Implementing a Common Controls Framework using Hyperproof
If you’re ready to take the next step in making your organization more compliant with current cybersecurity and privacy frameworks, Common Controls Frameworks are a great place to start. They allow you to implement a range of validated controls that you can use to form the basis of compliance with a variety of different frameworks. Whether you’re looking to start building compliance in your organization or you think it’s time to pivot towards a new framework, implementing common controls is a great direction to go in.
What is a Common Controls Framework (CCF)?
A Common Controls Framework (CCF) is a comprehensive set of control requirements that have been aggregated, correlated, and rationalized from the vast array of industry information security and privacy standards. Utilizing a CCF enables an organization to meet the requirements of these security, privacy, and other compliance programs while minimizing the risk of becoming “over controlled.”
Why a CCF approach makes sense
Implementing a common controls framework that is focused on the unique security of your organization is an effective way to reduce the operational disruption of your organization. Focusing on security first and mapping your security-focused controls to compliance frameworks will help you comply with several security certifications, standards, and regulations. Most frameworks have the same underlying security principles with minor differences in how you produce evidence and how your auditors evaluate your environment.
A common controls framework helps guide you and your auditors through existing compliance assessments. This central framework can also help you more easily identify any gaps with other frameworks that you may explore in the future. You can perform an analysis of your current control set against existing standards and avoid auditor fees for readiness assessments. This common framework helps you see your current state more accurately and allows you to easily adapt and expand into different security certifications and requirements.
What is the Secure Controls Framework (SCF)? And what does it provide?
The Secure Controls Framework (SCF), which is the basis for the compliance framework crosswalks within Hyperproof, is a comprehensive catalog of controls that enables companies to design, build, and maintain secure processes, systems, and applications. The SCF addresses both cybersecurity and privacy so that these principles are “baked in” at the strategic, operational, and tactical levels.
The SCF comprises thirty-three (33) domains that cover the high-level topics expected to be addressed by cybersecurity and privacy-related statutory, regulatory, and contractual obligations. These are the cybersecurity and privacy-related policies, standards, procedures, and other processes that are designed to provide reasonable assurance that business objectives will be achieved and undesired events will be prevented, detected, and corrected as much as possible.
The SCF aims to provide cybersecurity and privacy control guidelines to organizations of any size and across any sector, helping them to implement best practice controls to protect their data and processes and respond to evolving threats. The framework currently incorporates over 1,000 controls, is baselined across more than 150 regulations and standards, and is updated every few months.
Benefits of using a CCF based on the SCF
The SCF is designed to empower organizations to design, implement, and manage both cybersecurity and privacy principles to address strategic, operational, and tactical guidance. It is far more than building for compliance — we know that if you build security and privacy principles into your daily operations, complying with statutory, regulatory, and contractual obligations will come naturally.
There are many benefits to an organization adopting a CCF based on the SCF:
- By using a well-established baseline set of control requirements and associated controls, it allows the organization to get a headstart on optimizing the controls environment.
- The SCF is updated frequently, thus ensuring the organization remains aware of any changes to the compliance frameworks in use.
- By leveraging a common control to meet multiple compliance requirements, an organization can be expected to gain efficiencies in performing its current audit engagements, including SOX 404-ITGC, PCI-DSS, etc. Using the crosswalks provided by SCF, additional compliance frameworks can be assessed quickly, and a more rapid implementation plan can be developed using the controls already in place.
- Compliance fatigue should be reduced for the organization’s audit control owners and partners. Currently, these individuals are often subjected to multiple audit requests that can often be met by the same audit evidence.
- It provides a holistic view of the organization’s control environment as the CCF traverses the audit and compliance lines of SOX and PCI audit engagements.
- The organization will have the ability to benchmark its control environment and identify its maturity model against other organizations.
- The organization can begin evaluating controls to identify suitable candidates for automation.
- It can help the organization develop a consistent approach to performing and documenting controls across the organization and potential acquisitions.
