6 Key Findings from Hyperproof’s Summer 2025 IT Risk and Compliance Benchmark Report
Hyperproof’s recently published The Summer 2025 IT Risk and Compliance Benchmark Report offers our analysis and commentary on the current state of governance, risk, and compliance (GRC) and cybersecurity practices across organizations. We took a different approach to analyzing our data this year by comparing our findings with 10 other prominent industry research reports, highlighting persistent gaps between aspiration and implementation in security and compliance programs. We found that many organizations have made progress in certain areas, yet substantial challenges remain in bridging operational execution with governance expectations.
Let’s examine the top 6 key findings and themes from the report and perspectives from our panel webinar with Kayne McGladrey from Hyperproof and Amy Rojik and Jason Lipschultz from BDO.
Want a full breakdown of the Summer 2025 IT Risk and Compliance Benchmark Report’s findings?
1. Operational teams are experiencing a communication gap between board-level oversight
One of the most significant findings from the benchmark report highlights a significant disconnect between operational teams and board-level oversight. According to the report, 82% of teams believe they effectively assess control effectiveness, yet 45% of board directors still seek external validation despite this internal confidence. This misalignment suggests issues extending beyond technical assessment capabilities to more fundamental questions of governance and trust.
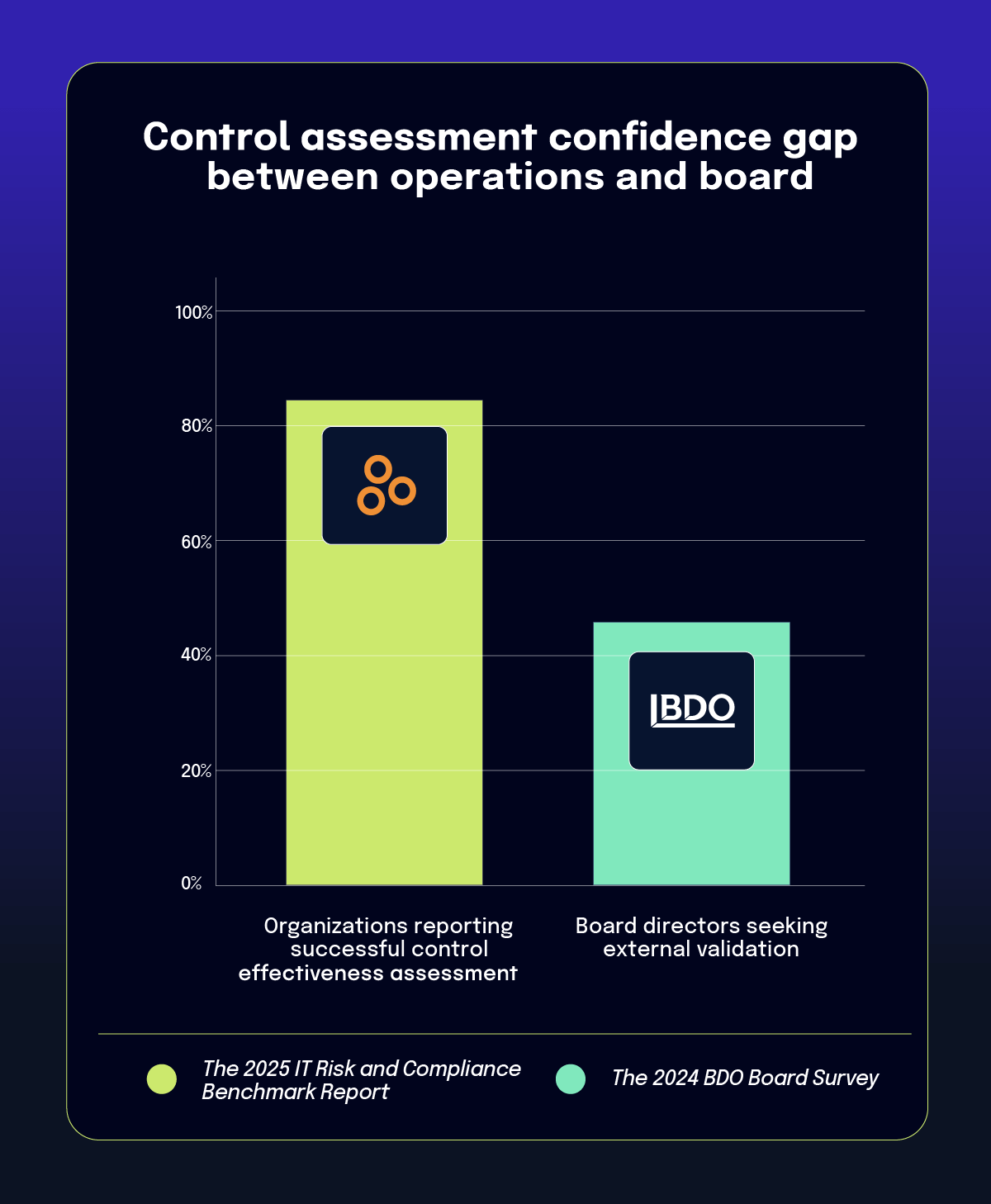
Our panelists noted that this gap might reflect the increasing regulatory scrutiny boards face, particularly following new SEC cybersecurity rules. As Amy explained, “Many directors are concerned that they’re not being provided with enough information about the risks to the enterprise posed from digital exposure and vulnerabilities, and they’re really eager to understand and ask better questions of management.”
