Eliminate Inefficiencies From Your IT Compliance Program
Organizations today are committing an ever-growing share of their IT security budget to cyber-related compliance tasks. Yet, they still struggle to maintain their desired risk profile even as they devote more resources to the challenge. The inefficiencies in compliance management have an insidious effect on organizations. Fortunately, there’s a way to reverse the trend.
See what you can do to create an efficient and effective compliance program — one that maintains your desired risk profile, protects the organization from cyber attacks, and assures customers, partners, and regulators that you take risk management seriously. And you can do it all without breaking the bank.
The Growing Burden of Compliance
If you’re feeling stressed and overworked because compliance work has become a growing burden for you and your team, you’re in good company.
A 2020 report from Coalfire and Omdia found that for the majority of organizations, growing compliance obligations are now consuming 40 percent or more of IT security budgets and threatening to become an unsustainable cost.
Organizations in all industries, locations, and company sizes are spending more time and money on compliance programs than ever before, for a few different reasons.
New data protection regulations
For one, this growing burden comes from a new generation of privacy and data security rules proliferating around the world that impose formidable duties of care for the data a company has in its possession or has trusted third parties with.
That means compliance with these regulations is about continuous monitoring and protection of data, rather than point-of-time audits. Compliance also requires effective vendor risk management.
Since these new privacy and data security laws have passed, security audits have started to consume more time and resources than they should. In the same report from Coalfire, nearly half of the surveyed organizations spend 20,000 man-hours a year on compliance, and 58 percent view compliance as a significant barrier to entering new markets.
Growth
Compliance work may become more challenging as your organization grows and evolves. This can be further complicated by executives wanting to achieve new security standards or colleagues onboarding new vendors without keeping you informed.
COVID-19
COVID-19 has complicated the risk landscape and forced businesses to quickly adjust and adapt their security policies and procedures like nothing before.
Many people are working from home on unsecured networks and devices, and cybercriminals are taking advantage of the gaps in security.
All of these internal changes and external threat vectors mean more work for compliance and security professionals. Further, security and compliance teams are often under great strain because many businesses don’t have a dedicated compliance function. Rather, the security team does the compliance work; they handle endless requests for audits, documenting internal controls, making changes to internal controls, uploading new copies of evidence and so forth.
Getting to the Roots: Why Compliance Work Isn’t Done Efficiently
Meeting both security and compliance needs at the same time is a difficult thing to achieve for many organizations, for two main reasons.
1. Redundancies between risk management activities and compliance activities
Organizations often manage risk and compliance in silos, resulting in inefficient processes and duplicated effort. It feels “normal” to conduct risk mitigation and compliance activities independently because they have separate objectives. While the objective of effective risk management is to maintain an acceptable risk tolerance level, the objectives of compliance are varied.
Companies have internal and external motivations for setting up compliance programs. For instance, your company has to comply with laws and regulations and maintain certifications that are requested by customers, suppliers, or business partners (external). Meanwhile, maintaining a compliance program is also about making sure that risk management activities are performed consistently, effectively, and in a timely manner (internal).
What ties risk management activities and compliance activities together are controls, which help both functions meet their objectives. A control is a specific action, process, or protocol that’s designed to mitigate a specific risk or neutralize a specific threat.
While your organization creates controls to mitigate specific risks to specific aspects, you also need controls to satisfy the requirements of industry-accepted security frameworks and standards (e.g. SOC 2, HITRUST, PCI DSS, etc.). Because risk management and compliance have different objectives but both use controls to meet their objectives, it is common for an organization to have some redundant controls and inefficiencies within their cybersecurity risk management and compliance activities.
At the same time, not all redundancy is bad. But unnecessary redundancy between risk management and compliance wastes valuable resources. Yet, without effective tools, risk and compliance professionals cannot determine where overlaps and duplicative efforts exist.
2. Ineffective Tools
Many organizations today use a patchwork of tools to manage their risks and get compliance work done. Spreadsheets, emails, file storage and project management systems are often used for various compliance activities.
But without a single repository of information that includes the results of risk assessments, compliance requirements, controls, and evidence, meeting compliance requirements is a manual, inefficient process, prone to error.
