Guide
Everything You Need to Know About Trust Management Platforms

Introduction
The pace of change that businesses must keep up with has been accelerating. Modern businesses looking to survive and grow are undergoing constant cycles of innovation, reinvention, and business transformation. The following research showcases a snapshot of how business environments at large have changed within industrialized countries between 2020 and 2024:
The evolution of the technology sector
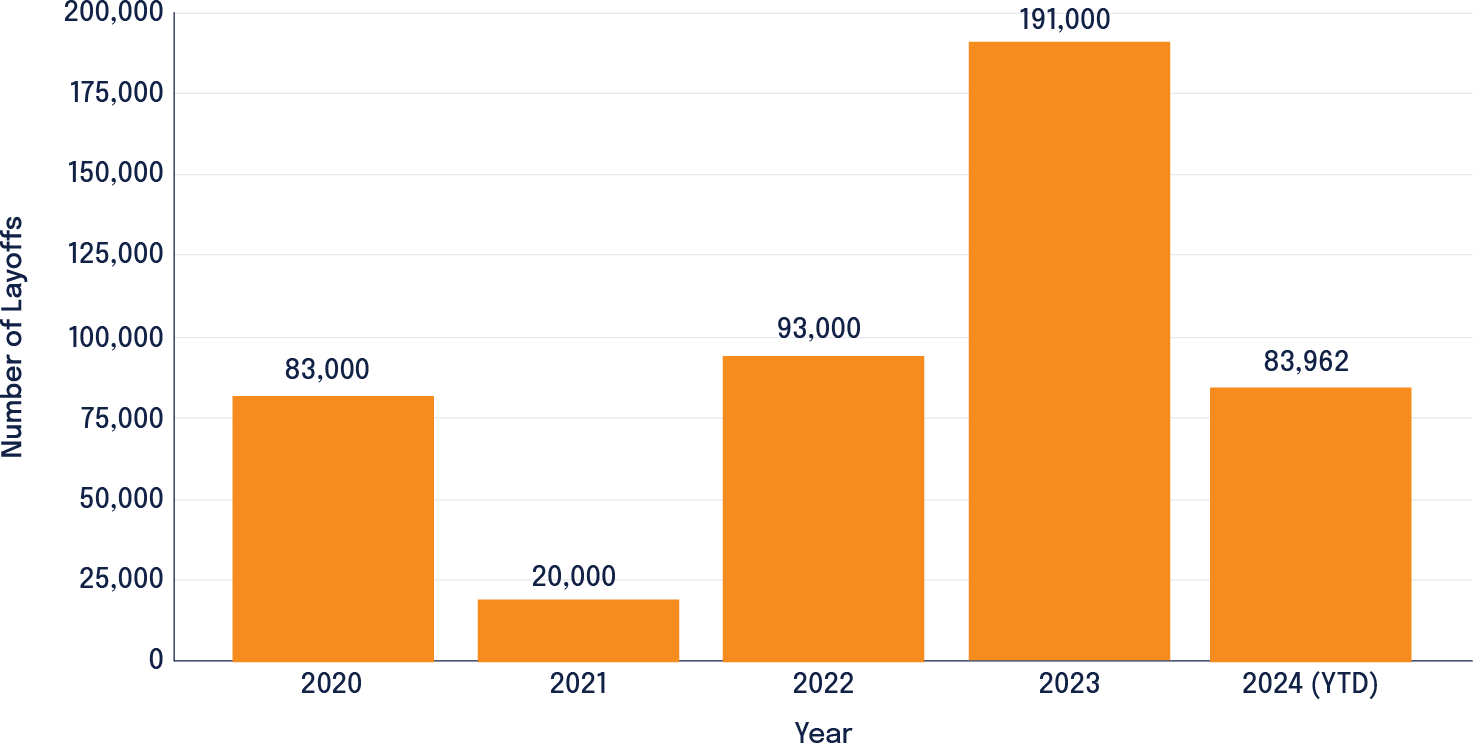
The technology sector, the darling industry of the 2010s and early 2020s has lost its luster. This sector had once engaged in aggressive hiring and spending sprees afforded by a low-interest rate environment and highly available venture capital money. It took a 180-degree turn in 2023 once interest rates rose. In 2023, more than 191,000 workers in U.S.-based tech companies (or tech companies with a large U.S. workforce) were laid off in mass job cuts. According to a Crunchbase News tally, at least 77,361 workers in U.S.-based tech companies have lost their jobs in 2024.
Tech Sector Layoffs in the U.S. (2020-2024)
Advancements in AI

In 2020, AI advancements were happening, but its applications were primarily limited to the technology and research sectors. Most companies outside those sectors were either not using AI or conducting early exploration but had not yet integrated it into their core business functions. In 2023, ChatGPT became a household name, and by 2024, AI has cemented itself as the driving force of innovation and efficiency in multiple industries. Businesses have reported tangible productivity benefits and cost savings in diverse functions like supply chain management, customer support, marketing, and human resources.
The decline of legacy software
Legacy industries (e.g., healthcare, CPG, manufacturing) have moved away from using stable but high-maintenance “legacy” software (e.g., custom-built software) and started to embrace cloud computing, microservice architecture, containerization technologies, and the usage of third-party, purpose-built software. The shift was driven by the need to innovate to remain competitive and adaptable in fast-paced environments.
Trust management is the discipline that supports all innovation efforts
Companies across the spectrum — startups, scale-ups, and enterprises — are continuously evolving their business processes, product mix, job roles, and technology stacks to maintain a competitive edge.

While fostering innovation and growth, this cycle of continuous transformation also introduces many new risks and vulnerabilities that organizations must adeptly manage to maintain trust with customers and other stakeholders. For instance, integrating AI into one’s products exposes the organization to new vulnerabilities through a broader attack surface. AI systems are susceptible to cyberattacks and adversarial threats, while reliance on third-party AI providers can introduce vulnerabilities stemming from vendor security practices. Over-dependence on AI for critical operations can result in significant risks if these systems fail or generate incorrect outputs.
Similarly, engaging in business restructuring during economic downturns — such as layoffs and replacing full-time employees with contractors — can result in losing vital security knowledge and reassigning responsibilities, increasing risk exposure. Integrating disparate systems and workforces following a merger or acquisition introduces additional complexity and potential vulnerabilities that must be addressed through effective trust management practices.
Every leader has heard that “innovation always brings new risks.” While this statement isn’t novel, what is different now versus five or ten years ago is how fast new risks can emerge for organizations because they’ve dialed the pace of innovation (or evolution) way up.
While risk management is a long-established discipline, risk management concepts have gained popularity among those outside the profession in recent years. Business managers, Operation professionals, and C-suite executives have also realized that they need to take extra precautions when changing business processes, creating new roles, and working with new technology.
After countless publicized stories of well-known, blue-chip companies betraying their customers’ trust due to inadequate security and privacy measures or profit motives, everyone is now wiser and more cautious — as consumers and agents serving their employers. We’re now living in a time where trust in a business is not automatically granted; it has to be earned and proven through robust evidence.
Thus, trust management has become an essential operating discipline for modern organizations.
What is trust management?
It’s worth emphasizing that both goals are equally important. Being trustworthy isn’t just about being a good corporate citizen, preventing the worst disasters from happening, or meeting regulatory and customer requirements. The bigger purpose is to make your organization more resilient, accountable, and transparent so you can build a secure base for all of your innovation initiatives.
It is essential to showcase that commitment to safeguarding stakeholder interests through rigorous trust management. An organization can create a loyal customer base and win in highly competitive environments by earning and maintaining the confidence of its customers, partners, and regulators.
Trust management
noun
Trust management is an operating discipline and set of practices that build upon the disciplines of sound governance, policy management, risk management, compliance, and vendor risk management. It involves creating a holistic system of people, policies, processes, and technology working together to ensure that:
- An organization consistently behaves in a trustworthy manner
- Can demonstrate its commitment to safeguarding stakeholder interests
How does GRC relate to trust management?
Governance, Risk, and Compliance (GRC) is an organizational function responsible for developing and enforcing practices, policies, and systems that help organizations ensure ethical operations, transparency, and compliance with legal and regulatory requirements. Historically, GRC professionals have focused on creating and evolving policies and supervising business functions to ensure compliance with legal and regulatory requirements. While some GRC professionals get “hands-on” in understanding the details of business operations, others have tried to be more “objective” and operate at an arm-length distance from the business.
But in today’s business environment, where technology and business processes evolve this fast, this top-down, “arms-length” approach no longer works. Behaving in a trustworthy manner consistently and maintaining stakeholder confidence requires active participation from a much broader base of stakeholders, ranging from senior executives to business unit operators. GRC professionals will continue to contribute valuable knowledge and perspectives and help orchestrate various initiatives. However, function area leaders, managers, and individual contributors must also consider the risk implications of their decisions, exercise judgment to mitigate risks, and be more vocal with improvement suggestions.
Trust management requires getting everyone involved in the right roles at the right time and empowering each person with the right information and technology tools to do what’s best for the organization.
Common challenges businesses face when following trust management practices
Trust management practices can be challenging and expensive to operationalize for several reasons:

Changing processes

Lack of resources

Risk prioritization

Getting buy-in across the organization
Changing processes

Business processes and the software and tech stacks used to run business functions change frequently. Business function managers and employees outside the purview of central it/compliance/risk management/security teams usually initiate these changes. Keeping up with all business process changes the vendors an organization uses and the risks they bring is a moving target for security teams.
Lack of resources

The designated teams with risk management and compliance responsibilities are usually relatively lean and often under-resourced for the amount of work they have to do. Many teams need help keeping up with the compulsory, audit-related work and don’t feel they have the time to proactively improve their trust management practices.
Risk prioritization
When many factors change within a business simultaneously, figuring out which risks to prioritize becomes increasingly time-consuming and difficult.
Getting buy-in across the organization

Building a risk-conscious and resilient organization requires grass-roots employee participation in all areas. Employees need to understand their roles and receive training on how to safeguard the organization’s interests. Yet, many companies have engaged in RIFs (reduction in force) or other restructuring efforts. These activities can result in losing vital security knowledge and reassigning responsibilities, thereby increasing risk exposure. Senior business leaders may intuitively understand why trust management is beneficial but still be unwilling to allocate adequate resources to prioritize this discipline because other issues seem more pressing and urgent.
How to operationalize trust management
To establish an effective trust management discipline, organizations need a strategy that addresses the challenges of changing processes, resource limitations, risk prioritization, and stakeholder buy-in.

Recognize and communicate its value
Senior leaders need to recognize the value of this discipline and communicate its benefits to employees. Rather than viewing trust management as an expense, leaders should understand why it’s an investment that enables their organization to drive innovation, organizational stability, and competitive advantage. By presenting case studies and data-driven insights on how effective trust management can prevent costly issues like data breaches, lawsuits, and critical systems taken offline, risk management teams can make a compelling case for allocating adequate resources to this vital function.
Create trust management policies

For trust management to take root, the policies and practices created must make sense to the operators and frontline employees within the organization. The organization should establish a cross-functional Trust Management Committee composed of representatives from business functions, engineering, compliance, risk management, IT, and Legal. This committee plays a crucial role in shaping the trust management strategy and ensuring that it aligns with the organization’s needs and realities.
Regularly review and update those policies
This committee should regularly review and update the organization’s policies, processes, and vendor lists to ensure they are suitable and appropriate for the organization’s objectives and ways of working. By integrating business function managers into this committee, organizations can ensure that changes in processes and technology stacks are communicated effectively and assessed for potential risks early on.
Encourage a risk-aware culture
Encouraging a risk-aware culture is crucial for gaining stakeholder buy-in and enhancing organizational resilience. Regular training sessions and workshops that educate employees on the importance of trust management and their role in maintaining sound practices in trust pillars, like safety, information security, privacy, and responsible AI, are key to fostering this culture. Encouraging a bottom-up approach to risk management, where employees at all levels feel empowered to report potential risks and suggest improvements, will foster a sense of shared responsibility and commitment to the organization’s trust management strategy.
Overcome resource limitations
Finally, organizations should leverage a trust management platform to overcome resource limitations. This platform centralizes, streamlines, and automates various work streams and tasks across domains such as policy management, compliance monitoring, risk assessment, and vendor risk management. It not only empowers IT compliance, risk management, and security teams to work efficiently but also helps everyone else, from executives to individual contributors in various business functions, to participate in trust management practices and make the right decisions on behalf of the organization.
A trust management platform allows organizations to adopt a risk-based approach to prioritizing projects and tasks. Teams can focus on high-impact areas first, ensuring that resources are allocated where they are most needed.
Understanding the benefits of a trust management platform
A robust trust management platform is built to benefit various roles and levels of an organization:

Executives and compliance teams
It serves as an insights platform and decision-making aid for executives and compliance teams, helping them determine what investments to make and what workstreams to prioritize to address risks and obtain or maintain compliance certifications.

IT, compliance, and risk management professionals
It boosts productivity for the security, IT, compliance, and risk management professionals through centralization, workflow optimization, and automation.

Managers
It provides an easy means for managers and individual contributors in various functions (e.g., marketing, engineering, product development, etc.) to participate in and support compliance/risk management work. These operators can work either in the tools they natively use or in a shared space within the trust management platform.

External auditors
It enables easy sharing and review of trust/compliance artifacts with external auditors and assessors.
Organizations with trust management discipline and a trust management platform will experience fewer audit findings, avoid high-cost crisis-level security incidents, lower their cost of meeting compliance requirements, and win business from their competition thanks to their more robust trust posture.
Benefits of trust management for IT, risk management, and compliance specialists
With a robust trust management platform, central IT/risk/compliance/security teams become far more productive in their day-to-day work. This type of software can help these professionals with:
Visibility
Gain comprehensive visibility into risks, risk mitigation measures, and the organization’s compliance stature
Policy management
Centrally manage their policies
Compliance management
Conduct assessments, identify gaps, and improve an organization’s security and compliance posture
Audit management
Automate their audit preparation processes
Risk management
Streamline risk evaluation, prioritization, and mitigation processes
Vendor risk management
Expedite vendor risk assessment and management workflows
Benefits for executives
This platform can help senior executives determine how to optimize their security and compliance investments and where they need to make additional investments to improve their trust management practices. It can also provide executives with a short list of key risks they need to address in a given quarter.
A trust management platform can also help leaders chart the path forward for achieving a significant compliance milestone requiring investment. For instance, if an organization wants to become FedRAMP Moderate to start selling products to U.S. government agencies, an executive must determine a reasonable budget and timeline. To figure out these components, a compliance leader can use a trust management platform to see what controls already exist that can satisfy specific FedRAMP requirements and where the organization needs to develop new controls to meet outstanding requirements. It is faster and easier to do this assessment and mapping in a dedicated platform than in spreadsheets.
Benefits for business unit operators
In compliance jargon, a system administrator who manages access to company systems (e.g., ERP, CRM, HRIS) and cloud computing resources is sometimes called a “control owner” or “control operator.” These workers follow specific guidelines when configuring system settings and provisioning resources to safeguard sensitive information. They are often asked to document certain practices when requested by compliance professionals. During audit season, they are asked to send evidence of guideline adherence to the compliance team.
With a trust management software in place, compliance professionals can quickly distribute work to these operators in business units — directly in the software or in another app, like Jira, Asana, or ServiceNow — where operators do their daily work (thanks to integrations offered by the trust management platform). The operators don’t need to change their workflows or adopt a new tool; they see the task/request in the systems they already use.
Critical capabilities to look for in a trust management platform
A robust trust management software application should include capabilities for managing compliance programs (including policy management), monitoring and testing controls, and managing first-party and third-party risks. It should help streamline the audit preparation process and reduce manual work in evidence collection. These platforms also have workflow automation features and native integrations with various enterprise applications and cloud services.
What to look for in a trust management platform
Compliance management features
Compliance management encompasses several types of work, including:

A comprehensive trust management system such as Hyperproof streamlines processes in all the above areas and provides automation to boost efficiency.
Assessment workflow support
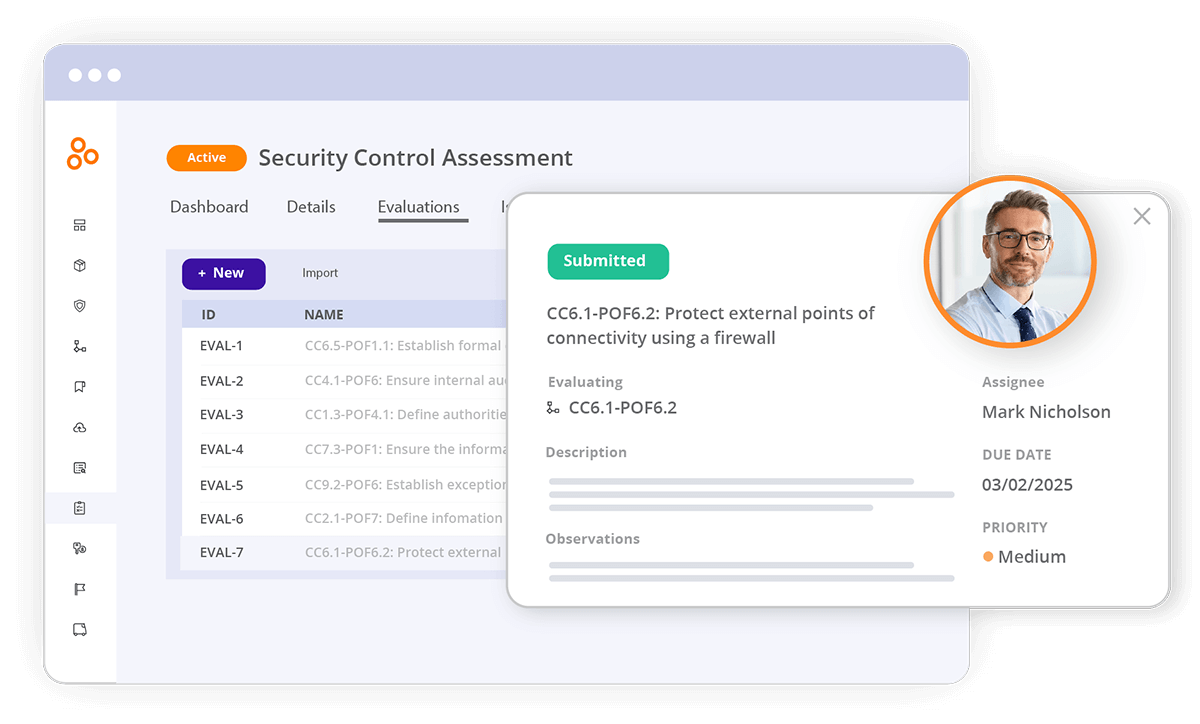
Hyperproof provides all the workflow management and automation tools compliance professionals need to conduct assessments and share the findings efficiently. In the Assessment module, an assessor can start an assessment from a template or from scratch, invite additional users into the system to evaluate specific items, record findings directly on each item, create new tasks, add issues, add proof, and share an assessment report with stakeholders.
Built-in compliance frameworks and crosswalks
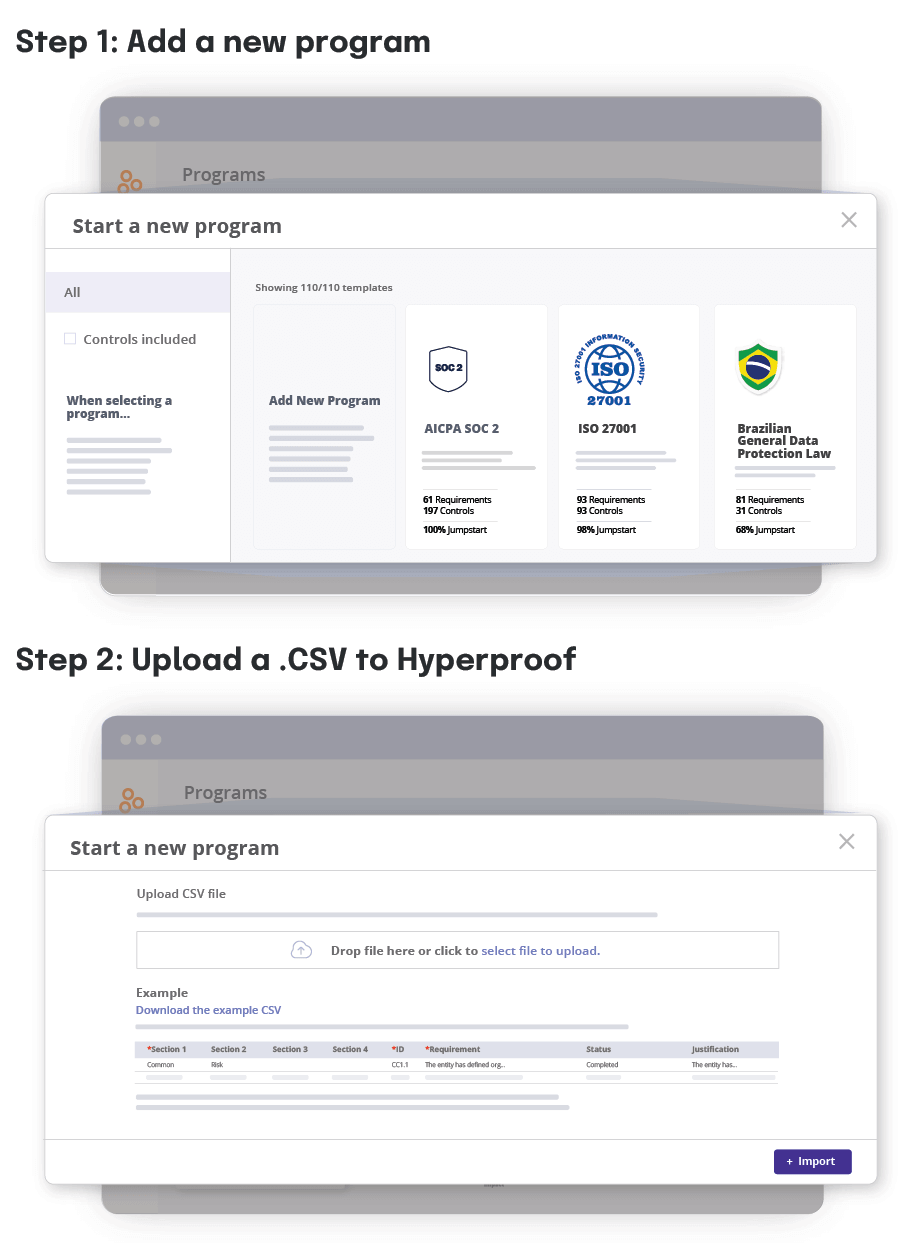
Hyperproof comes with 100+ out of the box framework templates and built-in crosswalks between cybersecurity frameworks to help organizations get a jumpstart in achieving new compliance programs and certifications. When an organization uses a starter framework or template to launch their new compliance program, they’re able to skip the research step and the work of creating controls from scratch.
Additionally, many of these cybersecurity compliance frameworks in Hyperproof are crosswalked following the Secure Controls Framework — meaning that similar or overlapping requirements across various cybersecurity frameworks have been identified and flagged. When a user creates a new compliance program in Hyperproof, the system will automatically display suggested controls they can use to meet requirements based on the controls already added in Hyperproof. This approach saves organizations time when becoming compliant with a new framework.

