California Data Breach Notification Law: Understanding the New 30-day Deadline
Why does the California Data Breach Notification Law matter now?
California’s breach‑notification law is changing to include a concrete 30-day deadline. A 15‑day deadline for a sample notice to the Attorney General kicks in when more than 500 residents are affected. The amendment becomes effective on January 1, 2026, giving businesses a clear timeline to update policies and test processes.
A timeline of the California Data Breach Notification Law
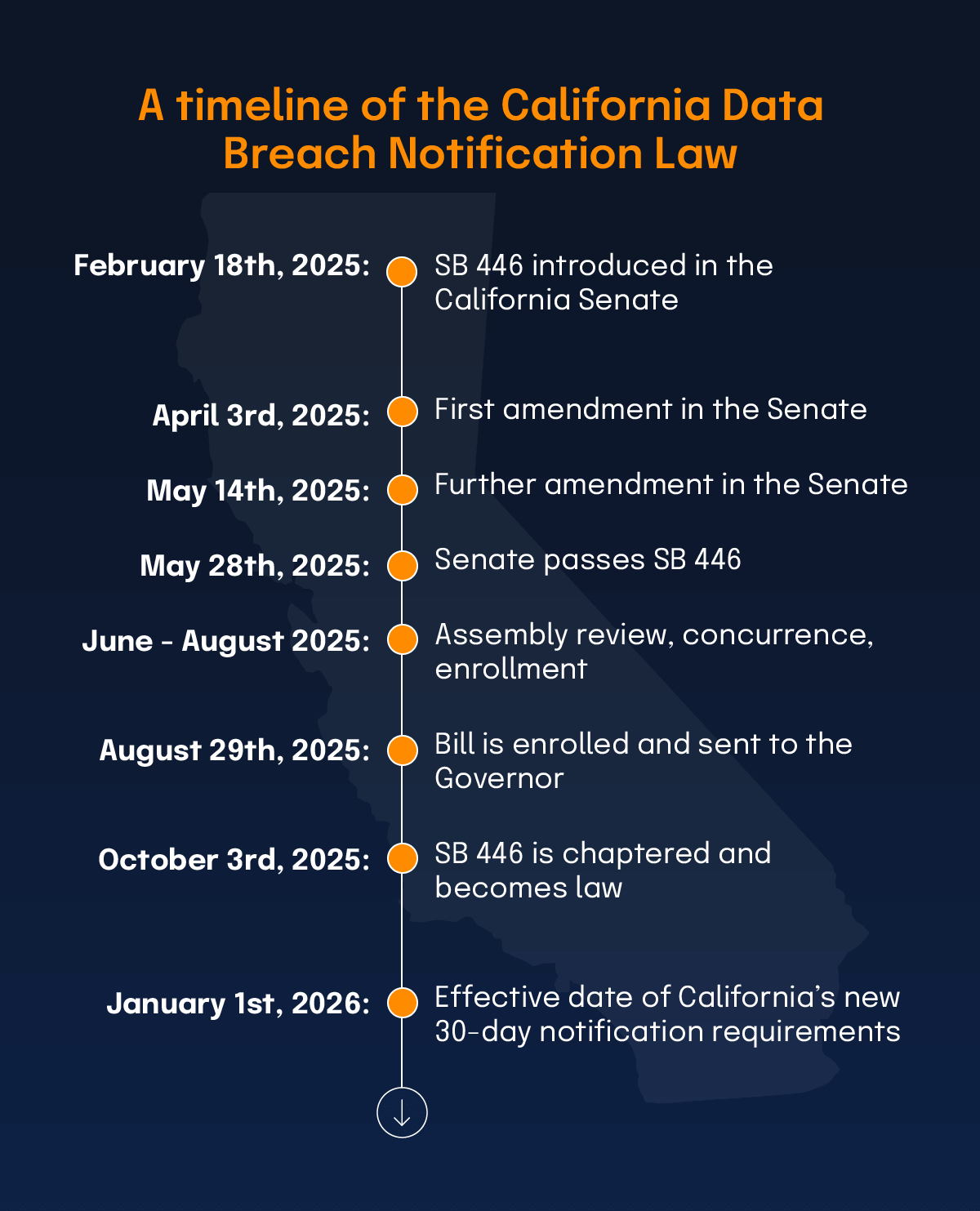
February 18th, 2025: SB 446 introduced in the California Senate
April 3rd, 2025: First amendment in the Senate
May 14th, 2025: Further amendment in the Senate
May 28th, 2025: Senate passes SB 446
June – August 2025: Assembly review, concurrence, enrollment
August 29th, 2025: Bill is enrolled and sent to the Governor
October 3rd, 2025: SB 446 is chaptered and becomes law
January 1st, 2026: Effective date of California’s new 30-day notification requirements
What does the 30‑day deadline require?
