
The Ultimate Guide to
The Digital Operations Resilience Act (DORA)
The Digital Operational Resilience Act (DORA) sets out unified digital resilience rules for European Union (EU) financial services and their technology suppliers. In practice, DORA moves decisions about contracts, registers of information, testing, and incident reporting into daily operations, with clear expectations for boards, executives, risk leaders, and Information and Communications Technology (ICT) providers.

The scope of this guide spans roles for supervisors, required processes, and the artifacts regulators expect to see, including ICT service registers, contract terms, testing records, and incident reports. You’ll also find preparation steps, coordination patterns, post-deadline maintenance, frequent roadblocks, quick wins, and metrics that help track resilience outcomes.
What is DORA, and why does it matter?
DORA is an EU regulation within the Digital Finance Package that strengthens the financial sector’s ability to continue critical operations during ICT incidents. It became fully applicable on January 17, 2025, after a two-year implementation window and set binding requirements for complete operational resilience frameworks. For an official overview, see the European Insurance and Occupational Pensions Authority (EIOPA) DORA page.
DORA’s purpose is to keep critical services running and harmonize risk management across the EU financial sector. It requires ICT risk management systems, DORA-aligned contracts with third-party service providers, and complete registers of ICT services for oversight. Coordinate delivery across business, risk, legal, procurement, and technology, so implementation does not sit in silos.
DORA regulation creates a single, consistent framework across the EU so financial entities can withstand, respond to, and recover from ICT disruption. DORA is a regulation that became fully applicable on January 17, 2025, and binds financial entities and their ICT providers to end-to-end operational resilience practices.
Scope and applicability
DORA applies to:

The scope extends across emerging digital finance segments, so entities providing financial services in the EU sustain strong operational resilience against ICT disruption.
Compliance runs on two tracks. Financial entities operate risk frameworks and registers. Technology providers support those obligations through contract terms and disclosures. Financial entities should monitor whether the European Supervisory Authorities designate any technology providers as critical, then assess the operational impact. See the European Supervisory Authorities’ (ESAs) roadmap toward designating critical ICT third-party providers by the end of 2025.
The shift to operational resilience often requires upgrades or integrations with legacy ICT systems to ensure monitoring, reporting, and testing work function as expected. To be DORA compliant, you’ll need to collaborate across departments, so staffing and ownership align with ongoing obligations.
Importance for financial stability
DORA supports financial stability by addressing deep digital dependencies and by setting common requirements that limit the chance that a single ICT failure turns into a wider event. Standardized governance, registers, and contracting practices give supervisors and firms clear visibility of dependencies that can affect the continuity of critical services.

Risk frameworks must document technology dependencies, testing coverage, and change control with enough detail to prevent isolated failures from escalating. Run threat-led testing and cross-functional delivery, so resilience controls work together rather than as separate checklists. Penalties can reach up to 2% of annual worldwide turnover for financial entities and 1% of average daily worldwide turnover for designated critical ICT providers.
Key deadlines and timeline
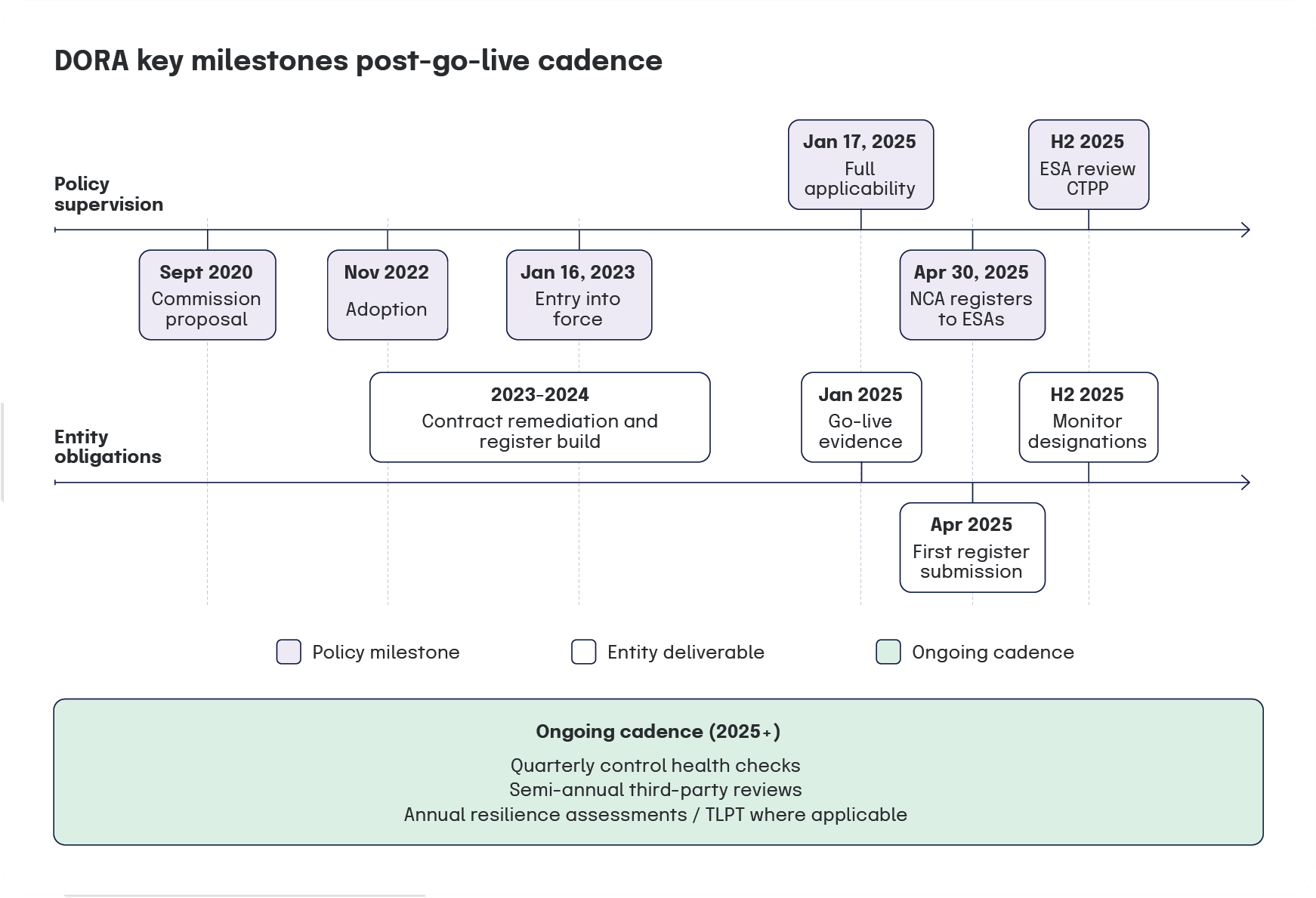
All covered entities and relevant ICT providers had to meet DORA requirements by January 17, 2025. National Competent Authorities (NCAs) delivered initial ICT registers to the ESAs by April 30, 2025.