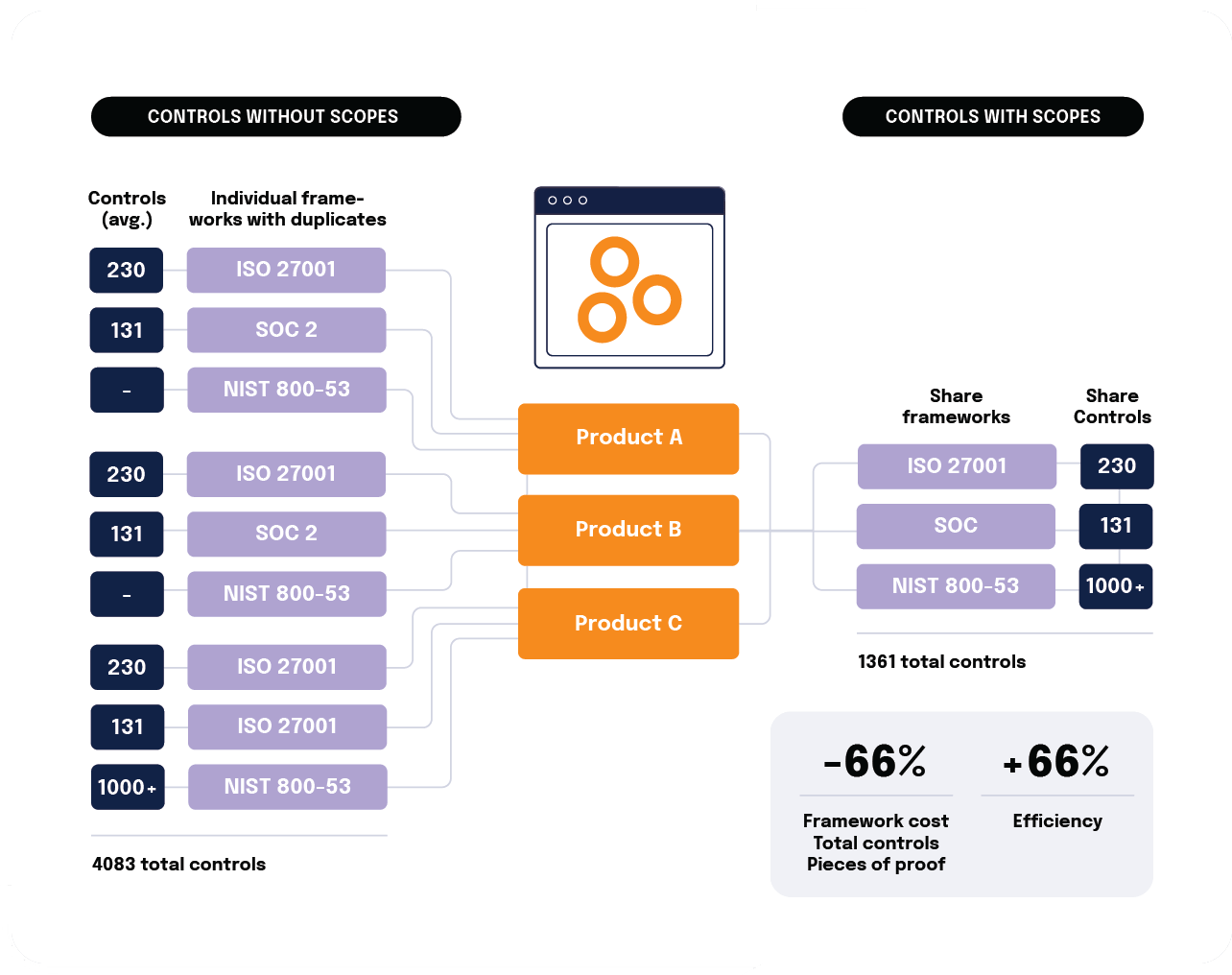
Support for custom frameworks
Organizations often use custom frameworks to streamline compliance efforts across multiple entities like regions, product lines, and business units and to manage specific legal oversight procedures.
In Hyperproof, users can easily create a new program or upload an existing framework into the platform, allowing them to tailor the platform to their organization’s specific needs. Once a custom framework is in Hyperproof, users can take full advantage of Hyperproof’s native features, such as Hypersyncs, automated control tests, and scheduled tasks, to effectively manage controls and requirements and streamline their workflows.
Smart “Labels” for evidence reuse
For years, compliance professionals were subjected to the tiresome work of having to request the same types of “proof” (e.g., docs, screenshots, meeting minutes) from their colleagues several times a year to gather evidence for multiple audits. Keeping that evidence organized was also a tall order.
Hyperproof comes with a unique “Labels” feature so that a compliance professional can collect a set of proof once and reuse it for different occasions. Labels in Hyperproof are similar to file folders, each containing a list of files but with some additional bells and whistles that make them work for compliance workflows.
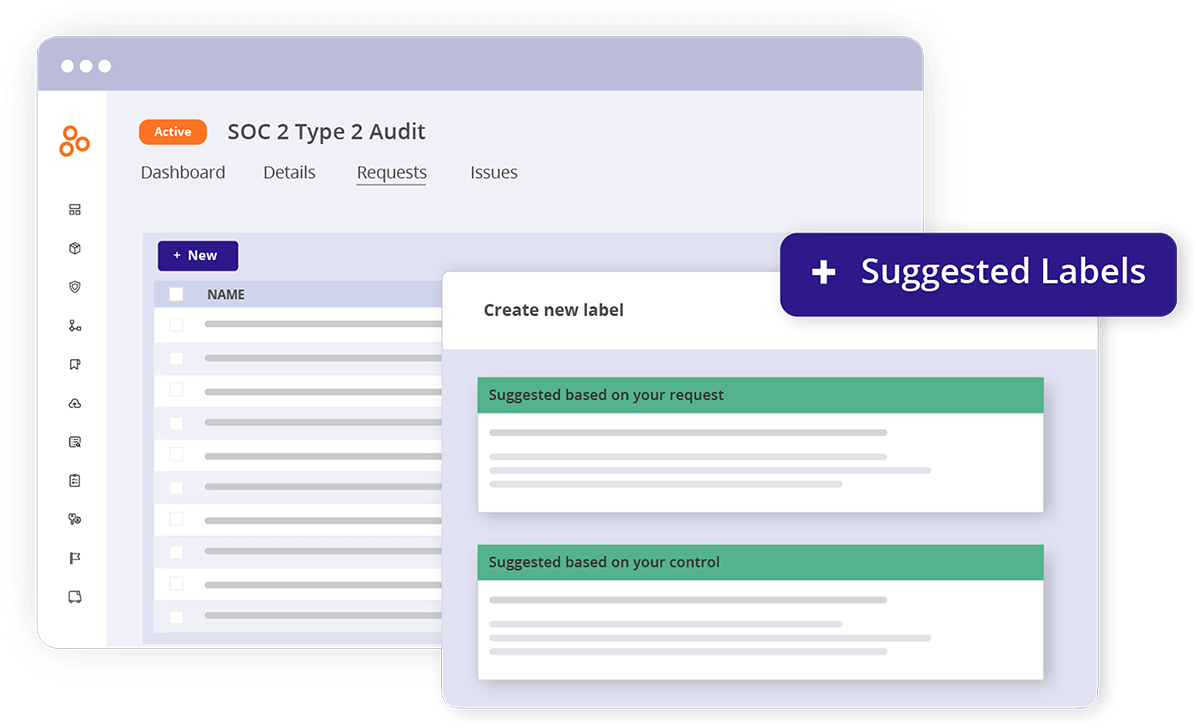
Labels serve as helpful storage buckets for proof. If a piece of evidence can be used to validate multiple controls, a user can create a label to store it and link it to multiple controls.
Labels can also distinguish between different types of proof needed to validate a single control. For example, imagine a user wants to show (1) a security policy and (2) background checks for all users who have access to production servers to validate a single control. These two types of evidence must be updated on different cycles: The security policy must be reviewed annually, and the background checks should be updated monthly. If a user just added all the proof to the control directly, the security policy review proof might get lost within the continual update of background checks. Thus, it’s better to use the labels to separate those two file groups.
In Hyperproof, labels have a Freshness feature. An individual can set a freshness policy for each label that will quickly tell every participant in a compliance program whether the evidence is up to date.
