CCPA Revisions: What You Need to Know
The California Privacy Protection Agency approved CCPA revisions that require automated decision-making controls, documented risk assessments, and annual cybersecurity audits on a phased schedule beginning on January 1, 2027. These rules create a data governance regime that expands privacy teams’ scope, demands cross-functional coordination, and raises documentation expectations for audits and assessments. The deadlines vary by obligation, but the direction is clear. You will need clear ADMT notices and opt-outs, risk-benefit analyses for defined high-risk processing, and independent cybersecurity audits that cover 18 program components, with certifications due to the CPPA.
Key points for business leaders
What changed in the July 2025 CCPA revisions?
The California Privacy Protection Agency approved a package centered on automated decision-making technology (ADMT), pre-processing risk assessments, and annual cybersecurity audits. The changes increase consumer protections and organizational accountability as AI and automation expand across operations.
In plain terms, businesses must tell Californians when ADMT is used for significant decisions, give opt-out choices, and explain logic and effects. They must conduct and maintain risk assessments for processing that presents significant risk. They must also complete annual cybersecurity audits when thresholds are met and submit certifications to the CPPA.
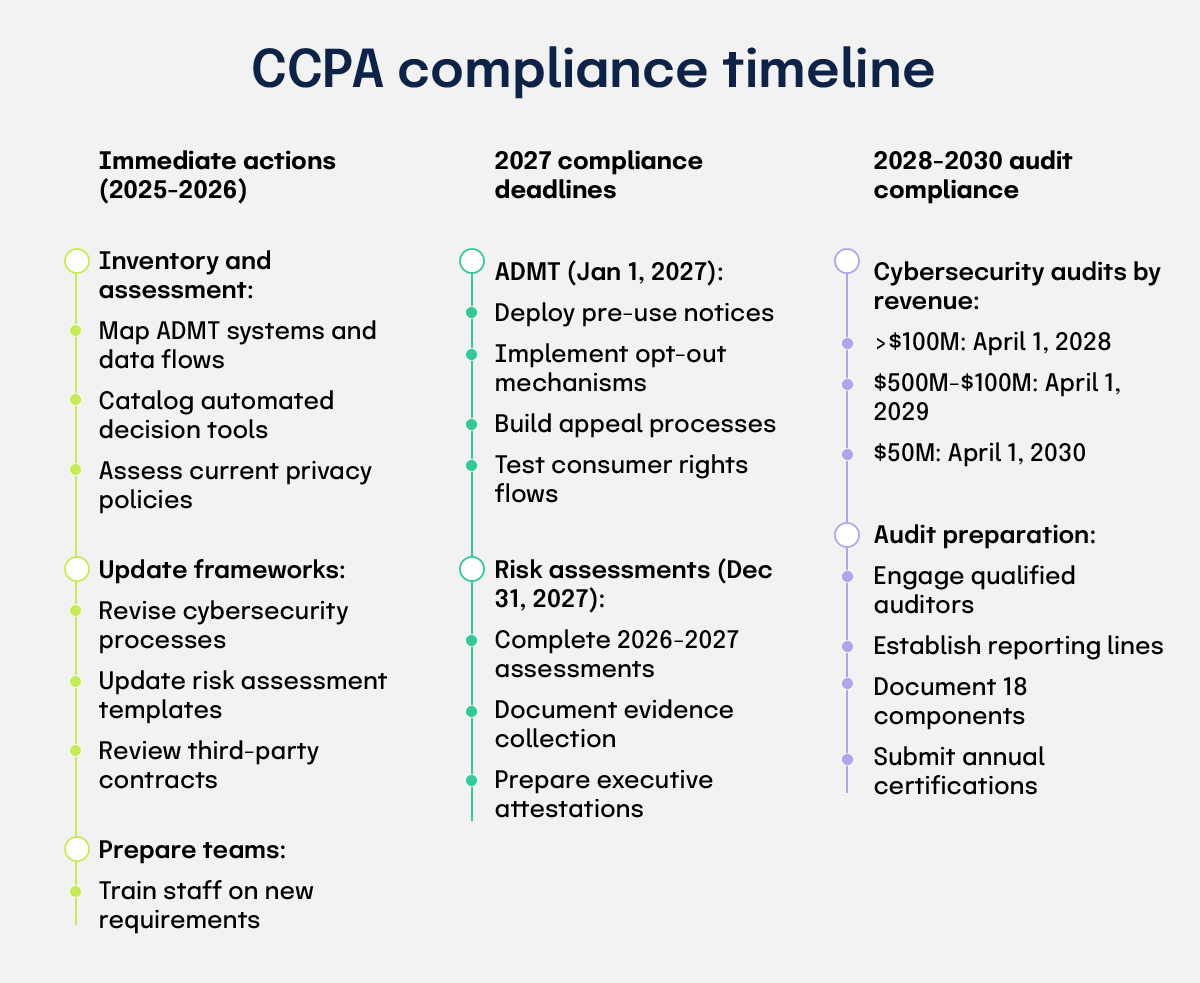
Compliance begins in 2027 and rolls through 2030, with earlier dates for larger businesses. Your project plans should reflect the interlocking nature of these requirements.