The disconnect has roots in both regulatory pressure and fiduciary responsibility. Board members, who face personal liability for oversight failures, often seek additional assurance beyond internal assessments. External assessments serve dual purposes: practical validation of internal security measures and documentation of due diligence for regulatory compliance. As regulatory expectations intensify, particularly with the SEC’s cybersecurity disclosure requirements (originally implemented in 2023), boards seem increasingly unwilling to rely solely on management’s self-assessment of control effectiveness.
2. Confidence in continuous controls monitoring is high, but implementation lags behind
The report reveals a sizable gap between ambition and execution in continuous controls monitoring. A striking 94.2% of CISOs believe continuous controls monitoring improves compliance and security, yet only 72% of organizations have implemented related monitoring solutions. Even more concerning, 53.7% of organizations lack compliance integration in their development pipelines.
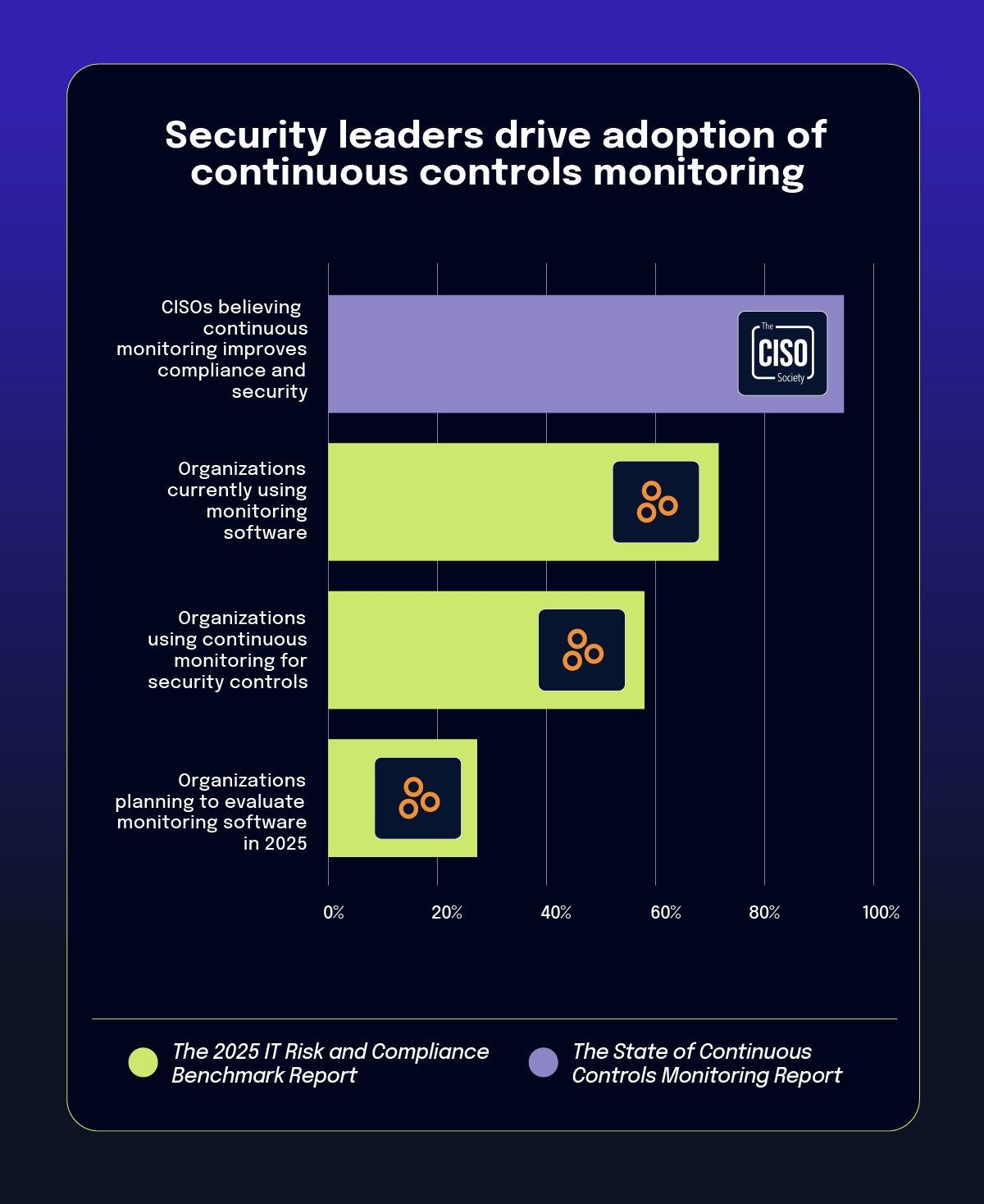
This gap between aspiration and implementation stems from several factors. During the webinar, Jason noted: “The difference of recognizing the importance of automation — the value it brings to do things quicker, faster, and even produce risk — but the reality is that employment can get a little bit more difficult.”
From a business perspective, this implementation gap creates several problems:
The panel discussion highlighted that successful implementation requires looking beyond technology to people and processes. As Jason explained, “To do it requires a change in mindset, in people, and changing processes in leveraging technology. It’s really about looking at every single thing you do and asking yourself: ‘How could I do this better?’”
In business terms, the data suggests many organizations invest in monitoring tools but fail to realize their full financial benefits because they don’t integrate these systems with their operational workflows. The result is similar to purchasing an expensive accounting system but continuing to track finances in spreadsheets: the capability exists, but it doesn’t deliver its promised value.
These continuous control monitoring challenges represent one facet of a broader integration problem facing organizations. The gap between security monitoring aspirations and implementation realities mirrors the larger disconnect between risk management and compliance functions. These scenarios reflect how difficult it is to move from conceptual alignment to operational integration, requiring organizations to address both technology gaps and process and cultural barriers.
3. Only 44% of organizations have fully integrated risk management with compliance operations
The report presents a nuanced picture of risk and compliance integration. According to the data, 84% of organizations have aligned their risk management with compliance (mapping controls to risks), yet only 44.1% report complete synchronization between these functions. Similarly, 51% of organizations have integrated risk responsibilities into compliance personnel roles, suggesting progress toward unified governance structures.