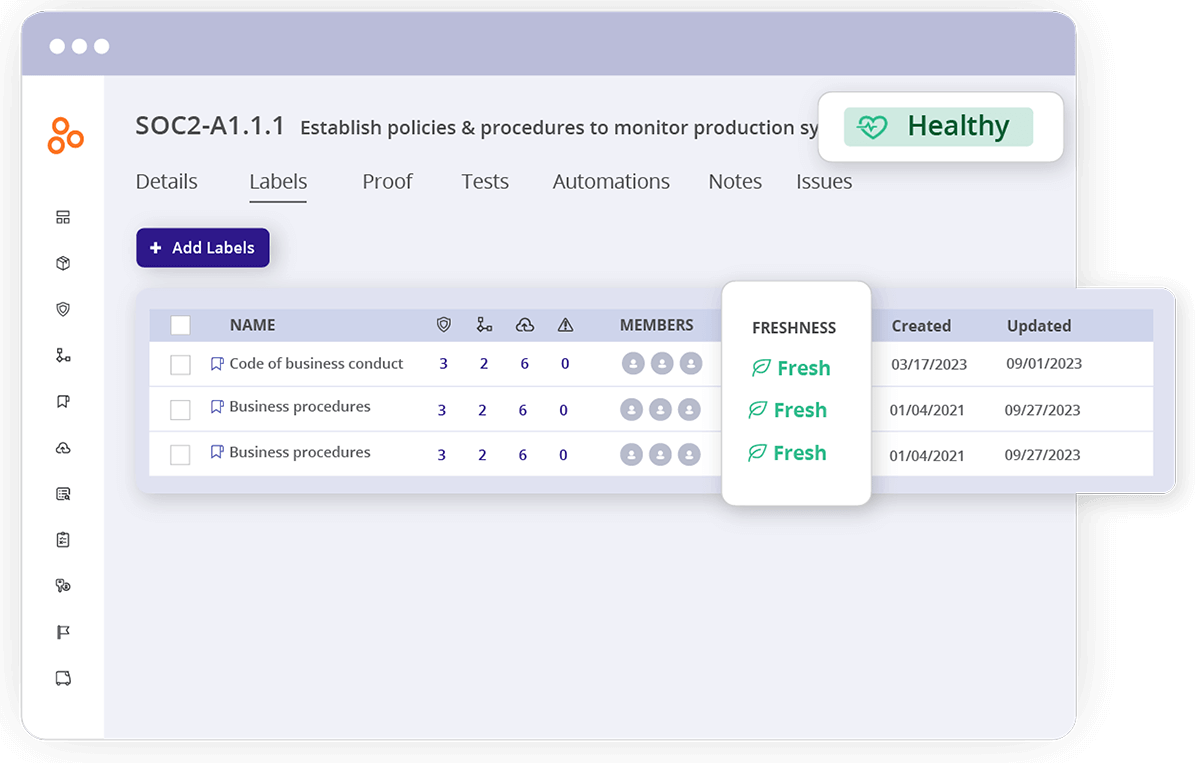
Integrated task management
Project management can take up significant time. Tracking tasks like evidence requests via email, chat threads, or spreadsheets is tedious and often leads to miscommunication and missed assignments. Task management features in Hyperproof were carefully designed to ease the project management burden and help organizations create a harmonious work environment.
Hyperproof has bi-directional task integrations with popular project management systems including Jira, ServiceNow, and Asana that help GRC professionals to create tasks and assign them in Hyperproof. Task assignees receive notifications in their current project management system, complete their tasks in their tool of choice, and then updates to proof are synced automatically to Hyperproof.
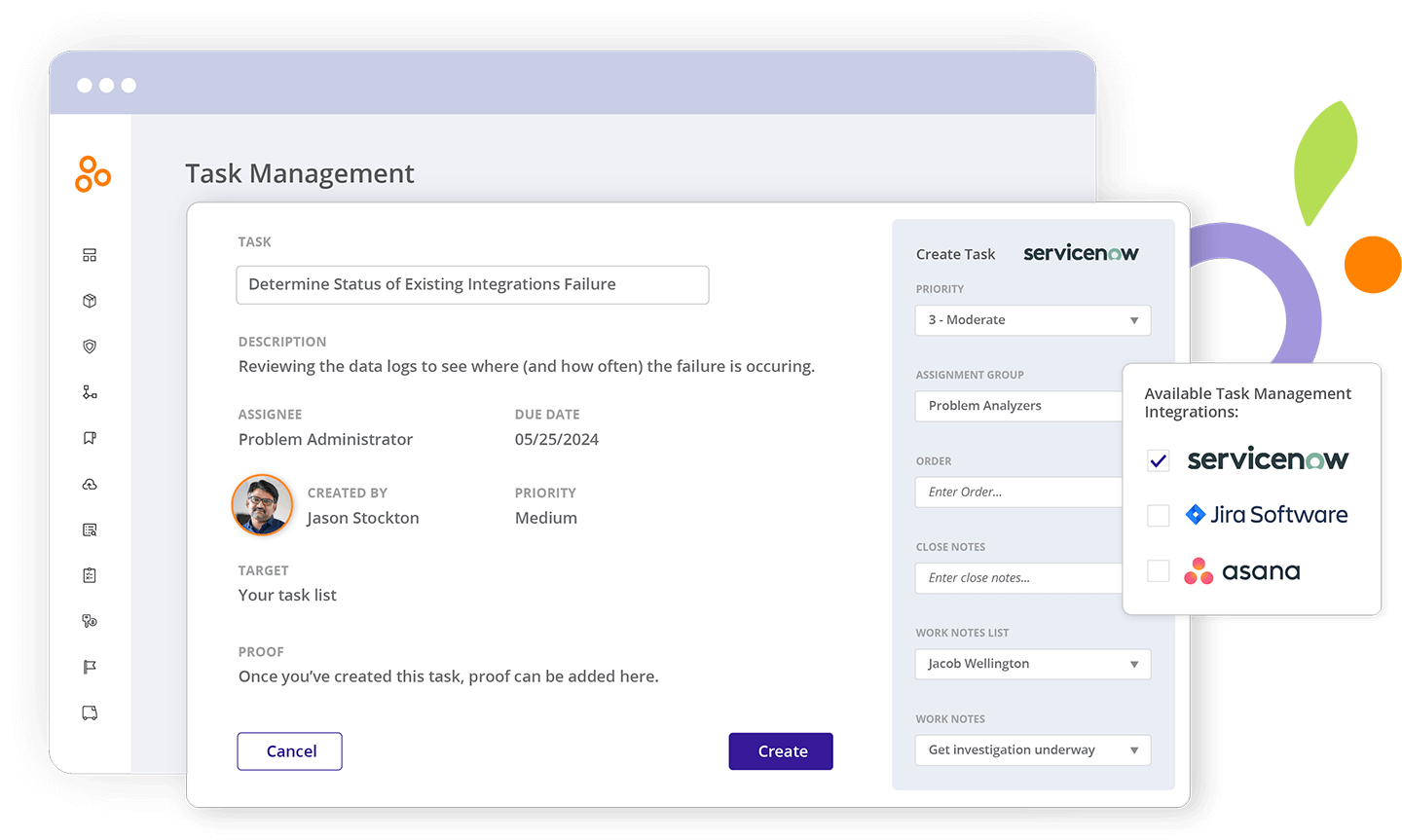
With Hyperproof’s integrated task management, IT, security, and GRC professionals can:
Audit management features
Trust management platforms like Hyperproof can save compliance teams many hours of work by streamlining audit preparation work and removing coordination and communication overhead. The software comes with features that help users:
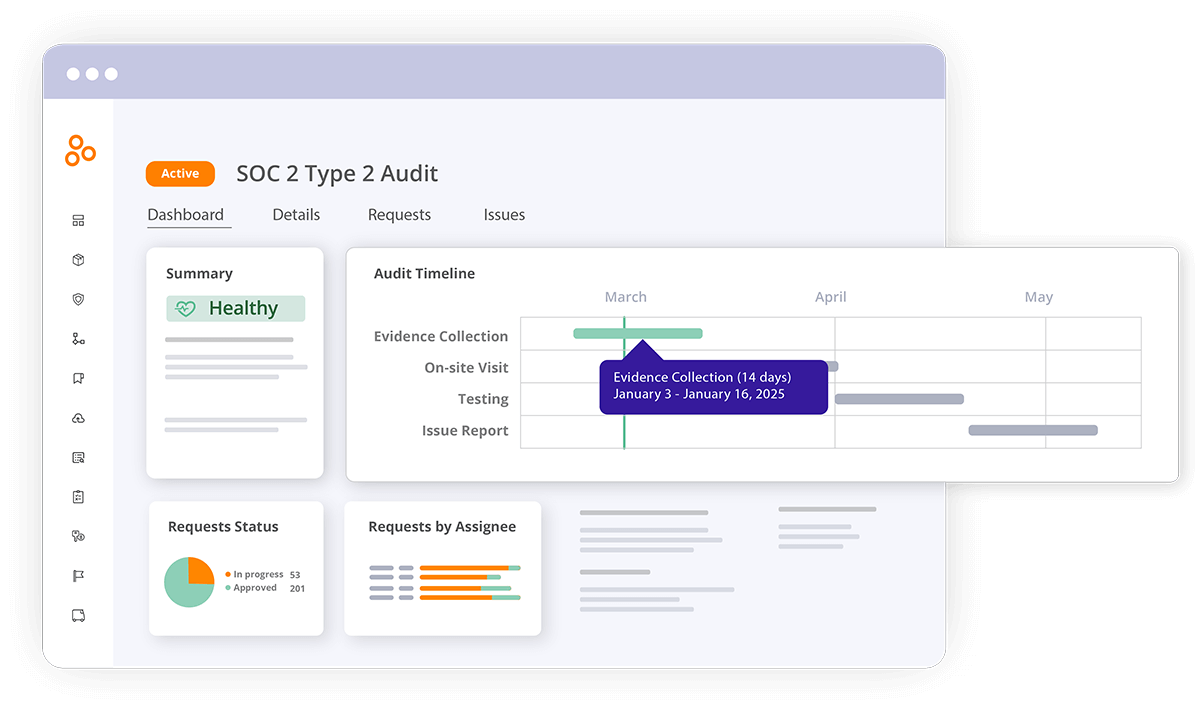
A structure for efficient, scalable controls management
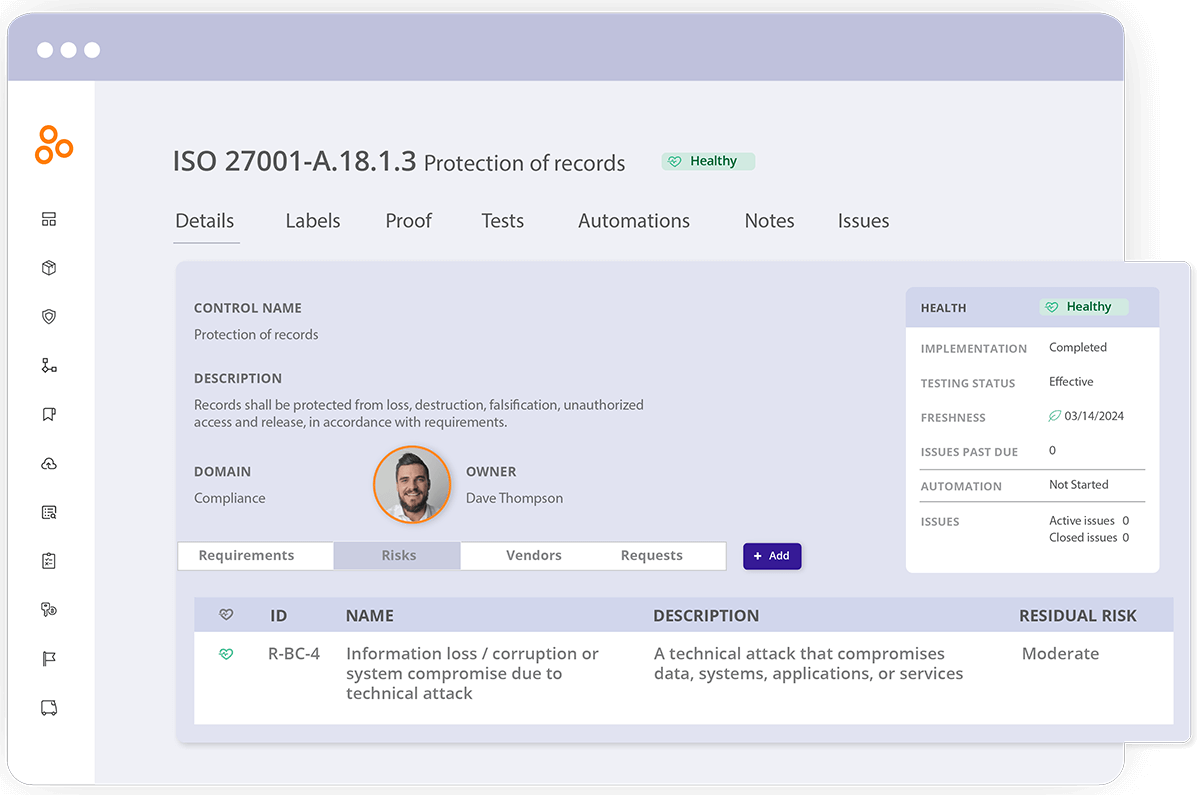
Trying to manage controls without duplicating work and getting visibility into the statuses of controls and risks can be challenging for larger organizations that need to manage controls across multiple sites, product lines and/or regions. In these scenarios, a supervisory team must communicate requirements to operators within the individual entities and ensure that the entities have implemented adequate controls that address the requirements. Operators within the individual entities must self-manage controls and provide evidence of their management to the supervisory team.
Hyperproof has a unique feature called Scopes that helps an organization efficiently manage controls at scale. It accomplishes four goals at once:
1. Control
The supervisory team can define baseline control requirements and communicate these requirements once to all operators within multiple entities, like product teams, facilities, and business units.
2. Autonomy
