How to Obtain PCI DSS Compliance and Why It’s Important
The PCI DSS, or Payment Card Industry Data Security Standard, is a group of security controls designed to make sure all companies that collect and process credit card information maintain a secure environment. The PCI Security Standards Council created an independent body founded by major card brands, including Visa, MasterCard, and Discover.
Our guide covers all critical aspects of PCI DSS compliance, from organizations new to the PCI DSS compliance process. This information is sourced from the PCI Security Standards Council, the creator of the PCI Data Security Standards and the definitive authority on this subject. If you’re wondering how to get PCI compliance, the high-level process is simple: identify where you handle cardholder data, fix any security gaps to meet PCI DSS requirements, and then validate your PCI compliance with the right reports and scans for your merchant level.
What is PCI DSS?
Data breaches that compromise sensitive cardholder data are extremely prevalent. The five major payment brands formed the Payment Card Industry Security Standards Council to address the need for a secure payment ecosystem. Its mission is to help all merchants, providers, and payment software developers ensure adequate cardholder data protection. As a result, the Council created the PCI Data Security Standards (PCI – DSS) — a set of technical and operational requirements for processing payment transactions. By following these standards, organizations can minimize the damage from cardholder data theft.
Want a comprehensive guide on PCI DSS?

Is PCI DSS compliance necessary for your business?
Payment security assurance is required for all organizations that handle cardholder data. The benefits of maintaining PCI DSS compliance are essential to organizations’ long-term success that deals with cardholder data. By being PCI DSS compliant, your organization can maintain trust with customers who use their cards to purchase your products and services.
However, there are severe consequences for not protecting cardholder data. Your organization may face liabilities when you experience a security breach that results in payment card data being compromised could include employees losing their jobs and a loss of confidence from customers, among others.
What are the most common PCI DSS control failures?
Forensic analysis of compromises had shown that common security weaknesses are often exploited when addressed by PCI DSS controls because they either were not in place or were poorly implemented when the compromises occurred. Common failures that occur include storing sensitive authentication data (SAD) after authorization, poorly coded web applications, or a lack of logging and monitoring. Another problem stems from poor scoping decisions, which results in the cardholder data environment being exposed to weaknesses in the network that have not been secured to the standard.
Related: PCI DSS Requirements and Common Control Failures
When should you consider PCI DSS compliance?
Given the severe consequences of non-compliance, it’s not worthwhile to take any risks by handling payments before receiving official validation of compliance. In other words, you need to become PCI-DSS compliant before accepting any card data from clients and customers.
What are the specific requirements in the PCI Data security standard?
If you want to build and maintain a secure network, the first step is to install a firewall configuration to protect cardholder data. To protect stored cardholder data, you must encrypt data transmissions before sending them across open public networks. If you want to manage a Vulnerability Management System, you need to regularly use and update anti-virus software or programs to maintain security systems. To install strong access control measures, you need to restrict physical access to cardholder data and assign an ID to each person with computer access. Lastly, if you want to monitor and test networks regularly, you must monitor all access to cardholder data and test security systems.
How to get PCI compliance: What is the process for becoming PCI DSS compliant?
If you want to know how to get PCI compliance in practice, the PCI Security Standards Council recommends a three-step process: assess, remediate, and report.
1. Assess
Identify cardholder data and take inventory of information technology assets and business processes for payment card processing. Analyze the IT assets and business processes for vulnerabilities.
2. Remediate
Fix any vulnerabilities and get rid of the storage of cardholder data unless keeping it is absolutely essential.
3. Report
PCI DSS compliance validation is determined by the individual payment brands and acquiring banks since they’ve each incorporated PCI DSS into their data security programs. Check with your acquiring bank and the brands you accept payment from to see what you need to submit for your PCI DSS compliance assessment – typically an SAQ or ROC plus any required scan results – since you’ll be expected to submit reports that demonstrate your compliance status.
What are the compliance validation levels for PCI DSS?
What is a PCI DSS compliance assessment?
A PCI DSS compliance assessment is the formal review process used to determine whether your organization meets the PCI Data Security Standard. Depending on your merchant or service provider level, this assessment may be completed as a Self-Assessment Questionnaire (SAQ) or a full Report on Compliance (ROC) performed by a Qualified Security Assessor (QSA), often combined with quarterly network scans from an Approved Scanning Vendor (ASV).