These CCPA revisions add ADMT controls, risk assessments, and cybersecurity audits with phased deadlines that start in 2027.
What is ADMT under the new rules?
ADMT is “any technology that processes personal information and uses computation to replace human decision making or substantially replace human decision making.” Replacing humans is the focus, not tools that simply assist. Human involvement must include interpreting the output, analyzing it with other relevant information, and having the authority to change the decision.
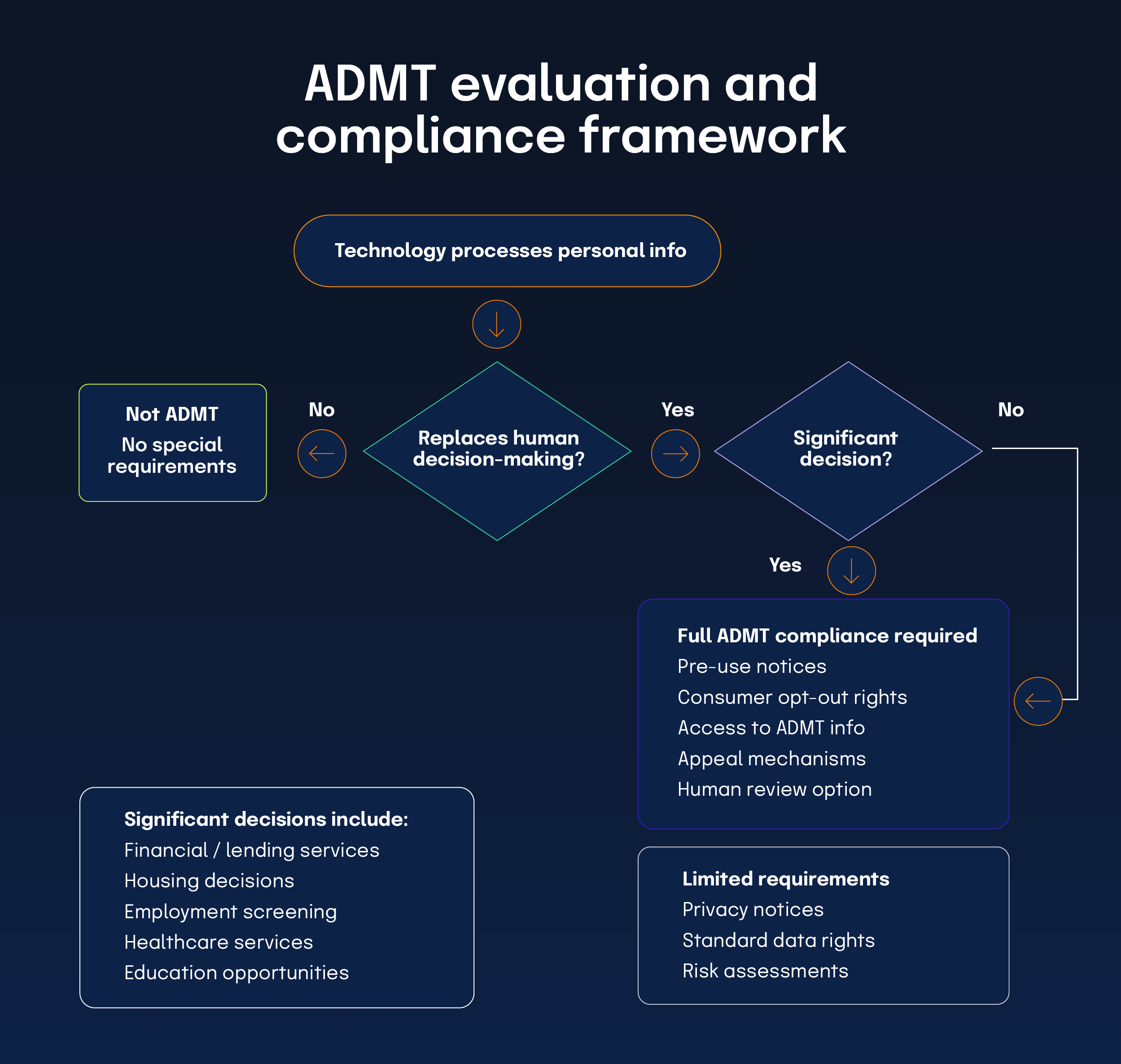
Which ADMT decisions and significant, and what rights apply?
Significant decisions include outcomes about financial or lending services, housing, education, employment or independent contracting opportunities or compensation, and healthcare services. When using ADMT for significant decisions, businesses must provide clear notices about purposes, logic, significance, potential consequences, and consumer rights, and must offer at least two methods to opt out.
What notices and disclosures are required?
Provide a pre-use notice in plain language that explains what the ADMT does and how consumers can opt out or access information. Present notices at or before collection, in the manner you primarily interact with the consumer. If you offer an appeal with qualified human review and authority to overturn decisions, that may affect the opt-out scope.