The statute now says any person or business that conducts business in California and that owns or licenses computerized personal information must disclose a breach within 30 calendar days of discovery or notification. A law enforcement delay is still allowed, but the organization must document the request and act without unreasonable delay once clearance is granted. For breaches that affect over 500 residents, a single sample copy of the consumer notice must be submitted to the Attorney General within 15 calendar days of notifying the affected individuals.
Which organizations must comply?
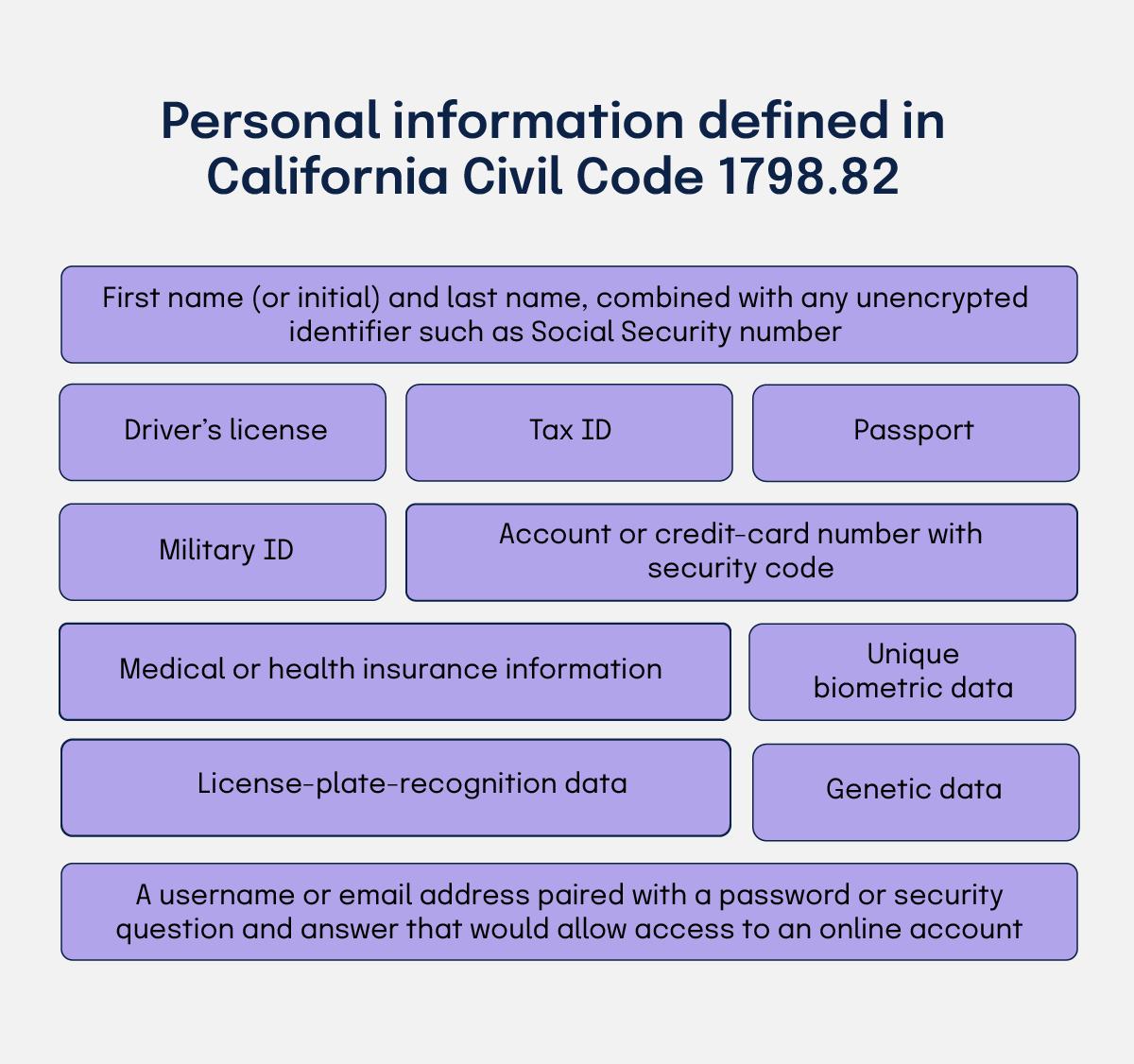
Any entity that collects, stores, or processes the personal information defined in California Civil Code § 1798.82 is covered. The definition includes:
Good‑faith acquisition by an employee or agent for a legitimate purpose is excluded, provided the information is not later used or disclosed without authorization.
What must the notice contain?
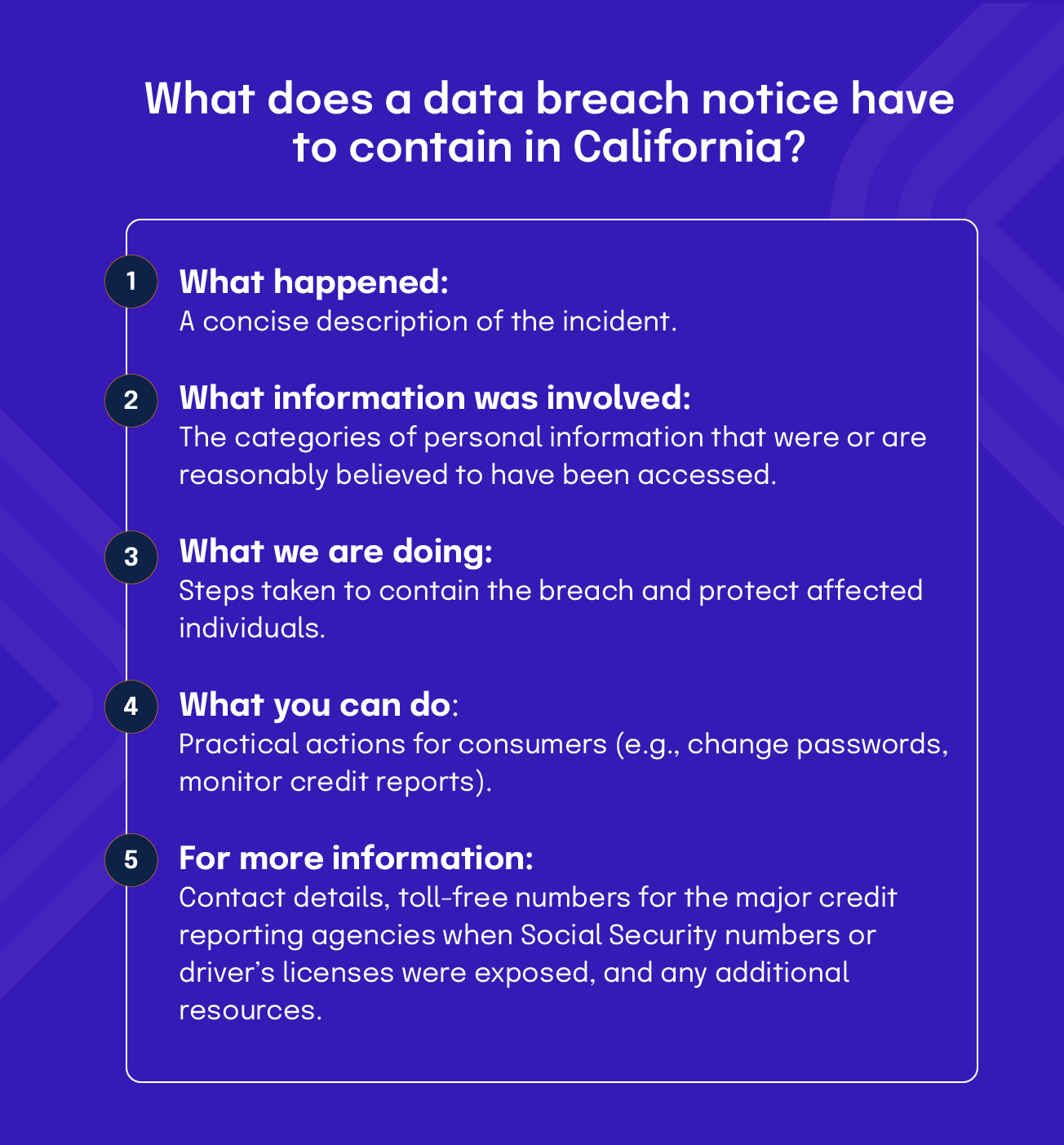
SB 446 keeps the existing content and formatting rules. The notice must be titled “Notice of Data Breach” and organized under five mandatory headings:
- What happened: A concise description of the incident.
