With a cyber attack being attempted every 40 seconds and ransomware attacks increasing at a rate of 400% year over year, it’s no wonder your organization has to take security seriously. But do you feel confident that you’ve allocated an appropriate amount of resources towards your security program?
Do you know which information assets and systems are most vulnerable? And have you calculated the potential financial costs you’d incur if key systems were to go down? In our modern, highly volatile cyber risk environment, these are critical questions for every organization to answer. Getting the answers will require your organization to become proficient in conducting an IT risk assessment.
What is an IT risk assessment?

IT security risk assessments focus on identifying the threats facing your information systems, networks, and data and assessing the potential consequences you’d face should these adverse events occur. Risk assessments should be conducted on a regular basis (e.g., annually), and whenever major changes occur within your organization (e.g., acquisition, merger, re-organization, when a leader decides to implement new technology to handle a key business process, when employees suddenly move from working in an office to working remotely).
Not only is IT risk assessment important for protecting your organization and right-sizing your security investment, but it may also be mandatory. Some information security frameworks, such as ISO 27001 and CMMC, actually require risk assessments to be conducted in specific ways and documented on paper in order for your organization to be considered “compliant.”
IT risk assessments are a crucial part of any successful security program. Risk assessments allow you to see how your organization’s risks and vulnerabilities are changing over time, so decision-makers can put appropriate measures and safeguards in place to respond to risks appropriately.
Is your compliance program effective for the current regulatory landscape? Find out what are the key elements you need with our free guide.

Why conduct an IT risk assessment?

For some businesses, especially small companies, it might seem like a big enough job just to put a team in place to develop and manage information security plans without the added work of proactively looking for flaws in your security system. But in reality, an IT risk assessment is something you can’t afford to skip over. Information security risk assessments serve many purposes, some of which include:
Cost justification
An IT risk assessment gives you a concrete list of vulnerabilities you can take to upper-level management and leadership to illustrate the need for additional resources and a budget to shore up your information security processes and tools.
It can be difficult for leadership to see why you need to invest more money into information security practices that, from their point of view, are working just fine. Showing them the results of an information security risk assessment is a way to drive home that the risks to your sensitive information are always changing and evolving, so your infosec practices need to evolve with them.
Productivity
If you are consistently performing risk assessments, you will always know where your information security team should dedicate their time, and you will be able to use that time more effectively. Instead of always reacting to a problem after it has caused a security event, you’ll spend that time fixing vulnerabilities in your security practices and processes so you can avoid the issue in the first place. IT risk assessments also show you which risks require more time and attention, and which risks you can afford to divert fewer resources to.
Breaking barriers
Information security should ideally involve two groups: senior management and IT staff. Senior management should dictate the appropriate level of security, while IT should implement the plan to help achieve that level of security. Risk assessments bring these two groups together. They give IT staff a tool to open up conversations with management about infosec risks the organization faces and how the company can achieve the highest level of security possible.
Communication
Above all else, risk assessments improve information security by facilitating communication and collaboration throughout an organization.
First, to properly assess risk within a business, the IT security staff will need to have conversations with all departments to understand,
- The operations of each department
- How employees are using different systems
- How information flows between different systems
This gives the security team a chance to learn about other peoples’ positions, challenges, and contributions to the information security of the business as a whole.
Second, risk assessments provide IT and compliance teams a chance to communicate the importance of information security to people throughout the entire organization and to help each employee understand how they can contribute to security and compliance objectives.
Changes in many different parts of a business can open it up to different risks, so it’s important for the people responsible for information security to understand if and when the business’s processes or objectives change.
As we said earlier, the more people and information sources you can include, the better the output will be. But it’s important to know that any company can perform an information security risk assessment and find areas for improvement, even if you don’t have extensive IT or compliance teams.
How is an IT risk assessment done?
