Third-Party Risk Management: Best Practices for Protecting Your Business

At this time, nearly every business outsources some aspect of its operations. But it’s becoming increasingly tricky for organizations to ensure that third-party providers remain a source of strength for their business — not a weak link.
According to Hyperproof’s 2025 IT Compliance Benchmark Report, 46% reported experiencing a third-party data or privacy breach that affected their organization’s records or data and 30% reported experiencing a compliance violation related to their organization’s third-party oversight.
Working with a third-party is inherently risky — you are trusting a business whose practices and processes you can’t control. As companies utilize third-parties more often and at a larger scale, the data security and privacy risks they face have also grown.
You don’t have to look hard to find examples of third-party data breaches. Large companies, from Solar Winds to Microsoft, Uber, and Toyota, have all fallen victim. According to the Verizon Business 2022 Data Breach Investigations Report, 62% of system intrusion incidents came through an organization’s partner, showing how prevalent supply chain issues have become.
When you’re working with a third-party service and trusting them with company, employee, or customer data, you can’t afford to take any chances. You need to ensure you are working with the most reliable, high-performing, and safe solutions.
So, what approaches, systems, processes, and procedures could you implement to protect your business while working with third parties? In this article, we’ll share some best practices you can implement to manage third-party risk systematically. We’ll also cover the changing nature of third-party risk and the most common types of third-party risks.
What is third-party risk management?
Sometimes referred to as TPRM, third-party risk management is a discipline that analyzes and controls risks associated with outsourcing third-parties or service providers. Third-party risk assessments are exercises you can conduct to help your organization determine how much risk exposure you’d take on if you were to outsource a business process or entrust your data to a third party.