Operators within each entity can handle control implementation details, manage controls, collect evidence of controls, and track issues and tasks when controls require remediation.
3. Visibility
The supervisory team can easily see the status of all controls, identify which ones are unhealthy, and determine which entity the issue(s) comes from.
4. Accountability
The supervisory team can easily see and review evidence of control operation provided by the entity-level operators.
Each organization can define entities to reflect their preferred organizational structure. For instance, entities can represent systems that process sensitive data, facilities, products, business units or subsidiaries of a parent company.
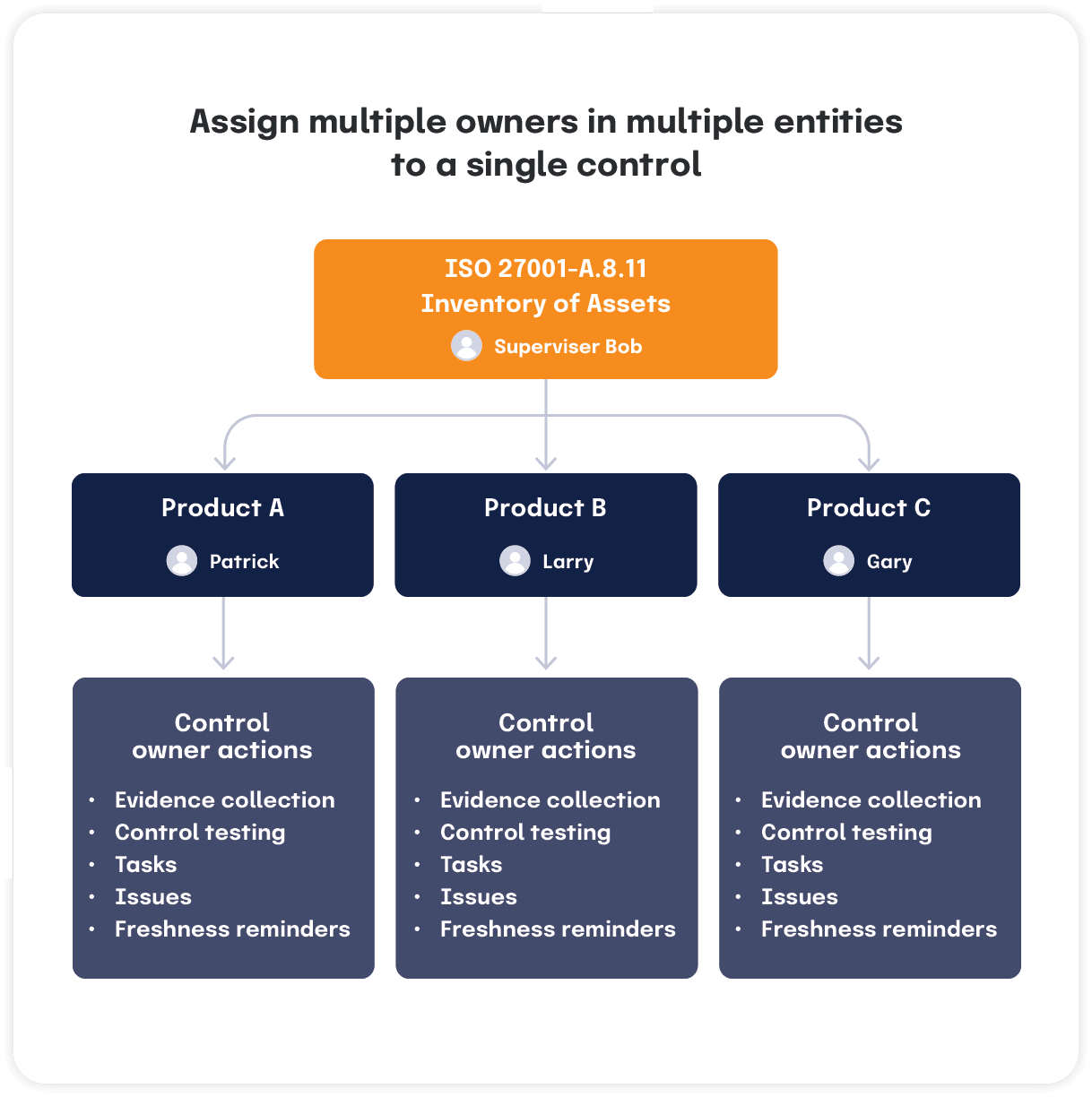
Once entities have been created, the supervisory team can assign a single control to multiple “owners” across entities. Entity-level control “owners” can conduct all control management activities in Hyperproof.
Meanwhile, the supervisory team can easily see the status of all controls, identify which ones are unhealthy, and determine which entity the issue(s) comes from. They can also see and review evidence of control operation provided by the entity-level operators, ensuring transparency and accountability throughout the compliance management process.
Risk management features
Trust management platforms play an essential role in risk management. They have features that help risk management teams and company executives track risks, gain greater visibility into their risk posture, and prioritize risk treatment. They also allow teams to execute risk-related work more efficiently.
Multiple risk registers
Maintain a central registry to track risks, document risk mitigation plans, and help stakeholders prioritize which risks to address first. Create new risk items in Hyperproof directly or migrate your existing risk register to Hyperproof by importing a CSV file. Larger companies can stand up multiple registers in their Hyperproof account – each register with its own assessment scale.
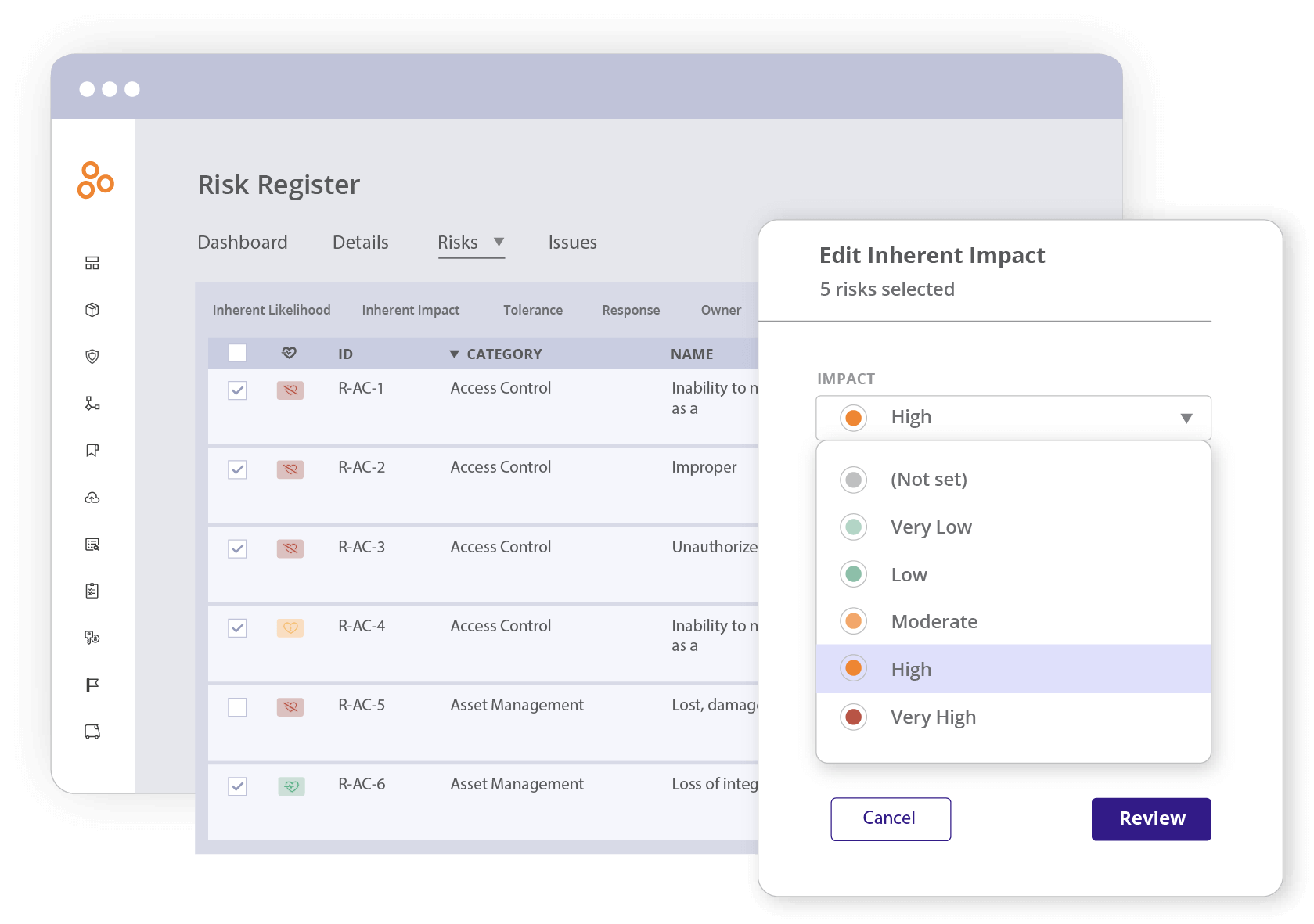
Built-in and custom fields
Use standard fields for evaluating each risk: tolerance, actual risk, inherent risk, likelihood and impact — all with customizable scales. Add custom fields that can function as filters on your dashboards and reports to track additional information on each risk.
Vendor tracking
