What Evidence of Control Operation Do Federal Regulators Really Expect?
Federal regulators have been changing their approach to cybersecurity oversight in recent years. Where checkbox compliance once satisfied most agency requirements, regulators now often demand comprehensive evidence demonstrating that security controls function as intended. This transformation suggests a maturing regulatory landscape that may place greater emphasis on measurable outcomes rather than relying solely on documented procedures.
The change is likely a result of lessons learned from high-profile breaches where organizations had extensive security policies yet failed to prevent or detect intrusions. Regulatory agencies are increasingly skeptical of compliance programs that exist primarily on paper, instead seeking concrete proof that controls operate effectively in production environments. This shift may create new challenges for organizations accustomed to traditional ‘checkbox’ compliance approaches.
The shift to evidence-based cybersecurity compliance
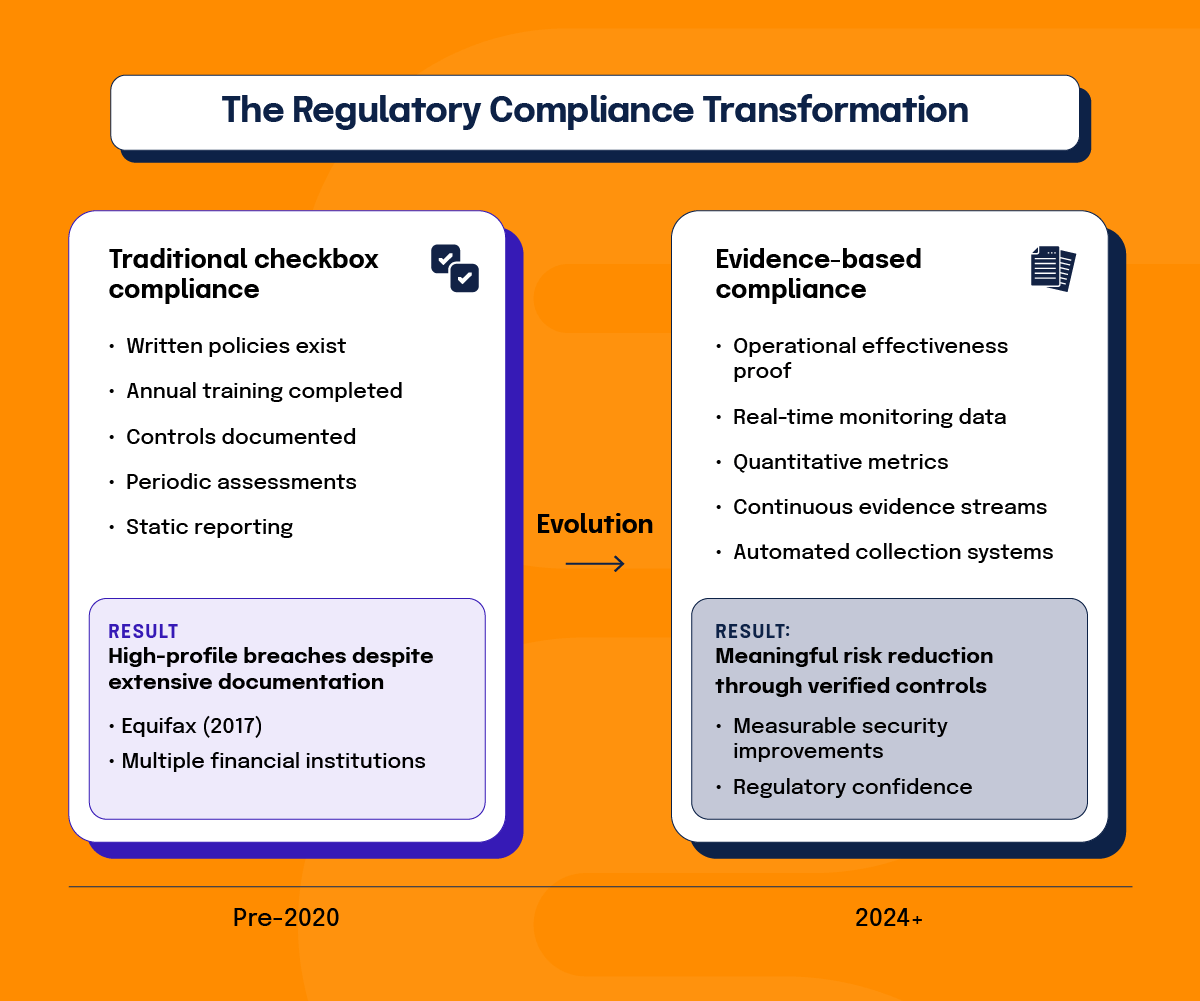
Traditional compliance methodologies, which emphasized policy documentation and procedural frameworks, are now insufficient for contemporary regulatory expectations. Now, agencies require continuous evidence streams that demonstrate control effectiveness through measurable operational outcomes.
This change is a result of several high-profile incidents where organizations maintained extensive compliance documentation while experiencing significant security failures. The 2017 Equifax breach served as a watershed moment, revealing how traditional audit approaches focused on policy review could overlook substantial operational deficiencies. The incident demonstrated that written procedures, no matter how comprehensive, provide little protection when actual implementation falls short of documented intentions.
Current regulatory frameworks prioritize real-time monitoring data, automated evidence collection, and quantitative security metrics over static documentation. Agencies now expect organizations to produce reports demonstrating policy adherence or statistical analysis proving security program effectiveness. The evidentiary burden has shifted from documenting good intentions to proving operational reality through continuous measurement.
Multiple compliance frameworks are converging around these evidence-based expectations. Healthcare entities subject to HIPAA enforcement now need to demonstrate actual safeguards implementation rather than just written policies. Financial institutions face similar expectations across multiple regulatory frameworks.
Understanding cross-agency coordination and common expectations
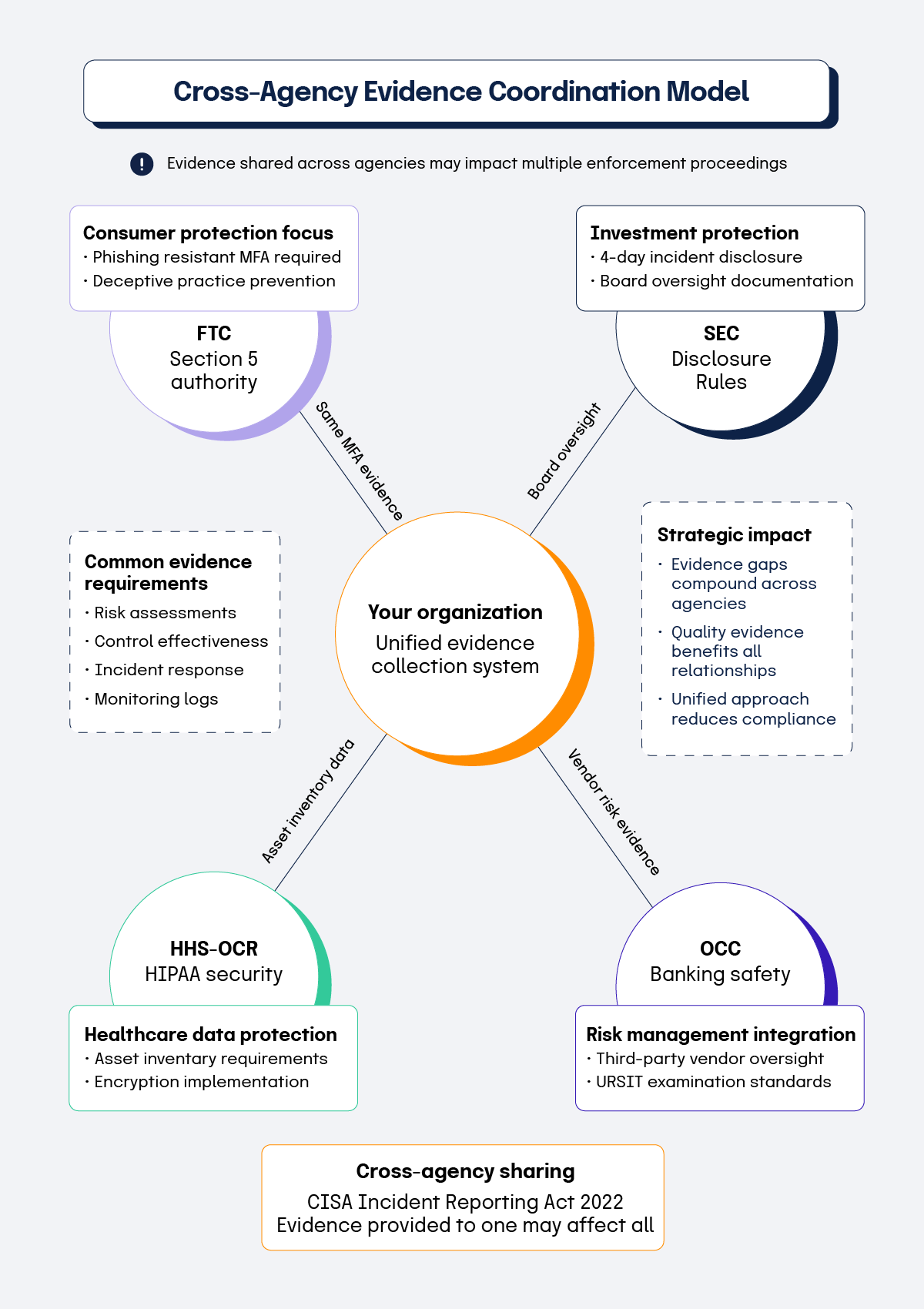
Organizations may increasingly face examination of identical controls by multiple agencies applying different regulatory lenses. For example, a financial services company might encounter SEC scrutiny under securities regulations, Treasury Office of the Comptroller of the Currency (OCC) examination under banking authority, and Federal Trade Commission (FTC) investigation under consumer protection jurisdiction. Each agency expects similar evidence types while applying distinct legal standards and enforcement priorities.