The policy path began with a Commission proposal in September 2020, adoption in November 2022, and entry into force on January 16, 2023. The two-year window gave firms time to align systems and contracts before the 2025 date.
With DORA now in effect, the focus shifts to ongoing compliance: maintain contract compliance, keep ICT service registers current, and work with NCAs on submissions and follow-ups. European Supervisory Authority (ESA) review of registers in the second half of 2025 initiated critical provider assessments and heightened oversight for systemically important technology suppliers. Follow the ESAs’ critical ICT third-party providers (CTPP) designation roadmap for process milestones.
Clear requirements let teams deliver resilience with confidence.
What are the core components of DORA?

DORA regulation organizes ICT risk management, third-party governance, testing, and reporting into a consistent set of controls and evidence. These components translate policy into day-to-day practices and artifacts.
ICT risk management requirements
Document your ICT risk framework and a register of information covering services, providers, relevant subcontractors, and links to critical or important functions. Registers anchor oversight and help supervisors understand concentration and substitution constraints. The core framework is supported by the regulatory technical standards (RTS) on ICT risk management.
Core compliance actions
- Engage early with your NCA on register content and format so fields and identifiers match expectations
- Keep contractual work moving so agreements include DORA-required clauses that align with register entries
- Map controls and evidence to DORA articles so audits run quickly and cleanly
Technical implementation steps
- Upgrade monitoring, logging, and configuration management on legacy platforms, or connect them to modern tooling
- Track technical standards for subcontracting and threat-led penetration testing, and prepare to adopt them
- Watch for ESA critical designations and assess service-portfolio impacts
Organizational coordination requirements
- Assign clear ownership across technology, risk, compliance, legal, and procurement
- Establish a delivery rhythm that avoids duplicate work and closes gaps
- Resource the program so that run-state obligations do not stall after go-live
ICT service registers
Registers sit at the center of DORA’s oversight model, connecting services, providers, and business functions. After the first NCA submission cycle on April 30, 2025, the focus shifted to accuracy, completeness, and change hygiene.
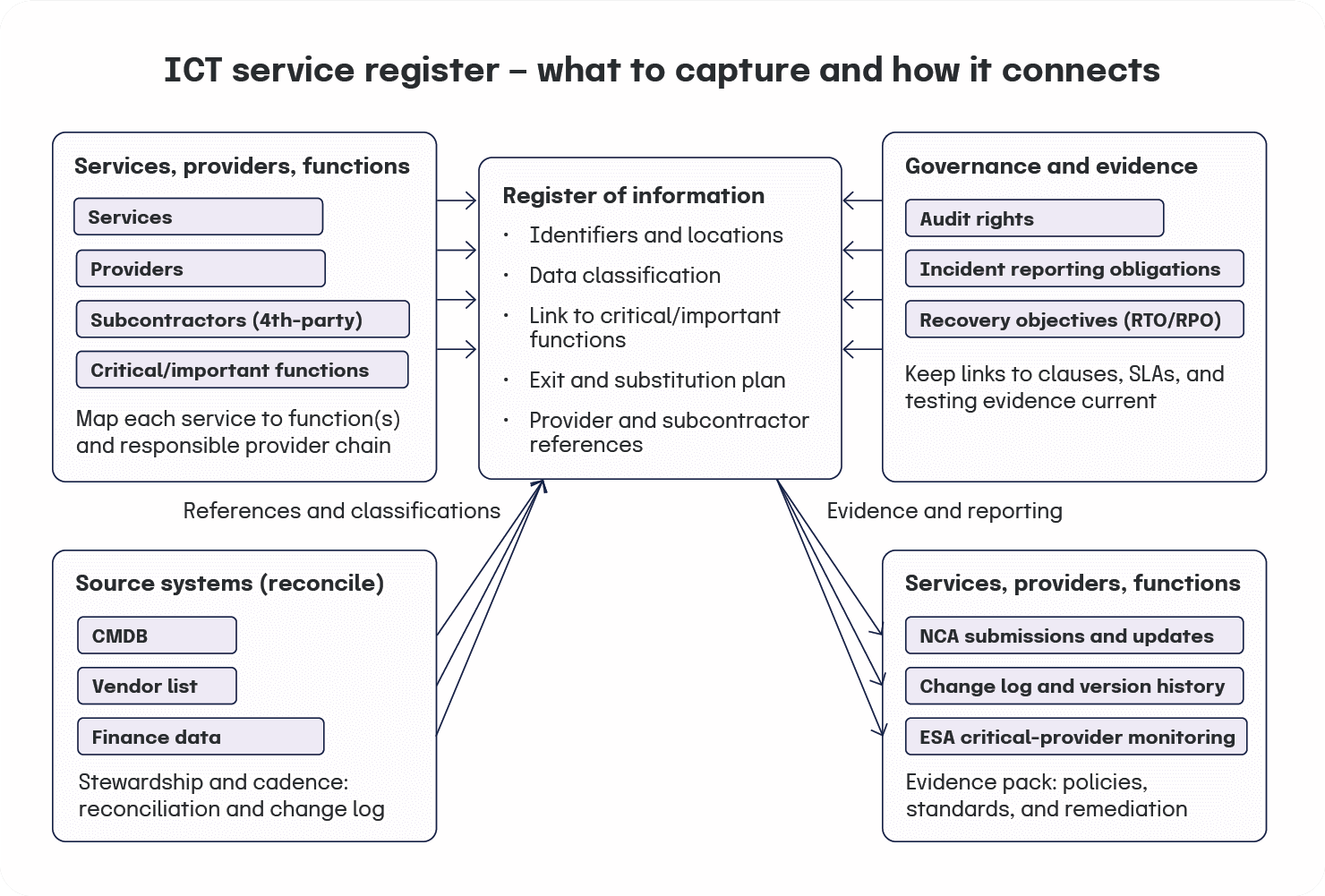
Purpose and required content
Include services, providers, and subcontractors where they support critical or important functions. Record identifiers, locations, data classifications, links to functions and processes, and exit arrangements. Capture audit rights, incident reporting obligations, and recovery objectives for each service. The detailed fields appear in the implementing technical standards (ITS) on the Register of Information. For implementation updates and background, see the European Banking Authority (EBA) press release on the register ITS process in 2024.
Ownership and cadence
Assign register stewardship and a maintenance schedule that updates entries after contract changes, service migrations, or architectural shifts. Reconcile Configuration Management Database (CMDB), vendor lists, and finance records. Keep a change log and versioning for supervisory review.
NCA touchpoints
When significant changes occur, align early with your NCA on timing and format. Keep a record of scope and classification decisions. Maintain identifiers that support timely resubmissions when requested.

Contractual arrangements with third-party providers (TPPs)