Recent changes in third parties risk
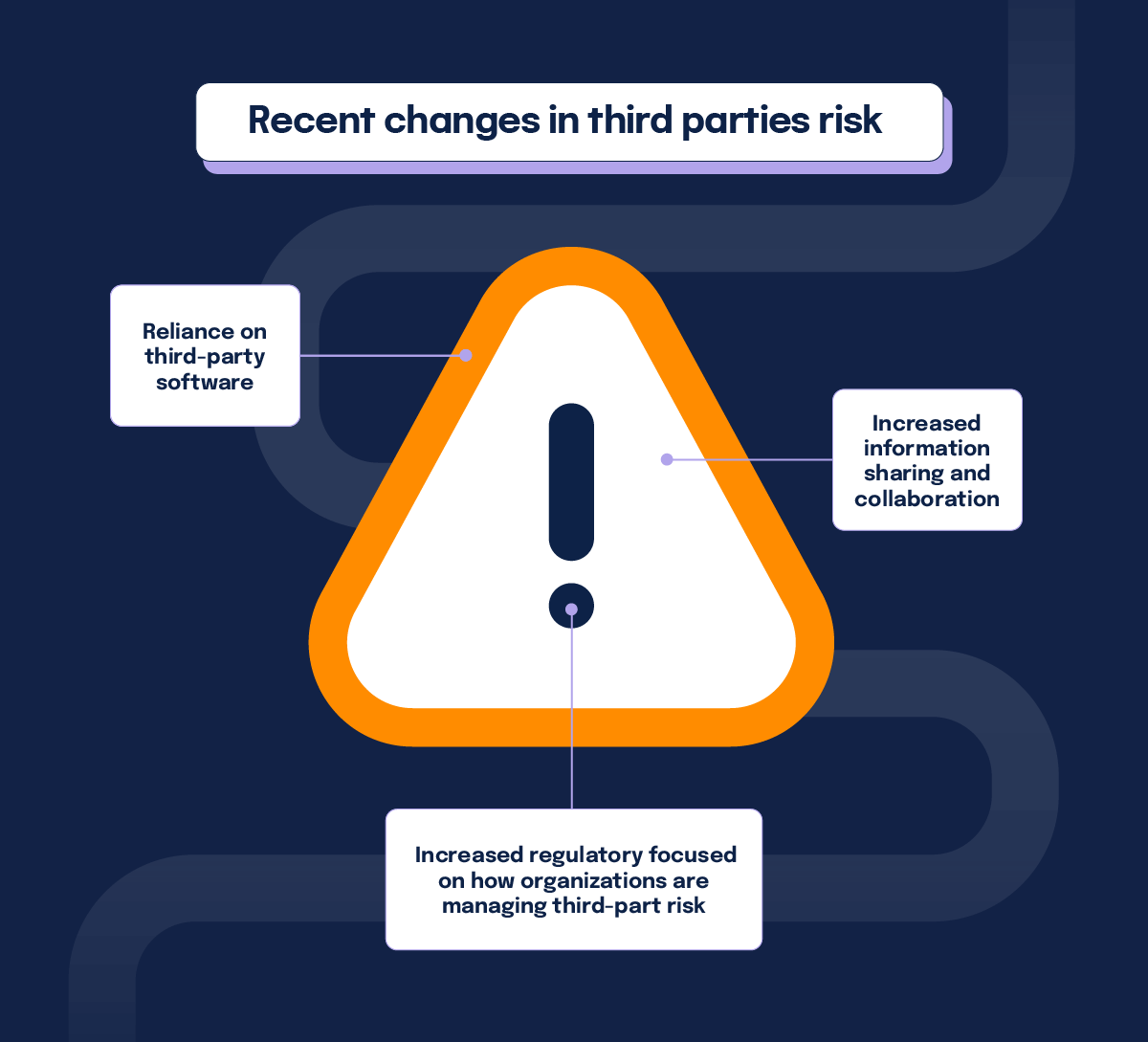
Many factors contribute to the growing and changing risks businesses face regarding their third-parties. Here are the top ones:
1. Organizations are increasingly relying upon software from third-parties to run their business
An example would be that many businesses use payroll, customer relationship management, and email marketing solutions that are readily available and don’t require engineering anything in-house. However, this also means that organizations are putting more of their data into third-party applications, creating more risk.
2. Organizations have become more reliant on a network of collaborators
There are many collaborators that organizations may rely upon to get things done such as partners, suppliers, vendors, and contractors. Increased information sharing and collaboration have enlarged the attack surface for cyber intruders.
3. Regulators have become more focused on how companies are managing outsourcing and third-party risk
This includes the fines for violations that have, in some cases, reached hundreds of millions of dollars. Fines often come with negative publicity and damage a brand’s reputation, which can be more difficult to recover from than monetary loss.
As a result, boards are more concerned than ever about how their organizations are handling third-party risk and consider third-party risk a top strategic risk.
Common types of third-party risks
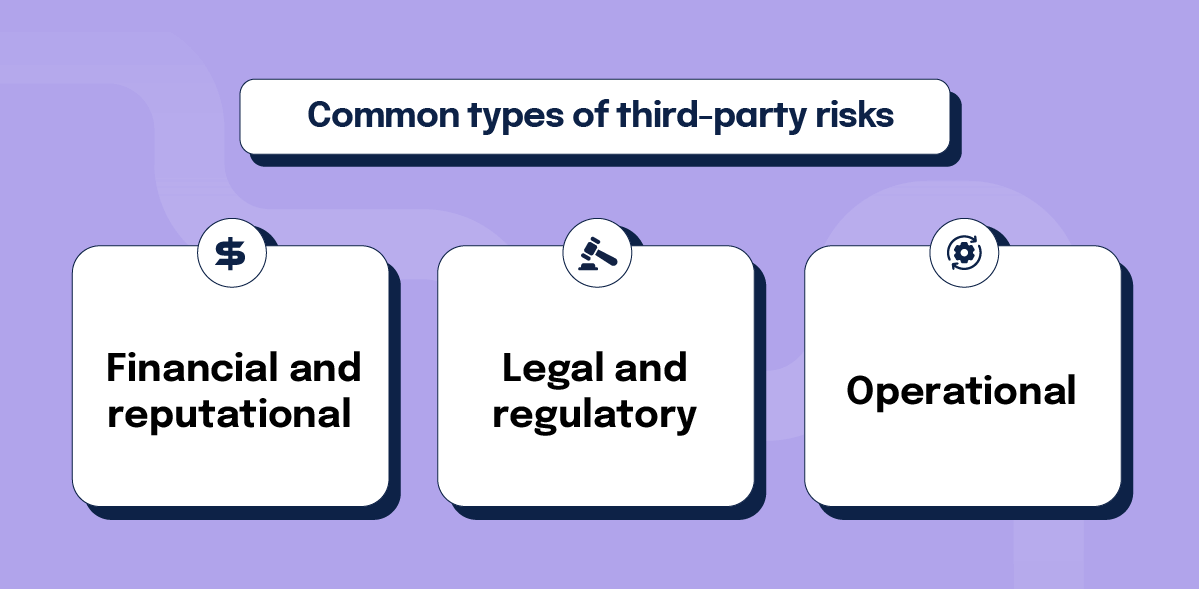
The risks faced when working with third parties are much the same as other business risks and they usually fall into three categories:
- Financial and reputational: When an organization must pay fees or fines, the potential loss of income is also a result of the reputational hit that sometimes follows a data breach.
- Legal and regulatory: Third parties can negatively impact your organization’s compliance with legislation. For example, if you work with a supplier who violates labor, environmental, data security, or other laws, you can also be liable.
