Inherent Risk vs. Residual Risk: What You Need to Know
Risk management is not new, but the way organizations look at risk has shifted. Modern businesses are moving at a breakneck speed, continuously making changes to their tech stack, product lines, services, vendor ecosystem, and org structures. With these changes, new risks can be introduced rapidly into an organization – and existing risks may be amplified. Many organizations have opted to deal with risk proactively and create comprehensive strategies for different types of risk. To manage risks appropriately, it’s vital to understand how to evaluate risk prior to and after certain controls are designed and implemented. This brings us to two terms that you may have heard of before: inherent risk and residual risk.
In this article, we will address what inherent and residual risk is, how to measure inherent risk vs. residual risk, why risk management programs need to include third parties, and how to best manage risk moving forward.
Inherent risk vs. residual risk
What is inherent risk?
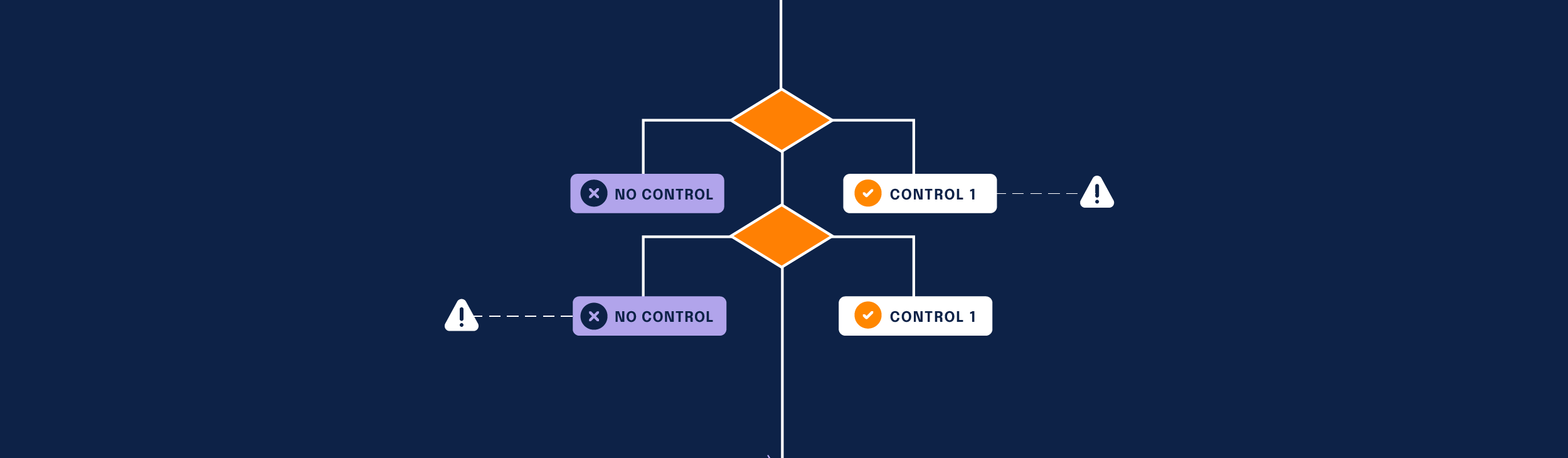
Inherent risk is the risk that an organization could encounter when no controls (i.e., activities, procedures, and processes your organization implements to mitigate risks and/or meet regulatory requirements) are in place. Simply put, inherent risk is what a company might face without any preventative measures in place.
When evaluating risk, most organizations aren’t starting from square one in regard to security controls. With this in mind, the Factor Analysis of Information Risk (FAIR) Institute — a Value at Risk (VaR) framework for cybersecurity and operational risk — suggests looking at inherent risk as the current risk level given the existing set of controls rather than the hypothetical notion of an absence of any controls.
What is residual risk?
On the other hand, residual risk is the risk that exists with controls in place. This type of risk can be thought of as the risk that still remains even after an organization has taken preventative measures to minimize the likelihood and/or impact of the risk event.
Residual risks are less likely to create problems for an organization since there are security controls in place, but as with any type of risk, they are not completely avoidable. Additionally, these risks can have a much smaller impact if the controls in place are effective.