Without visibility into the overlapping requirements across different security compliance frameworks, security and compliance teams often end up collecting the same set of information multiple times (e.g., evidence that would satisfy a control for PCI, ISO 27001, and SOC 2 is collected three times). A control owner ends up testing the same control multiple times (for multiple assessments) because they didn’t realize that this control is common across multiple security standards.
In Hyperproof’s 2020 IT Compliance Benchmark Report, we found that the typical professional responsible for security, data privacy, and compliance initiatives spends approximately one full workday every week on such administrative activities, or 20% of their total time at work.
When it comes to handling compliance projects, which administrative activities aren’t a good use of your time?
n=526
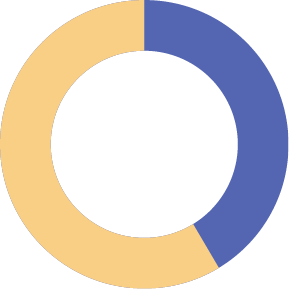
57%
Searching through emails to find documents needed or you have to submit to an external auditor
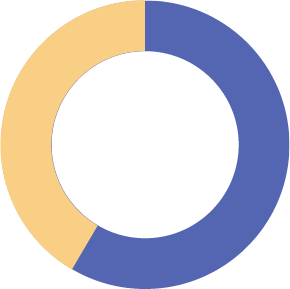
40%
Meetings

40%
Finding information needed to meet compliance requirements

41%
Training others to assist, complete tasks or do administrative activities

41%
Filing, storing, managing compliance documentation

1%
Other
Meanwhile, when compliance work happens in multiple systems, reporting becomes a major hurdle. Compliance and risk leaders and senior management don’t have a reliable view of how compliance efforts are progressing or how well they’re mitigating risks.
Inefficiencies In Compliance Management Have An Insidious Effect
Security and compliance teams have a finite amount of time and resources to accomplish their risk and compliance objectives. When a security team has to spend more time on administrative and repetitive tasks just to meet their existing compliance obligations, they will have less time for every other type of important task aimed at mitigating risks and improving security and resiliency, such as:
Investigating security alarms
Implementing new tools to better identify threats and prioritize their work
Testing controls on high risk areas
Training employees to uplevel their cybersecurity knowledge
Talking to business units to understand what’s changing in the business and how those changes may create new risks or amplify existing risks
Updating security policies and operating procedures in response to those changes
At an organizational level, the lack of adequate focus on risk management can result in consequences such as new risks being missed or vulnerabilities being left unaddressed, leading to financial loss, reputational damage, regulatory fines and penalties, and compromised intellectual property assets.
Whenever an organization is facing a threat that does not stay still, it is important for security and compliance teams to work closely with other parts of the business to understand how employees and operating units are responding to those threats. Compliance and security teams need to devote plenty of time to understanding which processes need additional control and appropriate mitigation.
Unfortunately, many security and compliance teams are struggling just to get through all the audits they have to pass, and are unable to devote the time needed to respond to emerging threats.
“The only time when we are confident in our security posture is right after our audit,” said a director of product security and compliance at a midsize B2B company in the technology industry.
Creating a More Sustainable and Efficient IT Compliance Program: Top Five Actions
If your goal is to reduce risks, improve your security posture, and eliminate inefficiencies and redundancies from your compliance program, there are five actions you should prioritize.
1
Strengthen Your Risk Assessment
Every compliance program is built upon a solid risk assessment. Security teams should spend plenty of time thinking about which risks your organization is facing. In practice, you’ll want to review any risk libraries you use to see how those libraries reflect the new reality coronavirus is forcing upon us.
Organizations like NIST and ISO have developed quality resources you can use to set up a holistic risk management framework. In fact, these two organizations are the authoritative sources for risk and compliance. For instance, NIST SP 800-53 is an excellent set of guidelines that give you a good solid foundation and methodology to create operating procedures and apply security controls across the board within your organization.