- Operational: A third party could disrupt your operations in any number of ways, whether it’s not providing the service you are paying for or through a data breach or outage that affects your data.
In some cases, these risks can overlap. A data breach, for example, is a regulatory threat, but can also disrupt your operations if you rely on their product or service to carry out a business process. A third-party data breach can also cause financial and reputational damage to your company.
Is my business liable for third-party breaches?
Businesses both inside and outside the United States might be liable for third-party providers’ actions. For instance, the EU’s GDPR imposes formidable duties of care for the data a company has in its possession, and they hold the company responsible for third parties working with that data on the company’s behalf. Thus, if your organization works with EU residents, it must demonstrate competency in third-party risk management.
While falling out of compliance with data privacy laws like GDPR is an important reason for creating a third-party risk management program, the really important reason is keeping customers’ data safe. When these information breaches happen due to a vendor’s security weakness, you lose something much more valuable—customers’ trust, and with it, their money and future business.
Why do you need a third-party risk management framework?
Although it is widespread for organizations to use an ad-hoc approach to third-party risk management, the data shows this approach isn’t working.
In fact, 60% of respondents in the 2025 IT Benchmark Report have experienced (or are expecting) an audit finding that they cannot promptly resolve related to third-party risk management. This number is staggering – showing just how difficult it is for organizations to have the bandwidth, budget, and insight to manage third-parties.
Successful organizations realize better risk management results from an integration of risk governance, cybersecurity, and compliance efforts, with teams working in unison around a “risk first” mindset.
