What is HIPAA Compliance: Why It Matters and How to Obtain It

What is HIPAA compliance?
HIPAA compliance is the process of adhering to the requirements of The Health Insurance Portability and Accountability Act (HIPAA) of 1996 Security Rule. This act established standards for protecting individuals’ electronic personal health information (PHI) that are created, received, used, or maintained by a covered entity.
Examples of PHI include:
- Health records and histories
- Medical bills
- Lab results
- Other identifiable health information
Examples of covered entities include:
- Healthcare providers
- Health plans
- Healthcare clearinghouses
Although the rule was passed into law in 1996, businesses today need to pay close attention. In 2017, the OCR announced an initiative to investigate HIPAA breaches affecting 500 people or fewer more widely. While small breaches can occur at organizations of any size, the announcement was a reminder to those at the small end of the scale, that when it comes to a HIPAA breach, size does not matter.
To learn more about HIPAA, read our comprehensive guide
Related: Key Strategies For Meeting Data Compliance Regulations
Does your business need to be HIPAA compliant?
If your business currently handles PHI or wants to work with companies in the healthcare field, you will need to be HIPAA compliant and be able to show that your business has protections for PHI in place and can safely and securely handle the data that your clients are trusted with.
Covered entities are the main group subject to HIPAA requirements. Covered entities include a wide range of different healthcare organizations and individuals.
Healthcare providers
The first group, healthcare providers, includes providers such as doctors, psychologists, nursing homes, and pharmacies. However, these groups are only covered if they transmit any information electronically in connection with a transaction that HHS has adopted as a standard.
Health plans
The second group, health plans, covers health insurance companies, health maintenance organizations (HMOs), company health plans, and government programs that pay for healthcare, such as Medicare, Medicaid, and military/veteran programs.
Healthcare clearinghouses
The third and final group, healthcare clearinghouses, includes organizations that process nonstandard health information received from other entities into a standard form (i.e., standard electronic format or data content), or vice versa.
HIPAA extends to business associates
Additionally, the law allows covered entities to disclose PHI to business associates as long as there is a contract in place that establishes what the business associate is going to do with the data and requires them to protect the privacy and security of the PHI they’re given access to.
Health and Human Services (HHS) defines a HIPAA business associate as a person or entity performing functions or activities that involve using or disclosing PHI on behalf of or providing service to a covered entity. In other words, if your company performs work involving the handling or disclosure of PHI for a customer who falls under HIPAA regulations, you are considered their business associate (BA). Typical functions business associates perform include payment processing or activities concerning some aspect of healthcare operations.
If you are a SaaS company or cloud service provider (CSP) who works with or wants to work with businesses that handle PHI, you will need to enter into a HIPAA-compliant business associate agreement (BAA) with your customer and must maintain compliance with all applicable HIPAA rules. If you’re a bit foggy on business associate agreements and your compliance responsibilities under the current HIPAA rules, check out this article below to learn how to stay compliant when partnering with companies that handle PHI.
Featured article: Business Associate Agreement: It’s Required for SaaS Companies Who Handle ePHI
HIPAA auditing and enforcement
The Health and Human Services Office of Civil Rights (OCR) audits organizations to ensure they are following HIPAA. In 2016, the OCR began the second phase of its audit program and collected covered entities’ contact information. They also collected questionnaires about each covered entity’s size, type, and operations and used them to create pools of potential organizations to audit. Auditees are chosen at random by OCR.
What are the consequences of violating HIPAA?
If the OCR discovers a HIPAA violation, it can issue both financial penalties and corrective action plans. Financial penalties for HIPAA violations are tiered — the penalty is based on the covered entity’s knowledge of the breach.
Violations start at Tier 1, which indicates a violation that the covered entity was unaware of and couldn’t have realistically avoided, all the way to Tier 4, which indicates a violation the covered entity knew about but made no attempt to correct. The fines for each tier are adjusted annually to account for inflation. In 2019, the fines for each tier were:
- Tier 1: Minimum fine of $117 per violation up to $58,490
- Tier 2: Minimum fine of $1,170 per violation up to $58,490
- Tier 3: Minimum fine of $11,698 per violation up to $58,490
- Tier 4: Minimum fine of $58,490 per violation up to $1,754,698
What are the key requirements of HIPAA?
The OCR takes intentional violations of HIPAA very seriously, as they demonstrated in 2019 when they fined the University of Rochester Medical Center $3M for HIPAA violations, including failing to encrypt mobile devices. A solid compliance program can protect you even in the event that you unintentionally violate HIPAA. A thorough and continually updated compliance program can mean the difference between a bump in the road and a potentially business-ending financial penalty.