DORA requires written contracts with ICT third-party service providers that include minimum provisions for oversight, performance, security, audit, and termination. Many agreements required negotiation beyond January 17, 2025, to align with new terms. The minimum requirements appear in the RTS on contractual policy for critical or important functions.
Strategic negotiation approach
Coordinate sourcing, legal, risk, and technology so service definitions, audit rights, exit plans, and reporting clauses are consistent. Allocate capacity to refresh legacy contracts while handling renewals and new deals. Use a common clause library, so updates progress steadily.
Minimum contractual provisions framework
Cover service levels, incident reporting timelines, security standards, access and audit rights for the financial entity and competent authorities where applicable, data location and protection, change control, business continuity, and termination and transition support.
Ongoing monitoring obligations
Track ESA critical designations and regulatory updates that can shift obligations or evidence needs. Adjust contract language and oversight methods to reflect provider status and new standards.

Technical standards and testing
With contracts and registers in place, testing confirms that resilience controls work in practice. DORA references additional standards on subcontracting and threat-led penetration testing that set methods and scoping rules for testing programs.
ICT services subcontracting standards
Expect specific requirements for fourth-party oversight. Document subcontracting chains that support critical or important functions, and hold required information in the register. Reference materials include the ESAs’ July 2024 final report on subcontracting RTS, the Commission’s January 21, 2025 letter, the ESAs’ March 7, 2025 opinion, and the official register entry for the adopted subcontracting RTS.
Threat-led penetration testing framework
Standards define scenario design, scope, frequency, reporting, and remediation cycles. Simulate attack paths on systems that support critical or important functions and involve key providers when access is required. For incident classifications used to scope reporting, see the RTS on classification of ICT-related incidents and cyber threats.
Preparation strategies
Monitor publications from ESAs and the Commission, including guidance that clarifies which services count as ICT services for DORA purposes. Keep an internal tracker so policy changes translate quickly into controls, contracts, and registers. For official timelines and documents on major ICT incident reporting, consult the Commission’s register entry for the delegated regulation on timelines: register entry and the delegated acts documents portal.

Supervisory model: ESAs and NCAs
DORA supervision follows a two-tier model. NCAs supervise entities in their jurisdictions and enforce requirements. ESAs coordinate at EU-level and can designate critical ICT providers. The Commission has also outlined ESA oversight responsibilities in a dedicated delegated regulation: see the register entry and the documents portal.
ESA supervisory functions
ESAs receive register data from NCAs and run the critical provider designation process. A designation can change oversight intensity and introduce extra obligations for providers and their financial sector customers.
NCA enforcement responsibilities
NCAs conduct reviews, request evidence, and take action where gaps appear. Be ready to demonstrate how controls, registers, testing, and contracts satisfy the regulation.
Engagement approach
Keep open lines to your NCA. Align on register delivery, incident reporting channels, and testing notifications where required. Maintain a documented trail of decisions, assessments, and remediation progress.
Aligned practices turn policy intent into measurable resilience.
How do you implement DORA compliance?
DORA compliance is based on four delivery tracks. Start where the operational risk is highest, then build repeatable run-state habits that keep your evidence current.