- If acquisitions need to be integrated into the organization environment, a CCF provides ease of onboarding and enables these acquisitions to come into compliance more quickly. A CCF enables the new acquisitions to inherit the existing simple and scalable controls to reduce the overall effort to meet compliance goals.
How using a CCF promotes efficiency
First and foremost, using common controls is advantageous because it is a flexible, achievable approach to a complicated problem. In the past, organizations would try to adhere to particular requirements to achieve compliance, but technical barriers make it difficult to communicate these needs to business units that aren’t involved in the technical side of operations. For this reason, we have noted a shift away from requirements towards a controls-focused approach. Since controls are the specific policies, procedures, and activities a business function is doing to meet compliance requirements and mitigate risks, they are easier to break down and document across an organization and reuse where needed.
All of the controls included in a CCF that has been validated by the SCF have been rigorously examined and found to be valuable by the security and privacy community at large, which means these are the most effective controls you can implement. For a real-life example, watch our webinar about how using common controls helped Nutanix and Qorus Software.
How to implement and manage a CCF with Hyperproof
Out of the box, Hyperproof provides a set of illustrative controls for many of the most commonly used security and privacy compliance frameworks, including NIST-CSF, PCI-DSS, ISO 27001, and many others. These controls are linked to program requirements providing a quick-start approach for many organizations.
For organizations who already have existing controls in place, it’s quite simple to edit the provided controls, add new controls, and remove superfluous ones. As requirements across frameworks are linked within the SCF model, all changes to controls will still map across frameworks, significantly reducing the risk of duplicate controls.
Within Hyperproof, all controls are defined once…
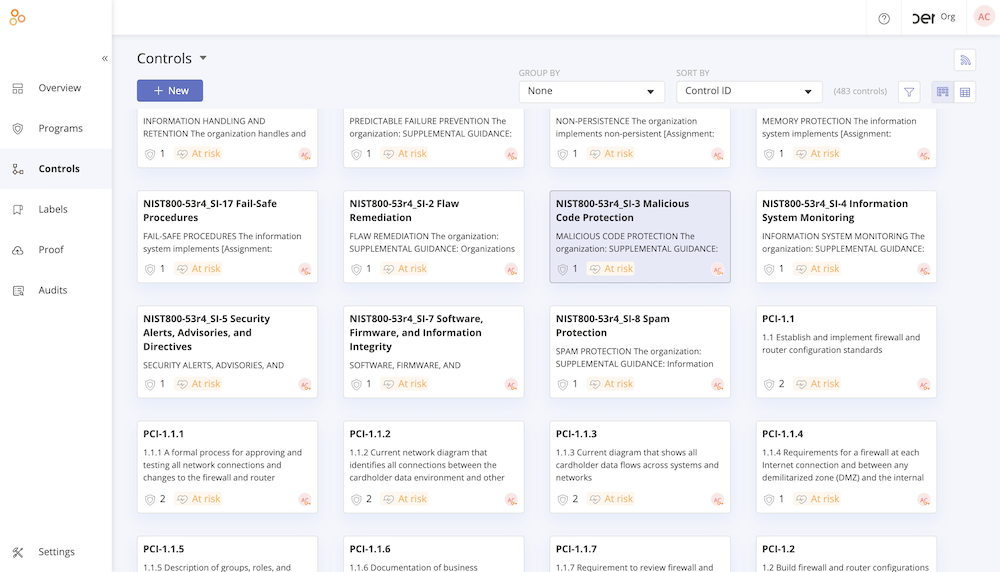
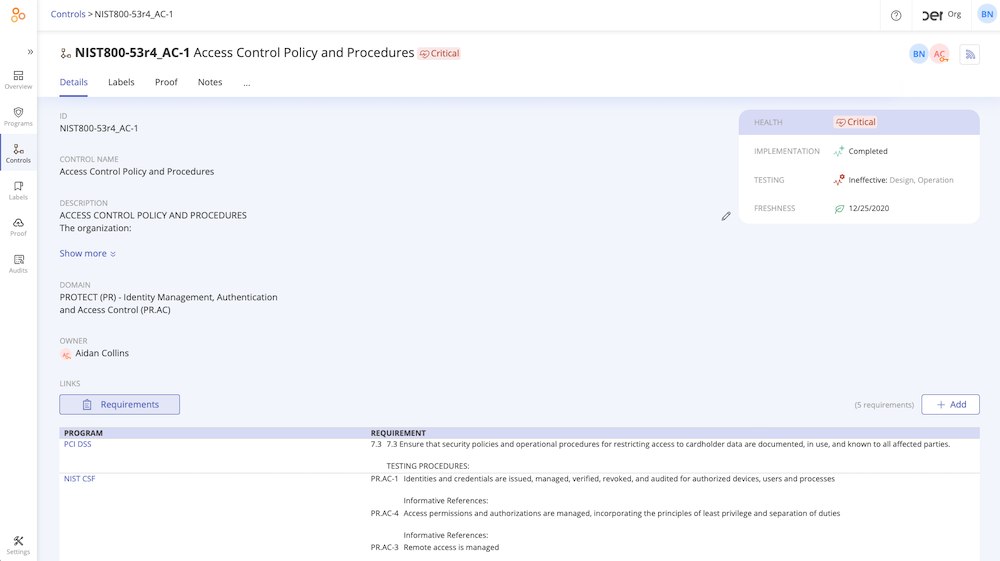
…and are linked to multiple requirements across multiple frameworks.
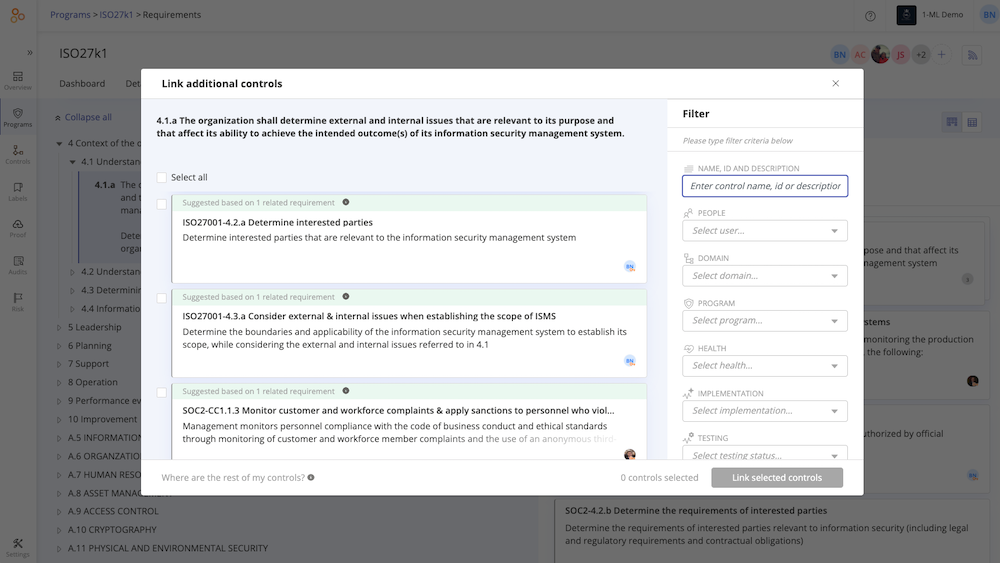
As changes are made to the details of controls, or new framework requirements are added, the application includes an option to select which controls should be linked to new requirements from suggestions based on the provided crosswalks.
