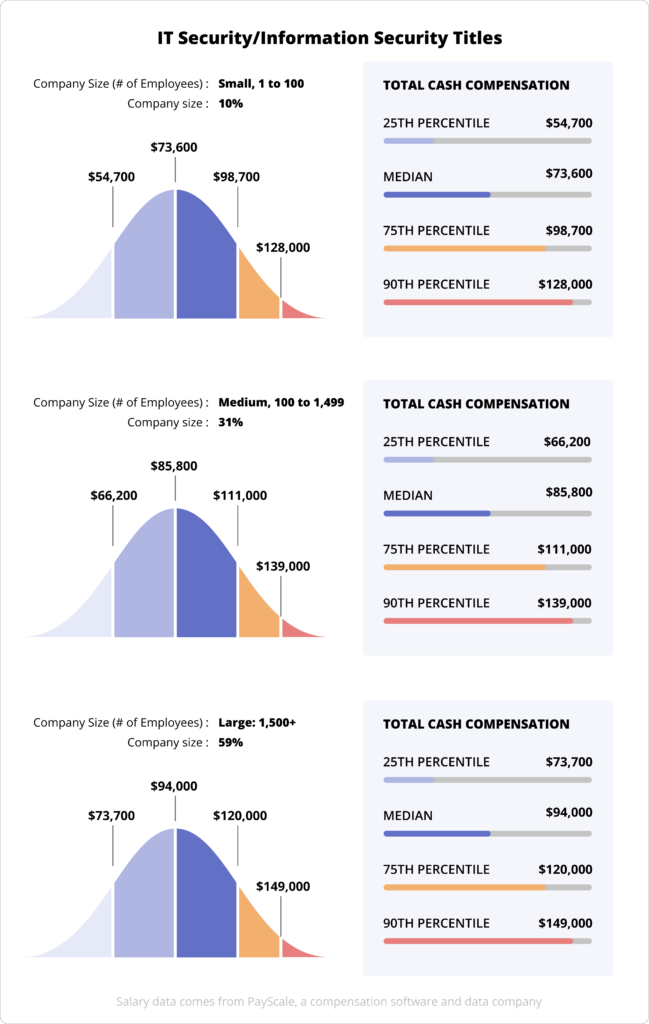
There are a variety of factors that impact pay, but one of the biggest ones is the size of the organization. When we look at the salary data by company size, it’s clear that bigger organizations are willing to pay a premium for cyber security talent.
Meanwhile, the industry itself and the location of a position also impact the compensation of a position (although we did not conduct this analysis for this particular dataset).
We also looked at the most prevalent skills and certifications among the cybersecurity professional population. Here’s what we found.
Top three skills for cybersecurity professionals
The top three skills for cybersecurity professionals are knowledge and experience in,
- Cybersecurity and trends
- IT security and infrastructure
- Security policy and procedures

Top three certifications for cybersecurity professionals
The top three certifications one should look for when seeking to hire a cybersecurity professional are,
- CompTIA Security+
- Certified Information Systems Security Professional (CISSP)
- Certified Ethical Hacker (CEH)

Interpret the data and make adjustments based on your particular context
Once you’ve pulled together salary reports (I recommend pulling reports from at least three different data sources), you’ll need to interpret the data and make adjustments based on your particular job requirements, budgetary constraints, and compensation strategy. You should consider the underlying characteristics of employers included in the dataset, such as organization size, industry, funding status (pre-IPO vs. publicly traded), and location.
Based on an analysis of hundreds of millions of salary profiles, PayScale has found that holding job title constant, the biggest drivers of variance in pay comes down to the following factors:
- Size of the organization. Larger organizations tend to pay significantly more for the same position compared to smaller organizations
- Location. Tech hubs in coastal cities like San Francisco, Seattle, Boston, and New York pay significantly more than other cities in the middle of the country.
- Professional skillset. Professionals with relevant and in-demand skills and certifications for their role command higher pay.
- Industry. Fast-growing industries like technology tend to pay more for the same position relative to stabilized industries such as manufacturing or hospitality.
2. Paint the full picture of the opportunity
While competitive compensation is a key component of an attractive job offer, it’s far from the only thing that matters. High performers often join organizations based on the nature of the work they get to do — they’re more likely to seek out opportunities where they get to do challenging, innovative work.
Here at Hyperproof, we’ve asked several cybersecurity professionals among our customer base about their career paths. When asked about why they’ve chosen to work in the security field, they often talk about their interest in solving difficult and dynamic problems, like experimenting with different ways of breaking through the defenses surrounding a network.
Besides challenging work, many workers value benefits such as flexible work hours/locations, paid parental leave, healthcare insurance, etc. As such, it’s important for you as the hiring manager to articulate all of the unique selling points of each job opportunity so candidates get the full picture. By doing so, you can minimize the chances that a candidate gets hung up on one particular element of the opportunity, such as a fairly average base salary.
3. Help your team minimize energy-sapping administrative work around compliance
In the last several years, cybersecurity jobs have become increasingly more stressful due to a variety of factors. For one, cyber security incidents are on the rise. Second, due to the prevalence of third-party data breaches, more and more organizations are requiring their vendors to produce SOC 2 and ISO27K certifications before they’re willing to sign new contracts. Meanwhile, the use of vendor-to-vendor security questionnaires will become more pervasive in the next few years. Responding to these vendor questionnaires and security audits may take up a significant portion of your cybersecurity team’s time and detract from other important work if you’re not deliberately managing these processes.