How organizations are addressing third-party risk today
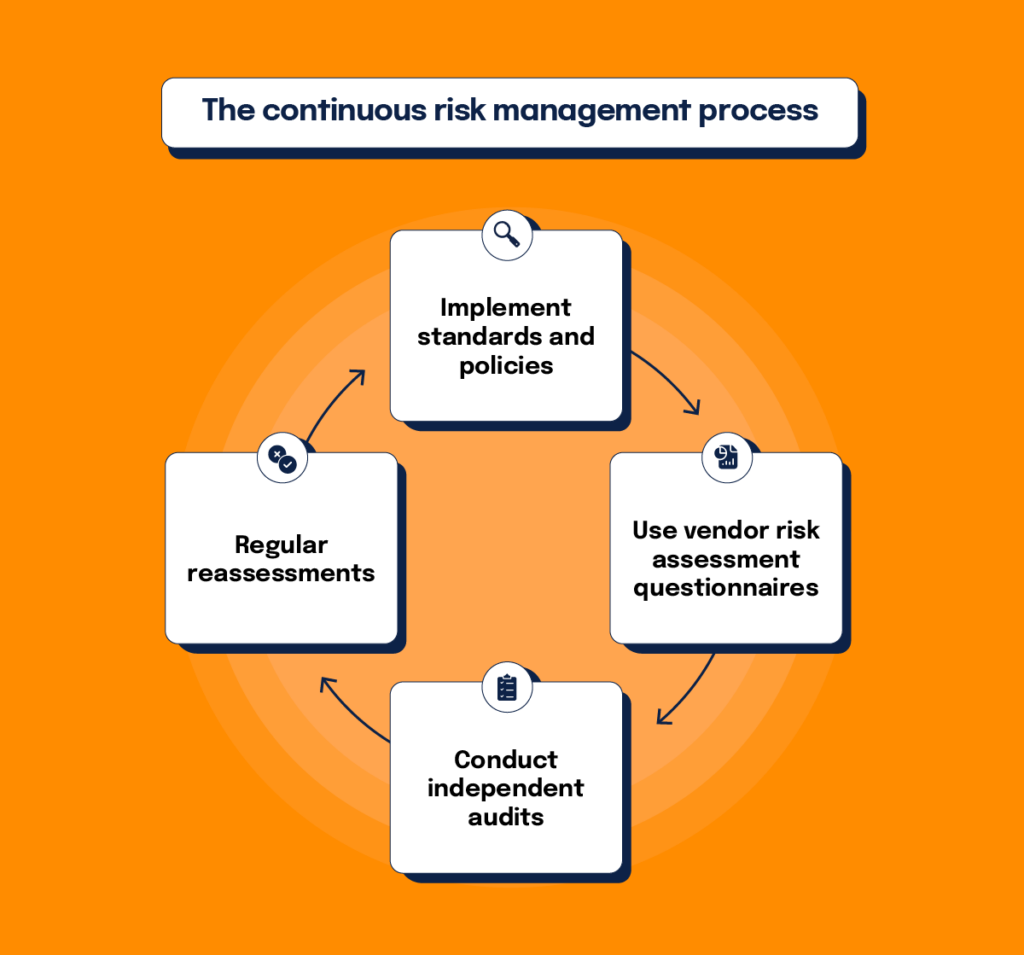
Forward-thinking businesses do not evaluate third parties on a case-by-case basis. Instead, they put standards, policies, and systems in place to mitigate risk continuously proactively.
At this time, many organizations have deployed vendor risk assessment questionnaires to understand what risk management processes a third-party has in place, how they approach data security, and whether they can reasonably trust them to handle consumer data properly. However, this questionnaire shouldn’t be the only part of your third-party risk assessment.
The downside of these risk assessment questionnaires is that they only offer a point-in-time snapshot of your third-parties’ data security measures. Additionally, they’re a self-assessment, so you can’t independently verify a vendor’s answers.
To increase due diligence on your vendors, you may consider conducting your own audits, at least on key vendors. For instance, Microsoft has created its own Supplier Privacy & Assurance Standards to instruct its suppliers on data privacy and protection and ensure their compliance with those requirements.
Meanwhile, Adobe has a similarly structured program for its vendors. Adobe utilizes a vendor risk assessment program called Guardrails, which includes a set of requirements to which third-party vendors that collect, store, transmit, process, or dispose of sensitive data must adhere to. The Guardrails Risk Assessment program evaluates each vendor’s compliance with Adobe’s Vendor Information Security Standard, providing a risk-based review of the vendor’s security practices and enabling Adobe managers to make fact-based decisions concerning whether or not to enter into a relationship with that vendor.
MX, a software company that creates software for financial and fintech companies, conducts a risk assessment when initially starting a relationship with a vendor and on an annual basis to identify any issues that need to be remediated. As part of this risk assessment, the services provided by a third party are evaluated to determine the types of data that will be processed by the third party. The level of sensitivity of data determines the depth of the security review performed on the third party. Findings from each security review are discussed with and provided to the third party to remediate within an agreed-upon timeframe.