- What information was involved: The categories of personal information that were or are reasonably believed to have been accessed.
- What we are doing: Steps taken to contain the breach and protect affected individuals.
- What you can do: Practical actions for consumers (e.g., change passwords, monitor credit reports).
- For more information: Contact details, toll‑free numbers for the major credit reporting agencies when Social Security numbers or driver’s licenses were exposed, and any additional resources.
What are the formatting rules for notice of data breach?
A minimum 10‑point type, prominent title and headings, plain‑language style. When the organization itself is the source of the breach and the compromised data includes Social Security numbers, driver’s licenses, or similarly sensitive identifiers, the law obligates the organization to provide at least 12 months of free identity‑theft mitigation services to each affected individual.
Starter template (replace brackets with case‑specific data and customize for your company):
[Company Logo] Date: [Month Day, Year]
NOTICE OF DATA BREACH
What happened?
On [Month Day, Year] we discovered that an unauthorized individual gained access to our network and obtained personal information described below.
What information was involved?
The compromised data includes:
- First name, last name, and Social Security number
- Driver’s license number
- Credit card number and expiration date
What we are doing
We have:
- Isolated the affected systems
- Engaged a forensic firm to investigate the breach
- Implemented additional encryption and multi‑factor authentication
- Notified law enforcement, which is assisting with the investigation
What you can do
We recommend that you:
- Review your credit reports for any unfamiliar activity
- Place a fraud alert with the major credit bureaus
- Change passwords for any online accounts that use the same credentials
- Consider enrolling in a credit‑monitoring service (we are providing a complimentary 12‑month subscription)
For more information
If you have questions, please call our dedicated hotline at 1‑800-867-5309 or visit www.example.com/breach‑notice.
If your Social Security number or driver’s license was exposed, you may also contact:
- Experian: 1‑888‑397‑3742
- TransUnion: 1‑800‑680‑7289
- Equifax: 1‑866‑640‑2277
How can organizations build a detection‑to‑notice pipeline that meets the deadline?