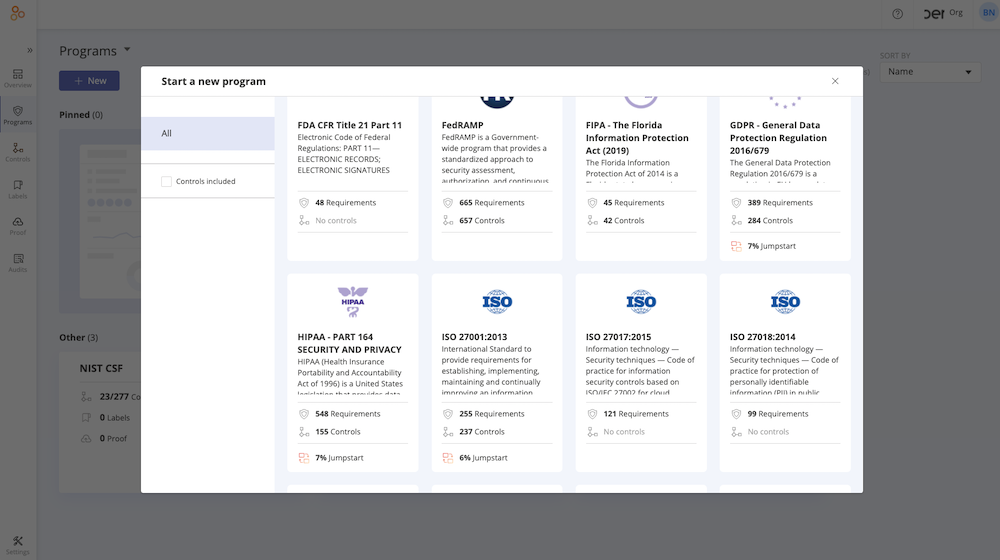
Additionally, as new frameworks are assessed and eventually operationalized, the “Jumpstart” feature provides a quick view into how the existing control environment meets the requirements of these new frameworks.
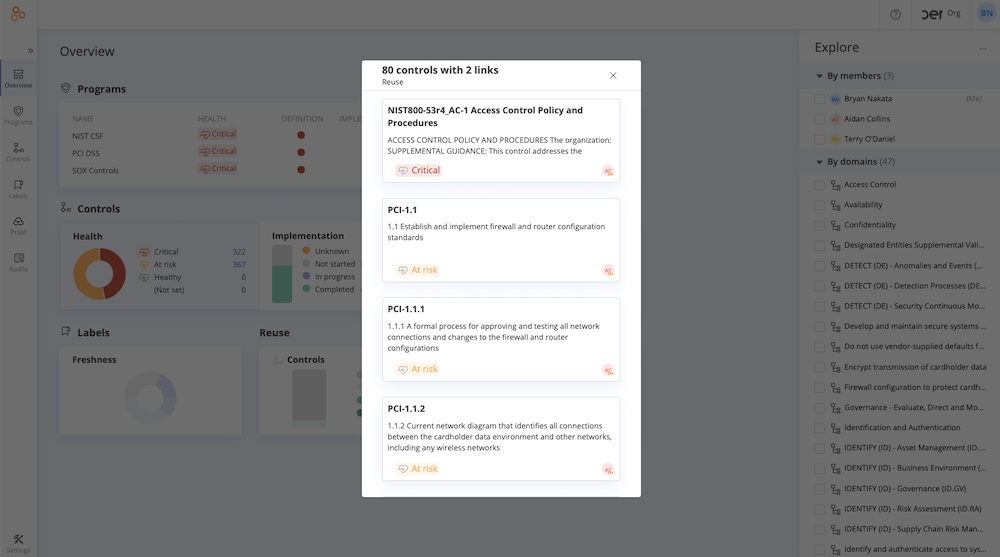
Hyperproof also quickly shows how “efficient” the control environment is by highlighting which controls are linked to more than one program requirement. This can help focus analyst efforts on increasing the percentage of controls that meet multiple requirements.