This coordination creates both opportunities and challenges for compliance programs. Organizations can satisfy multiple regulatory requirements through unified evidence collection systems that address common expectations across agencies. They must also understand how different regulators interpret identical evidence and adjust their documentation strategies accordingly. Evidence sufficient for one agency may prove inadequate for another with different enforcement focus areas.
Cross-agency information sharing is expanding, particularly for cybersecurity incidents affecting multiple sectors. The Cyber Incident Reporting for Critical Infrastructure Act of 2022 may facilitate greater coordination by requiring CISA to share incident information with relevant sector regulators. Organizations should consider that evidence provided to one agency may influence examinations and enforcement decisions by others with overlapping jurisdiction.
Courts are also setting precedents where sharing evidence with a regulator, under a regulatory requirement, may result in that evidence being available for discovery by other regulatory bodies or attorneys.
Regulatory landscape and enforcement patterns by agency
Understanding the distinct yet increasingly coordinated approaches of federal agencies provides the foundation for effective evidence collection strategies. Each agency operates under different legal authorities while converging around common evidence expectations that reflect the broader shift toward operational proof of security effectiveness.
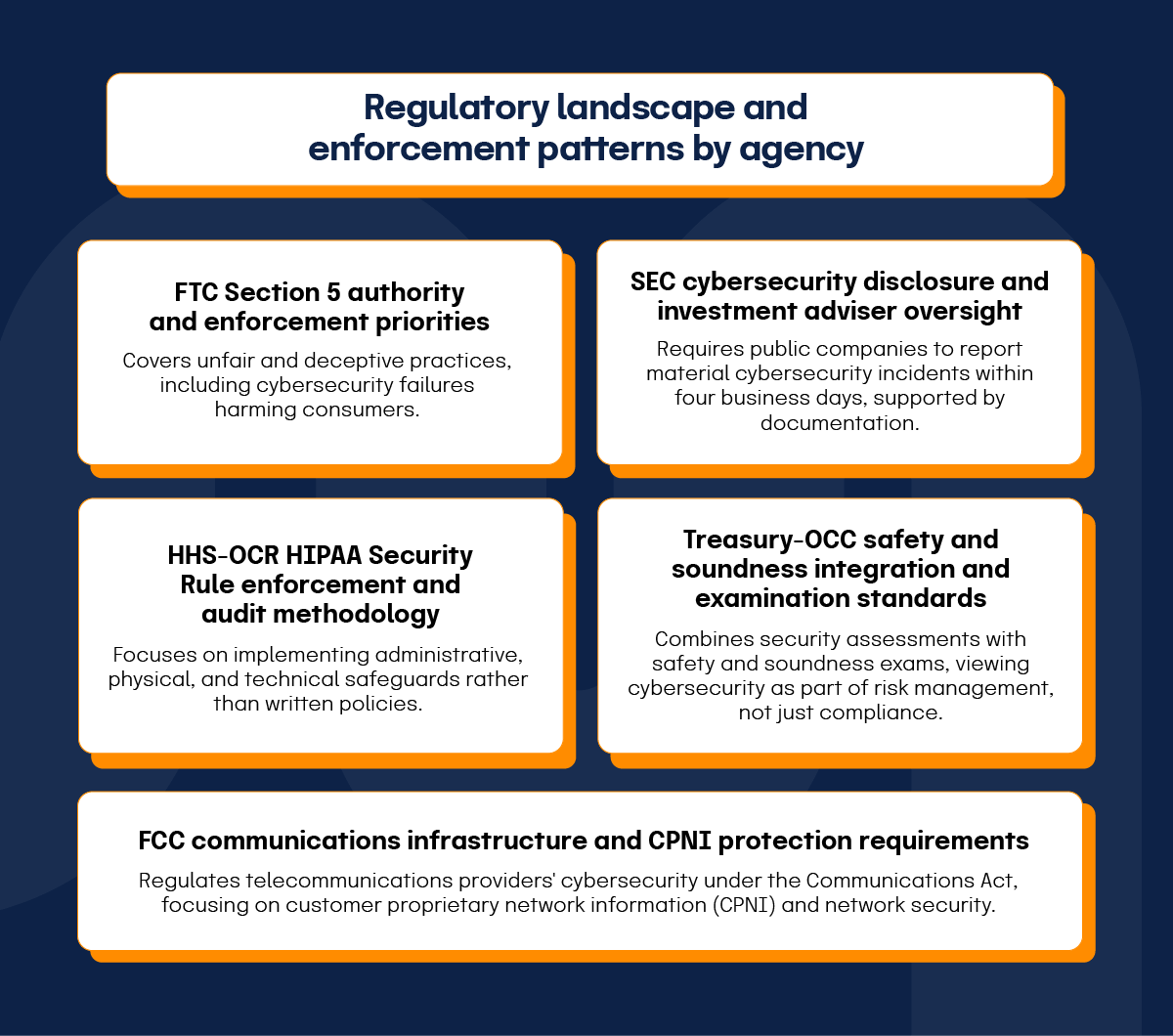
FTC Section 5 authority and enforcement priorities
The FTC’s authority under Section 5 of the FTC Act covers unfair and deceptive practices, including cybersecurity failures harming consumers. “Reasonable security” means implementing security measures suitable for an organization’s context, data sensitivity, and consumer risk, focusing on practical effectiveness over strict compliance.
Recent actions highlight expectations for comprehensive security programs: documented risk assessments, proportionate safeguards, ongoing training, and effective incident response. The FTC checks if organizations follow their security procedures rather than just theoretical compliance.
Settlements with GoDaddy, Chegg, and Drizly show the FTC’s focus on phishing-resistant MFA. Orders like the GoDaddy settlement mandate MFA “resistant to phishing,” excluding phone or SMS. FTC staff recommend “security keys instead of numeric codes or push notifications” to reduce security risks.