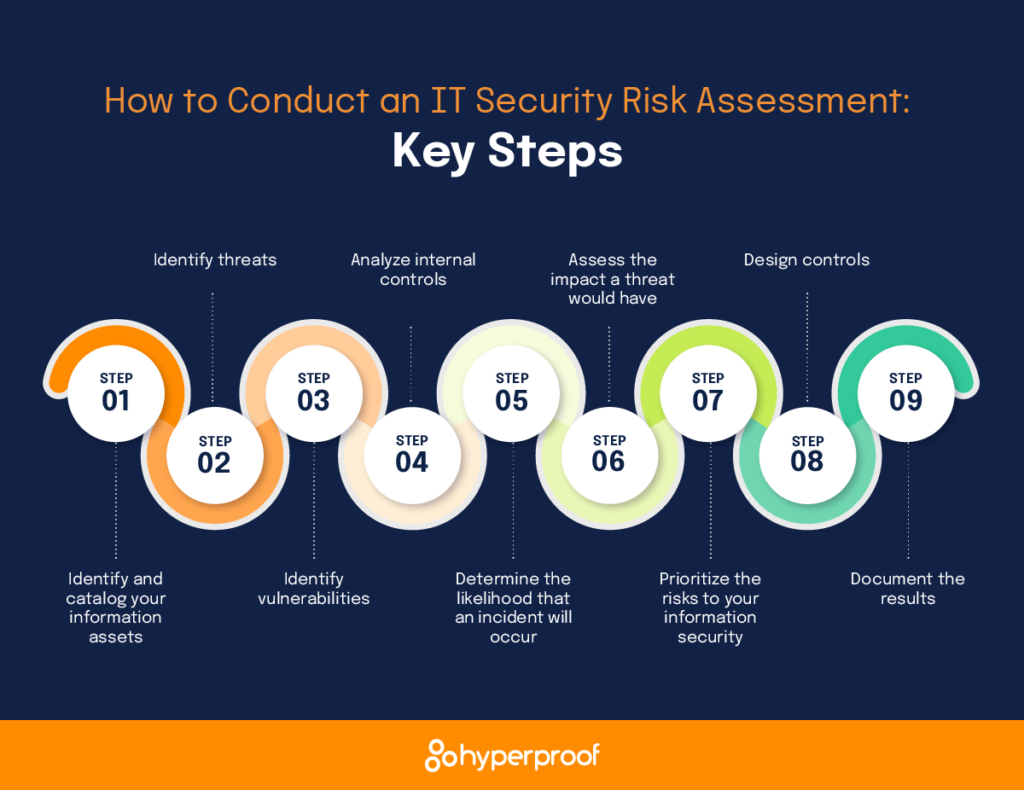
You can perform two categories of risk assessments, but the most effective approach is to incorporate aspects of both of them.
Quantitative risk assessments, or assessments that focus on numbers and percentages, can help you determine the financial impacts of each risk.
Qualitative risk assessments help you assess the human and productivity aspects of a risk.
Both of these categories have value, and both of them will allow you to communicate risk with different types of people. For example, your legal and financial teams will likely be most interested in the numbers, while your operations teams, such as sales and customer service, will be more concerned about how a security event would affect their operations and efficiency.
Following these steps will help you conduct a basic information security risk assessment and give you the tools you need to begin building a consistent process for identifying key business risks.
1. Identify and catalog your information assets
The first step in a risk assessment is to make sure that you have a comprehensive list of your informational assets. It’s important to remember that different roles and different departments will have different perspectives on what the most important assets are, so you should get input from more than one source here. The most important information asset for salespeople might be your company’s CRM. At the same time, IT likely sees the servers they maintain as a higher priority, while HR’s most important information asset is confidential employee information.
Once you have identified all of your information assets and key stakeholders within all departments, you’ll need to classify these data assets based on their sensitivity level as well as the strategic importance of the asset to the organization. To get accurate and complete information, you’ll need to talk to the administrators of all major systems across all departments.
Below is a sample data classification framework. For more information on how to classify data, please refer to this article from Sirius Edge.