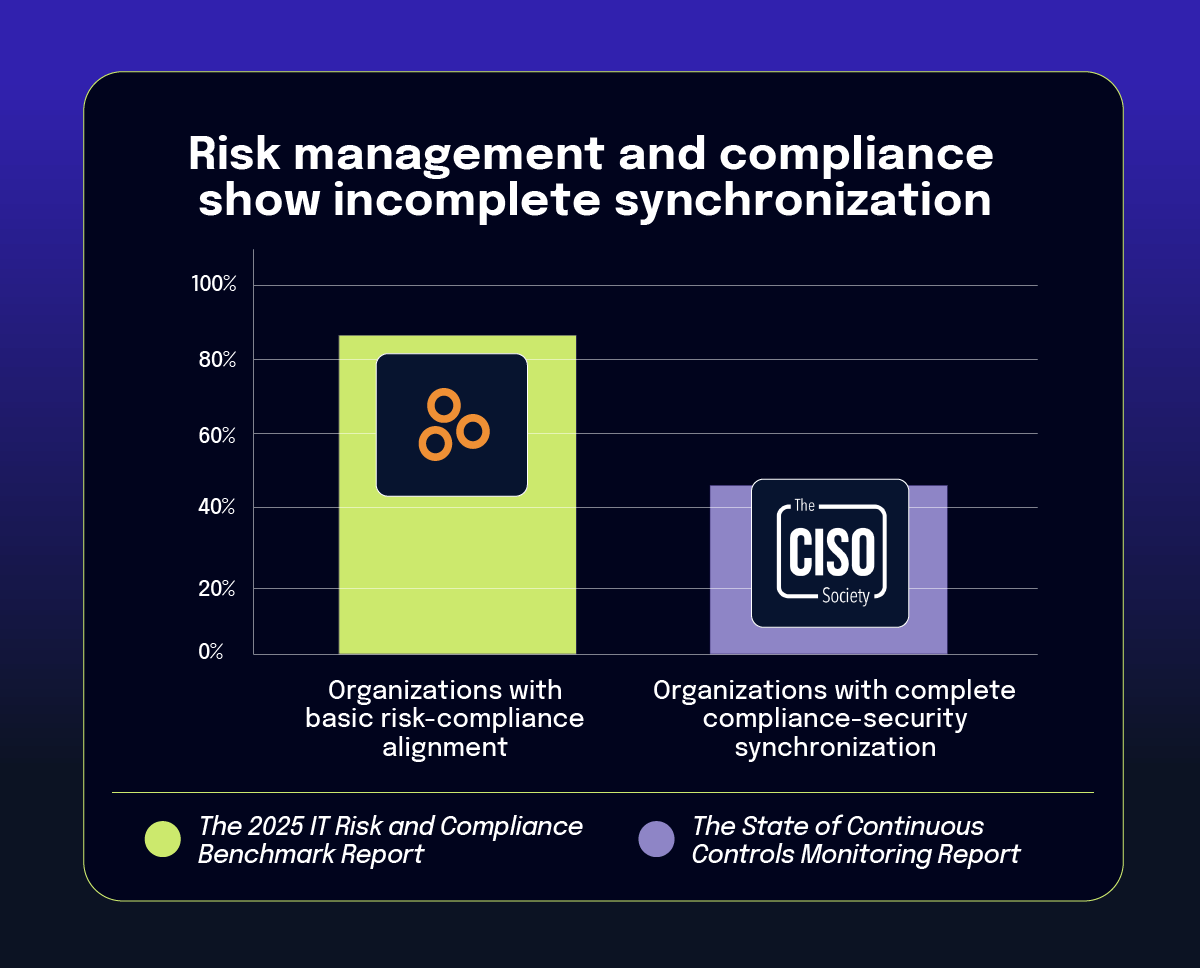
Integrated risk management faces significant technology architecture challenges, with 14% of organizations lacking supporting infrastructure. This translates to tangible business problems:
The panel experts recommended enterprise-wide risk frameworks rather than siloed approaches. Amy explained: “Companies need to be looking at their entire risk profile across the organization and not in these neat little silos… they should focus on their enterprise risk management structure and how it feed sall of these response plans and other resource allocation.”
The experts also suggested rethinking the role of the CISO in risk management. Rather than positioning GRC leaders as directly responsible for all security risks (a first-line defense role), organizations might benefit from positioning them in a second-line oversight function. This allows business leaders to make informed risk decisions based on security guidance, rather than placing the full burden of risk management on GRC teams.
The data suggests organizations are at different stages of maturity in their integration journey:
4. 56% of respondents view GRC as a cost center rather than a business enabler
The report highlights a perception problem that may undermine security programs: 55.8% of CISOs consider security and compliance a cost center rather than a business enabler. Regrettably, this perception continues to limit strategic influence and resource allocation for security initiatives.