The agency enforces cybersecurity representations in privacy policies and marketing. Organizations must support security claims with operational evidence, with penalties considering security failures and good faith compliance efforts through documentation.FTC examinations prioritize evidence of ongoing compliance with real-time monitoring over periodic assessments.
SEC cybersecurity disclosure and investment adviser oversight
The SEC’s cybersecurity disclosure requirements, effective December 2023, require public companies to report material cybersecurity incidents within four business days, supported by documentation. Evidence must include detailed incident response records, board-level oversight records, and risk assessment procedures to substantiate public statements about cybersecurity programs and incident impacts.
Regulation S-P amendments, effective May 2024, add safeguards for financial institutions handling consumer financial information. SEC examinations show common deficiencies like inadequate cybersecurity policies, insufficient board oversight documentation, and poor incident response capabilities. Broker-dealer examinations also focus on customer data protection evidence, trading system security documentation, and business continuity testing records.
The commission prioritizes practical implementation verification over policy documentation. Investment advisers must show cybersecurity program functionality through operational evidence, like monitoring data, testing results, and performance metrics that validate policy effectiveness. Recent enforcement actions suggest evidence quality affects settlement terms and penalties, with organizations demonstrating active security program management receiving more favorable treatment than those with limited implementation evidence.
HHS-OCR HIPAA Security Rule enforcement and audit methodology
HHS-OCR’s enforcement of the HIPAA Security Rule focuses on implementing administrative, physical, and technical safeguards rather than written policies. Their risk-based audit includes document requests, on-site interviews, and technical control assessments. Required evidence includes risk assessments, control deployment records, training materials, audit log review procedures, and incident response documentation.
Proposed HIPAA Security Rule updates, published in December 2024, introduce new evidence requirements. HHS proposes that covered entities “maintain an accurate and thorough written inventory … of the … electronic information systems and all technology assets” affecting electronic protected health information (ePHI).” The Inventory requirements would also cover business associate assets involved in ePHI handling, requiring inclusion in the covered entity’s network map and inventory.
Recent audits show common deficiencies in risk assessment, access control deployment, and audit log analysis. HHS-OCRs’s enforcement approach requires that organizations show HIPAA compliance programs lead to real security improvements. During settlement negotiations, comprehensive and quality evidence can result in more favorable resolutions.
Treasury-OCC safety and soundness integration and examination standards
The OCC combines security assessments with safety and soundness exams, viewing cybersecurity as part of risk management, not just compliance. Examiners use the Uniform Rating System for Information Technology (URSIT) and Cybersecurity Supervision Work Program to assess how banks identify, measure, monitor, and control cybersecurity risks with evidence.
The focus is on risk management process effectiveness rather than specific technical compliance. Banks must show cybersecurity programs fit their risk profiles, activities, and complexity. Quality evidence influences ratings, with strong documentation leading to better assessments.
The OCC’s vendor risk management assesses if banks maintain oversight of outsourced functions. Required evidence includes vendor risk assessments, contract security provisions, and monitoring records showing supply chain cybersecurity management. Recent updates stress integrating security metrics with risk indicators and incident escalation through governance.
FCC communications infrastructure and CPNI protection requirements
The FCC regulates telecommunications providers’ cybersecurity under the Communications Act, focusing on customer proprietary network information (CPNI) and network security. The updated 2024 cybersecurity framework mandates safeguards like access control, authentication documentation, and breach notification processes. Providers must show evidence of protections suitable for customer data sensitivity and regulatory needs.
FCC evidence requirements include network security assessments, incident response proof, and supply chain risk management, with a focus on operational evidence over policy alone. Coordination with federal initiatives through the National Cybersecurity Strategy aligns FCC rules with CISA and other standards, enabling unified evidence collection for multiple obligations.
Recent FCC enforcement actions indicate the agency expects comprehensive security programs with regular risk assessments, technical safeguards, employee training, and effective incident responses. Evidence quality heavily influences enforcement outcomes and penalties.
Technical control evidence requirements
The technical foundation of cybersecurity compliance now requires detailed operational evidence that demonstrates control effectiveness through measurable performance indicators. Regulatory agencies expect organizations to move beyond configuration documentation toward continuous proof that technical controls function as intended in production environments.
Want to ensure your technical security controls generate the evidence regulators expect to see?
Download the Technical Control Evidence Validation Checklist ›

Multi-factor authentication implementation and effectiveness proof
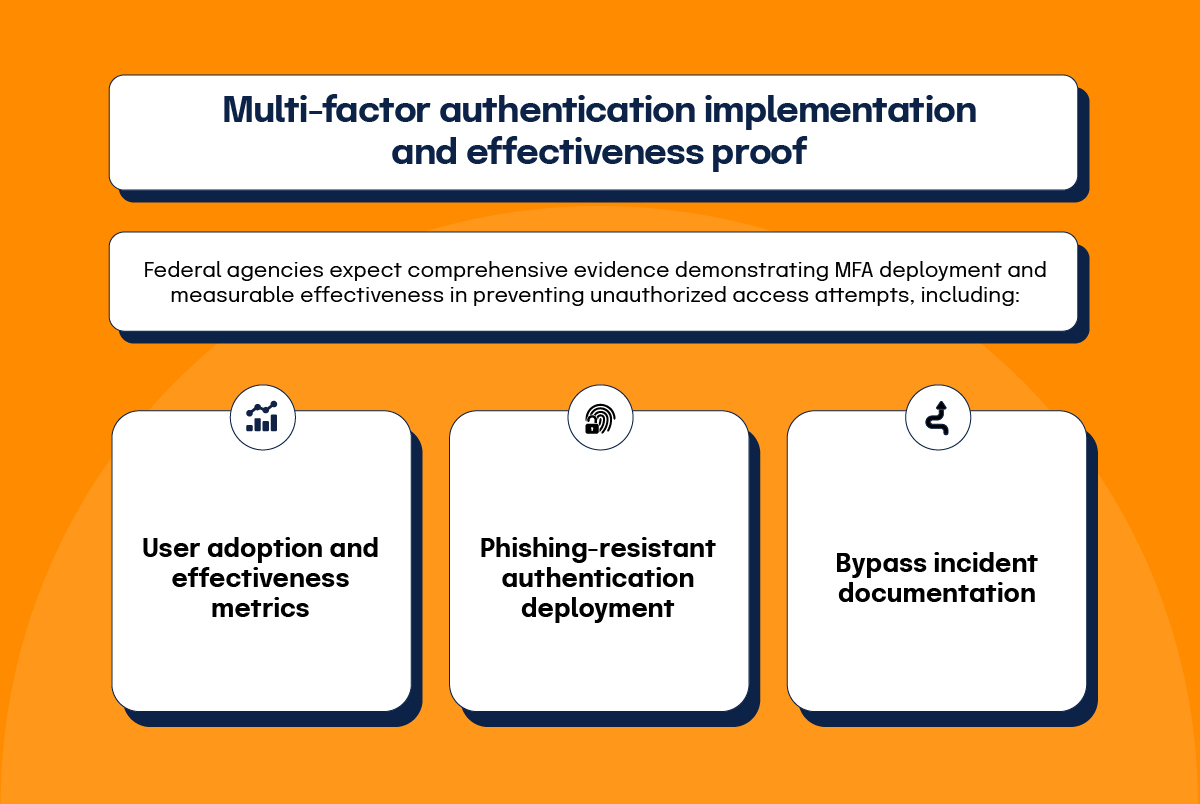
Federal agencies now expect comprehensive evidence demonstrating MFA deployment and measurable effectiveness in preventing unauthorized access attempts. Evidence requirements extend beyond technical configuration documentation to include usage analytics, resistance to attack vectors, and operational performance metrics that prove authentication controls provide meaningful security protection.
The regulatory push toward phishing-resistant MFA reflects growing awareness of traditional authentication vulnerabilities. The 2022 Office of Management and Budget (OMB) memorandum required all government agency staff, contractors, and partners to implement phishing-resistant MFA. The OMB indicated that phishing-resistant MFA is necessary because these identified users “are among the most valuable targets for phishing” and the problem can be “mitigated by providing users with phishing-resistant tokens.”
