How Cybersecurity Frameworks Can Protect Your Organization (Even in the Event of a Breach)
It’s certainly no secret how damaging data breaches can be for organizations today. And if lost revenue and a tarnished reputation aren’t enough to make you want to act, your organization could face punitive damages if you fail to protect your customers’ private information. Yes, that’s right—steep fines imposed by regulatory agencies can await those who violate today’s strict data privacy laws. Equifax paid 575 million to the Federal Trade Commission for a breach they allowed in 2017, while Uber’s ineffective handling of a 2016 breach cost the company close to 150 million.
Today, most states have increasingly stringent privacy laws and breach notification requirements. However, there is some good news—certain states have established a safe harbor for organizations that create and maintain written cybersecurity programs that comply with industry-recognized security frameworks like ISO 27001, NIST CSF, and PCI DSS. In this article, we will explore the new safe harbor option and how implementing a security framework could help your business avoid the costly damages of a privacy violation.
Need Help Implementing Cybersecurity Frameworks?
Stiffening privacy laws present compliance pitfalls
Today, many states are doing more to hold organizations accountable when they fail to protect their customers’ data. Companies must now safeguard a broader range of data than ever before, and in many states, they face a shortened breach notification timeframe. These stiffening privacy regulations create all sorts of compliance pitfalls for businesses trying to avoid regulatory infractions and punitive damages.
Connecticut provides an excellent example of these stiffening privacy laws. On June 16, 2021, Connecticut Governor Ned Lamont signed HB 5310, An Act Concerning Data Privacy Breaches. HB 5310 amends Connecticut’s existing breach notification requirements by expanding the types of personal information that can trigger notification requirements if it is breached to include taxpayer ID numbers, personal IRS ID numbers, passport numbers, military ID or other government-issued ID numbers, biometric data, health insurance ID numbers, and usernames or email addresses in combination with a password or security question and answer.
HB 5310 also shortens the notification timeline of a breach to affected Connecticut residents and the Attorney General from 90 days to no later than 60 days post-discovery of the breach. It requires “preliminary substitute notice” to individuals if a business cannot provide direct notification within the 60-day notification timeframe. Companies must also follow up with direct notice as soon as possible following the preliminary substitute notice.
In passing HB 5310, Connecticut joins several other states in expanding their definition of “personal information” and shortening breach notification requirements. In 2019, nine states, including Illinois, Maine, Maryland, Massachusetts, New York, New Jersey, Oregon, Texas, and Washington, expanded breach notification laws, further complicating compliance for many companies. Keep in mind that as of April 2021, all 50 states, the District of Columbia, Guam, Puerto Rico, and the Virgin Islands have legislation requiring private or governmental entities to notify individuals of security breaches involving personally identifiable information.
Safe harbor from punitive damages

Even the most optimistic security professionals must admit no defense is infallible, and breaches happen even with the best security controls in place. Is there anything your organization can do to protect itself from regulators threatening steep punitive damages if a breach occurs? Currently, several states—Ohio, Utah, and Connecticut—offer safe harbor protection for organizations able to document their security program’s adherence to a recognized security framework. Make no mistake—safe harbor protection doesn’t prevent lawsuits, but it provides a legitimate defense for companies actively implementing recognized security frameworks.
Let’s look at Ohio, which passed SB 220, otherwise known as the Ohio Data Protection Act, in 2018. Ohio was the first state to offer a breach litigation safe harbor to companies with security policies aligned with recognized frameworks. To be eligible for the safe harbor, covered entities must “create, maintain, and comply with a written cybersecurity program” that “reasonably conforms” to one of several named cybersecurity frameworks. As stated in the law, the recognized frameworks in SB 220 include:
- The NIST Cybersecurity Framework, NIST’s SP 800-171, SP 800-53, or SP 800-53a, FedRAMP, the Center for Internet Security (CIS) Critical Security Controls, or the International Organization for Standardization/International Electrotechnical Commission (ISO) 27000 family;
- For regulated entities, the cybersecurity requirements of HIPAA, the Gramm-Leach-Bliley Act, FISMA, or HITECH, as appropriate; or
- The PCI Data Security Standard (PCI DSS) in conjunction with one of the other standards listed in (1) or (2).
In July 2021, Ohio passed HB 376, or the Ohio Personal Privacy Act (OPPA), which echoed the original safe harbor legislation while explicitly identifying the NIST framework. OPPA states a business has an affirmative defense against the allegation of privacy violations if the business creates, maintains, and complies with a written privacy program reasonably conforming to the National Institute of Standards and Technology (NIST) Privacy Framework. The Ohio law also states when a security framework is revised, the organization must confirm its own privacy program to the revised framework not later than one year after the publication date stated in the revision.
In early March 2021, Utah became the second state to adopt a cybersecurity safe harbor statute as a viable defense in the event of breach litigation. Utah H.B. No.0080, known as the Cyber Security Affirmative Defense Act, states entities creating, maintaining, and reasonably complying with a written cybersecurity program (in adherence with a recognized security framework) may use their compliance with their cybersecurity program as an affirmative defense to data breach claims brought under state law.