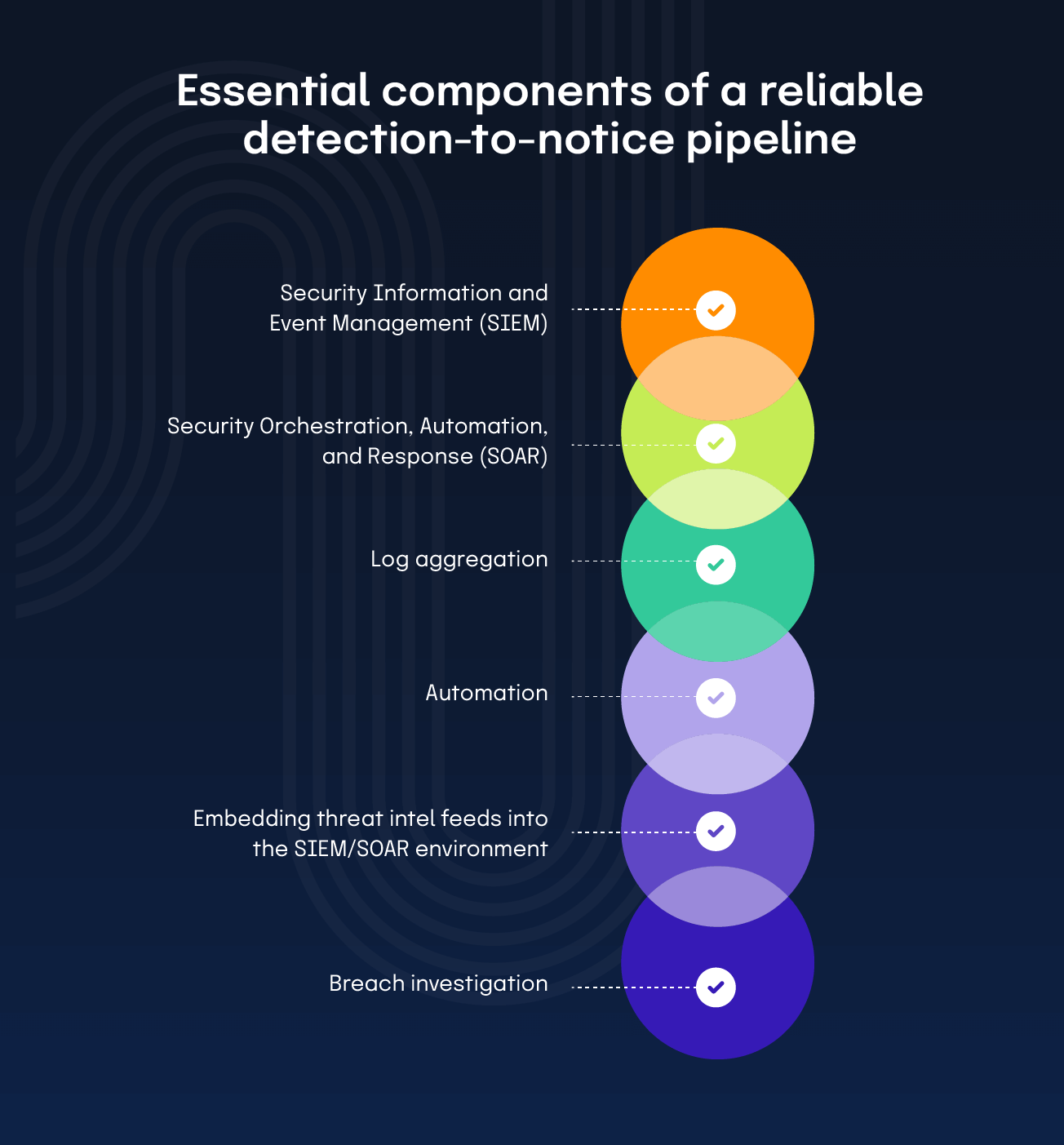
A reliable pipeline starts with early detection, moves through rapid analysis, and ends with a pre‑approved notice that can be released quickly. Essential components:
Security Information and Event Management (SIEM)
SIEM centralizes logs from firewalls, servers, endpoints, and cloud services for real‑time correlation of suspicious events.
Security Orchestration, Automation, and Response (SOAR)
SOAR automates routine triage steps, like generating alerts, creating tickets, and initiating containment actions.