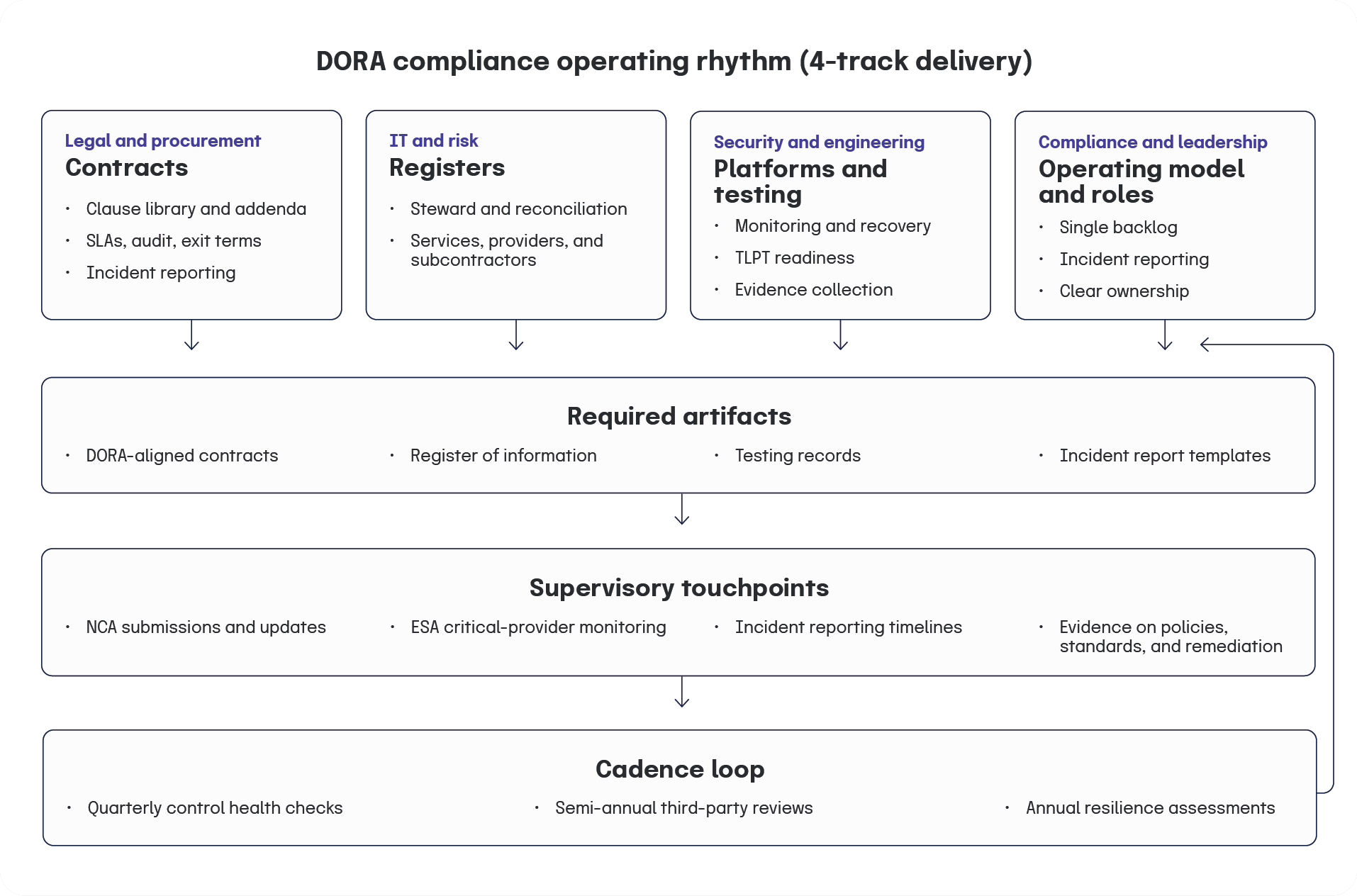
Contracts
Start with agreements that underpin critical or important functions. Refresh legacy terms that lack audit rights, exit support, measurable service levels, or incident reporting commitments. Use renewal windows and addenda to accelerate coverage and to reflect ESA designations when relevant.
Steps to keep the register accurate
Registers
Work with your NCA on required fields, identifiers, and coding. Capture services, providers, subcontractors where applicable, data flows, locations, and links to functions and processes. Keep the register synchronized with other inventories. Use the implementing technical standards (ITS) on the Register of Information as your reference for structure and content.
Platforms and testing
Assess monitoring coverage, logging quality, backup and recovery, configuration management, and identity controls. Plan upgrades or integrations so that data for classification, testing, and reporting is collected in a consistent way. Track progress against emerging subcontracting and threat-led testing standards, then feed results into service-level objectives and remediation plans.
Steps to operationalize testing
Operating model and roles
Define roles for framework ownership, register stewardship, testing leadership, contract stewardship, and incident reporting. Set staffing for both build and run phases. Run a single backlog across IT, security, risk, and compliance so platform work matches policy needs.
Clear ownership and a single backlog turn one-off projects into durable compliance.
How do you operate and work with supervisors after go-live?
Once the go-live date passed, programs moved into business-as-usual. The focus now is on systematic oversight, staffing, and evidence that supports supervision and enforcement.
Staffing and cadence
Stand up a small control office that tracks policy changes, register status, contract alignment, and testing coverage. Embed DORA controls in enterprise risk and internal audit plans so evidence flows without manual chases. Run quarterly control health checks, semi-annual third-party reviews, and yearly resilience assessments tied to business services.