Understanding the specific attack vectors that compromise traditional MFA is important for evidence collection strategies. Cyber-criminals such as Scattered Spider have used tactics such as “push bombing” to bypass MFA protocols. Push bombing involves an unauthorized party obtaining the user’s username and password and using those credentials to cause the MFA push notification to occur multiple times until the legitimate user approves the request. Additionally, one-time passwords delivered via SMS can be vulnerable to SIM-swapping, which allows a criminal to steal a victim’s phone number and then steal any MFA codes delivered to the victim’s phone.
Technical implementation evidence must include detailed configuration specifications showing authentication factor requirements for different access scenarios, risk-based authentication logic, and integration with existing identity management systems. Agencies expect organizations to document authentication method selection rationale, risk mitigation analysis, and consideration of alternative approaches that address identified threat vectors.
User adoption and effectiveness metrics
User adoption and effectiveness metrics are increasingly important for demonstrating MFA operational success. Regulators expect organizations to track enrollment completion rates, authentication success percentages, and user resistance incidents. Low adoption rates, frequent bypass requests, or high failure rates indicate implementation deficiencies requiring additional controls or improved user training programs.
Phishing-resistant authentication deployment
Phishing-resistant authentication deployment is subject to heightened regulatory attention as agencies recognize the limitations of traditional SMS and email-based authentication methods. Organizations must demonstrate progression toward more secure authentication technologies, implementation timelines for legacy method replacement, and risk mitigation strategies for systems that cannot support advanced authentication approaches.
Bypass incident documentation
Bypass incident documentation is particularly important during regulatory examinations. Agencies examine how organizations handle MFA bypass requests, approval process requirements, monitoring of temporary exceptions, and validation that bypasses are appropriately time-limited. The frequency and duration of authentication bypasses indicate whether MFA provides actual security protection or exists primarily for compliance purposes.
Asset discovery, inventory maintenance, and vulnerability management documentation
Comprehensive asset inventories are foundational for multiple regulatory frameworks, with agencies expecting organizations to maintain current, accurate catalogs of all technology components, including cloud services, mobile devices, and Internet of Things equipment. Asset inventory evidence must demonstrate continuous discovery processes rather than periodic snapshot assessments.
Software inventory documentation
Software inventory documentation requires detailed information about installed applications, version specifications, licensing compliance, end-of-life timeline tracking, and security patch status. Organizations must demonstrate automated inventory collection processes, change detection capabilities, and approval workflows for new software installations that maintain inventory accuracy over time.
Hardware inventory evidence documentation
Hardware inventory evidence requires similar comprehensiveness, including device specifications, network connectivity mapping, physical location tracking, and maintenance schedule documentation. Mobile device management and IoT equipment present particular challenges for comprehensive inventory maintenance, requiring specialized discovery and monitoring capabilities.
The challenge of maintaining comprehensive inventories is compounded by “shadow IT,” software or hardware used by employees without the IT department’s approval or knowledge. Organizations must account for these unauthorized assets in their evidence collection strategies while implementing discovery mechanisms that can identify previously unknown components within their environments.
Vulnerability management evidence
Vulnerability management evidence extends far beyond scanning report generation to include risk-based prioritization documentation, remediation timeline tracking, exception handling procedures, and effectiveness validation. Agencies expect detailed records demonstrating how organizations identify vulnerabilities, assess risk impacts, prioritize remediation efforts, and verify that fixes address identified security gaps.
End-of-life product management
End-of-life product management receives particular regulatory attention as organizations struggle to maintain security for aging technology components. According to the CISA, “continued use of EOL software poses consequential risk to [an organization’s] system that can allow an attacker to exploit security vulnerabilities.” Evidence must demonstrate proactive identification of products approaching support termination, replacement planning processes, risk mitigation strategies during transition periods, and validation that legacy systems receive appropriate security monitoring until replacement.
Logging, monitoring, and incident detection evidence trails
Security event logging requirements vary across regulatory frameworks, but most agencies appear to expect comprehensive log collection, centralized analysis capabilities, and correlation techniques for identifying potential security incidents. Evidence requirements include log retention policy documentation, analysis procedure implementation, and monitoring system integration proof.
Centralized logging evidence is particularly important for demonstrating security monitoring effectiveness across distributed technology environments. Organizations must show how logs from different systems are collected, normalized for analysis, correlated for incident detection, and retained for investigation purposes. Log management system integration influences how regulators evaluate overall monitoring capabilities.
Log retention periods appear to be extending as agencies recognize the importance of historical data for incident investigation and trend analysis. Organizations must balance storage costs with regulatory expectations for extended log availability, requiring cloud-based storage solutions that provide cost-effective long-term retention capabilities.
Incident detection and response documentation requires detailed evidence of detection procedures, analysis workflows, containment strategies, and recovery activities. Agencies examine how organizations identify security incidents, escalate response efforts, coordinate with external parties, and document lessons learned for future improvement. Response documentation completeness and accuracy influence regulatory assessments significantly.
Monitoring effectiveness metrics include detection time measurements, false positive rate tracking, and analyst response time analysis. Regulators expect organizations to demonstrate continuous improvement in monitoring capabilities through measurable performance indicators that show security program maturation over time.
Encryption implementation and data protection operational proof
Encryption evidence requirements now extend beyond policy documentation to include key management procedures, implementation testing validation, and effectiveness measurement through operational monitoring. Agencies seem particularly interested in how organizations protect encryption keys while maintaining that encrypted data remains accessible for legitimate business operations.
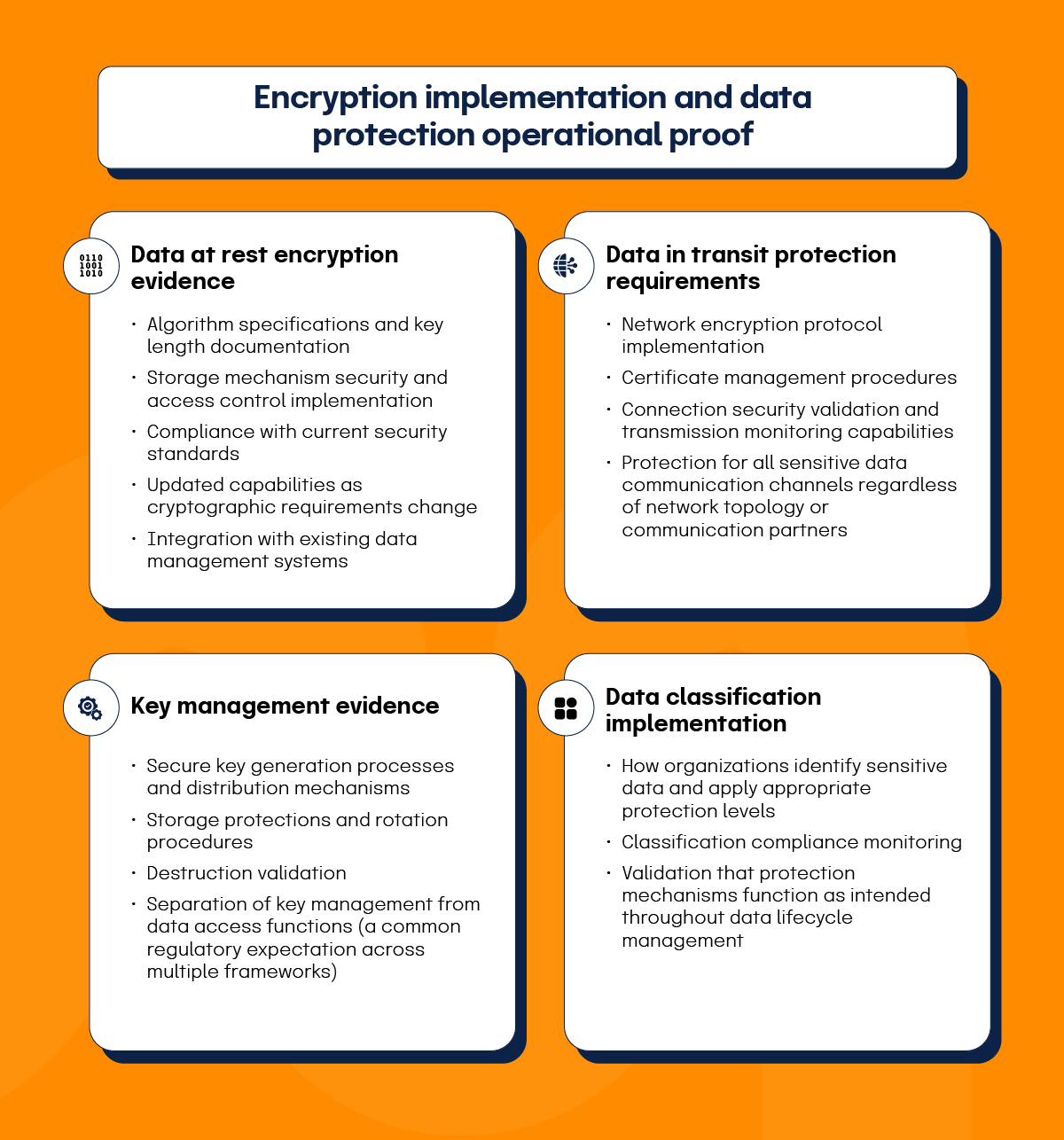
Data at rest encryption evidence
Organizations must provide detailed documentation covering:
Data in transit protection requirements
Similar detailed evidence is required, including:
Key management evidence
This area receives particular attention during regulatory examinations. Organizations must demonstrate:
Data classification implementation
Evidence must demonstrate appropriate encryption based on information sensitivity levels:
Administrative and governance control evidence
Administrative controls provide the governance foundation that confirms technical security measures operate within appropriate organizational frameworks. Regulatory agencies expect comprehensive evidence demonstrating that administrative controls create measurable improvements in security program effectiveness rather than just satisfying procedural requirements.