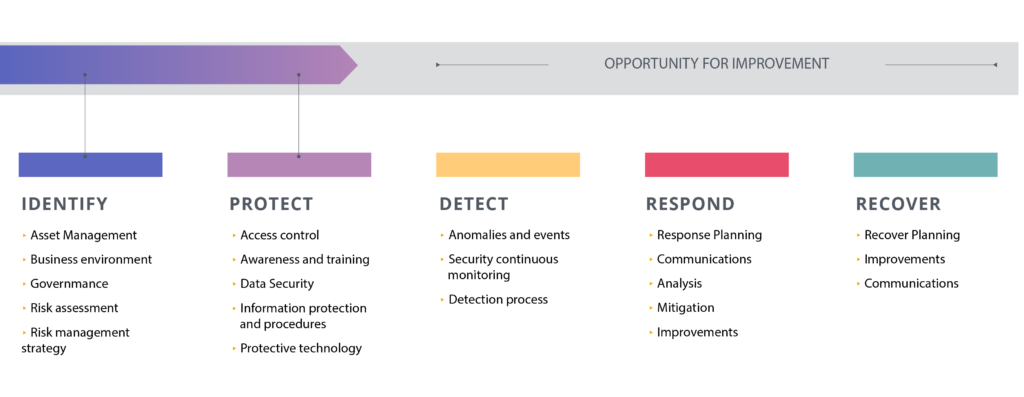
NIST’s cybersecurity framework outlines five key areas your organization should pay attention to from a cyber protection perspective: identify, protect, detect, respond, and recover.
NIST SP 800-53 Control Families
Webinar
Learn More About How to Use NIST SP 800-53 to Protect Your Organization From Cyberattacks, check out our on-demand webinar.
2
Identify Controls And Map Them to Regulatory Requirements
Identifying existing controls within your business and mapping them to a compliance standard (e.g. ISO 27001 or GDPR) is an important step; without it, you can’t perform a gap analysis to see where controls don’t measure up or develop a plan for remediation.
In fact, many frameworks in the information security space, including PCI, HIPAA, SOC 2, SOX, CSA’s Cloud Controls Matrix, and CMMC, have controls that pull directly from NIST and ISO. If your organization has to comply with multiple security frameworks (e.g. SOC 2, PCI DSS, HIPAA, GDPR, SOX, etc.), and your approach is to tackle one framework or one certification process at a time, you will end up duplicating controls and collecting the same set of evidence multiple times unnecessarily.
A better, more efficient way to approach meeting the requirements of these frameworks is to start by reviewing one of the two most comprehensive frameworks: NIST SP 800-53 (U.S.-based) or ISO 27001 (international).
Because nearly all other frameworks and certification programs use NIST SP 800-53 or ISO 27001 as the reference framework, by implementing either of these guidelines, you are well on your way to meeting these other frameworks’ requirements too. If you set your framework at the overarching level (NIST or ISO), you can identify how the main framework requirements cross-map to the secondary frameworks like SOX, SOC 2, PCI, or HIPAA.
Resources for cross-mapping controls
There are several resources that can help you with cross-mapping, including the Security Controls Framework Crossmap (open-source resource) and CIS controls (open-source resource).
If you understand your key problem areas (cross-mapped from the higher-level frameworks like NIST and ISO) and fit those into the subsidiary frameworks like SOC 2 or SOX, you can see where those overlap.
If you focus on the overlapping areas first, you will cover anywhere from 65 to 85 percent of your overall controls including those from non-NIST, non-ISO frameworks. Then you can address the unique controls of each framework. By taking this approach, you can gather evidence that can meet all the frameworks’ requirements once and apply them across the frameworks.
3
Focus on Automation
The more compliance processes you can automate, the more time you’ll have for more complicated tasks, freeing up resources in a budget-constrained environment.
For example, you can automate some work involved in collecting evidence for audits. With certain kinds of compliance software, you can associate a piece of evidence with multiple controls and reuse that evidence across multiple audits. Some compliance solutions have built native integrations to the business applications you already use – so you can automatically bring the latest evidence files from those business apps into the compliance management system without having to ask your colleagues.