Related: The Business Case for Compliance, Even Now, Cybersecurity Best Practices.
Key elements of third-party risk management: the most effective ways to address third-party risk
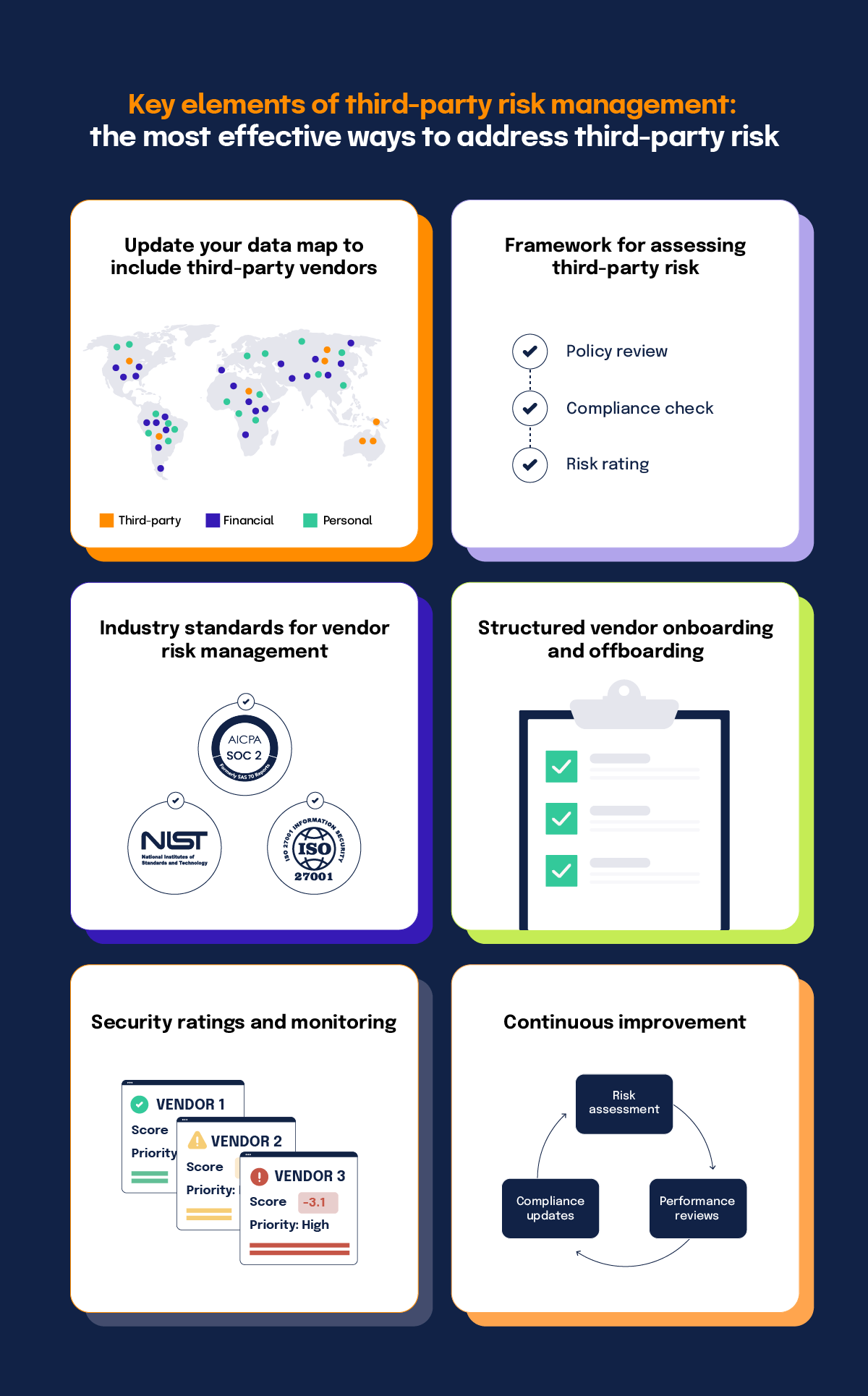
When it comes to third-party risk management, there isn’t a one-size-fits-all approach. What makes sense for a large organization like Microsoft or Adobe almost certainly will not make sense for a three-year-old consumer-focused startup. However, here is a set of foundational items businesses of all types should consider:
1. Update your data map to include third-parties
The foundation for your third-party risk management program should include all consumer data your vendors have in a data map. A clear view of what data your vendors can access and how they are using it will help you put the right agreements in place and ask for the right compliance information from each of your vendors.