Board oversight and risk management integration documentation
Board-level cybersecurity oversight evidence appears increasingly important across regulatory frameworks as agencies recognize governance failures as contributing factors in major security incidents. Regulators expect detailed documentation demonstrating active board engagement with cybersecurity risks rather than passive receipt of status updates from management.
Meeting documentation standards
Meeting documentation must show:
Risk reporting expectations
Risk reporting frequency and content specificity influence regulatory assessments of board oversight effectiveness:
Board cybersecurity expertise
Board cybersecurity expertise documentation is increasingly relevant as regulators examine whether board members possess sufficient knowledge to provide effective oversight. Organizations must demonstrate how board members develop cybersecurity competency through:
Decision documentation requirements
Decision documentation is particularly important for:
Security awareness training program effectiveness and measurement
Training program evidence requirements emphasize measurable effectiveness improvements rather than completion rate tracking alone. Agencies expect organizations to demonstrate that security awareness initiatives produce behavioral changes and risk reduction rather than just satisfying training hour requirements or compliance obligations.
Training program evidence requirements emphasize measurable effectiveness improvements rather than completion rate tracking alone. Agencies expect organizations to demonstrate that security awareness initiatives produce behavioral changes and risk reduction rather than just satisfying training hour requirements or compliance obligations.
Role-based training requirements
Role-based training documentation is particularly important for demonstrating that awareness programs address specific risks faced by different employee populations:
Modern training program approaches
Organizations are shifting away from standard “off-the-shelf” security awareness programs to more targeted approaches:
Phishing simulation and behavioral improvement
Phishing simulation results provide valuable evidence of training program effectiveness:
Competency assessment evidence
Competency assessment includes:
Continuous program improvement
Training program modification documentation should demonstrate continuous improvement based on:
Third-party risk management and vendor oversight evidence
Vendor risk assessment documentation requires detailed analysis of third-party security capabilities, incident history, and ongoing monitoring procedures rather than contractual compliance verification alone. Agencies expect organizations to evaluate vendor security practices continuously and maintain evidence of supplier cybersecurity posture throughout relationship lifecycles.
Contract security provisions evidence must include:
Generic contractual language is insufficient; provisions must address specific risks posed by vendor relationships and provide mechanisms for ongoing security validation.
Ongoing vendor monitoring evidence is increasingly important as agencies recognize that initial security assessments do not reflect current supplier capabilities. Organizations must demonstrate continuous monitoring of vendor security performance through automated assessment tools, periodic manual reviews, or third-party security validation services.
Supply chain cybersecurity evidence includes documentation demonstrating how organizations evaluate and monitor their vendors’ suppliers and business partners. Evidence must show an understanding of extended supply chain risks and implementation of appropriate mitigation strategies that address multi-tier supplier relationships.
Vendor incident response coordination evidence is important for demonstrating how organizations handle security incidents involving third-party suppliers. Documentation must show clear notification procedures, coordination workflows, and recovery activities that address vendor-related security events while maintaining business continuity.
Business continuity planning and disaster recovery testing records
Comprehensive testing program requirements
Business continuity testing evidence requires regular validation of different scenario types rather than annual compliance exercises alone. Agencies expect comprehensive testing programs that include:
Recovery time measurement documentation
Recovery time measurement documentation is particularly important for demonstrating that business continuity capabilities align with operational requirements. Organizations must show:
Tabletop exercise documentation
Tabletop exercise documentation is valuable for demonstrating decision-making capabilities during simulated crisis situations. Evidence must show:
Plan update and maintenance records
Plan update records must demonstrate that business continuity procedures remain current with:
Static plans are insufficient; regulators expect evidence of continuous improvement and validation.
Real incident recovery documentation
Real incident recovery documentation, when available, is particularly valuable for validating business continuity effectiveness in crisis situations. Organizations that have experienced security incidents must demonstrate:
Building an evidence-ready compliance program
Organizations must now create compliance programs around continuous evidence generation rather than periodic documentation collection. The shift toward evidence-based regulation requires systematic approaches to capturing, validating, and presenting operational proof of security control effectiveness.
Ready to assess your current evidence collection capabilities and identify gaps?

Implementing automated evidence collection systems
Automated evidence collection is essential for meeting modern compliance demands, which exceed what manual processes can support in terms of volume, frequency, and consistency. The most effective method integrates with existing security infrastructure, such as SIEMs, vulnerability scanners, and identity platforms, to collect evidence as part of routine operations.
As regulators shift toward continuous monitoring, real-time evidence collection is critical for demonstrating ongoing control effectiveness. Cloud-based platforms support this need by offering scalable, accessible, and auditable storage with built-in retention and access controls.
Hyperproof enables automated evidence collection through Hypersyncs, data connectors that automatically pull evidence from 70+ platforms like CloudTrail logs, IAM policies, and access configurations across accounts. Hypersyncs eliminate the need for manual screenshots and ensure consistent, audit-ready records.
Here’s an example of how easy it is to set up a Hypersync in Hyperproof:
First, you’ll navigate to Automations and select + Create Hypersync.