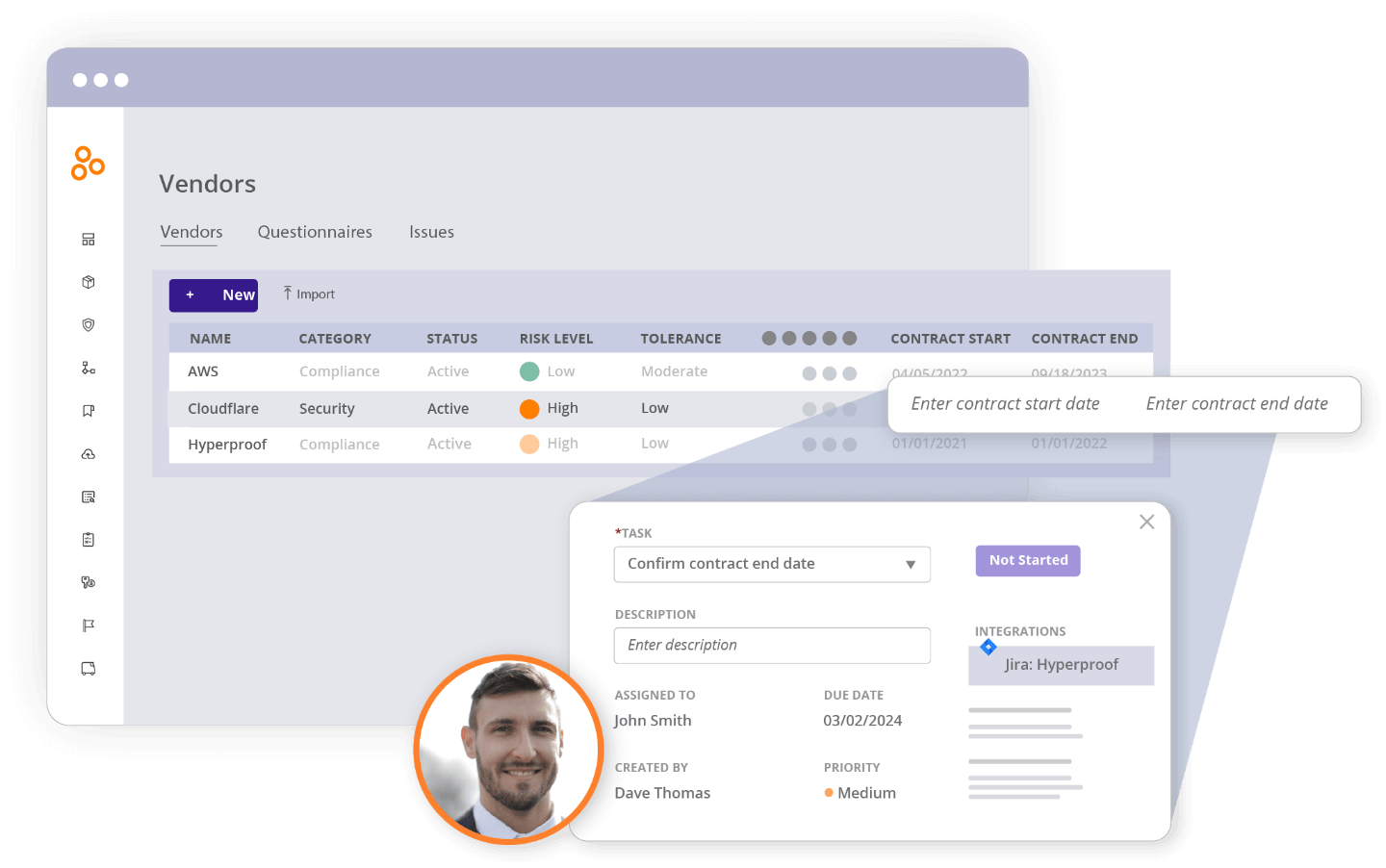
Use a central source of truth for all of your vendor contracts, risk assessment questionnaires, documents, and vendor information, and assess vendor risk profiles. Create vendor risk assessment questionnaires and track their vendors’ responses. Use questionnaire responses and other data sources to assess each vendor’s risk profile.
Link controls to risks
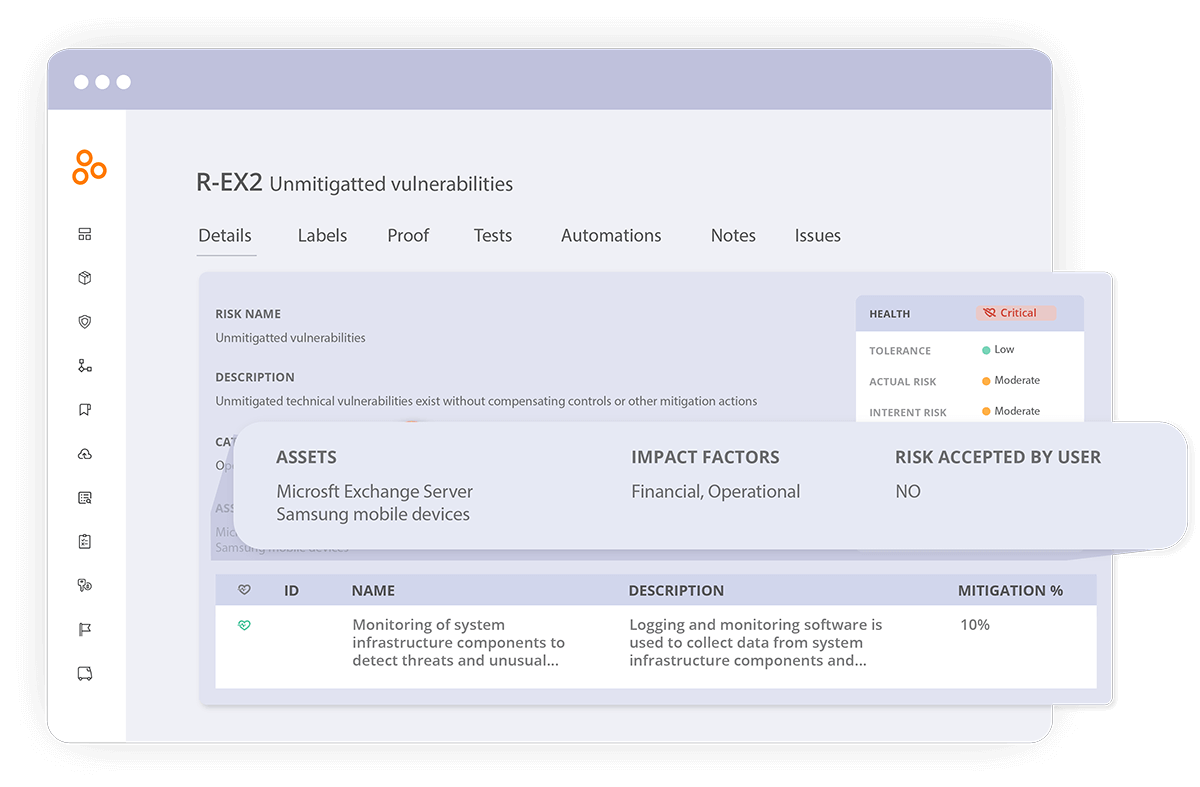
Prioritize which risks need attention and link controls to risks in the risk register. Document each control’s mitigation strength in percentage, understand how controls are used to mitigate risks, view residual risks, and monitor risks based on the health and effectiveness of linked controls. You can also specify how a control would reduce the risk in terms of likelihood or impact. This step helps users understand which risks require further mitigation and which are well covered.
Streamline remediation workflows
Hyperproof supports creating risk mitigation plans with tasks for different owners. With bi-directional syncs to Jira, Asana, and ServiceNow, tasks created in Hyperproof can be completed in the assignee’s preferred project management system. All task-related information, including updates to task attributes and uploaded proof, is visible in both applications and synchronized across platforms.
Dashboards and reporting
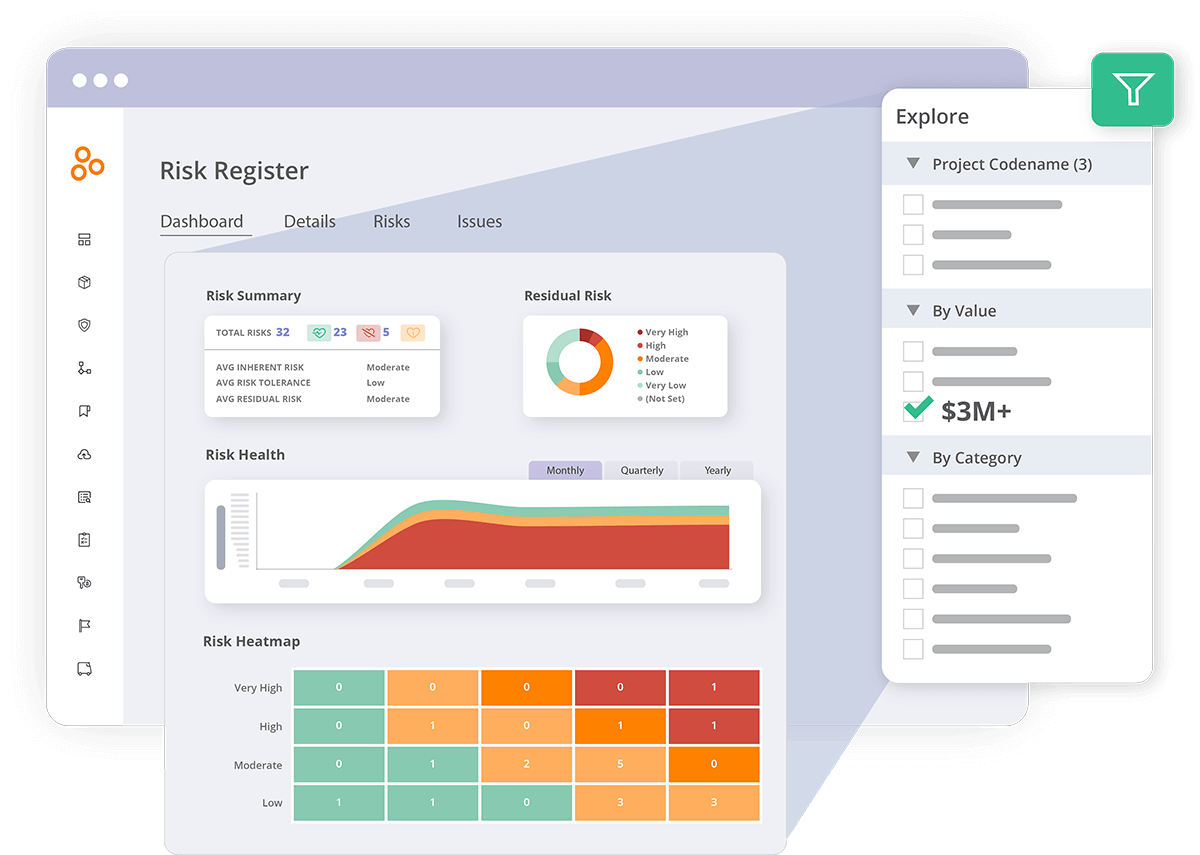
Monitor risks with a built-in dashboard that provides insights on which risks require mitigation, how risks are being mitigated within the organization, and how they trend over time. Answer important questions from company executives about risk in minutes instead of hours with built-in dashboards and custom reports. Distribute reports to stakeholders automatically in your preferred formats, like CSV or PDF.
Integrations for automated evidence collection, control testing, and risk detection
In a time when most organizations are heavily reliant on third-party software and cloud infrastructure providers to run their business, missteps in configurations and user access management have become a common source of cyber risk. Modern trust management platforms play a watchguard role, helping organizations notice flaws with their system configurations and user management controls so they can fix them before threat actors can exploit these vulnerabilities.