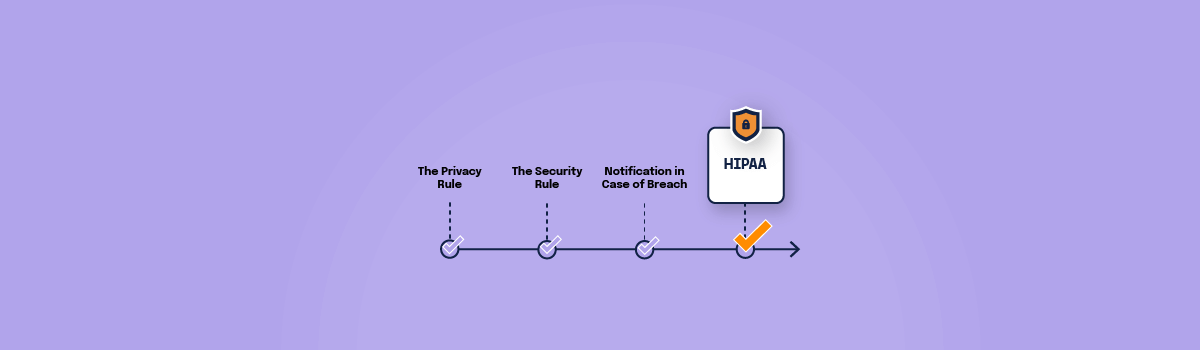
Covered entities must be in compliance with three core requirements. All controls and safeguards HIPAA-compliant organizations have in place ultimately serve to help them meet these three requirements.
The privacy rule
HIPAA ensures the privacy of PHI. HIPAA’s privacy rule establishes standards for protecting medical records and other PHI and sets limits and conditions on using and disclosing PHI without patient authorization. This rule also gives patients the right to a copy of their health records and ask providers to make corrections to their PHI.
The security rule
Businesses that HIPAA covers must establish security standards that protect electronic PHI (ePHI). These standards cover any ePHI that is created, received, used, or maintained by a covered entity and, in turn, their business associates. According to OCR, the security rule “requires appropriate administrative, physical and technical safeguards to ensure the confidentiality, integrity, and security of electronically protected health information.” This rule is broken down and discussed further in the next section.
Notification in case of breach of unsecured PHI
While the safeguards required by the security rule are designed to help organizations avoid breaches, if a HIPAA-compliant organization does experience one, they are required to notify certain parties — including individuals, the media, and the Secretary of breaches of unsecured information — depending on the type and size of the breach.
OCR defines a breach as “an impermissible use or disclosure under the Privacy Rule that compromises the security or privacy of the protected health information.” So breaches include not just those caused by hackers or malware, but also by employees inappropriately disclosing information or leaving it where unauthorized users can see.
How to satisfy the HIPAA security rule

The HIPAA security rule has three parts:
- Technical safeguards
- Physical safeguards
- Administrative safeguards
These parts have their own set of specifications, all of which are either considered required or addressable.
Keep in mind that a specification being marked as addressable does not mean you can simply ignore it — it means there is some flexibility with safeguard implementation. If an addressable safeguard isn’t reasonable for an organization to implement, they can introduce an alternative or not implement it at all. However, you will need to document that decision and be prepared to justify it during an audit.
Technical safeguards
This category covers the technology used to protect and access ePHI. When implementing these safeguards, organizations can implement whatever mechanisms make the most sense for them, except for encrypting ePHI (all ePHI, whether being stored or transmitted, must be encrypted to NIST standards once it leaves your internal servers).
These technical safeguards dictate that covered entities must:
- Implement a means of access control
- Introduce a mechanism to authenticate ePHI
- Implement tools for encryption and decryption
- Introduce activity logs and audit controls
- Facilitate automatic log-off of PCs and devices
Physical safeguards
The HIPAA physical safeguards cover physical access to ePHI wherever it is stored, whether it’s in a data center, cloud-based storage, in a covered entity’s physical location, or anywhere else. They lay out the standards for physically safeguarding ePHI.
The physical safeguards include requirements for:
- Facility access controls
- Workstation use and positioning policies
- Mobile device policies and procedures
- Hardware inventory
Administrative safeguards
These pertain to the policies and procedures that govern your organization’s conduct and integrate the privacy and security rules into one set of policies and actions. HIPAA requires that a dedicated security officer and privacy officer be assigned to implement these safeguards.
The administrative safeguards include requirements for:
- Conducting risk assessments
- Introducing a risk management policy
- Training employees on security
- Developing a contingency plan
- Testing of contingency plan
- Restricting third-party access
- Reporting security incidents
How does HIPAA fit into your overall compliance program?

