These days, a SOC 2 report is considered a must-have for any organization that manages customer data. Getting the SOC 2 type 2 report signals that an organization demonstrates a baseline level of maturity when it comes to safeguarding data and ensuring privacy, data confidentiality, availability, and processing integrity.
Launching an IT compliance effort to achieve a SOC 2 type 2 report is no easy feat. It’s often the first major compliance milestone young organizations achieve. Now that this big milestone is behind you, you’re trying to figure out where to go from here. You’re wondering:
- What IT security certifications, standards, and regulations should you consider next? If you want to take a more rigorous approach to managing cyber risks, what voluntary cybersecurity frameworks could you adopt?
- Would achieving compliance with certain cybersecurity standards or aligning your information security management program with a particular framework give you an edge over the competition?
- Could it provide an advantage in keeping up with new data privacy regulations?
There isn’t a single cybersecurity framework or standard that is inherently better than the rest. What you work on next should be based on your understanding of your market, the wants and needs of your customers, the regulatory requirements your organization needs to demonstrate compliance to, and the risks your business needs to manage. Key factors to consider include:
1. Business goals and customer requirements
How do you want to grow as a business? What types of customers do you want to serve in the next one to three years? Your target customers will have specific IT compliance requirements for their vendors depending on their industry, region, and the regulatory environment they’re in. For instance, here are some specific standards, certifications, and frameworks to consider:
- Want to do business in Europe? Consider ISO/IEC 27000 series. When an organization is ISO 27001 certified, it means that the organization’s information security management system (ISMS) conforms to the ISO 27001 standard. ISO 27001 is seen as a gold standard in information security by organizations around the world. You’ll also need to comply with Europe’s GDPR in order to earn the trust of your European customers.
- Want to do business with healthcare providers or health insurers? You need to be HIPAA compliant and may need to sign a Business Associate agreement to ensure that your organization will appropriately safeguard protected health information.
- Want to service the federal government? You need to prepare for the Cybersecurity Maturity Model Certification (CMMC) if you’d like to bid for contracts from the Department of Defense. If you want to sell a SaaS product, you’ll need to achieve a FedRamp authorization.
- Is your company planning to go public in the next 2-3 years? If so, you’ll need to prepare to comply with the Sarbanes-Oxley Act (SOX).
Achieving certain certifications and authorizations can be quite expensive and time-consuming. You’ll need to think carefully about whether it makes sense for your organization to invest the resources required to achieve compliance vs. the market opportunity opened up by having certain certifications and authorizations.
Want to know which data protection regulations and standards your business needs to adhere to? Take our Data Protection Compliance Quiz.
You’ve Done SOC 2, What’s Next?
See how you can use your SOC 2 effort to achieve other IT security certifications and standards ›

2. Security needs and risks

At this time, cyber attacks methods evolve quickly and they’re becoming increasingly sophisticated. Global cybercrime costs businesses 16.4 billion every day, with a ransom attack occuring every eleven seconds.
Chances are you have some security gaps at the moment. For instance, how would you score your organization’s capabilities in security assessment, access control, incident management and response, and configuration management? In addition to protecting your networks, systems, and data, your risk management plan should also cover your vendors. When over half of all data breaches are due to third-party vulnerabilities, you need to have a sound approach to vendor risk management.
Given your current security state and the risk landscape you’re operating in, it may be time to bring more rigor and discipline into your security and compliance program. At this time, many companies needing help in creating a rigorous approach to managing cyber risk have turned to voluntary security frameworks such as the NIST Cybersecurity Framework (CSF).
Developed by the National Institute of Standards and Technology, the NIST Cybersecurity Framework is a list of standards, guidelines, and practices designed to help organizations better manage and reduce cyber risk. It rests on industry best practices gathered from various documents and cybersecurity standards like ISO 27001 and COBIT 5. Security teams can use this framework to assess risk levels (both acceptable and current), align on risk tolerance objectives, set improved security priorities, and determine a budget to mitigate cyber threats.
The NIST framework discusses critical security activities incorporated into cybersecurity programs, which can be tailored to an organization’s unique needs. These critical security activities, broken down into five functions, are as follows: identify, protect, detect, respond, and recover. These five functions were selected because they represent the five primary pillars for a successful and holistic cybersecurity program.