The recognized frameworks referenced in H. B. No. 0080 include the NIST special publication 800-171, 800-53, and 800-53a; (CIS) Critical Security Controls for Effective Cyber Defense; and ISO 27000 Family – information security management systems.
Connecticut, the third state to adopt safe harbor legislation, passed H.B. 6607 known as “An Act Incentivizing the Adoption of Cybersecurity Standards for Businesses” in March 2021. H.B. 6607 protects businesses from punitive damages resulting from breaches exposing customer’s personal data if they adopt and adhere to a recognized cybersecurity framework. H.B. 6607 prevents the Connecticut Superior Court from assessing punitive damages against an organization that created, maintained, and complied with a written cybersecurity program containing administrative, technical, and physical safeguards to protect personal or restricted information and operates in conformity with an industry-recognized security framework.
The recognized frameworks referenced in H.B. 6607 include the NIST’s Framework for Improving Critical Infrastructure Cybersecurity; Special Publications 800-171, 800-53 and 800-53a; the Federal Risk and Authorization Management Program’s FedRAMP Security Assessment Framework; the CIS’s Critical Security Controls for Effective Cyber Defense; or the ISO/IEC 27000 series.
H.B. 6607 also states that when a framework is revised, the organization must confirm its security program to the revised framework no later than six months after the publication date stated in the revision.
Benefits of implementing cybersecurity frameworks

Aligning your security program with industry-recognized standards and frameworks delivers numerous benefits in addition to shielding your business from punitive damages in the event of a breach. When your team implements a standard like ISO 27001 or NIST CSF, your business is effectively choosing to take a risk-based approach to managing information security. You’re making a commitment to continuously improving the controls—systems, processes, policies, and technical components—in place to protect sensitive information and maintain regulatory compliance. With so many disparate privacy and cybersecurity laws in place, every organization needs a more sustainable, strategic approach to managing the rules and requirements; this approach needs to be something that can accommodate future rules easily. Aligning your IT risk management program with industry-recognized security frameworks like NIST CSF and ISO 27001 can help you do just that.
If I’ve recently done SOC 2® Type 2, does that qualify my organization for safe harbor in states that have safe harbor legislation?
Many smaller organizations and early-stage startups have already obtained a SOC 2® Type 2 report. But does a SOC 2® Type 2 certificate qualify them for safe harbor protection under the current laws? Unfortunately, SOC 2® is not currently considered an acceptable cybersecurity framework under these state laws. While the legal texts did not state why having a current SOC 2® attestation report does not qualify as complying with an industry-recognized security standard, it’s likely that regulators recognized two key differences between SOC 2® and the cybersecurity frameworks they put on the list:
- The scope of a SOC 2® Type 2 assessment is most likely narrower than the scope of an audit for the ISO 27001 certification process (and it’s narrower than the scope of the required activities covered by the NIST Cybersecurity Framework, NIST SP 800-53 and NIST SP 800-171). The SOC 2® attestation report outlines the controls that are actually meeting the applicable Trust Services Criteria based on the company’s commitment. For SOC 2®, a company chooses which of the five Trust Services Criteria—Security, Availability, Privacy, Confidentiality, and Processing Integrity—will be in scope for the assessment. On the other hand, if an organization wants to claim that it is “ISO 27001 compliant”, it would need to achieve a certification from an approved auditor showing that the organization’s information security management system (ISMS) conforms to the ISO 27001 standard. The ISO 27001 certification focuses on higher level ISMS processes and broader information security risk that can apply to matters like documentation management, human resources, asset management, and supplier relationships. This is not necessarily the same scope as SOC 2®.
- Time horizon. The SOC 2® type 2 assessment covers a historical period, so it can only show that an organization has maintained appropriate controls in the past. On the other hand, the ISO certification is meant to communicate that the ISMS is actively implemented and continues to operate effectively.
However, here’s the good news—organizations who have put in the work and obtained a SOC 2® Type 2 certificate are well on their way to aligning with ISO 27001, NIST CSF, and FedRAMP requirements. They already have numerous administrative, procedural, and technical controls in place to protect information and user privacy—so they don’t need to start from scratch. Instead, implementing ISO 27001, NIST CSF, or FedRAMP represent an expansion or maturation of their IT risk management processes.
How Hyperproof helps organizations adopt IT security frameworks

For businesses of all sizes, protecting customer data and remaining compliant with privacy regulations can prove quite challenging today. Organizations must be mindful of broadening definitions of what counts as “personal identifiable information” under state privacy laws and changing time frames within breach notification laws. Without a strategic approach, organizations can easily step into compliance minefields. The good news is that there is a way for modern security teams to mitigate compliance risk and improve their organizations’ security posture at the same time: by aligning their policies and security and risk management processes with recognized frameworks and standards. For those organizations yet to implement a security framework, there couldn’t be a better time to begin the process.