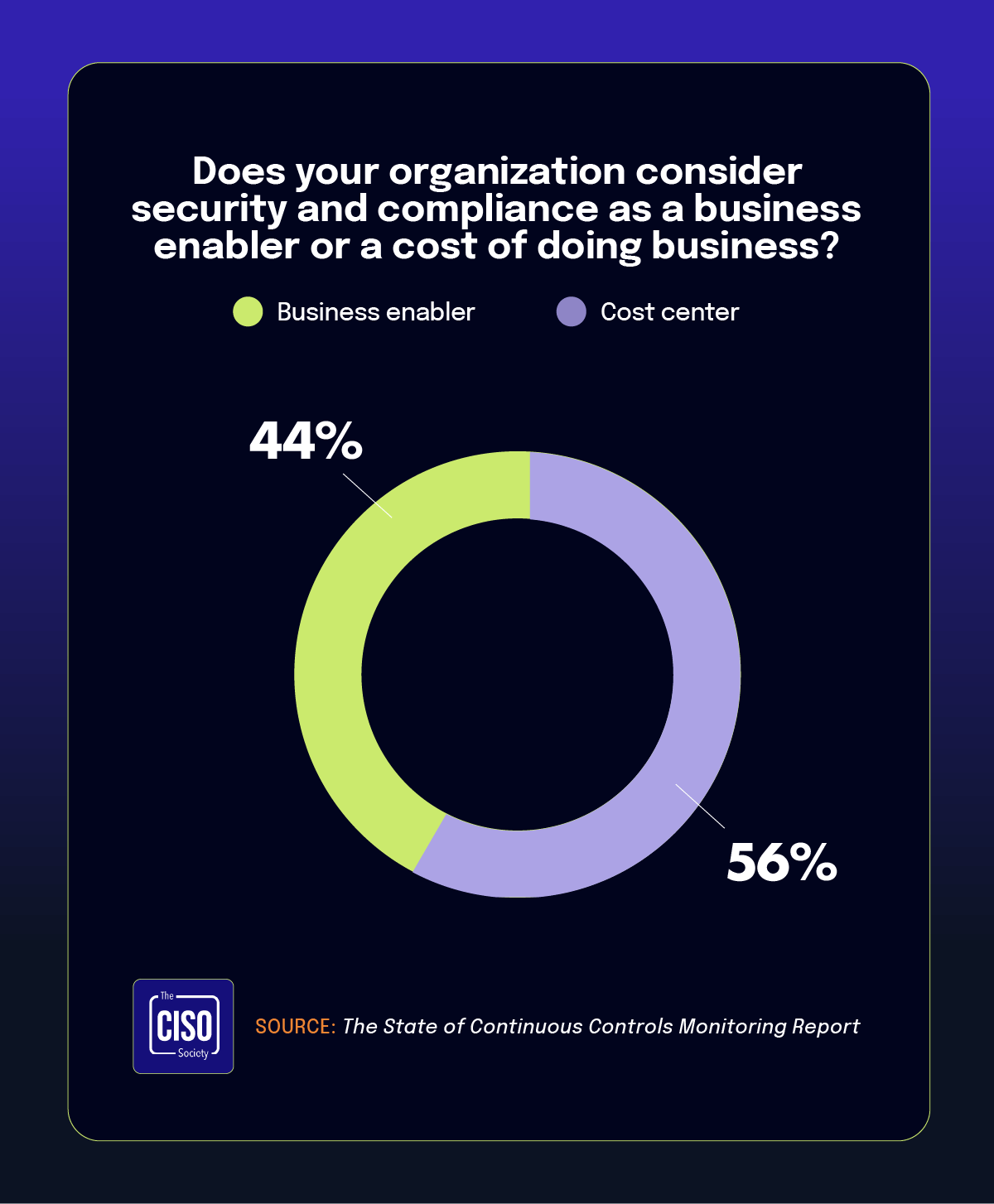
When GRC is framed as a technical expense rather than a business investment, it creates a language barrier between operational teams who discuss controls and technologies and directors who focus on business risk and compliance obligations. This communication gap further reinforces the trust issues discussed earlier, contributing to boards seeking external validation despite internal confidence in security measures.
The panel experts recommended several approaches to shift this perception:
- Integrating security metrics with business outcomes
- Establishing cross-functional committees that include security leaders alongside business executives
- Creating appropriate reporting structures that position security as a business function
- Demonstrating the revenue protection and customer retention value of strong security programs
Jason emphasized the importance of demonstrating business alignment: “Good CISOs can both be effective in the command center as well as at the boardroom level.” He further explained the need for making the direct connection between compliance work and business outcomes, noting that when prospects or customers require specific controls, and there’s direct dollars on the table…we can demonstrate that we’re supporting them and protecting that revenue.”
The panel suggested that normalizing security investments, similar to how physical safety measures are accepted with minimal debate, might help shift organizational thinking. As Kayne noted: “If you build a retail store, you’re going to have a fire suppression system; you’re not going to question why you have a fire suppression system.”