Platforms like Hyperproof were built with this use case in mind. Hyperproof comes with native integrations, called Hypersyncs, with 70+ enterprise apps and cloud services containing valuable risk detection information.
For instance, Hyperproof integrates with products provided by all major cloud service providers. An organization using AWS services (e.g., EC2, IAM, S3, and VPC) could connect these services with Hyperproof to automatically pull information from those services, revealing how the org handles information system security, identity, authentication, and configuration and change management. Once these Hypersyncs are set up, a security or compliance professional can write automated tests on the evidence brought in from AWS. This step helps them identify failing or unhealthy controls sooner than otherwise and take a more proactive approach to trust management.
Guidelines for choosing a trust management platform

How does an organization choose the right trust management platform?
Generally, the right software for your organization is one that allows you to accomplish your goals easily, supports your preferred ways of working, doesn’t create unnecessary overhead, can be implemented within your desired timeline, and comes at a price point you can afford.
As you consider various options to reach a decision, we recommend that you start with the end in mind and define what success looks like once the chosen software has been implemented and people in your organization are using it regularly.
After helping hundreds of customer organizations implement Hyperproof’s trust management software, here are the key things we recommend you consider during your buying journey.
1. Determine what you do and don’t need.
Different trust management software companies have taken different approaches in their product design because they’ve optimized their products to serve different user profiles and needs. While a particular vendor may be highly popular, it’s not necessarily suitable for you. Each organization must determine whether a vendor’s offering can help them accomplish what’s most important and whether the product design supports how they prefer to work.
For instance, Hyperproof is highly customizable so each organization can specify how they want to manage compliance. Other tools in the market are less customizable and contain many prescriptive workflows and guardrails. These tools are built for companies (primarily startups) with limited experience in compliance management. Their users want specific, prescriptive templates for managing their programs.
2. Start with clear priorities and desired outcomes.
You may want to improve multiple processes, and you will improve all processes over time. To choose the right partner for your needs, you should first define what is most important to accomplish.
What are the one or two features or modules, if implemented, that would provide a significant benefit in a relatively short amount of time? It is best to start by implementing the key features to achieve a “quick win” and build stakeholders’ confidence in the new software before implementing other “advanced” features.
3. Define what success looks like.
Ask yourself the following:
4. Know what resources and support you need to be successful.
What resources (e.g., people, training, documentation) and support does your organization need to use the new software? How will users become proficient? For example, could your users become self-reliant after initial training, or will they need to rely on specialists from the vendor company or external consultants to do things on their behalf? If you need extra support (e.g., consultants), does your organization have the means to pay for them? Answering these questions can help you understand what resources you need for a successful implementation.
5. Document and communicate your timeline.
If you know when you need to start using the software, you can find out from the vendor whether they can help you get up and running in time to achieve this milestone. Take into account any upcoming projects or initiatives you will use a trust management platform for when defining your timeline, and clearly communicate it to your vendor during implementation.
How to successfully implement a trust management platform: 4 helpful tips
While we’ve already touched on implementation in the last section, genuine success is achieved when you can use your new trust management platform to achieve your objectives and people in your organization start to notice the difference.
To ensure a successful implementation, be sure to consider the following:
- Have clear priorities and implement the most critical features first to get those quick wins under your belt.
- Consider your core user groups from the start. Educate them on the benefits of using a trust management platform and communicate what’s in it for them. Ensure they receive proper training and guidance. Once they’ve begun to use the software, check-in with them to ensure they’re making progress and accomplishing their goals.
- Review how implementing the new software may disrupt specific individuals and existing processes. Develop ideas and strategies to alleviate those concerns and disruptions.
- Partner with your account’s implementation specialist and customer success manager (CSM). When you purchase new trust management software, you’ll most likely be assigned to an implementation specialist and a CSM who will provide software implementation guidance and project management and change management support to help you achieve your desired outcomes. Lean on them as a resource – as these individuals can provide valuable guidance because they’ve helped many others with similar challenges adopt new software.
Find a comprehensive solution for your GRC needs

In today’s fast-paced business world, trust management is critical for companies looking to innovate while grappling with the risks of change. A solid trust management platform like Hyperproof provides a comprehensive solution to help businesses stay compliant, manage risks, and build trust. By centralizing and streamlining processes, these platforms enable IT, compliance, risk management, and security teams to work more effectively while getting everyone involved across all departments.
To successfully roll out a trust management platform, companies must set clear priorities, understand the resources they need, and involve all the right people in the transition. With the right approach, businesses can leverage trust management to boost resilience, drive innovation, and gain a competitive edge in their industries.
Download the PDF