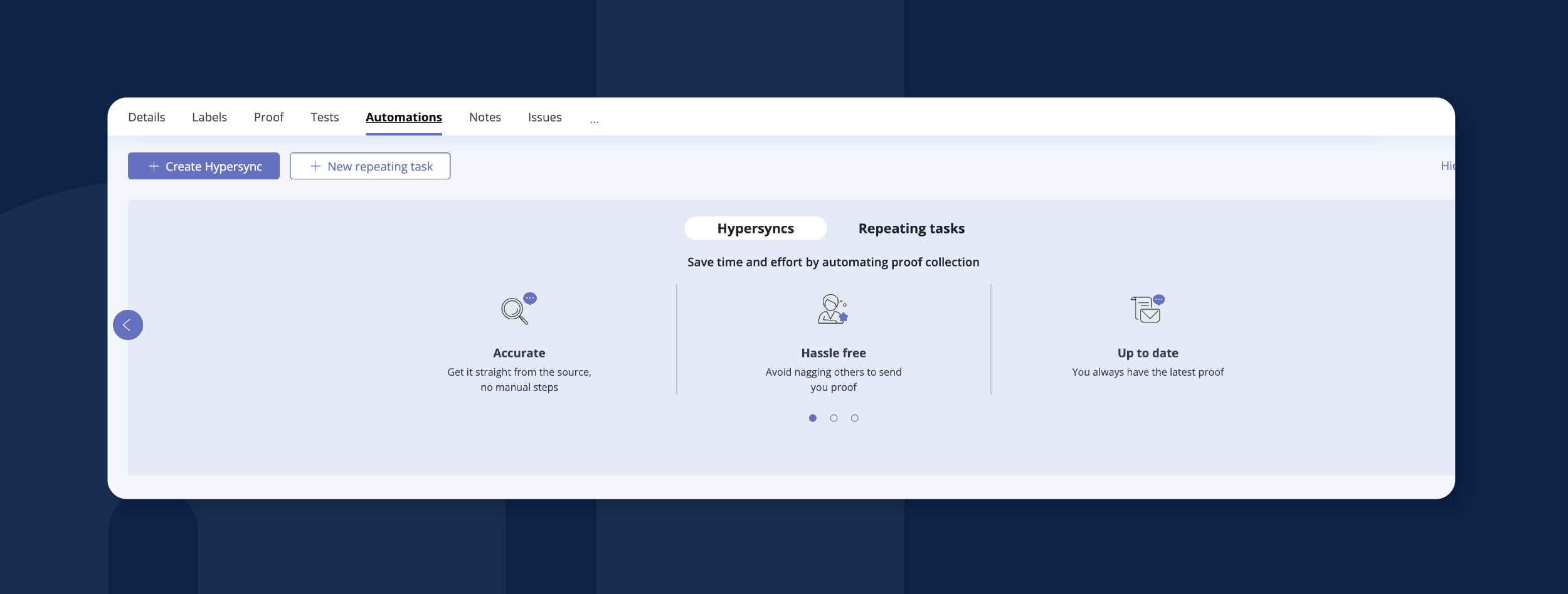
Next, choose your app of choice from the application library.

In this example, we’ve selected AWS. You will reuse your existing credentials to create your Hypersync, so select the Use the current account button. Click Next.
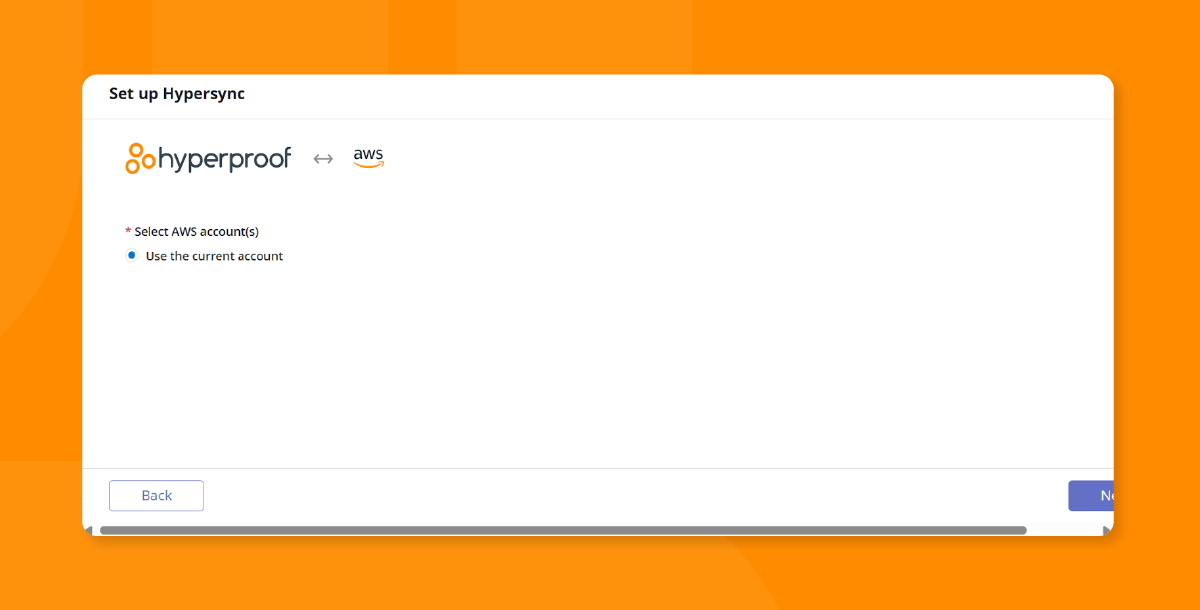
Next, select the AWS Service you would like to automatically sync to Hyperproof. In this example, we are choosing IAM (Identity Access Management).
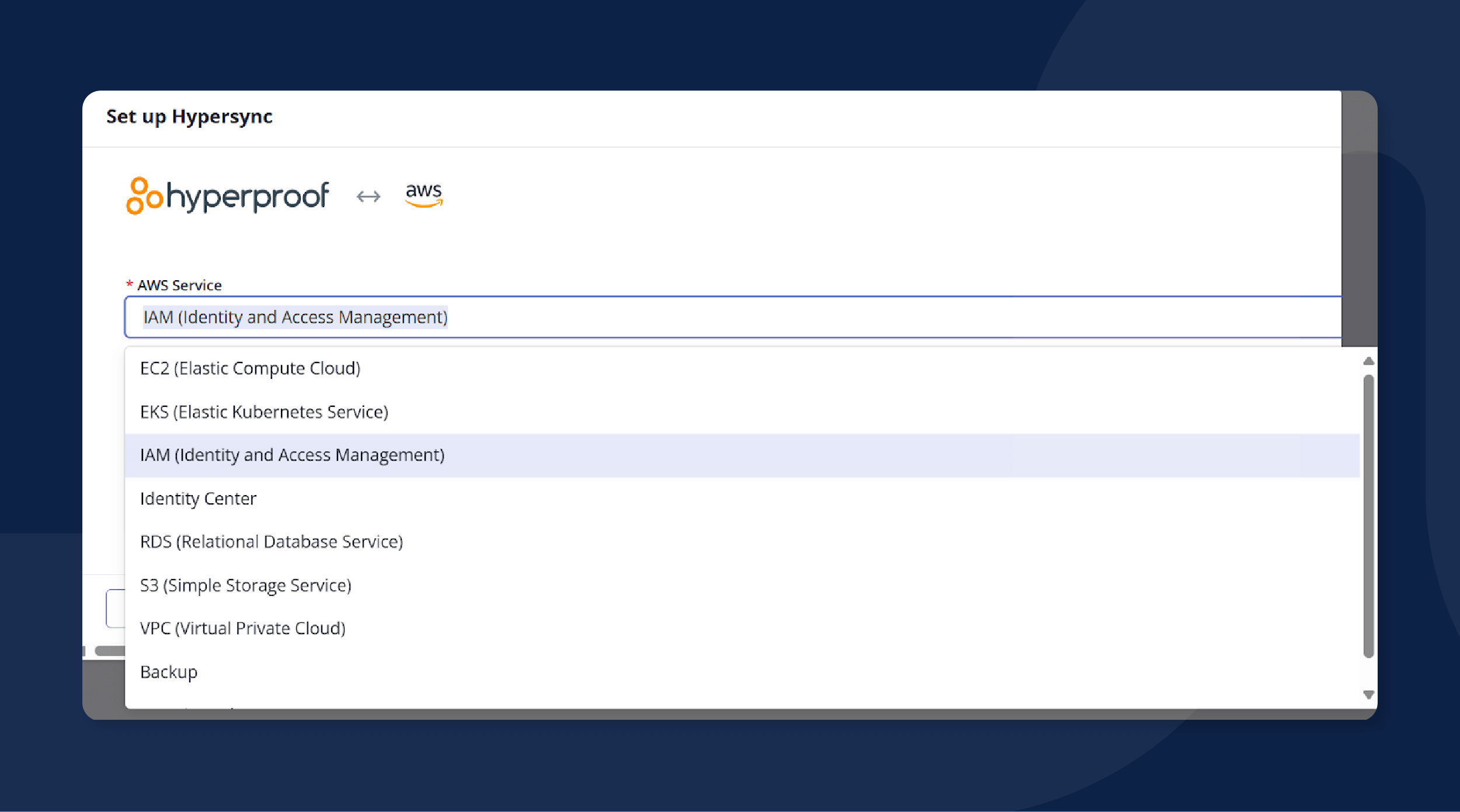
Next, select the proof you would like to sync from the Proof dropdown. In this example, we’ve chosen Users, Groups, Roles, and Policies.