5. 40% of respondents lack centralized systems for managing risk and compliance data
The benchmark report indicates that over 40% of organizations lack centralized systems for managing risk and compliance data. This technology gap reflects broader challenges in board oversight and technology literacy that impact governance effectiveness.
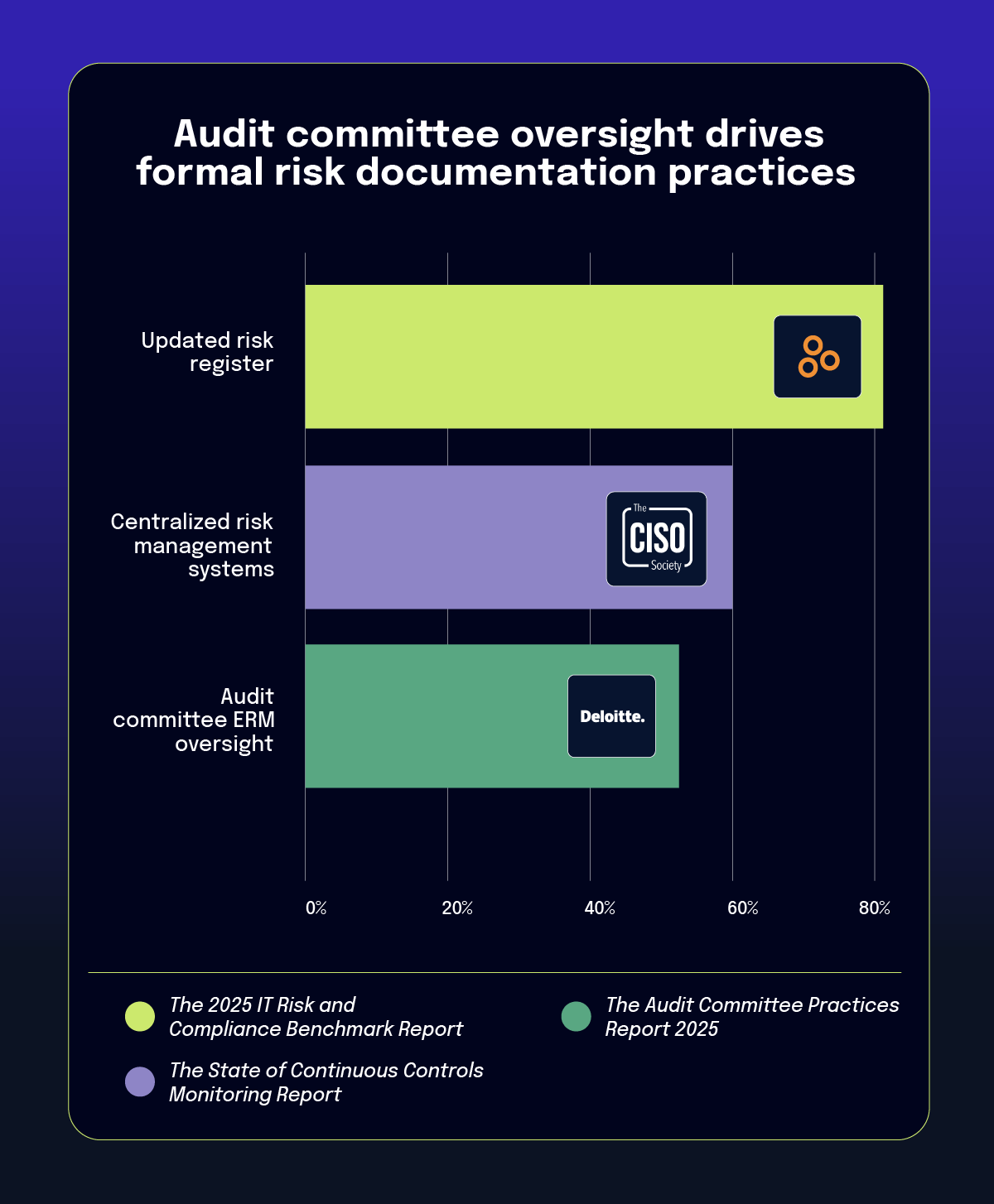
The panel experts emphasized that all board members need baseline technology literacy, not just designated “tech experts.” Amy noted: “If you think about the board in general, all board members are expected to have some level of financial literacy … It’s the same with technology and cybersecurity.” This perspective challenges earlier approaches that suggested having a single technology expert on the board would suffice.