Log aggregation
Aggregating network traffic logs, authentication logs, endpoint telemetry, and external threat intelligence feeds into a limited set of log servers lets analysts spot patterns that signal unauthorized data access, lateral movement, or exfiltration. The faster the scope is understood, the sooner the notice can be drafted.
Automation
Automation further accelerates the process. Alerts should route instantly to the Security Operations Center and the incident response team. Integration with a ticketing platform (ServiceNow, Jira, etc.) guarantees that each alert spawns a traceable incident record. Pre‑populated notice drafts that pull data from the ticket – discovery date, data types, affected systems – dramatically shorten the drafting phase.
Embedding threat-intel feeds into the SIEM/SOAR environment
Embedding threat‑intel feeds into the SIEM/SOAR environment enriches alerts with context about known adversary tactics, techniques, and procedures. Analysts can prioritize incidents that are more likely to involve personal information, focusing resources where the deadline matters most.
Breach investigation
Every breach investigation must produce a concise factual summary that includes the discovery date, the scope of compromised data, actions taken to contain and remediate, and an assessment of whether the breach qualifies as a “personal information” breach under § 1798.82. Having this documentation ready accelerates the creation of both the consumer notice and the Attorney General sample notice.
How does the new timeline align with existing incident response frameworks?
Many organizations already follow the NIST SP 800‑61r3 lifecycle: Preparation, Detection and Analysis, Containment, Eradication, Recovery, and Post‑Incident Activity. SB 446 does not require abandoning that model; it simply adds a hard deadline to the Detection and Analysis and Notification phases.
A practical adjusted timeline:
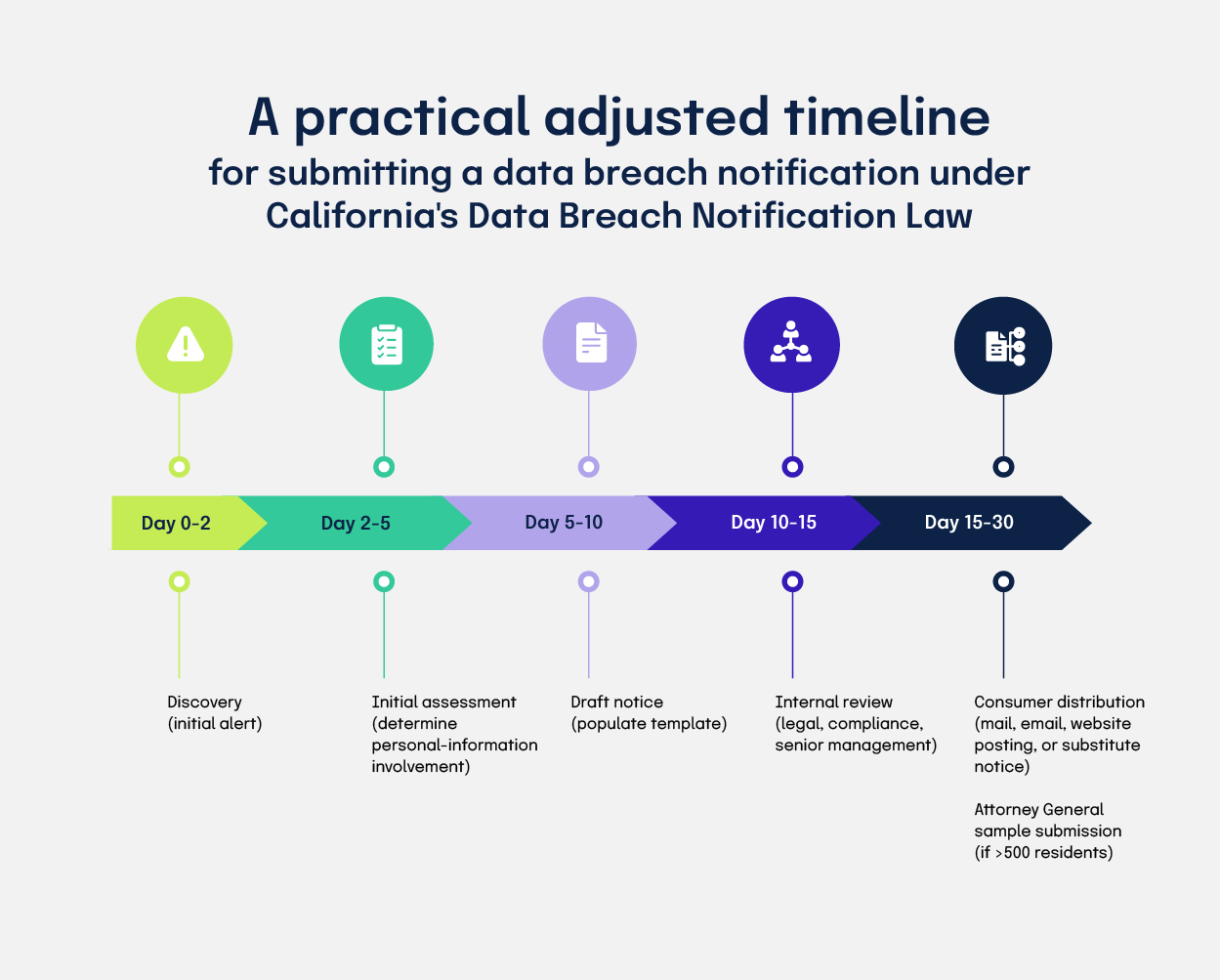
Discovery (initial alert): Day 0‑2
Initial assessment (determine personal‑information involvement): Day 2‑5
Draft notice (populate template): Day 5‑10
Internal review (legal, compliance, senior management): Day 10‑15
Consumer distribution (mail, email, website posting, or substitute notice): Day 15‑30