Your current cybersecurity team members and future hires should be prepared to take on a heavier compliance workload even though compliance isn’t what they signed up for.
In Hyperproof’s 2022 IT Compliance Benchmark Survey, we found that the typical IT security and compliance professional spends approximately 50% of their time at work on low-value, administrative tasks.
These administrative tasks include: Collecting and organizing compliance documents needed for external audits, searching through emails to find documents, reminding control owners to submit evidence, etc. If your team only needs to handle one or two audits every year, working through compliance-related tasks may be seen as a minor annoyance.
However, compliance work could become frustrating and even demoralizing if it piles up to the point where team members are unable to get to other high-value work (e.g., updating security controls, implementing new tools to improve response time to incidents, etc.).
As a leader, you can anticipate and prepare for this challenge by adopting tools to reduce administrative work from compliance processes. For instance, instead of using spreadsheets, file storage systems (like Dropbox), and emails to keep track of compliance documents and manage the ongoing work, you can use a compliance operations system like Hyperproof to manage everything in one place and save hundreds of hours per year.
Not only does Hyperproof serve as a single source of truth for all of your compliance activities, but it can also reduce the administrative work around collecting evidence and managing tasks (e.g., updating controls) by half.
Hyperproof comes with a set of features that enable greater efficiency, including:
- Crosswalk: Helps users identify the overlapping requirements and controls between various compliance frameworks. As such, compliance teams can manage a smaller set of controls to meet multiple compliance standards.
- Integrations with productivity tools and file storage systems where evidence is stored
- Collaboration capabilities between compliance managers, control operators, senior leaders, and external auditors
- Automated reminders to review controls and evidence
- Smart folders and labels to efficiently link a batch of evidence to controls
4. Improve your team’s capacity to quickly respond to emerging risk
The cybersecurity professionals you hire will no doubt bring a lot of risk mitigation experience to the table. However, given the sheer number of cyber threats that are now present in digital enterprises and how quickly they evolve, even experts will need help in effectively prioritizing and responding to risk.
For instance, deploying patches is an important component of vulnerability management. If patches are not consistently deployed at the time that they become available, your systems may be left exposed to vulnerabilities. As such, it is important to have visibility into control processes that were not timely performed so that you can quickly resolve issues. This is particularly important for high-risk areas like vulnerability management.
If your cybersecurity team doesn’t have the tools to help them understand what’s happening in real-time, they may be unable to deploy new controls in time to protect your digital assets.
And if your team is consistently hampered in their capacity to respond for a prolonged period, team members may start to consider opportunities at organizations that are willing to devote greater resources to cybersecurity.
As a security leader, it is your responsibility to establish visibility into all control processes, so team members (control operators) can make sure that controls are operating at the specific time interval, and in the same manner, as they were designed to. If you and your team members are evaluating control processes on a continuous basis, you have an opportunity to refine your risk management strategies in real-time.
Technology can make a big impact in helping your team refine your risk management strategy in real-time. For instance, you can use a compliance management solution like Hyperproof to keep all your evidence organized and linked to the right control/requirement and use automated reminders to alert control operators to review controls on a regular basis and submit evidence on time.
Additionally, Hyperproof has a feature called ‘Freshness.” You can set a ‘Freshness’ policy to remind yourself and your team to review controls on a cadence and ensure that all controls are appropriately evaluated throughout the year. This helps ensure that no one will forget any of their compliance tasks, which ultimately makes your entire organization more secure and resilient.
Besides using technology, the key to keeping team morale high is to listen to your team members. Get to know them as individual humans, know what they’re working on, understand what barriers they face in getting work done, and do what you can to unblock those barriers.
5. Continue to educate your leaders on the importance of cyber risk mitigation
Speaking of those potential barriers, one common barrier to improving an organization’s security posture is a lack of senior leadership involvement and support. To ensure that your cybersecurity team is well-positioned to address risks, it’s important to continuously educate your senior leadership team and board about the importance of investing in cybersecurity.
CEOs and business leaders must pull cybersecurity out of its silo in IT and spread the responsibility among their peers. For instance, the CFO must understand the financial impacts of a data breach. The CTO must understand how to build security into the product. The COO needs to understand how policy impacts operations, and how operations impact policy.
As a security leader, you’ll need to make continuing education of your leadership team an ongoing focus. This work matters because if leaders don’t see the strategic value in something, they won’t continue to invest in it, they won’t enforce the policies designed by your team, and they won’t send the right messages to frontline staff.
History tells us that when the market turns, companies tend to start to prioritize short-term profit over long-term strategic planning and put compliance efforts on the backburner. Given that an economic recession may be on the horizon, it’s important that you make efforts now to educate senior leadership about why prioritizing governance, risk and compliance is good business.
Related content: Download Hyperproof’s 2022 IT Compliance Benchmark Report to get key statistics you can use to build a business case for cybersecurity and compliance.
Hiring cybersecurity talent – final thoughts
With the market for cybersecurity talent heating up, now is the time to look closely at your talent acquisition strategy as well as the measures you’re taking to keep your existing staff on board. By getting compensation right, clearly conveying the full opportunity, and giving your team the right set of tools to effectively identify and mitigate risks, you can position your organization as an employer of choice in today’s highly competitive talent market.
Contact Hyperproof today to book a demo.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?