ADMT under the CCPA focuses on decisions that replace human judgment and requires clear notice, opt-out, and human-review pathways.
How do the timelines and thresholds work?
Plan toward three significant dates:
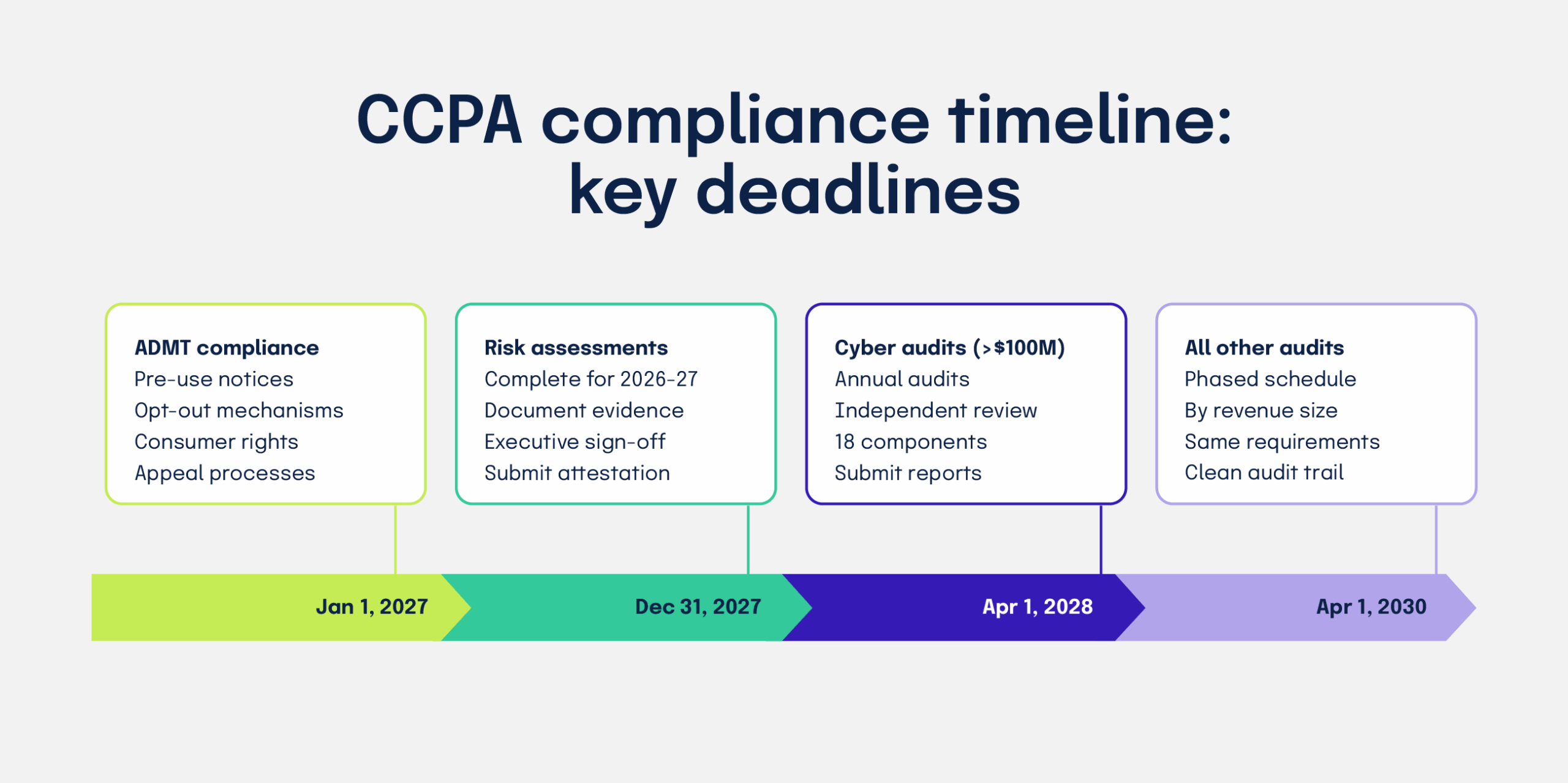
The ADMT rules apply first. If your business used ADMT before January 1, 2027, you must be fully compliant by that date, including pre-use notices and available opt-outs where required.
Complete risk assessments covering 2026-2027 by December 31, 2027, then submit an executive attestation by April 1, 2028. Continue reviewing every three years and update within 45 days of any material processing change. Retain records while processing continues, or for five years after the assessment, whichever is longer.
For cybersecurity audits, submit the first audit certification by:
Set program milestones backward from January 2027, December 2027, and April 2028-2030 to reduce deadline stress.
When are risk assessments required, and what must they include?
Risk assessments are required before initiating processing that presents significant risk to consumer privacy or security, and they must be updated over time.
What triggers a mandatory assessment?
Triggers include:
Most organizations share personal information with third parties, so many will be in scope.
What is the required content?
Each risk assessment must describe processing purposes and benefits in specific terms, identify categories of personal and sensitive personal information, outline operational elements like ADMT logic and expected retention, evaluate negative impacts on privacy, and describe safeguards. Vague phrases like “to improve services” or “for security purposes” are not sufficient.
How often must risk assessments be reviewed?
Review and update at least once every three years. If processing changes in a material way, update as soon as possible, and no later than 45 calendar days. Retain assessments for the life of the processing, or five years after completion, whichever is later.
Treat risk assessments as a living record that proves benefits, mitigations, and timely updates for high-risk processing.
Who must complete cybersecurity audits and what do they cover?
Annual cybersecurity audits apply when your processing presents a significant risk to consumer security, based on revenue and volume thresholds, and the audit must address 18 defined program components.
Which businesses fall in scope?
You are in scope if you derive 50% or more of annual revenue from selling or sharing personal information, or if you had annual gross revenue over $25 million and processed the personal information of at least 250,000 consumers or the sensitive personal information of at least 50,000 consumers in the preceding year.