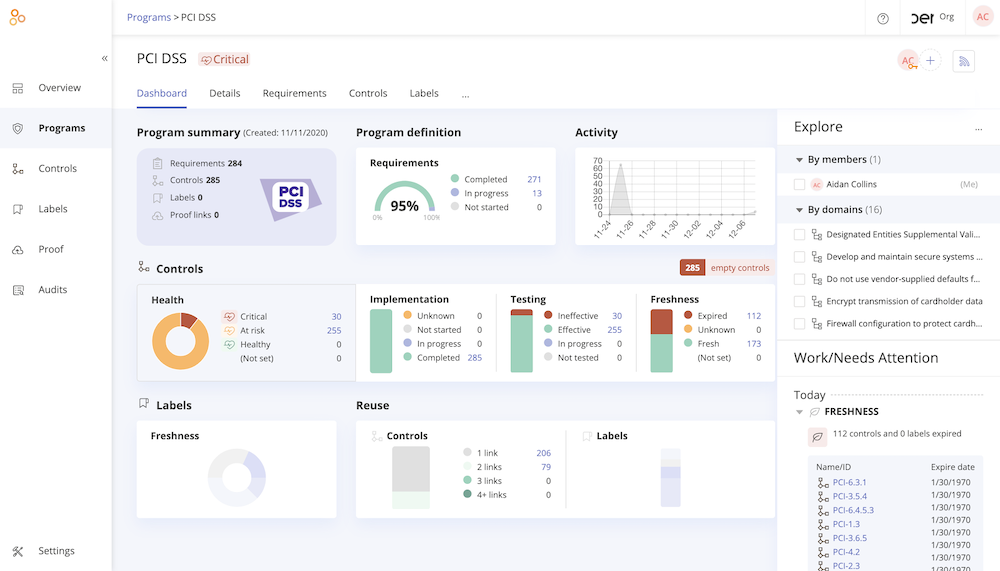
The dashboard reporting features of Hyperproof allow the organization to quickly see the compliance status against the requirements of a single compliance framework…
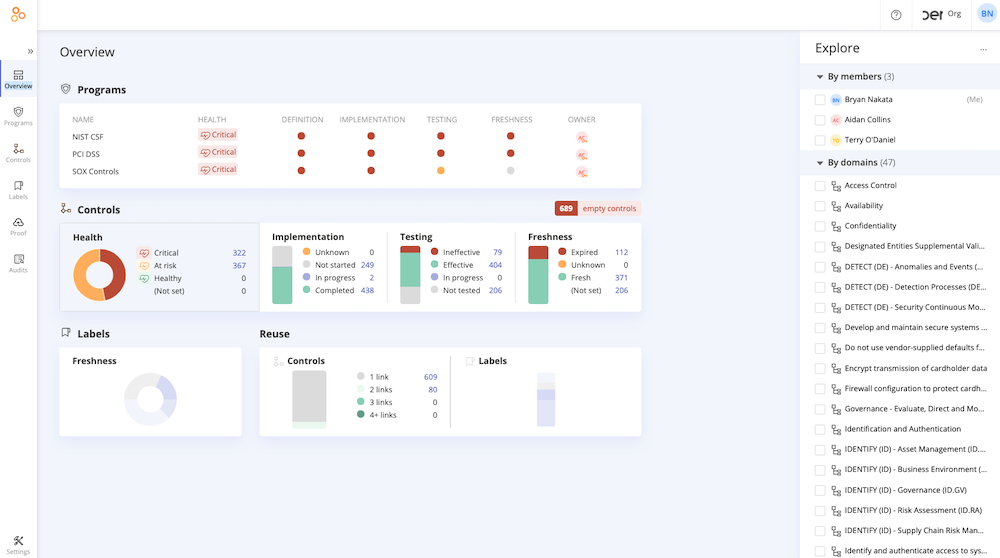
…as well as across all the frameworks currently operationalized across the organization.
Get started with a CCF and Hyperproof today
It’s never a bad time to start using a common controls framework within your organization. Even if your business doesn’t have an immediate need to comply with a specific framework, it’s always good to follow industry best practices around security and privacy and work toward improving your organization’s security posture.
Furthermore, using Hyperproof to keep track of your controls makes it easy to figure out what steps your organization needs to take in order to become compliant with a specific framework, which can be extremely helpful if your company grows or moves in a direction that requires more rigorous controls.
Learn more about how to implement a Common Control Framework using Hyperproof.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