2. Have a framework and defined process for assessing third-party risk
Instead of assessing vendors on a case-by-case basis, your organization should have a third-party risk assessment framework in place before you even begin researching vendors and know exactly what you expect from potential third-party service providers.
As a general rule, the framework should generally be a high-level guide that details exactly how vendor risk management will be handled. This guide will help to provide steps for senior management in different lines of business to follow. Generally, the guide will outline day-to-day vendor risk management responsibilities in explicit detail, so that no step is overlooked.
A good place to start with this is reviewing any past application vulnerability assessments you’ve done, and seeing where those vendors had issues. You should also consult your company’s compliance policies and requirements to make sure your vendor is able to meet the standards your company has set for itself.
3. Base your third-party risk management program on industry standards
You can use vendor assessment programs from established enterprises (e.g., Microsoft, Adobe) as a starting point for your own vendor assessment framework. For instance, Adobe’s Vendor Assessment Program whitepaper lays out the types of security controls they assess for every third-party vendor that stores or processes company data. Below is a sample of the controls and some of these may make sense for your organization as well:
- Assertion of security practices: review of security certification attestation reports (SOC 2® Type II, ISO 27001) and internal security policies and standards
- User authentication: password policies, access control processes, and support of multi-factor authentication
- Logging and audit: details about system/app/network logs and retention periods
- Data center security: physical security controls in locations where company data is hosted
- Vulnerability and patch management: cadence of external/internal vulnerability assessments and pen tests as well as timelines for vulnerability remediations
- End-point protection: policies that cover end-point security
- Data encryption: encryption of data in rest and transit
In developing a vendor assessment framework, you may also find it helpful to look at some of the industry-standard cybersecurity risk management methodologies such as:
- SOC 2®
- ISO 27001
- Consensus Assessment Initiative Questionnaire
- NIST Cybersecurity Risk Management Framework (CSF)
- NIST 800-171
- VSA Questionnaire
- CIS Critical Security Controls
You can extract thousands of potential questions from these frameworks and adapt them for your own vendor assessment questionnaire.
Are you looking for comprehensive solutions surrounding the integration of compliance operations for your company? Hyperproof is a great place to start with third-party risk management and more.
4. Develop structured vendor onboarding and offboarding processes
Just as you have an onboarding process for new employees to make them aware of your corporate policies, it is important to develop a standardized onboarding process for your vendors. In your onboarding process, you’ll want to make sure vendors understand your information security standards/policies and have agreed to adhere to those standards.
For instance, if a vendor plans to have individuals conduct work on your behalf on their own devices, you’ll need to communicate your “bring-your-own-device” restrictions on what data the vendor can and cannot store on their devices.
5. Consider security ratings
Security ratings allow you to monitor your vendors and their vendors’ security ratings in real time. If your organization uses many vendors, this will allow your organization to streamline the vendor assessment process, monitor for changes in security posture, and request remediation of key issues at high-risk vendors. Businesses such as BitSight evaluate vendors for you so you can ensure you’re partnering with secure, high-quality organizations.