Next, select the cadence you would like to automatically sync this proof. You can select from Day, Week, Month, or establish your own custom cadence. Click Next to continue.
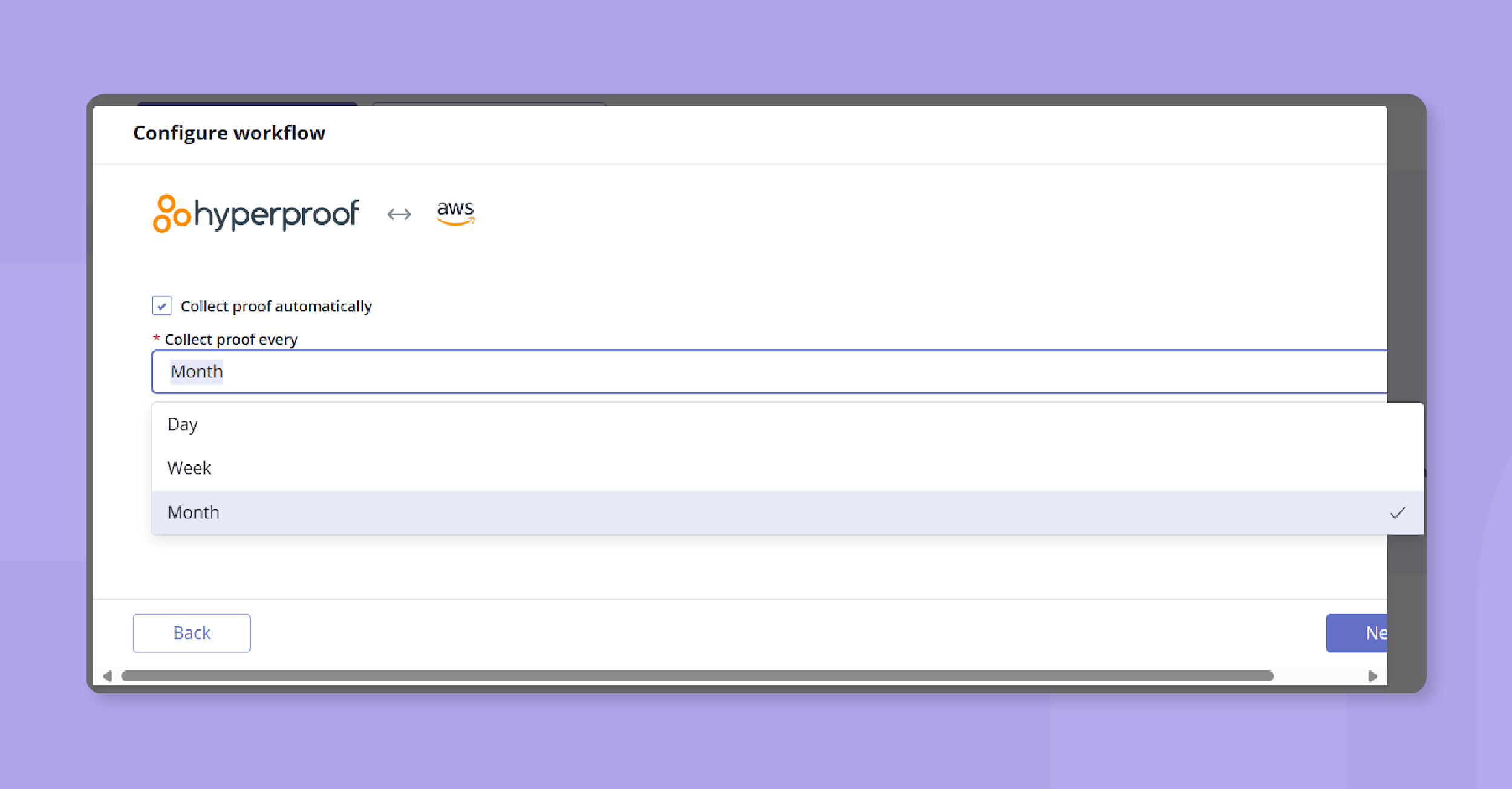
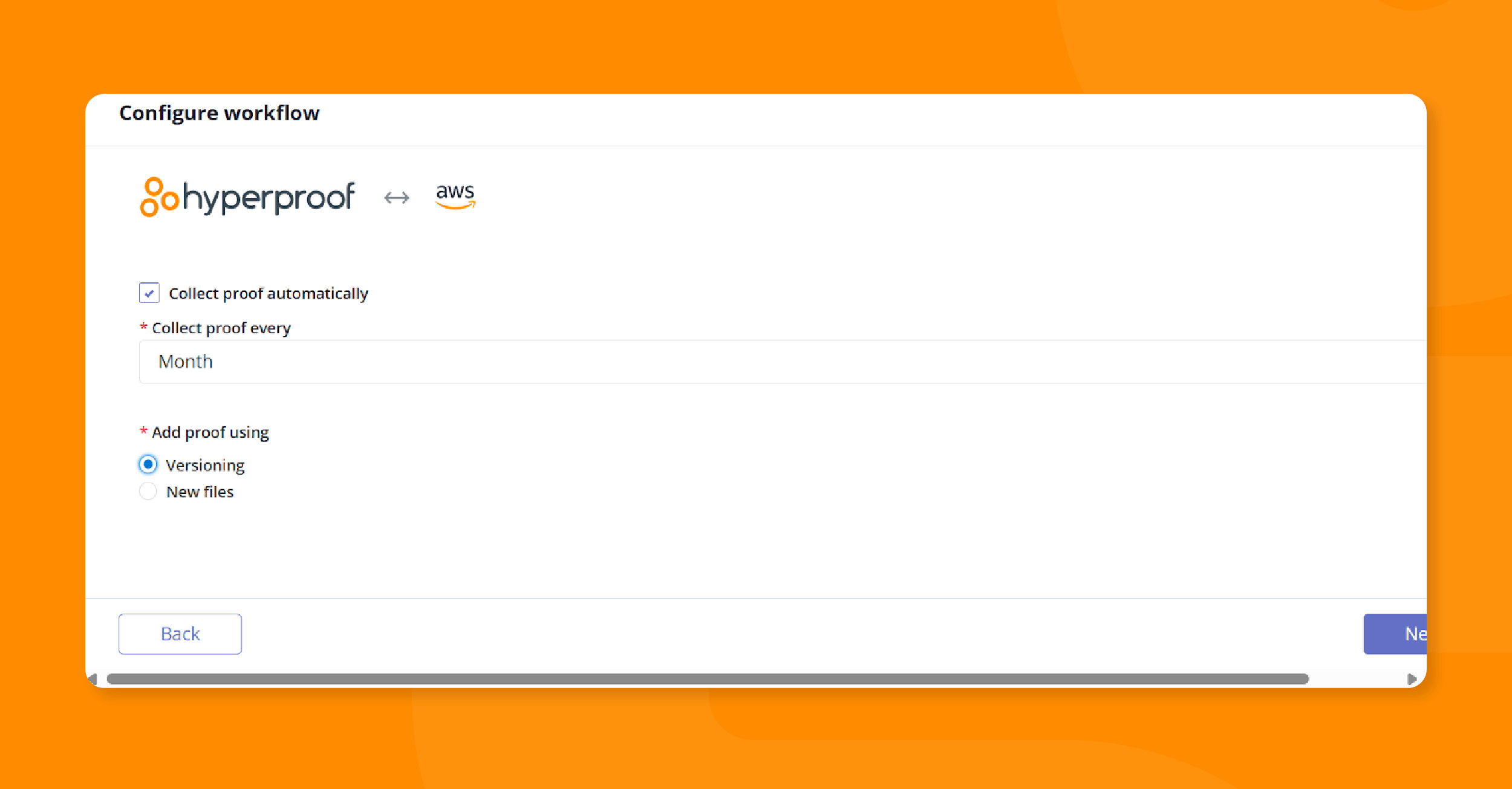
Next, specify whether you want to add proof using versioning or new files by selecting the Versioning or New files buttons. Click Next to continue.