Incident reporting timelines and evidence
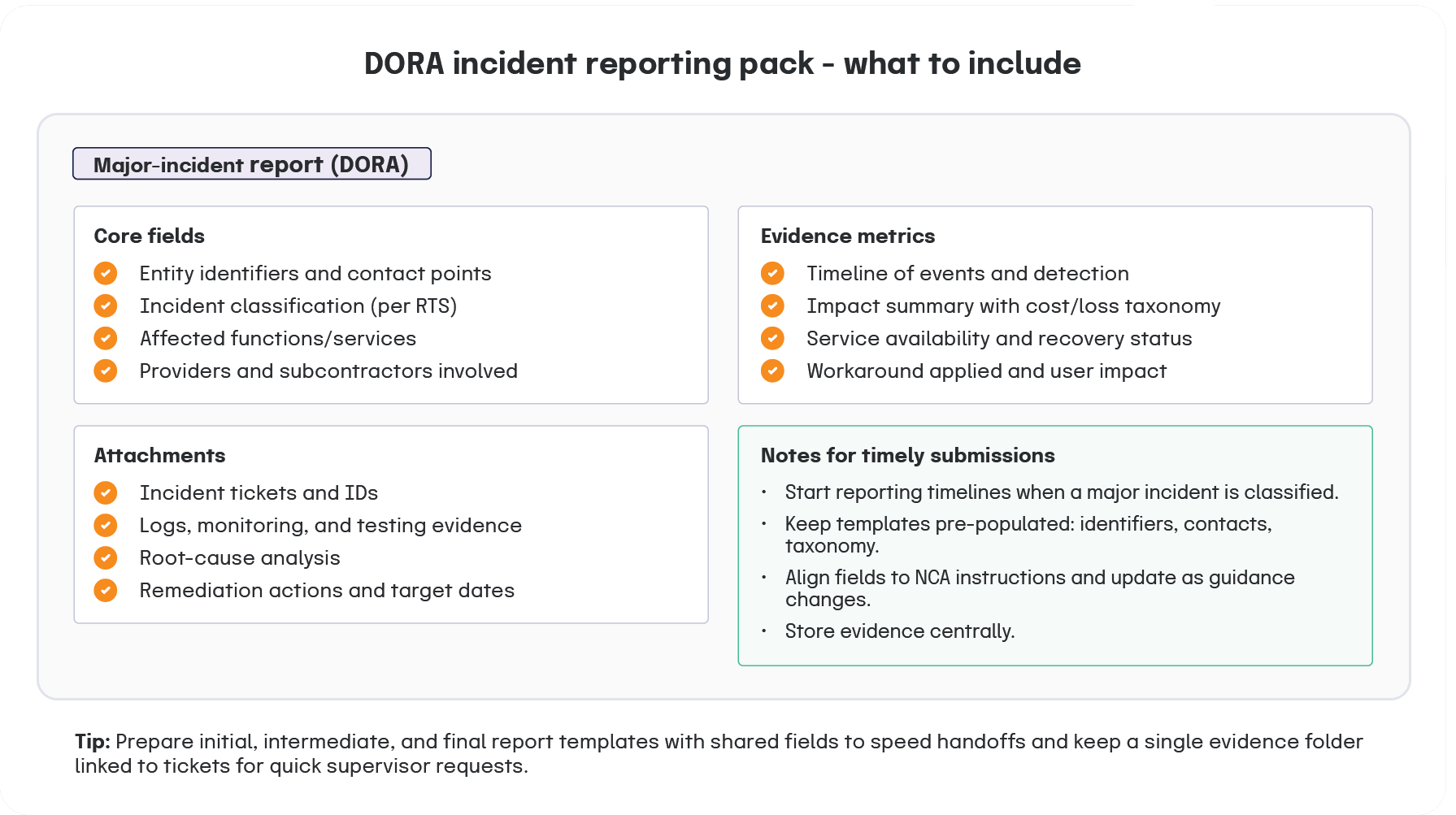
Plan for reporting timelines that start at the point of major-incident classification. Build templates for initial, intermediate, and final reports. Pre-populate static fields, including entity identifiers and contact points. Store cost and loss taxonomies so financial impacts can be rolled up consistently. Keep policies, standards, and procedures current and mapped to DORA articles. For official sources on reporting timelines, use the Commission’s register entry and the documents portal.
Enforcement readiness
Maintain an evidence catalog with references to policies, standards, procedures, reports, and tickets. Keep a change log for register updates and contract changes that affect risk. Document root cause analysis and remediation steps for incidents, including direct and indirect cost estimates and recurrence details. Log regulator interactions and decisions, and escalate material issues with clear actions and dates. For ESA roles and oversight scope, consult the delegated regulation register entry.
Monitoring critical TPP designations
Provider status can change obligations, reporting, and test scope. Monitor ESA communications, NCA circulars, and public registers. Set internal alerts so service owners and legal teams react quickly when a provider’s status changes. Assess impacts on access, audit, data location, incident reporting, and testing coordination. Where substitution is impractical, document mitigations and apply enhanced monitoring. Prepare playbooks for renegotiation and for transitions that might be triggered by enforcement. Track process updates via the ESAs’ CTPP roadmap.
Consistent routines keep supervision predictable and fair.
What challenges slow teams down, and what are quick wins?

The fastest progress comes from fixing a few common blockers, then locking in a repeatable rhythm built to survive staff changes and audit cycles.
Address coordination gaps by creating a single operating model
Siloed work between IT, risk, legal, and compliance leads to duplicate tasks, uneven priorities, and missed handoffs. Create a weekly working session to clear blockers, and use a shared tracker for contracts, register entries, testing scope, and incident workflows.
Weekly cross-team reviews reduce friction and speed measurable results.
Overcome legacy constraints through targeted modernization
Underestimating the work to add telemetry, backup and recovery, or configuration control on old platforms causes delays. Identify systems tied to critical or important functions, then add monitoring, strengthen backup frequency and recovery objectives, and harden configurations. Where changes are not feasible, plan for isolation and compensating controls.
Focused improvements on critical systems cut outage risk and audit burden.
Prevent contract drift with clause libraries and renewal playbooks
Contract updates can stall after initial deadlines. Use a common clause set for audit, incident reporting, continuity, exit, and data handling. Apply it at renewal and through addenda. Track coverage across services linked to critical or important functions.
Standardized clauses and a renewal playbook keep contracts aligned with DORA.