A typical PCI DSS compliance assessment includes:
- Scoping your cardholder data environment (CDE) and identifying in-scope systems
- Testing security controls against PCI DSS requirements
- Documenting results in an SAQ or ROC
- Submitting required reports and scan results to your acquiring bank or payment brands
Becoming PCI DSS compliant will depend on your designated compliance level, which the individual payment brands determine. Generally, upper management will assign merchants and service providers with low transaction volumes (under 50,000 card transactions per year) to a lower validation level. These organizations will need to complete annual self-assessments and have them certified by Senior Management before submitting all reports to their acquiring bank.
Merchants with high volumes of transactions (e.g., over 2.5 million card transactions per year) will be designated to a higher validation level. Such organizations will be required to go through annual on-site security examinations by a Qualified Security Assessor (QSA) and submit reports of quarterly network scans conducted by an approved scanning vendor.
For an example of how payment brands designate validation levels and the requirements for each level, check out the reporting requirements for merchants and service providers from American Express.
For specific questions about compliance validation levels, you’ll need to contact your acquiring financial institution or payment card brand. Once you know what compliance level to aim for, you’ll need to submit the validation requirements to your acquiring bank, then report your compliance status to the payment card brand.
Small businesses can complete a self-assessment
If you are a small merchant or service provider who isn’t required to submit a full Report on Compliance (check with your financial institution), you can use a Self-Assessment Questionnaire (SAQ) to complete your PCI DSS compliance assessment. The SAQ helps you assess the security of your cardholder data environment and document how you meet applicable PCI DSS requirements. There are different types of questionnaires for different methods of accepting payment cards. To see which self-assessment you need to complete, visit the PCI Standards Council website.
Related: Who Needs to Comply with PCI DSS
Where are PCI DSS controls required and which systems need to be protected?
Implementing PCI DSS starts with scoping, which involves identifying all system components located within or connected to the cardholder data environment (CDE). Your CDE is made of people, processes, and technology that interact with cardholder data or sensitive authentication data. To determine what’s in scope, you’ll need to look at internal systems and networks and all connections from third-party vendors (e.g., business partners, firms providing remote support services).
You must identify all locations and flows of cardholder data to ensure all relevant system components are included as in-scope for the PCI Data Security Standard assessment. Scoping should be done annually and must occur before the annual evaluation. The PCI DSS also recommends organizations evaluate the flow of cardholder data in and out of the CDE. The general guidance provided by the PCI Security Standards Council is to assume everything is in scope until verified otherwise.
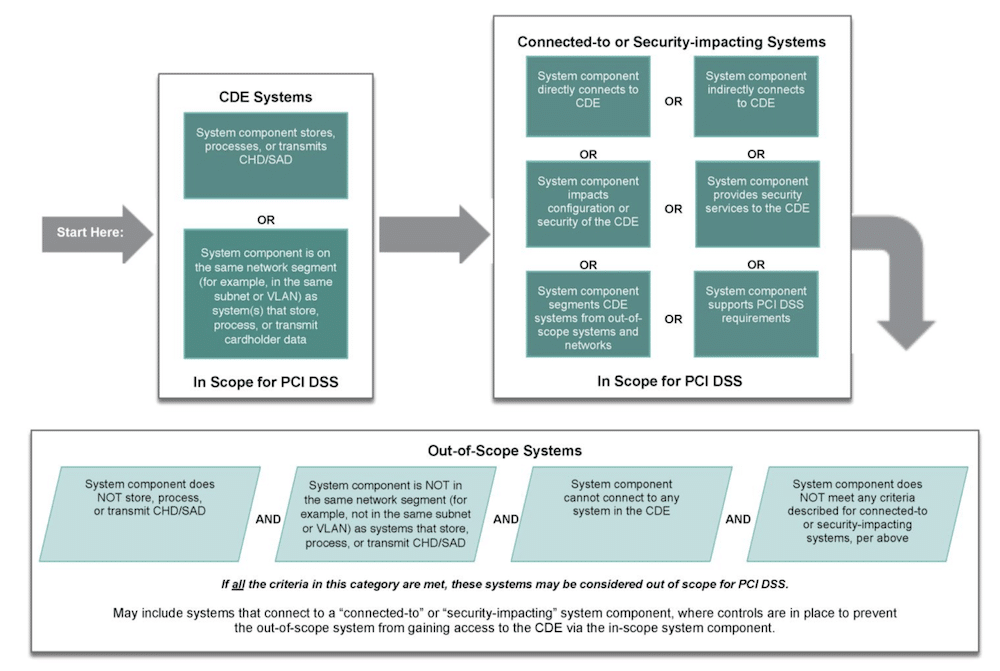
Ways to reduce the scope of PCI DSS
Don’t store cardholder data
The best step you can take to reduce the PCI scope is not to store any unnecessary cardholder data. For instance, if you don’t store the primary account number (PAN), the PCI DSS does not apply to that area of your organization, and the assessment’s scope can be reduced.