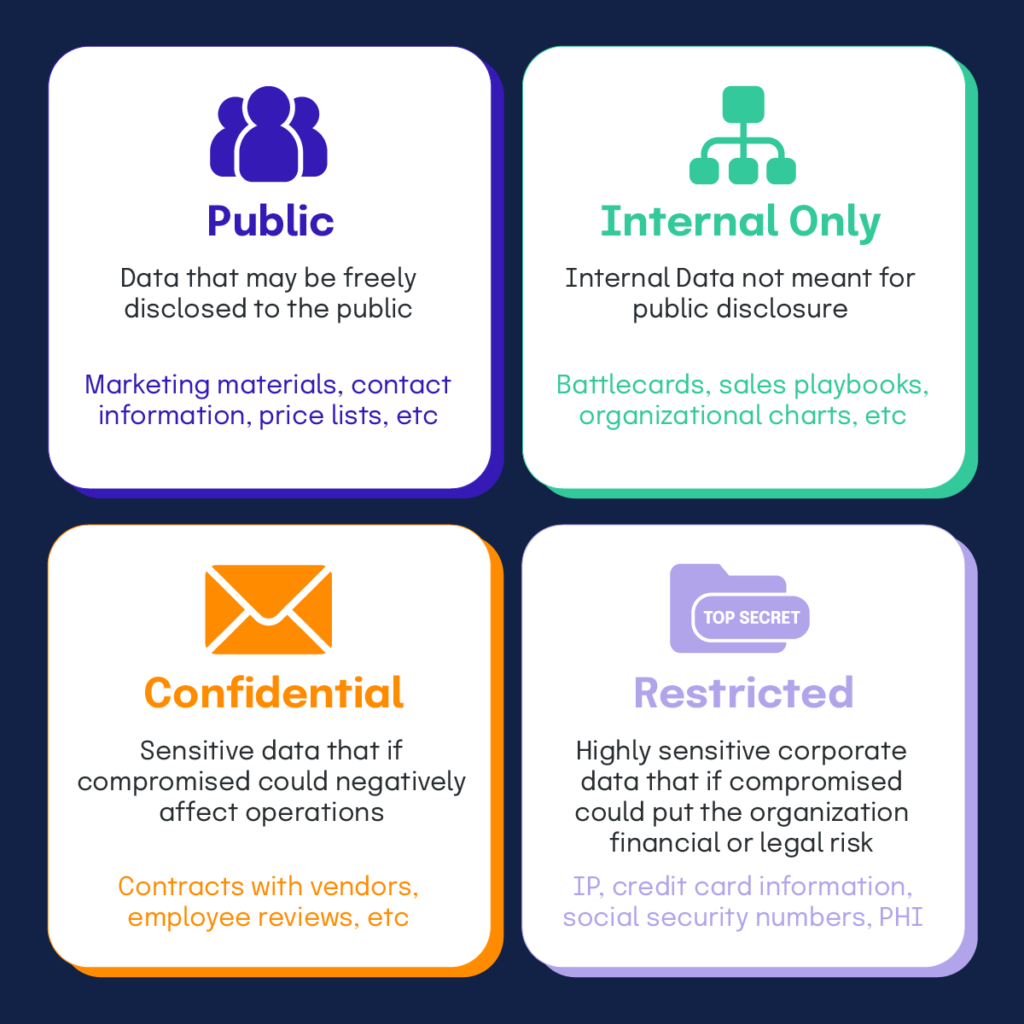
Once you have your data classified, you can zero in on the most sensitive data and see how it is being handled.
2. Identify threats
When thinking about threats to data security, hackers are usually top of mind, but threats to your business’s information security come in many different forms. You can see from this list of 2019 data breaches that while hackers exploiting weaknesses in a business’ firewalls or website security programs has been very common, a lot of different threat types contributed to data breaches in 2019. You need to take into account many different threat types when compiling a list of all the unique threats your business faces.
For example, you also have to take into account not just malicious human interference, but also accidental human interference, such as employees accidentally deleting information or clicking on a malware link. Depending on the quality of your hardware and your information systems, you might also need to account for the risk of system failure.
Finally, things such as natural disasters and power failures can wreak as much havoc as humans can, so you need to account for any of those kinds of threats as well. After you’ve completed this step, you should have a thorough list of the threats to your assets.