Common examples of inherent risk
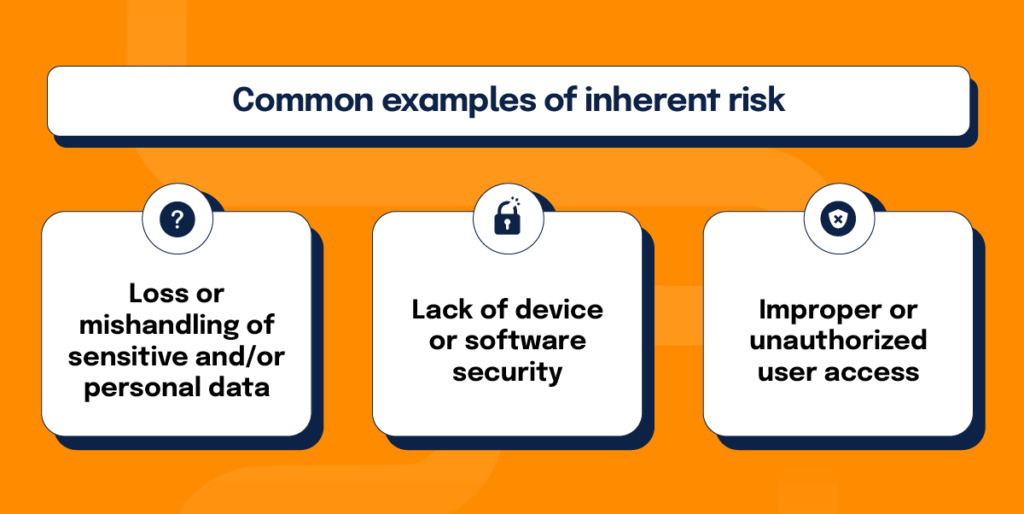
While inherent risk will vary from organization to organization, here are some common examples that have the potential to cause major security issues when not addressed with controls:
- Loss or mishandling of sensitive and/or personal data: Without the proper controls in place to ensure that information is being protected, managed, and stored, organizations could lose or expose sensitive customer or company data.
- Lack of device or software security: Standardizing employee password guidelines and creating rules for how employees should handle their devices are examples of controls that can help to secure company hardware and software. If either of these controls are too lax or nonexistent, data breaches will have a higher likelihood of happening.
- Improper or unauthorized user access: Access to information needs to be regulated and monitored so that only authorized employees can view and handle specific information. Having the “wrong eyes” on certain information could lead to violating privacy laws, a breach of contract, or even potential lawsuits.
Common examples of residual risk
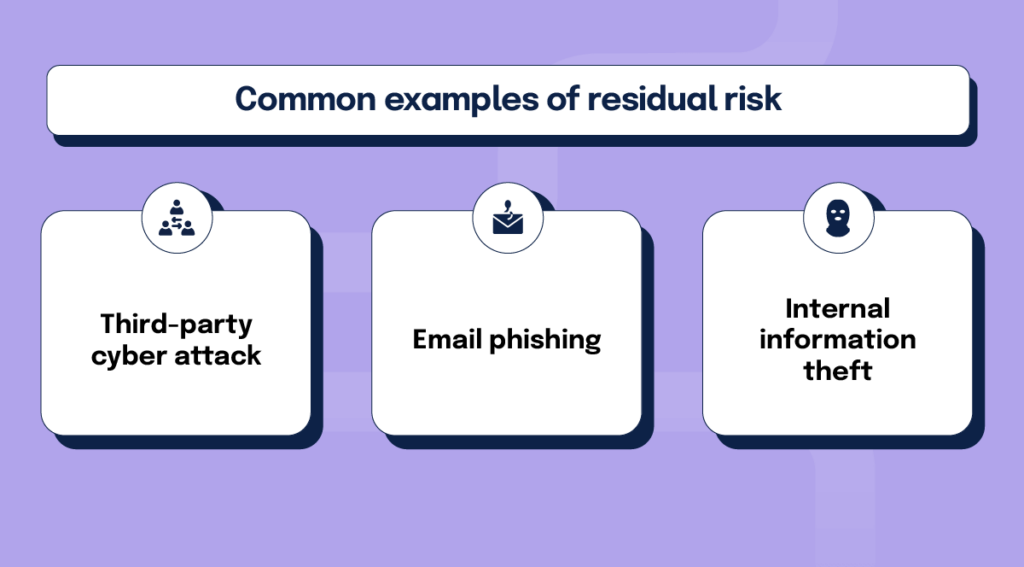
Like inherent risk, residual risk will be different at every company. Here are some common examples of residual risk that should be monitored even when security controls are in place:
- Third-party cyber attack: This kind of cyber attack occurs when an external actor targets an organization’s computer network with the goal of disrupting, disabling, and/or controlling stored information. Because these attacks are carried out by third parties, it’s essentially impossible to know if and when an attack like this will happen. Meaning, even with preventative controls in place, a third-party cyber attack is a potential risk to any organization.
- Email phishing: Another risk from an external party, email phishing is when an attacker sends an email with the intent of gaining personal information or hacking into a system. Phishing emails are often built to look like they’re coming from senders of authority — company executives, customer service or HR departments, etc.—when in reality, the messages are being sent by third parties with malicious intent.