Control register sprawl through canonical ownership and cadence
Multiple inventories create inconsistencies. Assign a single steward and reconcile your CMDB, vendor, and finance sources. Update the register after service changes and contract events. Keep the change history for supervisor review. Anchor your process with the ITS reference text.
Dedicated stewardship and a set cadence keep the register accurate.
Move beyond paper-only testing with scenario-led programs
Paper-based testing misses real failure modes. Design scenarios that follow attack paths and failure chains for systems that support critical or important functions. Include providers where access is required, and feed findings into remediation and contract terms. Use classifications aligned with the RTS on classification of ICT-related incidents and cyber threats to drive consistent reporting.
Scenario-led testing exposes gaps and improves resilience.
Avoid post-go-live fade through fixed review rhythms
Programs can lose momentum after go-live. Use a quarterly rhythm to validate register accuracy, assess designations and their impacts, and adjust testing scope. Keep the cross-department forum active so delivery stays aligned with changing expectations.
Regular quarterly reviews sustain compliance and resilience over time.
What should you do next?

Key takeaways
DORA created a single framework for ICT risk and resilience across a large set of EU financial entities. It became fully applicable on January 17, 2025, and centered on five core components: ICT risk and governance, incident response and reporting, third-party risk management, digital resilience testing with threat-led exercises where applicable, and information sharing.
The scope extends to crypto-asset service providers, crowdfunding platforms, and ICT third-party providers, with a path for ESA designation of critical providers. Penalties can reach up to 2% of annual worldwide turnover for financial entities and 1% of average daily worldwide turnover for designated critical ICT providers.
Immediate actions and owners
Prioritize contract remediation and register completeness. Legal and procurement should take the lead on contract terms. IT and risk similarly should take the lead on registers and on the control upgrades that support testing and reporting. Compliance coordinates engagement with NCAs and tracks ESA updates, including critical designations and technical standards. Senior management sponsors cross-department work and keeps resources steady. Testing leaders plan scenarios for systems that support critical or important functions and schedule threat-led exercises where required.
Prioritize ownership and early remediation, then scale run-state routines.
Metrics to monitor and revisit cadence
Track the percentage of agreements aligned to DORA clause requirements, register completeness and accuracy, and modernization milestones for systems tied to critical or important functions. Review quarterly for control health, third-party risk posture, and policy changes.
Essential compliance metrics
Measure completion rates for contract updates and the number of services with current register entries that include providers and subcontractors, where needed. Track incident reporting timeliness and data quality.
Operational resilience indicators
Monitor adoption of subcontracting and testing standards, growth in automated evidence collection, and time to complete recovery drills for critical services. For subcontracting policy sources, keep the ESAs’ final report and the adopted RTS register entry in your toolkit.
Review and improvement schedule
Use a quarterly rhythm to validate register accuracy, assess designations and their impacts, and adjust testing scope. Keep the cross-department forum active so delivery stays aligned with changing expectations. Maintain momentum by measuring progress, scheduling reviews, and refreshing evidence.
Protect your financial institution and effectively manage digital risks with Hyperproof
Moving from DORA preparation to ongoing operational resilience requires the right tools and processes. Hyperproof accelerates this transition with ready-to-use DORA templates, centralized risk management, and automated evidence collection that integrates with existing technology stacks. The platform’s dashboard visibility and cross-framework mapping capabilities support the systematic oversight and fixed review rhythms essential for sustained compliance.
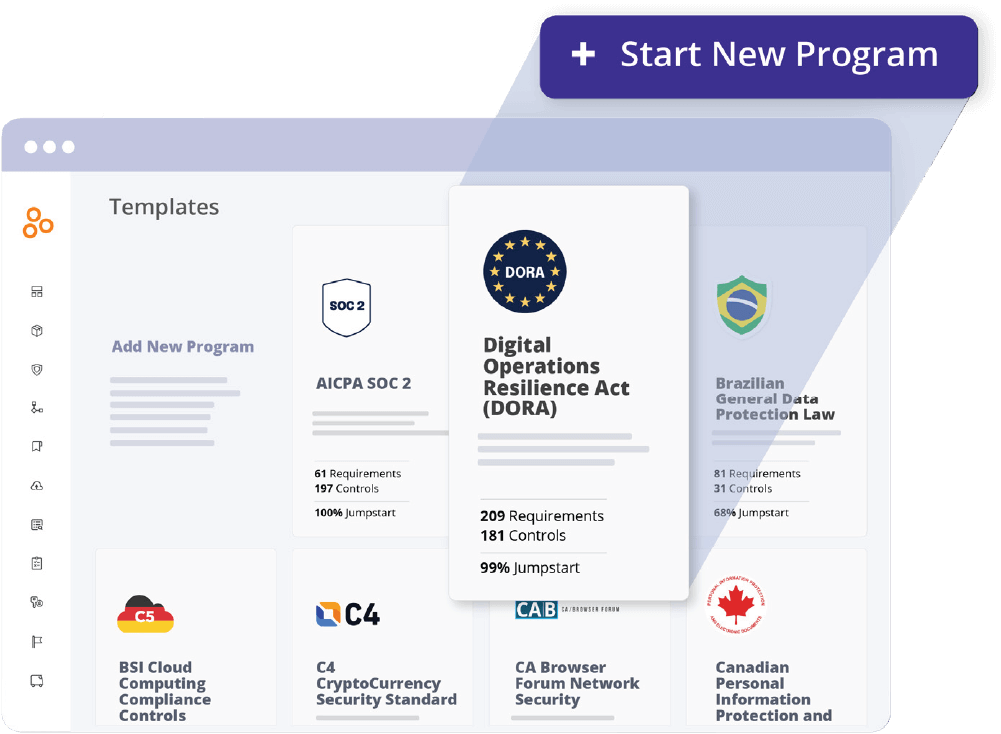
Jumpstarting DORA implementation with Hyperproof
Hyperproof’s Jumpstart feature lets you launch a DORA-compliant program in minutes by reusing the controls, labels, and risks you’ve already built for other frameworks like ISO 27001, SOC 2, or NIST CSF. Import relevant controls from other frameworks and link them to the appropriate DORA requirements, saving the time you’d have spent recreating the same controls from scratch. Hyperproof’s Smart Content feature also populates the risk register and label library with pre-mapped evidence placeholders, so you can immediately attach proof collected via Hypersyncs or uploads. Because the jump-start percentage shows how closely your existing control set matches DORA’s articles, you get instant insights into any coverage gaps that need remediation, allowing you to focus your resources on more strategic tasks. This rapid reuse of your existing controls dramatically shortens the time-to-compliance, reduces duplication of effort, and ensures a consistent, auditable foundation for your ongoing DORA obligations.