New cybersecurity risks prompted by COVID-19
Now that the novel coronavirus has forced most organizations into a remote-only operating model, organizations are left more vulnerable. Employees are working outside of corporate firewalls. Malicious cybercriminals could take advantage of public concern surrounding the novel coronavirus by conducting phishing attacks and disinformation campaigns.
Phishing attacks often use a combination of email and bogus websites to trick victims into revealing sensitive information. Disinformation campaigns can spread discord, manipulate public conversation, influence policy development, or disrupt markets.
During this time, your IT security team should remind employees to take precautions, reiterate key concepts covered in your security training, ensure that all monitoring systems are operating correctly, and be ready to respond to any security incidents promptly.
3. Identify vulnerabilities
A vulnerability is a weakness in your system or processes that might lead to a breach of information security. For example, if your company stores customers’ credit card data but isn’t encrypting it or testing that encryption process to ensure it’s working properly, that’s a significant vulnerability. Allowing weak passwords, failing to install the most recent security patches on software, and failing to restrict user access to sensitive information are behaviors that will leave your business’s sensitive information vulnerable to attack.
Another vulnerability you may face during the coronavirus health crisis is the lack of staff. Security controls are at risk of not being performed as IT security staff are working remotely or worse, sick themselves.
You can find vulnerabilities through audits, penetration testing, security analyses, automated vulnerability scanning tools, or the NIST vulnerability database.
It’s also important to consider potential physical vulnerabilities. For example, suppose your employees work with hard copies of sensitive information or use company electronics outside of the office. In that case, this can lead to the misuse of information, just like vulnerabilities in your software and electronic systems.
4. Analyze internal controls
After identifying the vulnerabilities in your systems and processes, the next step is to implement controls to minimize or eliminate the vulnerabilities and threats. This could be either control to eliminate the vulnerability itself or control to address threats that can’t be totally eliminated.
Controls can be technical, such as computer software, encryption, or tools for detecting hackers or other intrusions, or non-technical, such as security policies or physical controls. Controls can also be broken down into preventive or detective controls, meaning that they either prevent incidents or detect when an incident is occurring and alert you.
Creating effective controls requires experience and skills. Suppose your firm does not have security and compliance subject matter experts on staff. In that case, it is crucial to seek out assistance from professional services firms that have deep expertise in addressing IT security issues.
5. Determine the likelihood that an incident will occur
Using all the information you have gathered – your assets, the threats those assets face, and the controls you have in place to address those threats – you can now categorize how likely each of the vulnerabilities you found might actually be exploited. Many organizations use the categories of high, medium, and low to indicate how likely a risk is to occur.
So, if, for example, a core application you use to run your business is out-of-date and there’s no process for regularly checking for updates and installing them, the likelihood of an incident involving that system would probably be considered high.
On the other hand, if you handle a large volume of personal health information, have automated systems for encrypting and anonymizing it, and regularly test and check the effectiveness of those systems, the likelihood of an incident could be considered low. You will need to use your knowledge of the vulnerabilities and the implementation of the controls within your organization to make this determination.
6. Assess the impact a threat would have
This step is known as impact analysis, and it should be completed for each vulnerability and threat you have identified, no matter the likelihood of one happening. Your impact analysis should include three things:
- The mission of the system, including the processes implemented by the system
- The criticality of the system is determined by its value and the value of the data to the organization
- The sensitivity of the system and its data
If possible, you should consider both the quantitative and qualitative impacts of an incident to get the full picture. Depending on the three factors above, you can determine whether a threat would have a high, medium, or low impact on your organization. Taken together with how likely an incident is to occur, this impact analysis will help you to prioritize these risks in the next step.
7. Prioritize the risks to your information security
Prioritizing your security risks will help you determine which ones warrant immediate action, where you should invest your time and resources, and which risks you can address at a later time.
For this step, it might help to utilize a simple risk matrix that helps you use the information you already have about each vulnerability/threat pair you’ve identified and plot it on the matrix. Risks that are both likely to happen and would have severe consequences would be mapped as a high priority, while risks that are unlikely to happen and would have marginal consequences would be mapped as the lowest priority, with everything else falling somewhere in between.