6. Don’t wait until your framework is perfect to start using it
Implementing something is better than nothing when it comes to risk management and compliance. It’s common for compliance and data security programs to need updates, tweaks, additions, and adjustments as you find processes that aren’t working, encounter new risks or become subject to new privacy requirements. So don’t wait until your vendor security framework is perfect – deploy it now and commit to consistent review and improvement.
7. Ensure you have a thoughtful selection process in place
When it’s time to make a selection, you should have a vendor vetting process in place. Having one of these processes is another critical step in ensuring that you make the right selection of a third-party vendor for your organization. That said, making the correct perceived selection should only be a starting process, rather than the end-all-be-all. During this vetting process, you may want to consider points such as comparing certain vendors to relevant competitors, issuing requests for proposals (RFP), and completing due diligence tasks such as completing a risk assessment as dictated by your policies.
8. Establish and put contractual standards in place
While it is okay, to begin with, a general template for the contracts you put in place with a third-party vendor, it should also be understood that no two contracts will be exactly alike. Make sure to communicate to ensure both parties have an understanding of responsibilities before a contract begins. The contract should include steps such as how things need to be negotiated and the approval process for how contract changes should be made, in addition to how they will be stored and approved.
9. Once a plan is in place, keep up with it
Due diligence is just as necessary as the policies put in place surrounding third-party compliance risk management. Keep up with your due diligence on an ongoing, (sometimes) annual basis. Your success with your vendor will be in direct proportion to your ability to continue understanding any changes your vendor may have gone through.
There are several steps that you may want to take in your due diligence process. First, you will want to review the vendor’s financial statements when they are released. You’ll also want to continue to request and evaluate your vendor’s SOC reports. Overall, several annual assessments should be conducted and completed, including risk, performance, and information security reviews.
10. Define your internal vendor risk audit process
An internal audit process will be an essential component of your vendor risk assessment program. A final internal audit will be a wonderful last-review process for your vendor before an examiner arrives on-site. It’s a much better idea to catch any mistakes present in your process before your examiner does. Overall, it will also help to mitigate any general risks.
The future of third-party risk management
In the next few years, we can expect more organizations to take a Microsoft-type approach and develop their own standards and audit programs for their suppliers and vendors. These assessments require a significant amount of work, but they offer better security and mitigate risk more efficiently than a questionnaire or informal discussion.
If you’re selling a software application or processing sensitive client data, you need to be prepared to respond to these types of assessments. You may need to complete a third-party questionnaire, produce evidence of compliance like a SOC 2® or an ISO 27001 certification, or complete a more in-depth assessment of your data security and privacy measures to meet your client’s requirements.
As demand and urgency to manage third-party risk continues to grow, organizations will need to find the right tools to help them manage the complexity and keep costs in check.
Related: 3 Governance, Risk, and Compliance Trends to Watch
How Hyperproof can help third-party risk management
Hyperproof is a compliance operations application that provides a central, secure place for an organization to maintain compliance against well-accepted cybersecurity frameworks such as NIST Cybersecurity Framework and ISO 27001. Hyperproof enables you to align your internal controls to the requirements of a cybersecurity framework and monitor the operating effectiveness of controls continuously – so you can be confident that your controls are working as intended to mitigate the specific risks facing your assets, resources, and environment.
Additionally, Hyperproof offers a third-party Vendor Management module that allows you to easily assess your vendors’ security and compliance posture and manage third-party risk. Within the third-party Vendor Management module, you can:
- Maintain a central database of all vendors, including contracts, vendor risk assessment questionnaires, and internal control activities to mitigate third-party risk.