Leveraging Hypersyncs for automated DORA evidence collection
Hypersyncs turn the manual, time-consuming hunt for ICT evidence into a seamless, scheduled data pull that aligns directly with DORA’s core obligations. By connecting to the same cloud services and SaaS platforms that power your financial operations — AWS, Azure, Google Cloud, GitHub, ServiceNow, and dozens of others — Hypersyncs automatically collect the exact proof required for DORA’s ICT service registers, third-party contract attestations, and more.
The collected data is formatted consistently, tagged with timestamps, and linked to the relevant controls, labels, or vendor entries, eliminating duplicate uploads and ensuring you always have the latest evidence. When a Hypersync detects a change — like a new IAM role, an updated backup job, or a revised security group rule — it triggers a task or a notification, prompting the responsible stakeholder to review and certify the evidence before the next supervisory submission. Hypersyncs provide continuous, auditable proof that your organization’s ICT environment remains resilient and DORA-compliant without the overhead of manual evidence gathering.

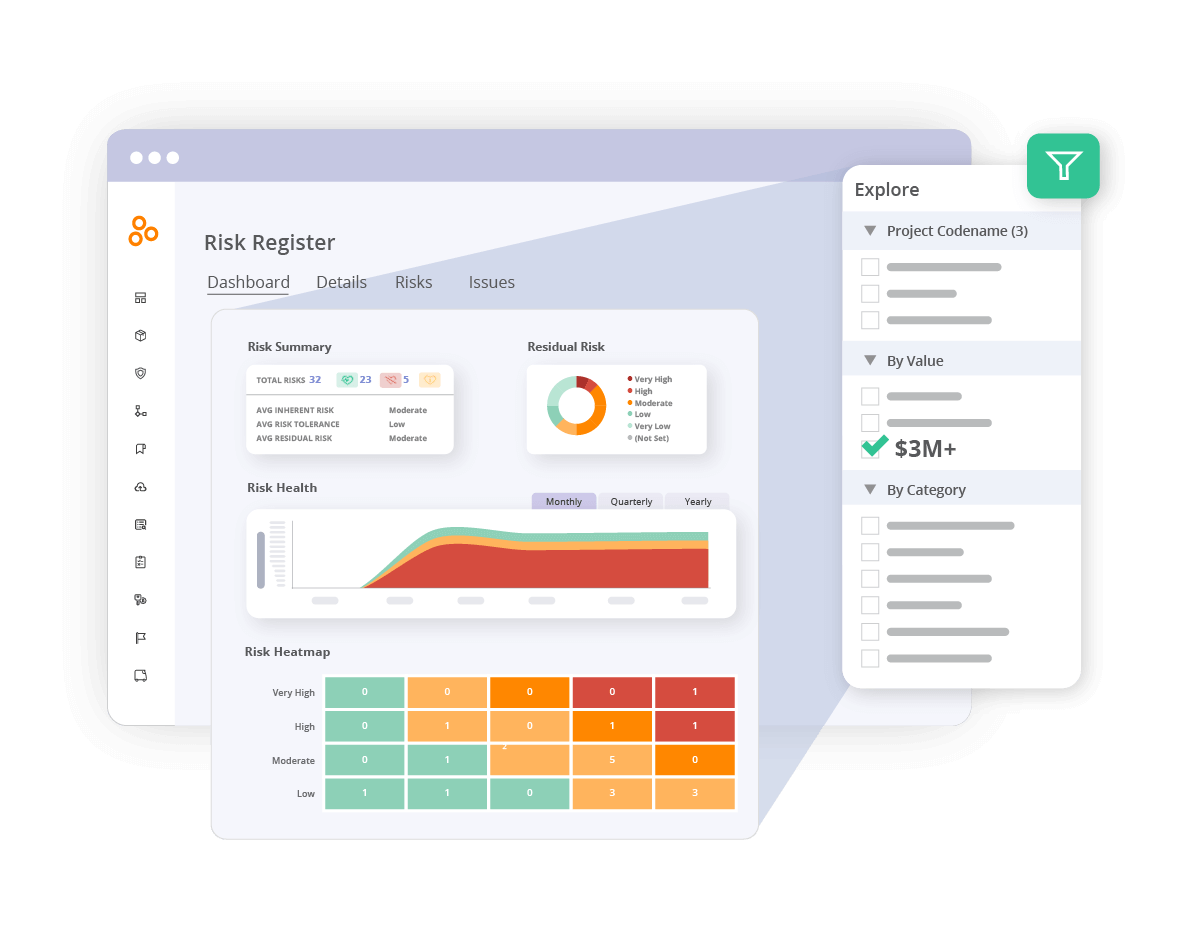
Using the risk register to meet DORA’s risk management requirements
Hyperproof’s risk register consolidates every ICT-related risk that falls under DORA’s scope into a single, searchable inventory, whether it’s from internal systems, third-party providers, or emerging crypto-asset services. Each risk captures the underlying threat, the affected business function, the likelihood and impact scores, and the associated mitigation controls, allowing you to map directly to DORA’s Articles 4 and 5 clauses on risk assessment and treatment. Built-in dashboards help show risk health, tolerance, and remediation status so you can prioritize high-impact items, demonstrate a documented risk-management process, and provide regulators with the transparent, evidence-backed risk posture that DORA mandates.