- Internal information theft: People often associate cyber attacks with faceless third-party actors. However, sabotage carried out by people within the organization (disgruntled employees, contractors, etc.) needs to be taken into consideration as well. Addressing inherent risks like the mishandling of personal data and misuse of privileged accounts by using logging and monitoring software can help to lower the likelihood of this kind of attack, but internal destruction should still be considered a residual risk.
How do you calculate inherent risk and residual risk?

With a large number of possible inherent and residual risks out there, organizations need to decide which potential risks are worth their time, attention, and resources. This can be accomplished by categorizing the likelihood of such risks, then prioritizing any potential risks by the urgency for if/when they happen. Here are the steps you can take to calculate inherent and residual risk:
1. Complete a security risk assessment
In order to fully understand what inherent and residual risks your organization might face, it’s important to first know the current state of your security. Start with these tips to complete such an assessment:
- Understand how and where data is stored and who has access to it. No matter the size of your organization, it is important to keep an up-to-date inventory of your organization’s information assets. Once inventory is taken, you need to track who has access to this data. In reviewing information storage and access, an organization will be able to see if there are any vulnerabilities that could lead to breaches or attacks.
- Review and evaluate types of security risks. This piece of your security risk assessment might start as simply as listing every possible security risk that your organization’s network could encounter (i.e., weak security permissions, attacks from hackers, email phishing, lack of network segmentation, etc.). From there, you can dive deeper into how each of these risks might affect your organization and what the consequences of each risk could be.
While it may be time-consuming to conduct your initial assessment, doing so will save you time and resources in the long run. And if you need some help, you can turn to vCISO and security advisory firms that can conduct risk assessments for your organization.
Easily complete a security risk assessment with this template.
2. Build a comprehensive risk register
Once your security assessment is complete, it is important to closely monitor past security incidents and potential future security risks. The best way to do this is via a risk register.
A risk register is an information repository that documents the risks an organization faces and the responses taken to address the risks. At a minimum, each risk documented in the risk register should contain a description of a particular risk, the likelihood of it happening, its potential impact, how it ranks overall in priority relevant to all other risks, the response, and who owns the risk.
In regards to calculating inherent and residual risks, focus on the following:
- Likelihood: This is how likely it is that a specific risk will actually result in a security incident. While a high number of potential risks may exist, some will never come to fruition. Many organizations use the categories like high, medium, and low to indicate how likely a risk is to occur.
Even if a risk does turn into something more, that issue may not have a huge impact on the organization. This brings us to the next primary factor – potential impact.
- Potential impact: The impact of a security incident can manifest itself in many different ways – financially, company reputation, endangering customer privacy, etc. Some security issues will have catastrophic results, while others will carry less weight (financially or otherwise).
After identifying the likelihood and potential impact of inherent or residual risks, you can prioritize them to determine how much of your time and resources should be allocated to mitigating each risk.
Additional Resource: Best Guide to Building a Risk Register

3. Take action
With new inherent risks identified, you can move forward with building preventative protective controls to manage these risks. Some controls may be straightforward and easy to implement, while others will take time to build out and get running smoothly. Either way, it’s vital to put time into developing the proper controls for each unique risk.
Although residual risks will have accompanying controls already in place, you need to consistently test your security controls and look for potential gaps. Regularly analyzing gaps in your security controls will help you to be proactive in protecting your organization against cyber-attacks and data breaches.
Protect your organization by better understanding and strengthening your security posture: https://hyperproof.io/resource/strengthen-security-posture/
Inherent and residual risk in third-party risk management

Third-party risk is the likelihood of your organization experiencing an adverse event (e.g., data breach, operational disruption, reputational damage) when you choose to outsource certain services or use software built by third parties to accomplish specific tasks. Third parties include any separate business or individual providing software, physical goods, or supplies or services, such as software vendors, suppliers, staffing agencies, consultants, and contractors.
Understanding and analyzing third-party inherent and residual risk is just as important as monitoring your own, but it is oftentimes overlooked. If one or more of your vendors are lacking in risk management processes and controls, your organization and customers could suffer the consequences. All vendor platforms that touch your networks and/or process sensitive data on your behalf should be evaluated for inherent and residual risk.
- Inherent third-party risk: Like an organization’s own inherent risk, this can be viewed as the risk that may exist without security controls in place. As an outside party with fresh eyes, it may actually be easier for you to identify any inherent risk when evaluating a third party.
- Residual third-party risk: Many potential vendors do not have a well-established compliance program, so they may not refer to controls as “controls”. That said, it’s still important to evaluate preventative measures third parties take to maintain the security of information and systems. You will also want to consider the steps a vendor will take if/when a security incident occurs.