Attorney General sample submission (if > 500 residents): Day 15‑30
If a law‑enforcement agency requests a delay, the organization must document the request and the anticipated new delivery date, then act without unreasonable delay once clearance is granted.
How does California’s deadline compare with other states?
California joins a small group of states that impose a strict 30‑day deadline. Maine and Washington have similar requirements. Many states still rely on “most expedient time possible” language, which creates uncertainty for multi‑state operators. Thresholds for notifying the state differ:
California: 500 residents, 15‑day Attorney General sample deadline
Illinois: 500 residents, notice to the Attorney General within 45 days
Texas: 250 residents, Attorney General notice within 30 days
These variations highlight why organizations with a national footprint should centralize breach notification logic while retaining the ability to apply state‑specific thresholds and timelines.
What options do smaller organizations have to meet the deadline?
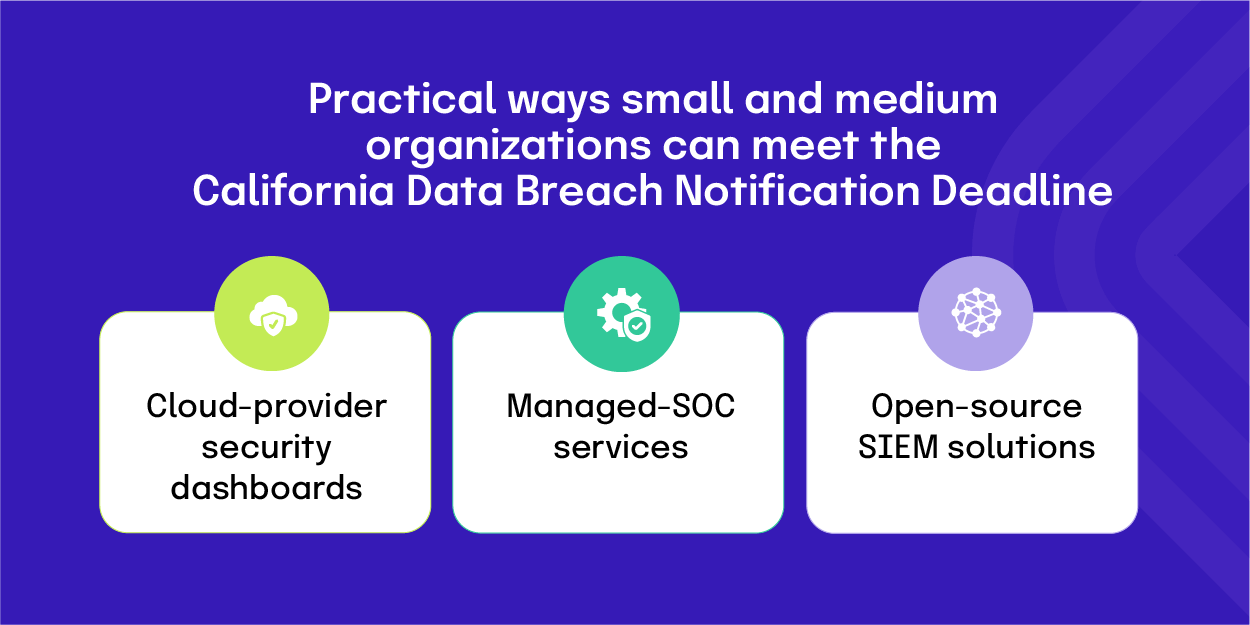
Small and medium‑sized enterprises often lack dedicated security teams, yet the statutory obligations apply equally. Practical ways to satisfy the deadline without extensive resources include:
Cloud‑provider security dashboards
Major providers (AWS, Azure, Google Cloud) aggregate logs and generate alerts out of the box.
Managed‑SOC services
Third‑party providers can triage alerts, conduct initial investigations, and help draft the required notice.
Open‑source SIEM solutions
The Elastic Stack or Apache Kafka can provide basic log collection and correlation at modest cost.
Even with limited budgets, the essential element is a documented process that can be executed within 30 days.
What immediate steps should organizations take before January 1, 2026?

Update incident‑response playbooks
Insert a “30‑Day Notification” milestone and assign ownership for drafting the consumer notice.
Create a pre‑approved notice template
Use the sample structure above, brand it with your logo, and store it in a secure, easily accessible location.
Map data flows
Identify every system that stores or processes the personal information categories listed in the statute. Knowing where the data lives speeds up scope determination.