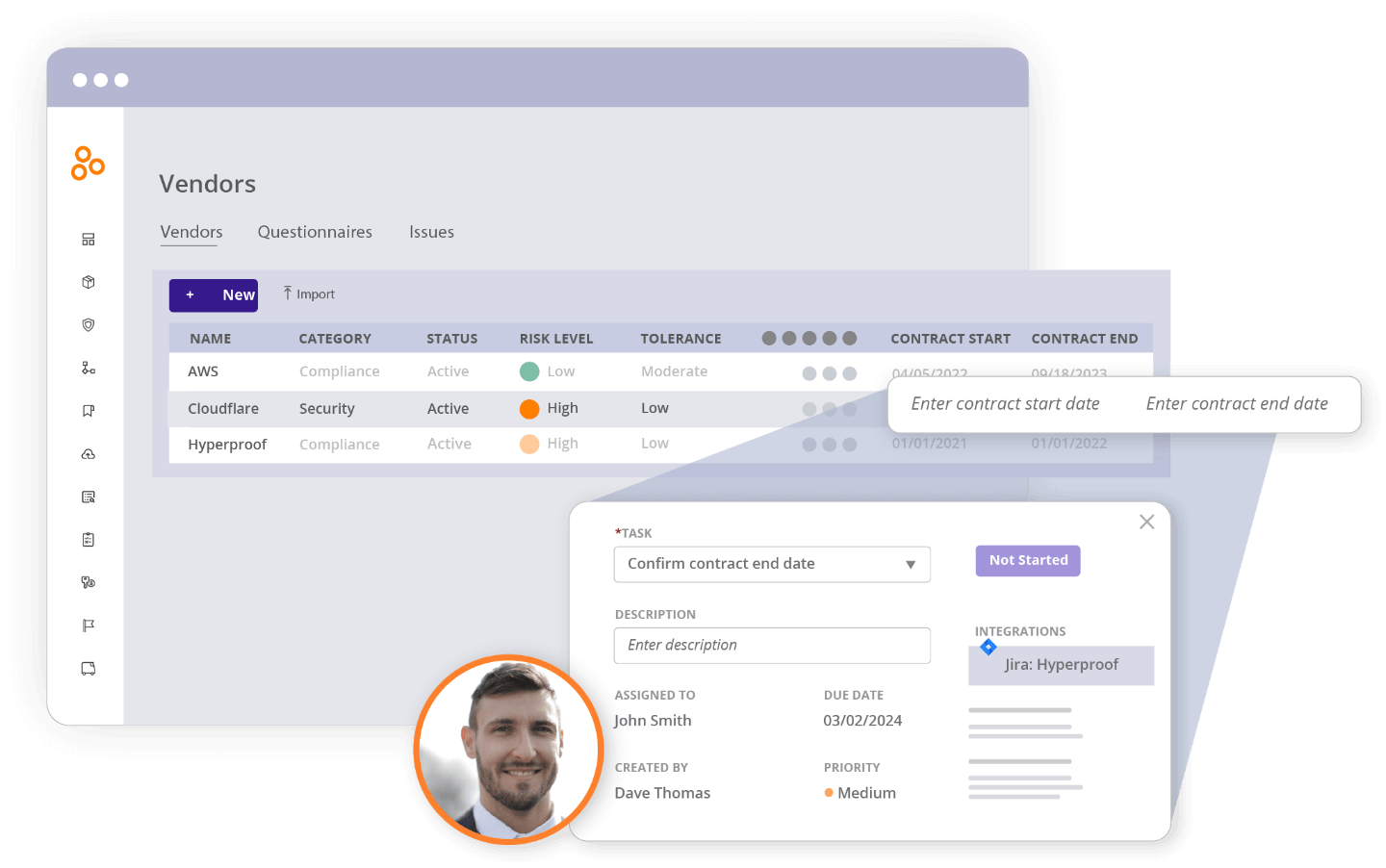
Streamlining DORA third-party governance with the vendor register
Hyperproof’s Vendor Register gives you a single source of truth for every ICT supplier that falls under DORA’s third-party oversight obligations. By capturing contract identifiers, service classifications, data-location clauses, and exit-strategy provisions in one searchable inventory, you can instantly demonstrate to supervisors that all critical and important providers are documented as required by the regulation.
Our built-in health widget flags at-risk and critical vendors, while the freshness setting ensures contract evidence is refreshed on a defined cadence, preventing stale or missing documentation. Integrated issue tracking surfaces open compliance gaps, like pending security-assessment reports, and the renewals view highlights upcoming contract expirations, prompting proactive renegotiation or termination before a deadline. Each vendor can be linked to related controls, risks, and proof, so the register automatically aggregates the supporting evidence needed for DORA’s contractual and monitoring checkpoints, turning a traditionally fragmented process into a consistent, auditable workflow.
DORA expertise
Hyperproof has partnerships with professional service firms with proven track records and deep expertise in DORA. If you need a referral, we’d love to talk.
Hyperproof for
DORA compliance
Hyperproof can help you get ready for the DORA in the most streamlined and efficient way:

Hyperproof partners with professional service firms with proven track records and deep expertise in helping organizations get DORA ready. Our partners help customers design their compliance programs, build them out, and conduct readiness assessments to ensure there are no surprises when the audit occurs. If you need a referral, we’d love to talk.
Download the PDF