Regarding oversight structures, the report reveals that cybersecurity oversight commonly resides with audit committees (81% of Fortune 100 companies), yet only 4% of organizations have board members directly overseeing compliance. This delegation to committees allows boards to maintain strategic focus while ensuring specialized attention to complex compliance areas.
The experts suggested establishing minimum technology literacy standards for all directors, regardless of their primary expertise. As Amy explained: “There’s a certain minimum bar of education that all directors need to have in this space with respect to industry risks and business-specific risks like cyber and other things.”
The experts also noted the increasing importance of the board’s role in setting the risk appetite for the organization and clearly communicating those boundaries throughout the business. This top-down guidance provides clarity for operational teams making security decisions and helps bridge the gap between governance expectations and implementation realities.
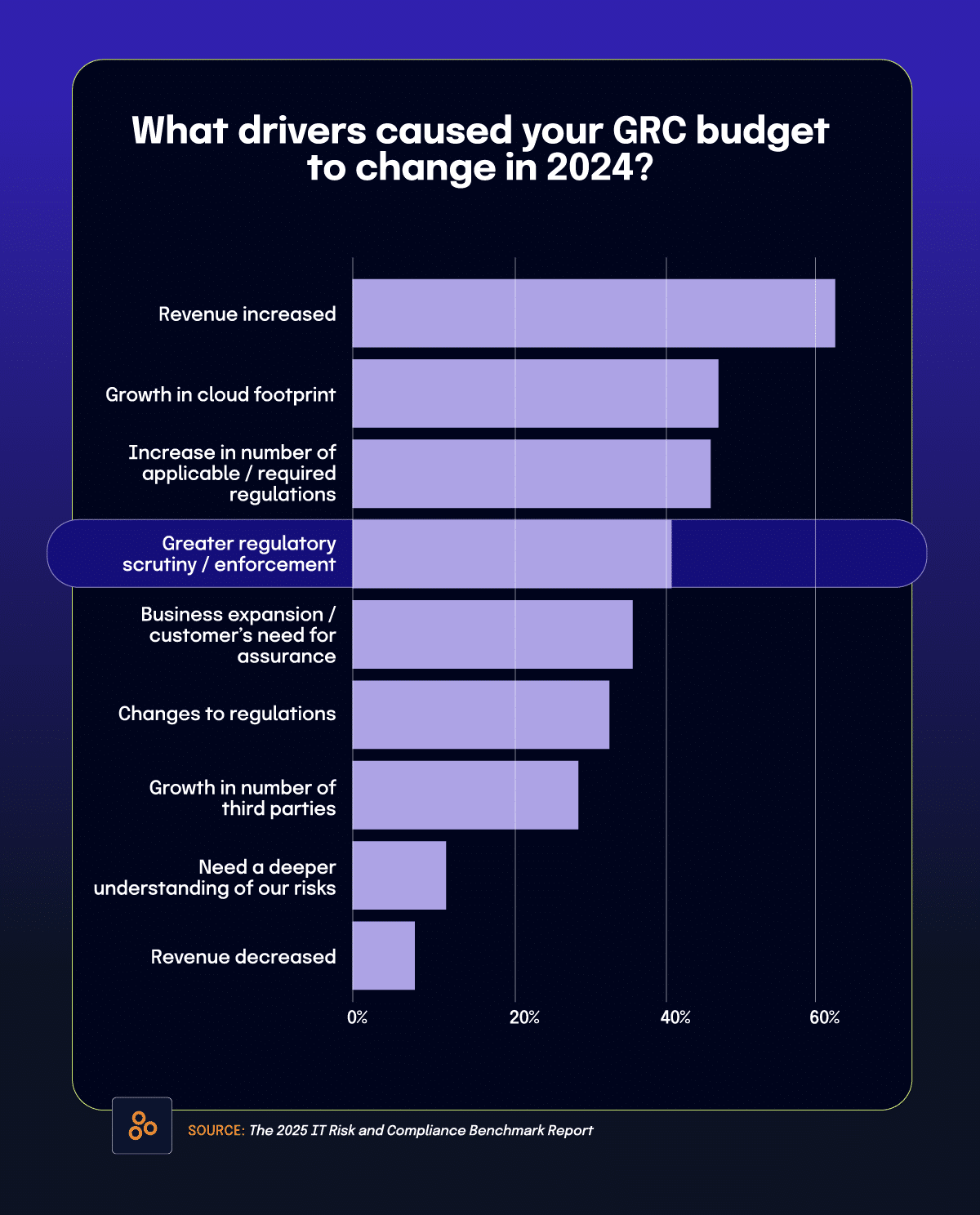
6. 41% of respondents adjusted their budgets due to increased regulatory scrutiny
The benchmark report identifies significant compliance challenges stemming from regulatory fragmentation across jurisdictions. According to the findings, over three-quarters of CISOs report that regulatory fragmentation significantly impacts their compliance efforts. Perhaps more concerning, only 17% of organizations adhere to country-specific data security and privacy laws despite their growing prevalence.