Once you’ve evaluated third parties for risk, you’ll have a more comprehensive picture of how they work and deal with potentially adverse situations. This will help you to make an informed decision about whether to move forward with engaging with them or not.
Learn more about third-party risk management
Hyperproof makes managing inherent and residual risk easy
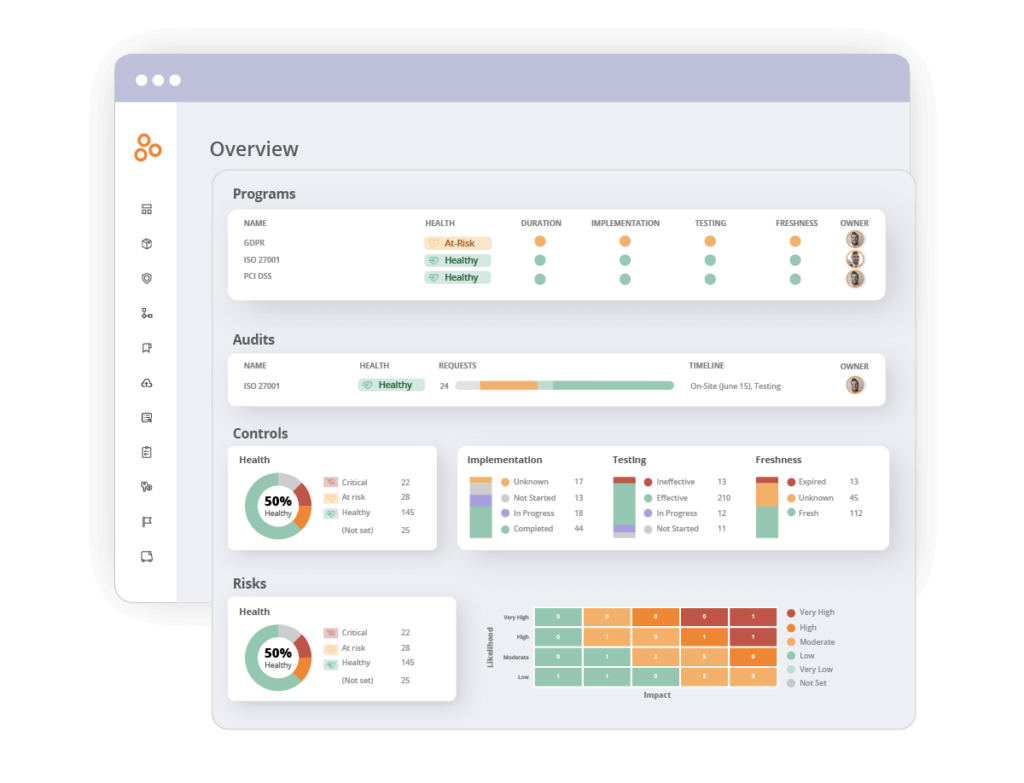
Risk management is a complex task that requires strict due diligence and attention to detail. The good news is that you don’t have to tackle it alone. Hyperproof’s compliance operations platform conveniently organizes risk information in a user-friendly dashboard and provides the tools to help you remediate risks on a continuous basis:
- Identify, assess, and prioritize risks
Using our intuitive Risk Register, risk owners from all functions and business units can document their risks and risk treatment plans, and organizations’ leaders can better prioritize risk management activities. Risk scoring criteria can be customized.
- Integrate risk and compliance activities
With Hyperproof, you can tie a control to the risk and to compliance requirements. It is easy to gauge how much a specific risk has been mitigated by existing controls (inherent risk) and how much residual risk remains. By using Hyperproof to align your risk management and compliance management activities, you’ll save time and gain operational efficiency.
- Manage Third-Party risk
Our Vendor Management module allows you to easily assess your vendors’ security and compliance posture and manage third-party risk. Use Hyperproof’s intuitive and easy-to-use built-in tools for risk assessment, vendor criticality, and risk scoring. Utilize prebuilt or tailored questionnaires with vendors to collect relevant information. Conduct one-off assessments, assessments on a fixed schedule, or both. Monitor questionnaire completion progress.
- Reduce time spent on monitoring risks
Spend less time monitoring and determining the latest risk status as remediation activities are completed. Once risk and/or control owners complete mitigation activities (by working on controls in Hyperproof), the actual risk health status is updated automatically in Hyperproof. Hyperproof comes with a risk monitoring dashboard out of the box, so you can easily provide your leadership team with a complete picture of your security and compliance posture.
Take your risk management to the next level with Hyperproof. Book a demo today and let us show you how we can support all your risk management needs. Book a demo today.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