You can make your risk matrix as simple or as complex as is helpful to you. If you’re a large organization with a lot of risks competing with each other for time and attention, a more in-depth 5×5 risk matrix will likely be helpful; smaller organizations with fewer risks to prioritize can probably utilize a simple 3×3 matrix and still get the same benefit.
Cyber risk models for information security
At this time, there are several different frameworks for risk quantification. Here are a few popular frameworks to date for risk quantification:
FAIR Model: The FAIR (Factor Analysis of Information Risk) cyber risk framework is touted as the premier “Value at Risk (VaR) framework for cybersecurity and operational risk”. The FAIR quantitative risk analysis model defines risk management as “the combination of personnel, policies, processes, and technologies that enable an organization to achieve and maintain an acceptable level of loss exposure cost-effectively.” You can learn more about how to implement the FAIR model by reading The FAIR book.
NIST SP 800-30: Originally published in 2002 and updated in 2012, NIST Special Publication 800-30 or NIST Risk Management Framework is built alongside the gold-standard NIST Cybersecurity Framework as a means to view an organization’s security threats through a risk-based lens.
World Economic Forum Cyber Risk Framework and Maturity Model: This model was published in 2015 in collaboration with Deloitte, and bears some similarities to the NIST RMF in that it relies on subjective judgments. The model looks at risk through a lens known as “value-at-risk” and asks the stakeholders to evaluate three components: 1) existing vulnerabilities and defense maturity of an organization, 2) value of the assets, and 3) profile of an attacker.
8. Design controls
Once you’ve established priorities for all risks you’ve found and detailed, then you can begin to make a plan for mitigating the most pressing risks. To determine what controls you need to develop to mitigate or eliminate the risks effectively, you should involve the people who will be responsible for executing those controls.
Senior management and IT should also be heavily involved to ensure that the controls will address risks and align with your organization’s overall risk treatment plan and end goals. You’ll also need to develop a plan to implement all new controls. You may also need to consult with professional services firms with IT and security expertise to develop a new set of controls. In this plan, be sure to include the resources you would need to train pertinent employees.
For further guidance on how to design effective controls to mitigate risks, check out this article The Four Signs of an Effective Compliance Program
9. Document the results
The final step in your risk assessment is to develop a report that documents all of the results of your assessment in a way that easily supports the recommended budget and policy changes.
Risk assessment reports can be highly detailed and complex, or they can contain a simple outline of the risks and recommended controls. Ultimately, what your report looks like depends on who your audience is, how deep their understanding of information security is, and what you think will be the most helpful in showing potential risks. A risk assessment aims to document your organizational risks and create a plan to address those risks to avoid encountering a risk without preparation.
Creating this report for senior management is the final step in this process and is crucial for communicating what they need to understand about information security risks. It’s important to note that assessing risks should be an ongoing process, not a one-time-only exercise. As your systems or your environment change, so will your information security risks.
IT risk assessment template
To make it easier for you to document the results of your risk assessment, we’ve created an IT risk assessment template.