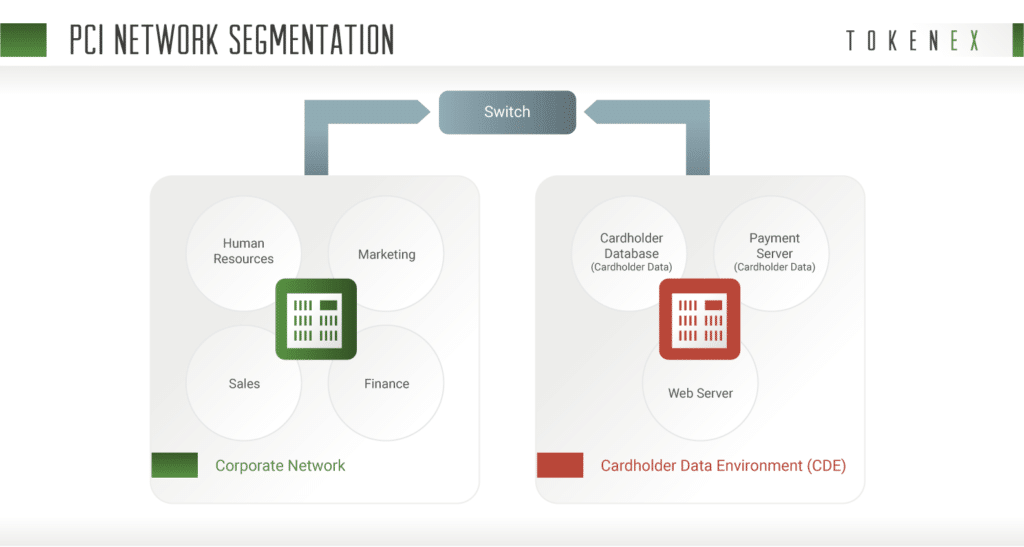
Segmentation
Segmentation uses additional controls to separate systems with different security needs. It can consist of logical or physical controls or a combination of both. These controls would keep your payment card processing systems from interacting with your back-office systems.
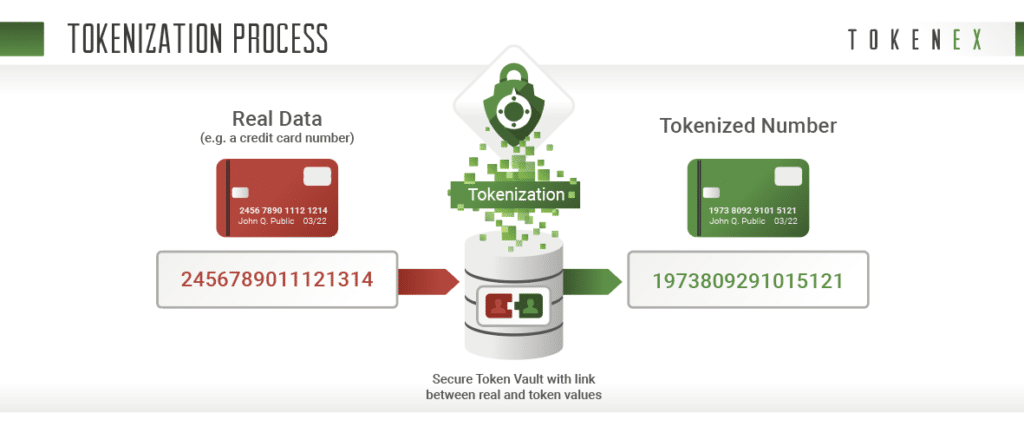
Tokenization
Tokenization is removing sensitive data from your business systems by replacing it with an indecipherable token to store the original data in a secure cloud vault. Essentially, the process allows you to outsource the handling and storage of sensitive data to a secured third party.