Establish a law‑enforcement liaison process
Designate a point of contact who can receive and document any delay requests.
Conduct a tabletop exercise
Simulate a breach, track the timeline from discovery to consumer notice, and verify that the 30‑day deadline is met. The NIST SP 800‑61r3 guidance recommends regular testing of incident‑response capabilities.
Prepare the Attorney General submission
Build a redacted version of the notice that excludes any personally identifiable information. Store the file in a repository that can be quickly exported and emailed to the Attorney General’s portal.
Completing these actions now positions the organization to comply smoothly when the law takes effect.
TL;DR
- SB 446 creates a statutory 30‑day deadline for consumer breach notices and a 15‑day deadline for a sample notice to the Attorney General when more than 500 California residents are impacted.
- The deadline is part of the law, not merely an interpretation of existing civil‑code language, so all communications must reference the amendment.
- Notices must include the five mandatory headings, be written in plain language, use at least a 10‑point font, and, when the organization is the source of the breach, provide at least 12 months of free identity theft mitigation services.
- Building a detection‑to‑notice pipeline ensures the deadline can be met consistently: SIEM > SOAR > automated ticket > draft notice > internal review > consumer distribution > Attorney General sample submission.
- Document any law‑enforcement delay request and act without unreasonable delay once clearance is granted.
- Run tabletop exercises before the January 2026 effective date to verify that the 30‑day clock can be satisfied.
- Smaller firms can meet the requirement by leveraging cloud‑native logs, managed SOC services, or open source tooling, but must still maintain a documented, repeatable process.
- By revising incident response plans, preparing a compliant notice template, and rehearsing the end‑to‑end workflow today, organizations can confidently meet California’s new data breach notification deadline and avoid the regulatory penalties that accompany missed timelines.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?