Everything to Consider When Integrating Risk and Compliance Operations
Organizations rarely begin with integrated risk and compliance, nor do they intentionally create silos. Yet teams naturally split around their mandates (compliance handles regulatory requirements, risk assesses operational exposures), and before long, you have parallel operations answering similar questions with different methodologies.
On the surface, both functions collect evidence, test controls, and report to governance. But look closer, and the duplication becomes clear: vendor assessments are run twice, control testing is performed against separate frameworks, and when a control fails, two teams independently analyze the same issue, meaning teams are operating without visibility into each other’s work.
Several factors determine whether integration closes these gaps or just produces cleaner-looking silos. But before exploring those, let’s first understand what integrated risk and compliance looks like in practice.
What does integrated risk and compliance look like in practice?
In practice, integrated risk and compliance means your organization operates from a single control framework and shared data model where compliance requirements are treated as specific risk types rather than separate activities.
When you assess a business process, you’re simultaneously evaluating operational risks, regulatory obligations, and control effectiveness in one workflow instead of running parallel risk and compliance assessments that get reconciled later.
Practically, this looks like:
The key indicator you’ve truly integrated is that testing a control once satisfies both risk validation and compliance audit requirements without any duplicate efforts or reconciliation between risk and compliance teams.
That said, achieving this integration doesn’t happen by chance. Here are the considerations that play a very important role.