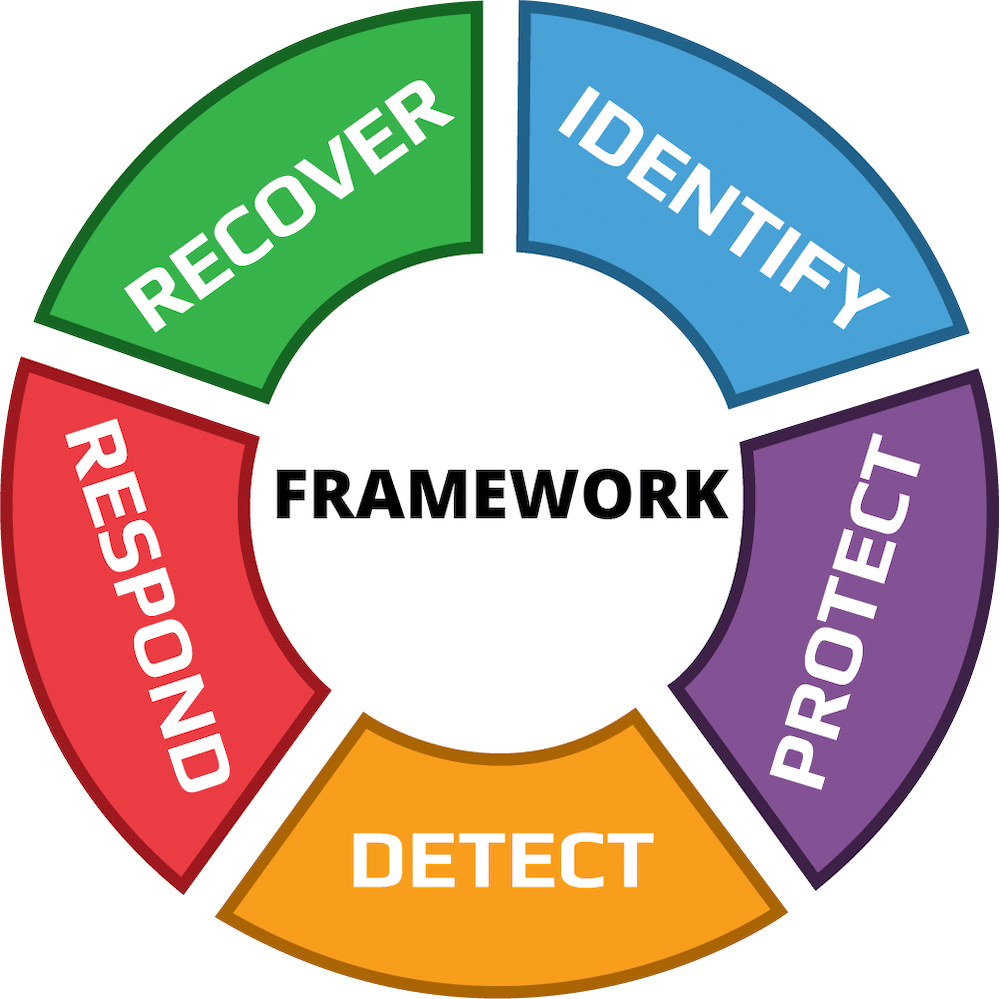
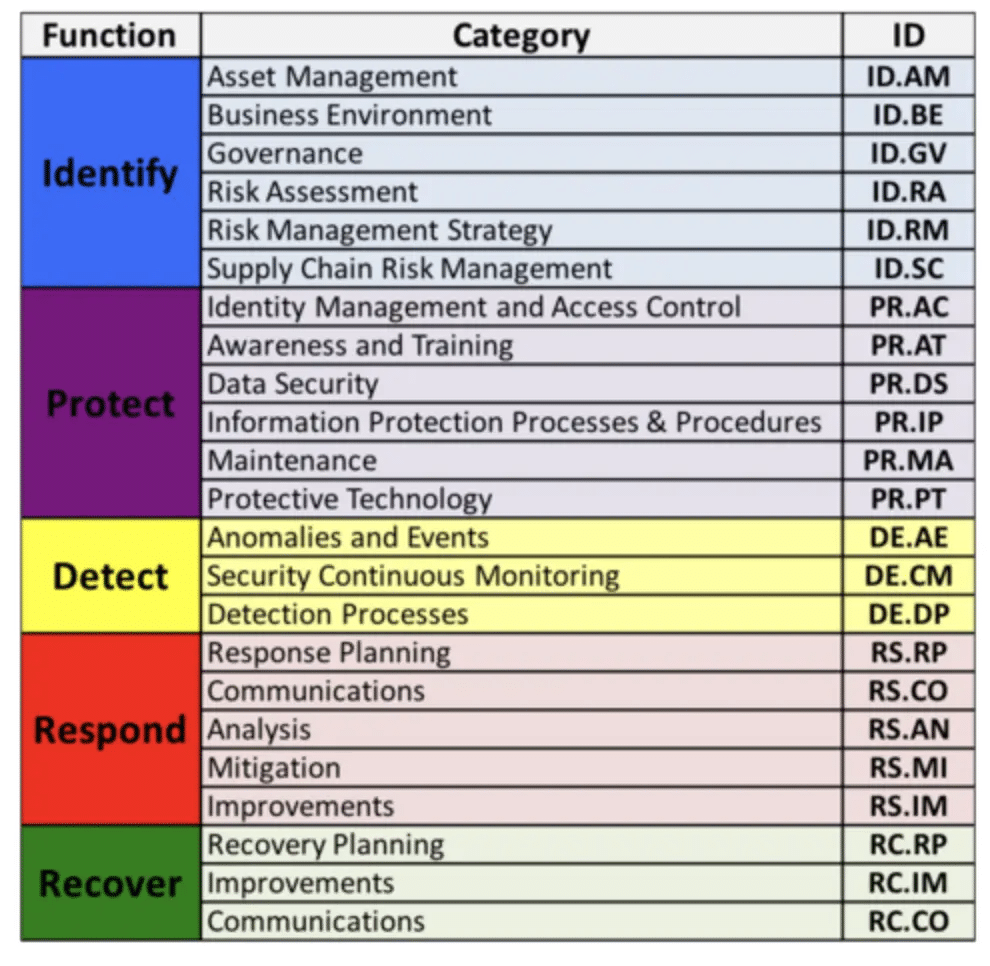
The five functions break out into 23 Categories which contain specific outcome driven statements that provide consideration for creating or improving a cybersecurity program. The categories were designed to cover the breadth of cybersecurity objectives for an organization. Subcategories (not shown here) are the deepest level in the CORE. There are 107 Subcategories, which are outcome-driven statements that provide considerations for creating or improving a cybersecurity program. Examples of Subcategories include 1) External information systems are cataloged, 2) Data-at-rest is protected, and 3) Notifications from intrusion detection systems are investigated.
The NIST CSF is outcome-driven but flexible on how each organization can achieve security objectives. This flexibility allows all companies, from the smallest and newest to the largest and most established to benefit from this guiding framework. By aligning your internal controls to the suggested security activities in NIST CSF, you’ll be in a position to meet the requirements of other industry-specific or regional cybersecurity standards and regulations easier.
If you want to get more details on this framework, you can visit the NIST website.
States Starting to Offer Liability Protection In Data Breach Lawsuits For Organizations that Have Adopted NIST CSF
In addition to the benefits mentioned above, adopting NIST may give you an additional benefit: Liability protection when your organization falls victim to ransomware and other cyber attacks.