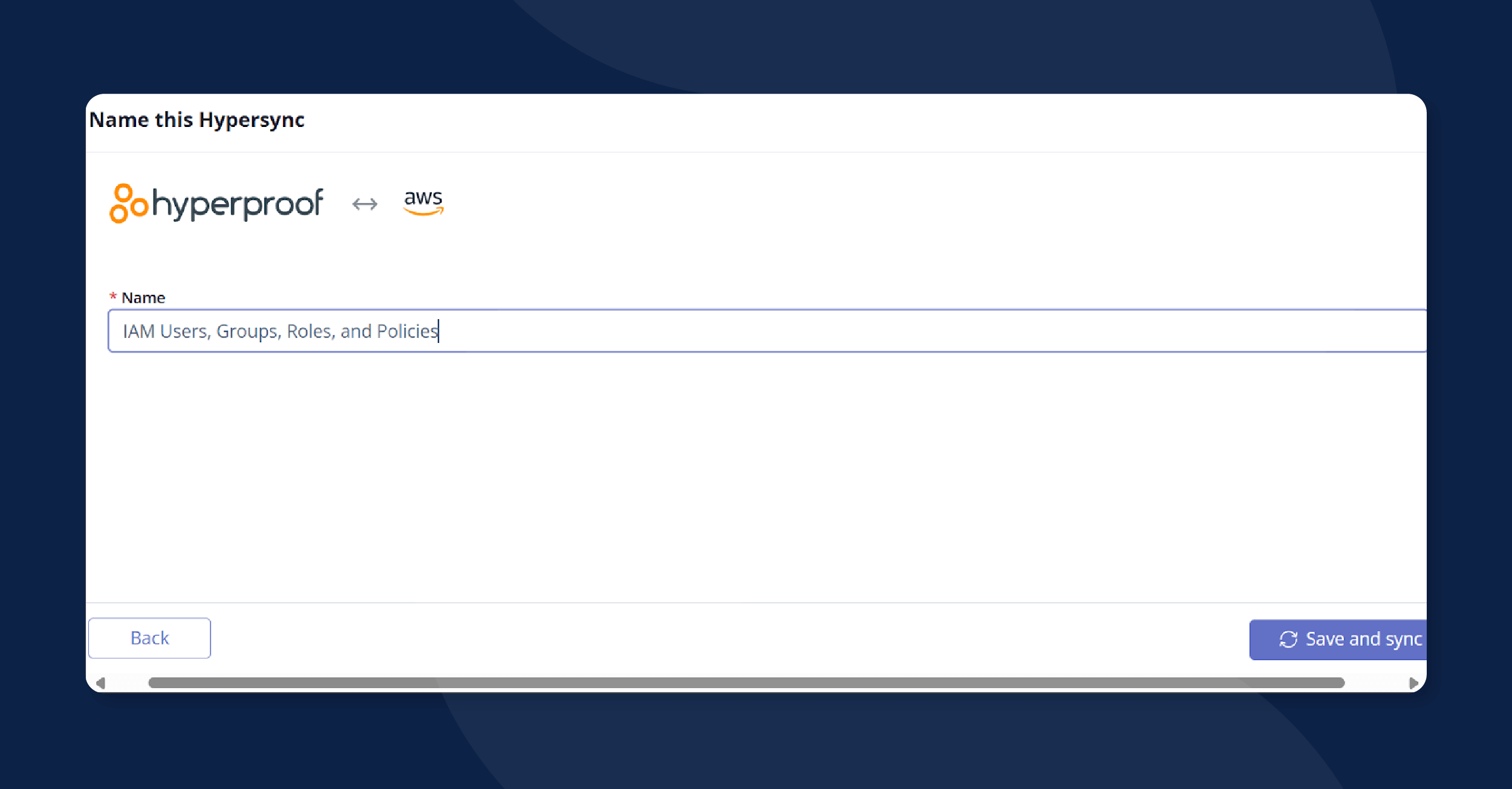
Finally, you’ll name your Hypersync in the Name field. Click Save and sync to run your first sync and test your Hypersync’s setup.
This automated approach scales beyond what manual processes can achieve. Organizations need to establish the initial connection between Hyperproof and their security tools once, after which multiple Hypersyncs can be configured for different controls.
Creating audit-ready documentation frameworks
Documentation frameworks should be designed with regulatory examination requirements as primary considerations rather than internal compliance needs alone. Evidence organization and presentation can significantly influence how regulators perceive compliance programs during investigations and enforcement proceedings.
Standardized evidence packages
Standardized evidence packages for different regulatory scenarios may improve examination efficiency and outcomes by:
Version control and change tracking
Version control and change tracking are important for maintaining evidence integrity throughout retention periods. Regulators may examine:
Access control implementation
Access control implementation for evidence repositories must balance:
Retention policy development
Retention policy development must exceed minimum regulatory requirements to account for:
Continuous monitoring and evidence validation processes
Evidence validation and testing
Evidence validation and testing are necessary to confirm that automated collection systems:
Gap identification procedures
Gap identification procedures are important for discovering areas where:
Quality assurance processes
Quality assurance processes for evidence collection must include:
Continuous improvement procedures
Continuous improvement procedures must include feedback mechanisms from:
Performance metrics for evidence collection
Performance metrics for evidence collection systems include:
Preparing for regulatory examinations and investigations
Examination preparation requires systematic approaches beyond evidence organization alone. Organizations need examination response procedures, role assignments, and personnel training on regulatory interaction protocols to maintain effective cooperation during investigations.
Evidence presentation formats must be tailored to specific regulatory agency preferences and examination procedures. Different agencies have varying expectations for evidence organization, delivery methods, and supporting documentation that accompany primary evidence submissions.
Response timeline management during examinations requires pre-positioned evidence that can be rapidly produced without extensive manual compilation. Organizations need systems capable of generating requested evidence packages quickly while maintaining quality and completeness standards.
Legal coordination is important for managing examinations that may lead to enforcement action. Organizations must balance transparency and cooperation requirements with appropriate legal protections during evidence production and examiner interactions.
Post-examination follow-up procedures must include evidence gap analysis, remediation planning, and system improvements based on examination experience. Each regulatory interaction provides valuable insights for improving evidence management capabilities and regulatory relationship management.
Need a structured approach to managing regulatory examinations?

Continuous evidence collection and controls monitoring is becoming the norm
Cybersecurity compliance has shifted from checking boxes to proving control effectiveness through real-world, measurable outcomes. Federal regulators now require operational evidence, like logs, forensic artifacts, and continuous monitoring data, to demonstrate that controls are functioning as intended, not just documented.
This shift follows major breaches where organizations appeared compliant on paper but failed operationally. As a result, regulators across frameworks are aligning around common expectations: automated evidence collection, continuous monitoring, and quantifiable results.
To succeed, organizations must move beyond static documentation and invest in automated evidence systems. Hyperproof addresses these needs with Hypersyncs, API-based integrations that pull fresh, auditable data from supported systems on customizable schedules. The platform generates standardized reports and applies automated control testing to verify evidence quality and compliance alignment.
With Hyperproof, you can streamline compliance while meeting regulators’ demands for proof of operational effectiveness. Learn how Hyperproof reduces audit stress and strengthens your regulatory posture.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