What are the cybersecurity audit standards?
Audits must be objective and independent. Internal auditors are allowed if they report to an executive who does not run the cybersecurity program, and if they have access to all relevant facts. The report must be evidence-based, signed by the highest-ranking auditor, and include gaps and justifications.
What must the audit cover?
The regulations list 18 components, including authentication, encryption, access controls, inventory and configuration, vulnerability management, log management, network defenses, anti-malware, segmentation, port and protocol control, threat awareness, education and training, secure development, third-party oversight, retention and disposal, incident response, and business continuity and disaster recovery.
Can prior audits be reused?
Yes. You can leverage audits prepared for another purpose, like NIST CSF 2.0, if they meet CCPA requirements on their own or with supplementation.
What deadlines apply?
Certifications must be submitted annually. Build an independent, evidence-based audit program that covers all 18 components and meets annual certification dates.
How do ADMT, risk assessments, and audits work together?
The rules are designed to reinforce one another. ADMT often triggers risk assessments, and high-risk processing drives audit obligations. A coordinated program will save time and reduce rework.
ADMT used for significant decisions is specifically called out as an activity that triggers assessment. Processing that presents a significant security risk similarly triggers cybersecurity audits when thresholds are met. These overlaps make integrated governance, shared inventories, and common evidence repositories practical.
Your teams should align data maps, system inventories, assessment workflows, and audit artifacts. This helps you answer regulators with one consistent record set.
Plan once, document once, and reuse evidence across ADMT notices, risk assessments, and cybersecurity audits.
What should you know about CCPA project planning and resourcing?
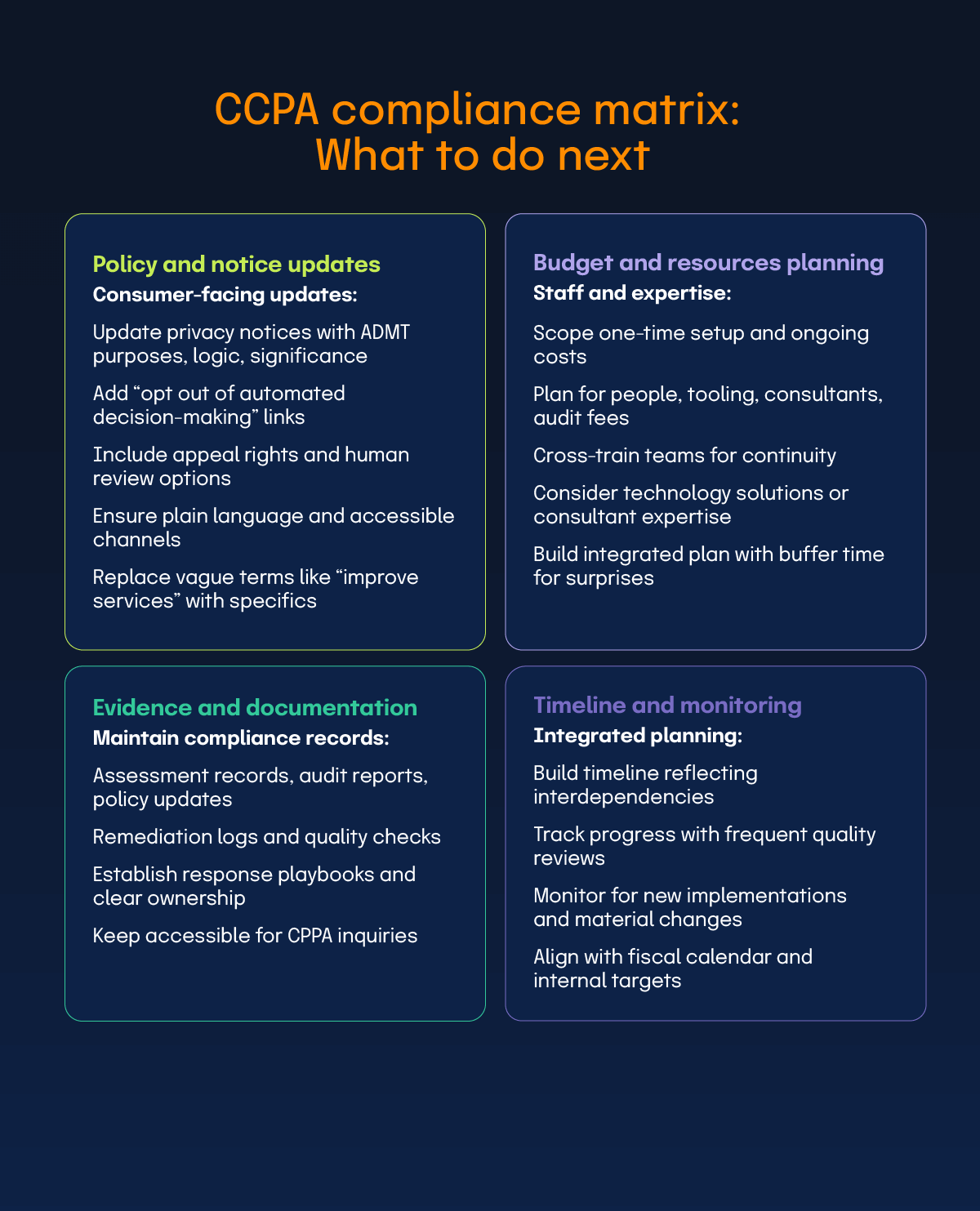
Start now with an enterprise-level gap analysis, then build a cross-functional roadmap that covers technology, policies, notices, documentation, and training.
Run a current-state review of ADMT use, risk assessment practices, and audit readiness. Catalog systems that process personal information and influence decisions. Monitor new deployments to catch triggers early.
Update policies and procedures to reflect ADMT notices, risk assessment content, approval roles, and audit evidence standards. Convert policy language into repeatable steps, owners, and timelines. Refresh privacy notices and forms so ADMT disclosures appear at or before collection.