Although HIPAA covers a very specific type of information, the controls and safeguards required to protect ePHI are similar to those in other cybersecurity compliance frameworks. If you already have a robust information security program, you may already meet certain HIPAA requirements.
Inversely, if you are already HIPAA compliant and are looking to achieve compliance with other data protection standards such as SOC 2, ISO27K, or CCPA, your HIPAA-compliant policies and safeguards will likely give you a headstart. Access control, mobile device usage policies, risk management policies, and employee training are just a few examples of HIPAA compliance requirements that overlap with requirements in other data security frameworks.
Utilizing dedicated compliance software such as Hyperproof allows you to map evidence to more than one control/requirement, re-use evidence from past audits and avoid duplicating efforts.
When should you consider HIPAA compliance?
If you want to do business with HIPAA-covered entities, you need to become HIPAA compliant before accepting or working with any PHI from clients. If there is a data breach or one of your clients is audited and they identify you as a business associate, the OCR will expect you to be able to demonstrate HIPAA compliance. As we discussed earlier, willful noncompliance is punished, and if you accept PHI from a covered entity without compliance, you could face steep penalties.
If you want to eventually do business with covered entities, you should be pursuing compliance now; don’t wait until you’re courting a client to think about it. In all likelihood, if you’re not compliant, one of your competitors is.
HIPAA vs. HITRUST: What’s the difference?
Unlike some data security frameworks, no HIPAA certification is obtained after an OCR audit: you are simply either found to be in or out of compliance. However, the Health Information Trust Alliance (HITRUST), a group of healthcare industry leaders, has developed a certification system that helps organizations become compliant with HIPAA and other regulations called the Common Security Framework (CSF).
The CSF is a standardized, voluntary compliance framework that ensures compliance with HIPAA and other frameworks, such as PCI and NIST, when organizations become compliant.
CSF certification offers organizations the chance to show that they take data security compliance seriously and an easy way to prove to clients that they are HIPAA compliant. However, obtaining the HITRUST CSF certification is time-consuming and expensive, so unless their potential clients require it, many organizations opt out of obtaining the certification.
Tips for getting started with HIPAA

If your business is just starting its compliance journey, or if HIPAA compliance is new to your organization, you should have a plan in place for determining what security measures need to be put in place, how your organization is going to put those measures and controls in place, and what controls you plan to test and monitor activities you’ll need to do regularly. Don’t wait for an issue to crop up — be proactive about completing the activities that will keep your data secure.
Develop an incident response plan
If your organization does experience a data breach, you are required to notify certain parties — including individuals, the media, and the Secretary of breaches of unsecured information — depending on the type and size of the breach.
Related: How to Create a Cybersecurity Incident Response Plan
Record audit trails
As you complete internal and external audits, keep records of those activities: what documentation is being pulled, what processes you’re evaluating, and what the findings of each audit are. An audit is a point-in-time snapshot of your compliance process, and keeping track of your discoveries can tell you what you need to work on and what processes are working as intended.
Have dedicated staff and resources
To be as successful as possible, you need to have staff and resources that are dedicated to compliance. It can be tempting for startups, small businesses, or companies that don’t see the value in proactive compliance programs to tack compliance responsibilities onto a current employee’s responsibilities. Still, a successful compliance program requires dedicated and knowledgeable employees and resources to back them up.
Get leadership’s buy-in
Like any program or corporate value, compliance must come from the top down to succeed. Having leadership’s buy-in is invaluable and will make a world of difference. Having their buy-in will mean your compliance program is more likely to have the dedicated staff and resources we discussed above and to be a priority for everyone in the company, not just the compliance staff.
Case study: Learn the benefits of automating administrative tasks and maintaining compliance at scale.
Maintaining compliance with HIPAA
As with any other compliance framework, HIPAA compliance isn’t something you can achieve once and move on from. Cybersecurity threats are constantly evolving, so if you don’t prioritize compliance, your compliance program will quickly fall behind and fail to protect your business. Once you achieve compliance, you need a maintenance plan.
Using Hyperproof to become (and stay) HIPAA compliant
Any business handling PHI, whether they’re a health insurance company, a data storage company, an insurance broker, or a part of any of the other many industries that touch PHI, needs to understand HIPAA and have the required processes and protections in place to ensure they are safely and securely handling that data.
If you need to ensure that your organization is compliant with HIPAA, Hyperproof’s compliance operations software can make your compliance journey simpler and faster. Hyperproof allows you to easily see the requirements for HIPAA (as well as those for other common cybersecurity standards such as SOC 2 and ISO 27001), create or update internal controls, store, tag, and organize compliance evidence, and automate many repetitive administrative tasks associated with the audit process.
If you’re interested in learning more about ways to manage your HIPAA compliance process efficiently, we’d love to talk.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?