Additionally, compliance solutions like Hyperproof allow you to automate reminders to business executives to test or execute a certain control and automate alerts to you or other compliance officers when that work isn’t done in a timely manner. Results of those tests can be fed into standard reports or risk dashboards to let you see and report security compliance quickly.
4
Integrate Compliance into Operations
One significant threat is when some parts of the business change their operations without telling the compliance team, so existing internal controls no longer fit their original purpose.
For instance, “During the COVID-19 pandemic, a company might lay off employees and neglect to tell the security team, so user access controls might remain valid when they should be deleted. Or the company might begin processing certain transactions on new apps, exposing confidential data to vendor risk. In both cases, the security risks there are well understood and can be controlled. The true risk is poor integration that leaves the security team isolated from the company’s changing risk profile,” says Matt Kelly.
5
Focus on Documenting Your Response
To cut down on administrative work, you’ll need to document your controls and manage them in a central, secure location. Once controls are mapped to specific requirements, you’ll be able to collect evidence once and re-use it across the different controls. With a single repository, you can quickly find the right evidence files at audit time and easily keep track of the latest version of your policies and procedures.
Going back to the COVID-19 example, any policy changes you make or new controls you introduce should be documented and organized so you can demonstrate the company’s attention to COVID risks to other parties, like auditors, regulators, customers, or consumers.
The more quickly you can provide such documentation, the more quickly you can soothe skittish customers, pass security audits, answer regulators’ questions, and prove that your business takes a thoughtful approach to risk.
Reducing the Compliance Burden: How Hyperproof Makes Compliance Work More Efficient and Improves Risk Management
Hyperproof has created continuous compliance software that helps organizations get compliance work done faster, more accurately, and more effectively so they have time to focus on other important tasks, like identifying emerging risks, developing new mitigation measures, updating controls, etc.
Hyperproof provides a central, secure place for an organization to get all of its IT compliance work done and comes with a set of innovative features designed to automate processes and eliminate inefficiencies. Here are some unique features of Hyperproof that are designed to give you time back, streamline your IT compliance effort, and inform risk management decisions.
Hyperproof has developed starter templates for dozens of cybersecurity and data privacy compliance standards, including NIST SP 800-53, ISO 27001, PCI DSS, HIPAA, SOC 2, SOX, CSA’s Cloud Controls Matrix, and CMMC and many others. Each template comes with all the requirements of the framework, organized by domains. Many of our frameworks also come with illustrative controls as a starting point for creating your custom controls. We invest ongoing resources into supporting emerging standards and regulations in the data security and privacy space.
Hyperproof has completed the mapping between requirements within various cybersecurity frameworks to help you jumpstart your efforts to adhere to multiple compliance programs. The mapping follows the Secure Controls Framework (SCF), a framework developed by Compliance Forge. This allows you to design and manage a smaller set of controls to meet multiple compliance standards more efficiently.
Collecting compliance documentation and fulfilling audit requests can be a major time sink if a team has to complete several audits each year but tackles each audit independently. Labels (a Hyperproof concept) are containers for storing specific types of evidence, you can collect evidence once and re-use it across multiple controls or frameworks. Link a label to as many controls as you like. Any evidence attached to the label will be reflected across all the controls.
Hyperproof has native integration with the tools you already use and love. With our native integrations, you can automate the collection of evidence files and reduce friction from collaboration processes. You can also use the Hyperproof API to detect compliance events, extract evidence from source systems (e.g. Jira, GitHub, Workday, Checkr, etc.), and auto-import evidence into Hyperproof.
Hyperproof supports continuous compliance. With automated reminders, you can ensure that testing and evidence collection are happening throughout the year, rather than right before an audit.
Hyperproof provides reports to give teams a thorough understanding of the status of each compliance program and a high-level view of their overall compliance posture. With real-time data on where they stand, teams can hone in on what remediations are needed, which controls need to be reviewed, and exactly where they need to focus their energy.
Elevate your risk management with Hyperproof. Schedule a demo today and discover how our platform can meet all of your risk management requirements. Book your demo now to see the difference.
Ready to see
Hyperproof in action?