Strengthen documentation management. Keep assessment records, audit reports, policy updates, and remediation logs organized and accessible for CPPA inquiries. Define who responds to regulators and how you communicate.
Form a cross-functional program with legal, IT, security, and business operations. Use regular checkpoints and clear decision rights. Treat privacy and security as operating requirements, not side projects.
A structured gap-to-goal plan with clear owners, artifacts, and timelines delivers faster compliance and better audit outcomes.
What are some practical checklists to get started?
Use short, repeatable checklists to drive progress across ADMT, risk assessments, and audits. Simple, focused checklists keep teams moving and produce the artifacts regulators expect to see. Here are a few templates you can use:
ADMT Readiness Checklist
Risk Assessment Checklist
Cybersecurity Audit Checklist
How should you manage enforcement risk and future change?
Expect increased scrutiny of ADMT and high-risk processing. Early enforcement will likely spotlight missed basics and weak documentation.
Keep leadership informed about California’s procedural timing and board meeting updates, then refine plans as guidance and enforcement priorities become public. Use progress reviews to correct gaps before they become audit findings.
If you operate in multiple states, anticipate similar initiatives elsewhere. A unified governance approach lets you meet variable state requirements without duplicating effort. Proactive documentation and steady iteration reduce enforcement risk while positioning you for cross-state requirements.
What to know about CCPA next steps
Start an integrated program now. Align your ADMT notices and opt-outs, lock in risk assessment workflows and evidence, and schedule audits against the 2028-2030 deadlines. The CCPA revisions favor organizations that can prove purpose, logic, mitigations, and outcomes with clear records.
Set measurable targets for each quarter. Fund training for customer-facing teams, product owners, and internal auditors. Track vendor readiness across ADMT and data-sharing uses.
Close the loop with executive attestations, annual certifications, and a single source of truth for regulators. The path is explicit. Timely, documented action now will lower cost and risk later.
Treat the CCPA revisions as a data governance program that delivers consumer trust, audit readiness, and sustainable compliance.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