Given the high frequency of ransomware and nation-state actors targeting US critical infrastructure, federal lawmakers are considering liability protection for organizations that experience malicious intrusions. However, lawmakers have said that if organizations want this protection, they need to step up their game to implement better cybersecurity practices.
During a Senate Intelligence Committee hearing in February 2021, Chairman Mark Warner (D-VA) said, “While I am very open to some level of liability protection, I’m not interested in a liability protection that excuses the kind of sloppy behavior, for example, that took place in Equifax, where the didn’t even do basic hygiene.”
In addition to federal level activities, a number of states (Ohio, Utah, and Nevada) have moved forward with their own liability exemption measures that seek to boost cybersecurity practices. These states have enacted laws that incentivize the adoption of robust and thorough industry-leading cybersecurity frameworks and recommendations such as the NIST Cybersecurity Framework or the Center for Internet Security’s (CIS) Critical Security Controls by making them requirements for obtaining liability protection.
How to Manage Compliance Work Without Getting Overwhelmed

If your organization has decided to adopt a new voluntary cybersecurity framework or comply with a regulatory standard, you may be thinking how do I manage this work efficiently and not get overwhelmed? Although the work is growing, my team isn’t.
To address this common question, we’ve created a new ebook: You’ve Done SOC 2, What’s Next? This guide details how you can leverage your SOC 2 work to achieve additional IT cybersecurity standards, frameworks and certifications with less effort. You can grab your copy below.
Ebook: You’ve Done SOC 2, What’s Next?

Monthly Newsletter
Get the Latest on Compliance Operations.