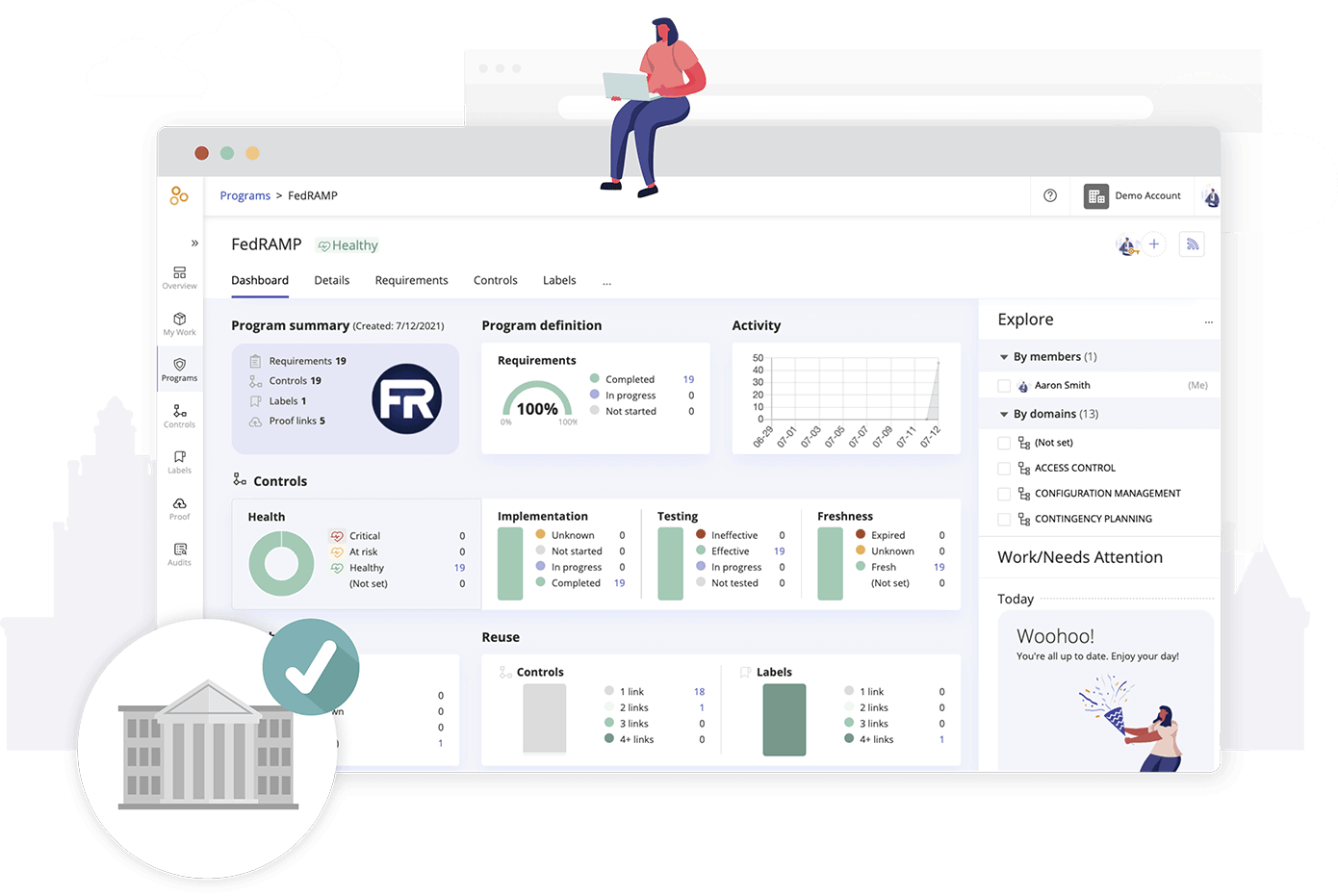
Hyperproof’s compliance operations platform can help any size business implement industry-recognized cybersecurity frameworks in the most efficient and effective way. Hyperproof provides a central system for planning, managing, and monitoring all security assurance/compliance work, helping compliance professionals drive accountability for security and compliance to stakeholders across an organization. Here are some specific ways Hyperproof’s compliance operations platform can help your business implement a security framework:
- Understand each cybersecurity framework’s requirements in detail
- Document your infosec risk assessment results and risk response plans
- Develop your ISMS by implementing controls, assigning roles and responsibilities, and keeping people on track
- Streamline evidence collection and management by putting evidence in a single repository
- Automate evidence collection by setting up automated connectors to third-party file-sharing systems and cloud-based business apps
- Set up an internal audit program which includes the required steps for your company to audit its own ISMS and control activities
- Know how close you are to being certification-ready and invite auditors to review work in the Hyperproof platform
- Conduct mapping between SOC 2® controls and ISO 27001 Annex A controls
To learn more about how Hyperproof can help your team implement a security framework, sign up for a demo.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?