Outsourcing
Using a qualified vendor that is PCI compliant can reduce your PCI exposure. You could also have a hosted contact center/customer support solution, so payment card data flows through eCommerce and contact center environments without touching your operational environment.
Caveats for reducing scope of PCI DSS
The PCI Security Standards Council says that reducing the number of in-scope systems for PCI DSS compliance does not reduce your need for security measures. A system that is not in scope for PCI DSS may still need certain protections.
Based on forensic analysis, a typical pattern in data breaches is for an attacker to target systems deemed to be out-of-scope for PCI DSS. They will use those systems to gain more access and provide a digital path to where cardholder data can be found. Thus, implementing scope-reduction tactics should not replace a holistic approach to securing your infrastructure.
General tips and strategies for implementing PCI DSS
1. Limit the cardholder data you store
The best step is not to store any cardholder data you don’t need and isolate the data you DO need. It may be beneficial if you weighed the business benefits of storing data against the risks associated with storage, as well as the ongoing maintenance efforts to remain PCI DSS compliant over time.
2. NEVER store sensitive authentication data after authorization
Sensitive authentication data includes the full track contents of the magnetic stripe or equivalent data on a chip, card verification codes, PINs, and PIN blocks.
3. Ask your POS vendor or a QSA about your system’s security
If your business uses POS in retail locations, you need to ensure that your POS vendor has sufficient security measures by asking them how to mitigate common control failures. You can also seek assistance from a Qualified Security Assessor (QSA).
4. Compensating controls
If your organization has alternative controls that meet the PCI DSS definition of compensating controls, your organization can use such controls instead with proper documentation.
Related: Integrated Risk Management for Your Business

How does PCI-DSS fit into your overall compliance program?
Although PCI DSS covers a particular type of information, the controls and safeguards required to protect payment are similar to those needed in other frameworks. If you already have a robust information security program, you may meet certain PCI DSS requirements and the additional work may be insignificant. If you want to achieve compliance with other data protection standards, your PCI data security standards will likely give you a head start. Access control and employee training are just a few examples of compliance requirements that overlap in other cybersecurity frameworks.
Using Hyperproof to become (and Stay) PCI-DSS compliant
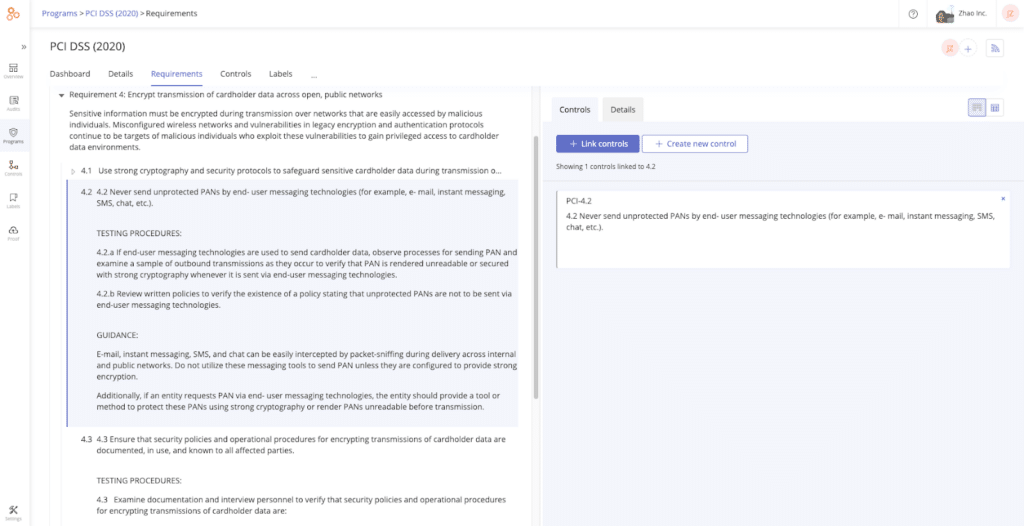
If you need to meet PCI DSS requirements and implement security controls to protect cardholders’ information, Hyperproof’s compliance operations software can make it simpler and faster.
Hyperproof allows you to easily view the requirements and controls for PCI DSS, collect evidence of operating effectiveness, and automate repetitive administrative tasks relating to compliance efforts. Through Hyperproof’s dashboards, you can easily view if evidence has been provided to demonstrate a network scan.
If you want to learn how to use Hyperproof to get started with PCI DSS, we’d love to talk!
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?