This fragmentation creates multifaceted challenges:
The financial impact can be substantial, with 41% of organizations reporting they adjusted their GRC budgets due to increased regulatory scrutiny. Despite these pressures, compliance teams remain remarkably stable compared to other security functions, with only 1% of organizations expecting reductions in compliance personnel.
The panel experts noted that technology debt and merger and acquisition (M&A) integration create additional compliance complications. Amy explained: “I think particularly about companies that have grown very quickly through M&A transactions … and they’re bringing in all kinds of disparate systems and trying to say, ‘We’ll deal with that later.’” This approach can create significant security and compliance gaps that become apparent only after integration.
Looking ahead, the regulatory landscape appears likely to remain fragmented despite some consolidation efforts. The panelists noted that although the EU had suggested deconflicting and consolidating regulations (hopefully in November 2025), limited progress has been made toward that goal. In the US, state-level privacy and security regulations continue to multiply, creating additional compliance complexity for organizations operating across state lines.
Recommendations for GRC and cybersecurity professionals
Based on the expert panel discussion and report findings, cybersecurity and GRC professionals should consider the following action items to strengthen their programs and address common challenges:
Improve board communication
Developing metrics and reporting that align with board expectations and regulatory requirements is essential for building trust between operational teams and governance bodies. This communication should focus on business impact rather than technical details, addressing the board’s concern with risk oversight rather than technical implementation.
Specific actions might include:
Reposition security narratives
Framing security initiatives in terms of business value, customer requirements, and revenue protection rather than technical compliance can help shift perceptions of security as an operational expense. This repositioning requires consistent messaging and demonstrable business alignment.
Practical tactics include:
This repositioning addresses the communication gap by creating a shared language between security teams and the board, potentially reducing the perceived need for external validation as internal assessments become more business-focused and trustworthy.
Enhance board education
Creating tailored technology and cyber risk education for directors that focuses on business implications rather than technical details can strengthen governance oversight. This education should acknowledge directors’ existing expertise while expanding their technology awareness in relevant areas.
Effective approaches to consider:
Prioritize automation strategically
Given the gap between aspirations and implementation for continuous controls monitoring, organizations might benefit from a phased approach. Starting with the highest-risk areas and building toward development pipeline integration allows for incremental progress, demonstrating value at each stage.
Consider these implementation strategies:
Pursue meaningful integration
Moving beyond surface-level alignment between risk and compliance toward true operational synchronization requires shared processes and technology platforms. Organizations should consider a maturity model approach that establishes clear milestones for integration progress.
Integration strategies could include:
Address regulatory complexity
Developing a systematic approach to regulatory tracking that prioritizes requirements based on business impact and enforcement likelihood can help manage the fragmented compliance landscape. This approach requires both processes and technologies that support efficient compliance operations.
Consider implementing:
Prepare for continued investment
Compliance team staffing remains remarkably stable despite potential budget pressures, indicating organizational recognition of compliance importance. GRC professionals might leverage this stability to secure resources for long-term program improvements rather than focusing exclusively on immediate compliance requirements.
Investment priorities could include:
The Summer 2025 IT Risk and Compliance Benchmark Report contains additional findings and detailed analysis that can help organizations benchmark their practices against industry standards and identify specific improvement opportunities. As regulatory expectations continue to change and cyber threats grow increasingly sophisticated, the ability to balance compliance requirements with business objectives becomes even more valuable.
Want to unlock all the findings from this report? It’s available now at no cost to you!
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