1. Connect controls to risks and regulatory requirements
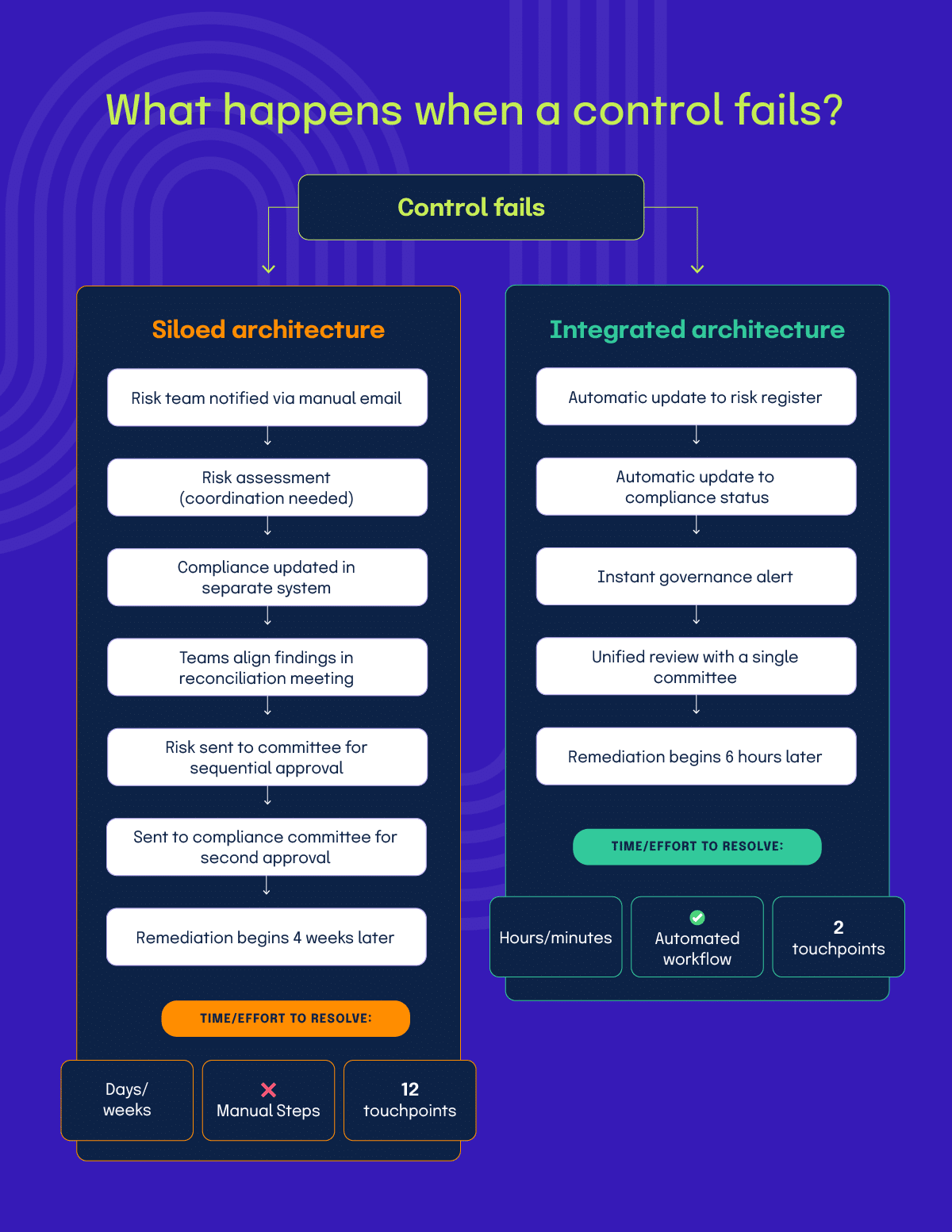
In siloed models, risk-to-control mappings exist in risk management systems while control-to-compliance mappings live in Governance, Risk, and Compliance (GRC) platforms, requiring manual reconciliation. This separation means control effectiveness changes don’t automatically update both risk exposure and compliance status. Teams must manually connect the dots.
Integration begins by architecting these relationships as unified, traceable linkages. Without this architecture, a single control failure requires separate manual analysis by risk and compliance teams to understand the full organizational impact, the exact delay, and the duplication that integrated architecture is designed to eliminate.
Building this architecture requires considering two critical decisions:
|
Decision |
Tradeoff |
Consideration |
|---|---|---|
|
Mapping granularity |
Specific risk scenarios (e.g., “inadequate segregation of duties in AP processing”) provide precise impact analysis but create more relationships to maintain. Broad categories (e.g., “operational risk”) are manageable but sacrifice analytical precision. |
Balance depends on operational tempo and regulatory environment: high-change organizations need simpler structures, while heavily regulated industries need the specificity auditors expect. |
|
Propagation rules |
Technical controls with objective metrics can auto-propagate. Subjective assessments (e.g., management review effectiveness) need human validation before triggering alerts. |
Determine which scenarios warrant an immediate automated response versus those that require manual validation before cascading through the system. |
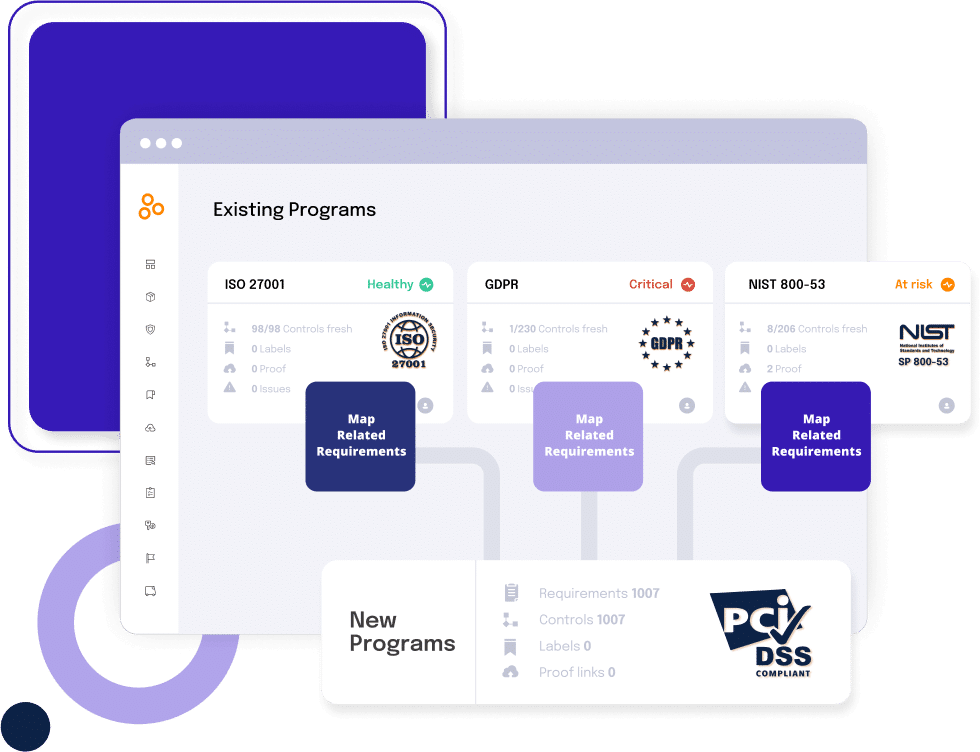
2. Link controls across multiple frameworks
Organizations operating under multiple regulatory frameworks typically maintain separate control sets for each standard.