IT risk assessments don’t need to be complicated

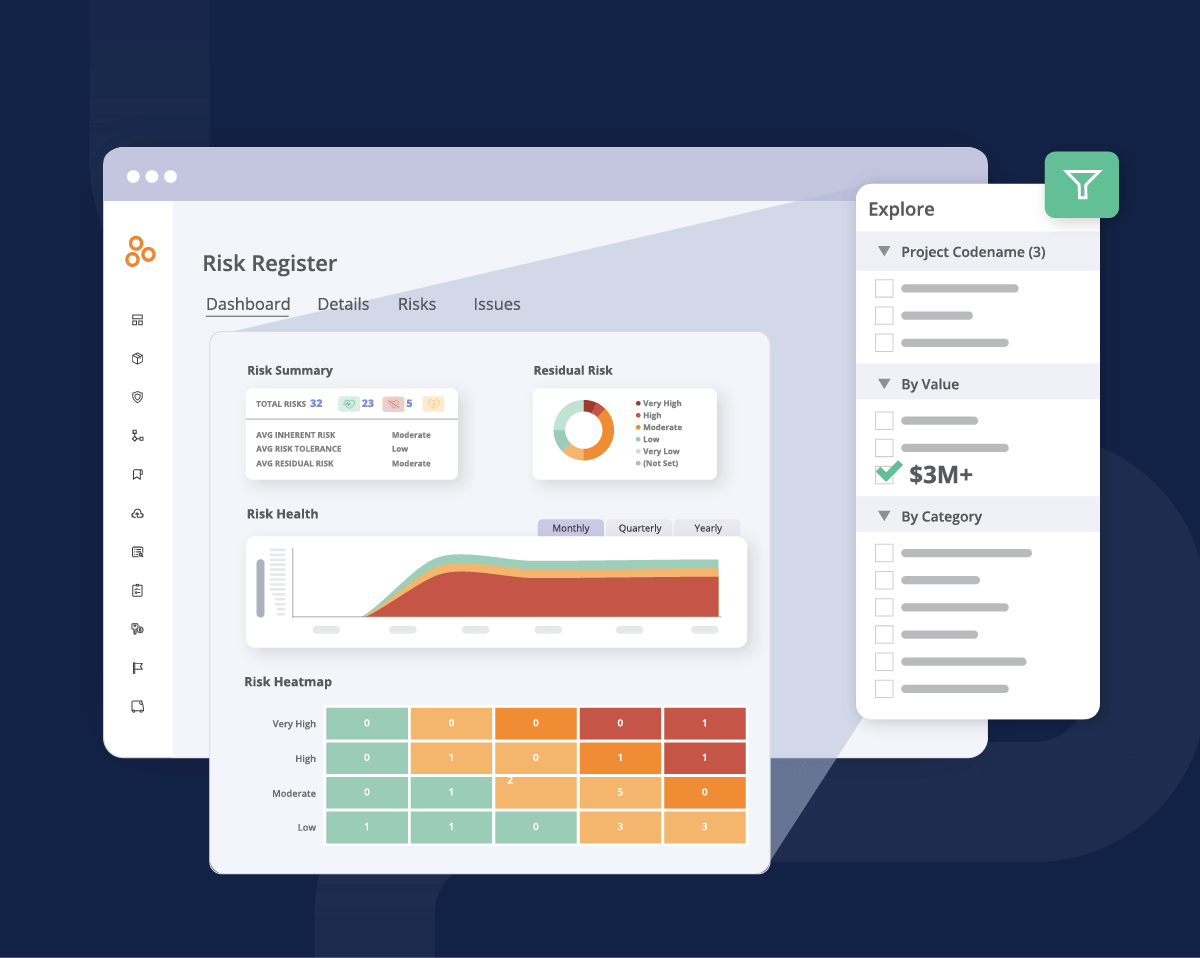
Purpose-built risk register software makes it easy for risk owners to document everything that should go into a risk register, make updates to risks on the fly, visualize changes to risks, and communicate risk information to leadership teams.
Hyperproof offers a secure, intuitive risk register for everyone in your organization. With the application, risk owners from all functions and business units can document their risks and risk treatment plans. You can link risk to control and gauge how much a specific risk has been mitigated by an existing control versus the residual risk that remains. With this clarity, your risk management, security assurance, and compliance teams can focus their energy on the risks you truly need to worry about.
With Hyperproof’s dashboard, you can see how your risks change over time, identify which risks and controls to pay attention to at a given moment, and effectively communicate the potential exposure for achieving strategic operations, reporting, and compliance objectives to your executives.
If you can successfully bring together the parties necessary for a thorough risk assessment and account for all of the risks to your data, you’ll be taking a huge step toward earning your customers’ trust and protecting the sensitive data you’re entrusted with.
Safeguard your organization’s sensitive data and earn your customers’ trust with Hyperproof. Request a demo today and discover the power of their dashboard. Track risk changes over time, prioritize key risks, and effectively communicate potential exposure to executives. Don’t miss this opportunity to enhance your strategic, operational, reporting, and compliance objectives.
Monthly Newsletter
Get the Latest on Compliance Operations.