- Assess each vendor’s security and compliance posture through customizable questionnaires and assign risk tiers to vendors
- Manage all remediation activities related to your vendors and collaborate with internal and external stakeholders
- Leverage answers to security questionnaires and other work you’ve done around vetting vendors as proof of compliance for IT security audits and assessments
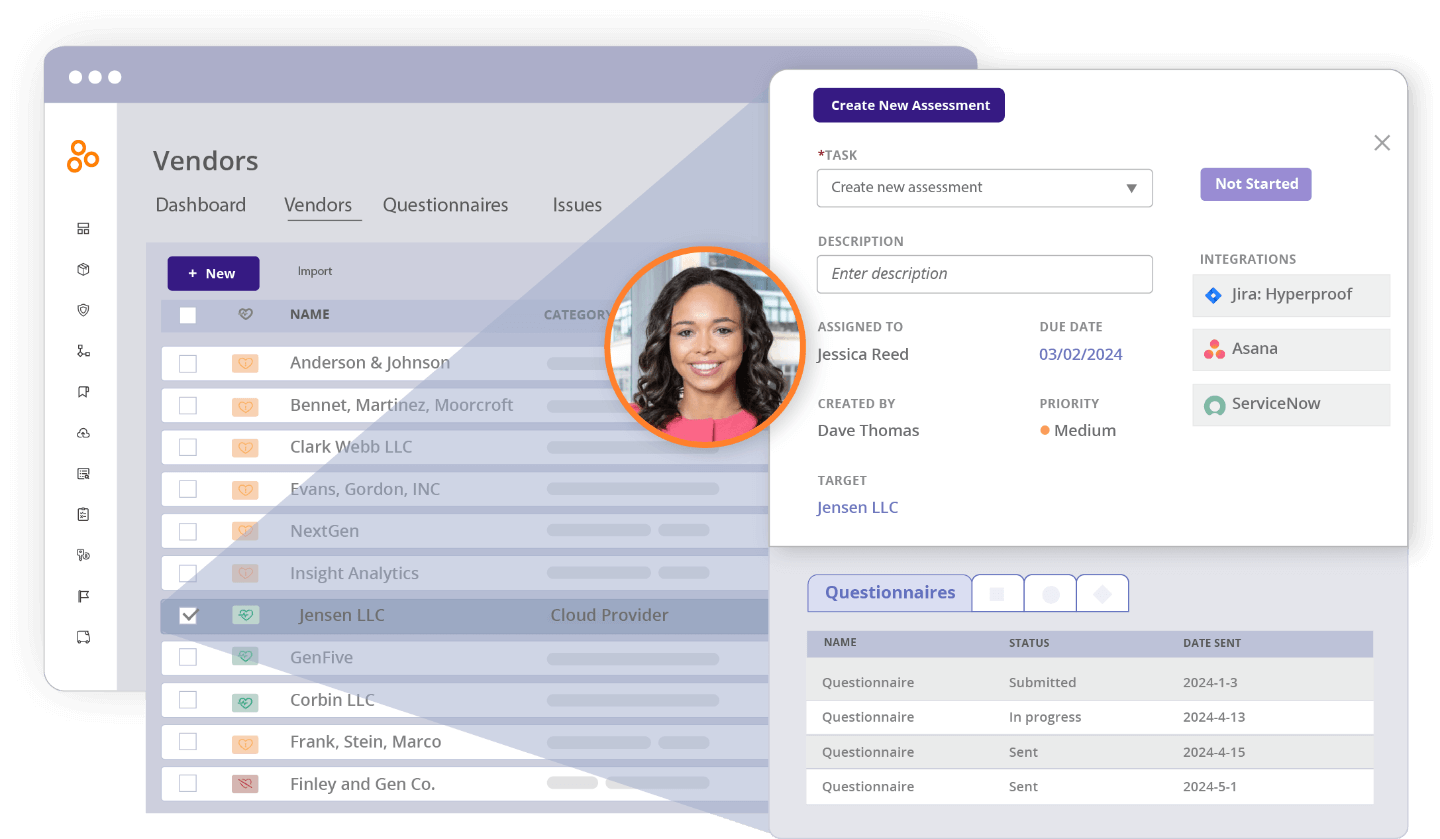
Find out more about maintaining a central source of truth of your third-party vendors and assessing their risk profile and potential impact with automated assessments. We’d love to talk.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