For example, a financial services firm might document access controls three times: once for Sarbanes-Oxley (SOX) compliance, again for Payment Card Industry Data Security Standard (PCI-DSS) requirements, and a third time for state privacy regulations.
Integration requires consolidating these duplicate control inventories into a single library where each control’s regulatory coverage is explicitly mapped.
Here’s a baseline approach you can adopt to link controls across multiple frameworks and refine based on your organization’s needs:
- Inventory all existing controls across frameworks and group them by functional category (access management, change control, incident response).
- Select a master taxonomy (GDPR, ISO 27001, NIST CSF, for example) that aligns with your organization’s primary regulatory focus.
- Map each framework-specific control to common control objectives, identifying where different labels describe identical activities.
- For each consolidated control, adopt the most stringent requirement across all mapped frameworks as your baseline (e.g., if NIST 800-53 requires quarterly access reviews, PCI-DSS requires monthly, and GDPR requires risk-based, your unified control defaults to monthly reviews to satisfy all three).
- Document explicit traceability showing which regulatory citations each unified control satisfies.
- Establish governance to determine when new regulations map to existing controls versus when new controls are required.
As mentioned, this is a starting point. You’ll refine this approach as you learn which consolidations work and which create audit friction.
3. Operationalize workflows through platform architecture
If even after architecting control relationships and rationalising frameworks, risk analysts continue working in separate systems from compliance officers, operational integration hasn’t occurred. The documentation may be unified, but the work remains siloed.
Organizations must therefore determine which work needs to happen together versus which work simply needs access to the same information. This distinction determines platform architecture and implementation approach. If all activities are forced into single workflows, it will result in unnecessary complexity. Conversely, those that maintain excessive separation perpetuate the inefficiencies that integration should eliminate.
Here’s a sample framework organizations can refer to when designing their operational integration (adjust where your operational context requires different approaches):
|
Activity |
Merge workflows |
Share data |
Rationalle |
|---|---|---|---|
|
Vendor risk assessments |
Yes |
Yes |
Risk and compliance evaluations ask overlapping questions about the same vendor. Conduct one assessment that addresses both dimensions. |
|
Control testing |
Yes |
Yes |
Testing validates control effectiveness. The same evidence satisfies both risk validation and compliance audit requirements. |
|
Issue remediation |
Yes |
Yes |
Control deficiencies create simultaneous risk exposure and compliance gaps. A single remediation process addresses both. |
|
Risk quantification |
No |
Yes |
Risk modeling requires specialized analytical techniques that compliance doesn’t use, but models consume the same control effectiveness data. |
|
Regulatory reporting |
No |
Yes |
Compliance submits framework-specific reports in required formats, but reporting draws from shared control and incident data. |
|
Board reporting |
Yes |
Yes |
Risk and compliance present different perspectives on governance, but both reference the same underlying facts about control performance. Present a single dashboard/source of truth for your risk and compliance data. |
In the simplest terms, activities addressing the same question benefit from workflow integration. Activities serving different purposes but requiring the same underlying facts need data integration with separate workflows.
4. Align governance and decision-making structures
Organizations face three specific governance breakdowns when operations integrate, but committees don’t:
- Authority conflicts when single issues need multiple approvals. When risk committees want to accept residual risk but compliance committees can’t due to regulatory requirements, which decision prevails? Without a clear authority hierarchy, organizations escalate everything unnecessarily.
- Timing mismatches between integrated operations and sequential governance. Integrated systems surface issues in days, but if committees meet on different schedules (quarterly, monthly, varied), organizations wait months for approvals, even though the analysis is complete.
- Conflicting prioritization when risk and compliance metrics disagree. When risk scores rate a deficiency as medium priority but compliance scores rate it critical, which drives resource allocation? Organizations need tiebreaker mechanisms that most governance structures lack.
Resolving these governance breakdowns requires answering several fundamental questions:
|
Governance breakdown |
Questions organizations must answer |
|---|---|
|
Authority conflicts |
|
|
Timing mismatches |
|
|
Conflicting prioritization |
|
5. Translate integrated operations for framework-specific auditors
Organizations that achieve internal integration face an external barrier: auditors and regulators operate in framework-specific silos regardless of how unified your internal operations become. For example, when a single control failure surfaces in your integrated system, you still need to present evidence in different ways for different auditors:
Organizations must decide how to bridge this gap. The most efficient approach would be to build presentation layers that translate unified control data into framework-specific formats that auditors expect. Alternatively, maintain some level of framework-specific documentation despite internal integration.
The challenge intensifies with regulatory examinations, where examiners often have less flexibility than third-party auditors and require specific evidence formats regardless of internal operational models.
Organizations addressing this challenge can leverage platforms that map common controls across multiple frameworks while automatically generating framework-specific audit views. For example, Hyperproof seamlessly connects audit requests to controls and evidence, enabling organizations to test controls once while presenting evidence in whatever format each auditor requires across 140+ frameworks.
How to integrate risk and compliance
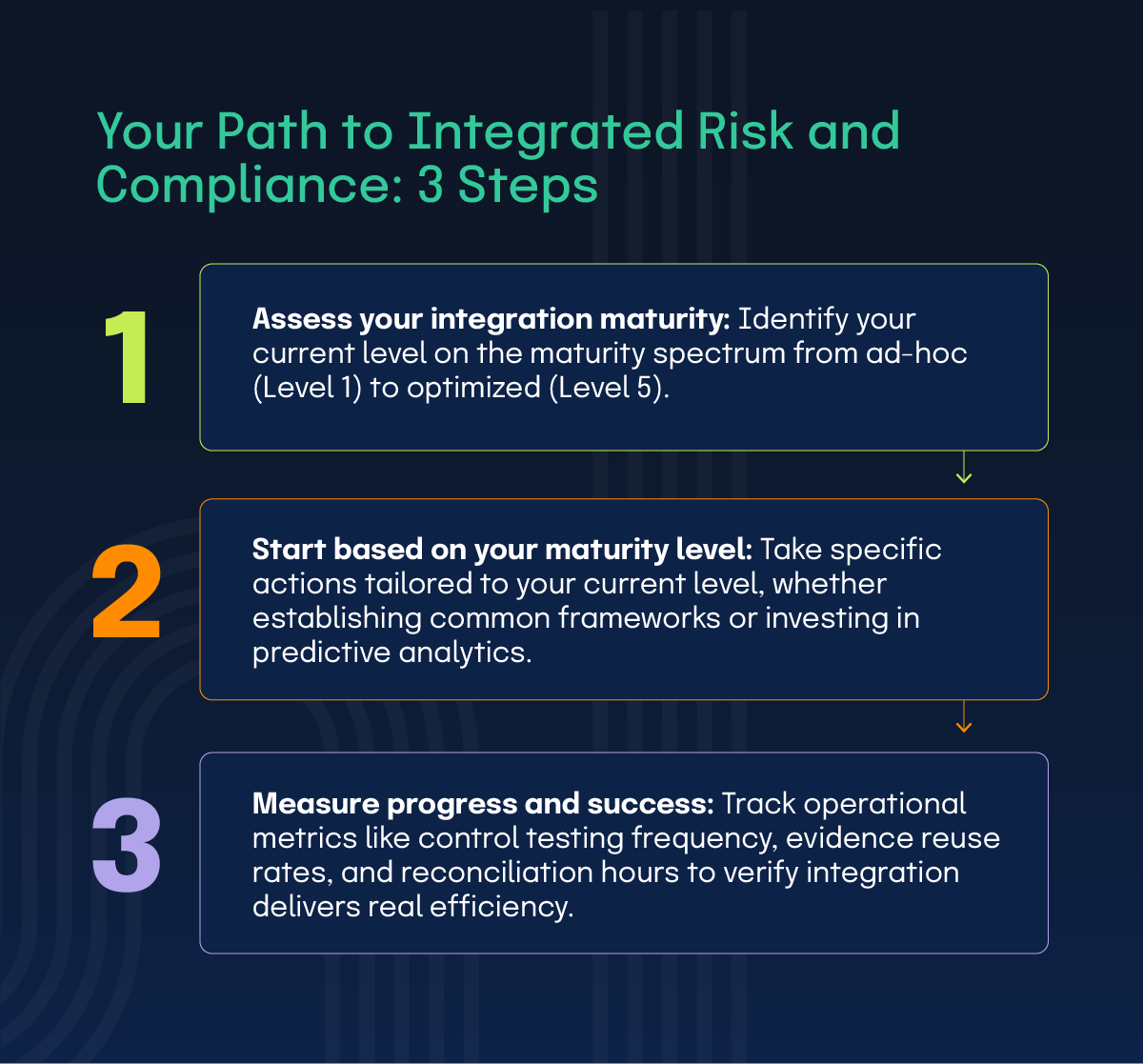
The path to integrated GRC depends on where you’re starting from and which gaps present the highest-priority opportunities.
Step 1: Assess your integration maturity
Most organizations fall somewhere along a GRC maturity spectrum, ranging from completely siloed operations to fully integrated risk and compliance functions. Understanding your current position helps identify the most impactful next steps rather than pursuing integration approaches that don’t match your operational readiness.
|
Maturity level |
Architecture |
What this looks like |
|---|---|---|
|
Level 1: Ad-hoc |
Separate risk and compliance data models with no linkage |
Control failures require manual analysis by both teams to understand the impact. Regulatory changes don’t trigger risk assessments. |
|
Level 2: Fragmented |
Risk and compliance teams manually share information, but no systematic integration |
Teams know they’re duplicating work but lack mechanisms to consolidate. Cross-functional meetings happen reactively. |
|
Level 3: Standardized |
A common control framework was established with manual mapping to risks and requirements |
Controls map to both risks and compliance requirements on paper. Platform consolidation has begun, but teams still operate independently. |
|
Level 4: Integrated |
Automated linkage where control changes trigger risk and compliance updates |
Control testing happens once. Risk and compliance teams work from the same data. Governance addresses integrated issues without sequential committee reviews. |
|
Level 5: Optimized |
Predictive analytics using integrated data to identify emerging risks and compliance gaps |
Integration is embedded in culture. Teams don’t think about “risk vs. compliance.” They address combined exposure holistically. |
Step 2: Start based on your maturity level
Below are recommendations on what steps you should take to get to Optimized maturity, tailored to each starting maturity level:
Level 1: Ad-hoc
If you’re at Level 1 (Ad-hoc), start by establishing a common control framework by inventorying controls across risk and compliance first, identifying duplicates, and creating unified definitions. Start with IT general controls where requirements clearly overlap.
Level 2: Fragmented
If you’re at Level 2 (Fragmented), start by selecting and implementing a unified platform or establishing robust system integration. Pilot with one high-value process like third-party risk management, document efficiency gains, and establish joint risk-compliance leadership meetings.
Level 3: Standardized
If you’re at Level 3 (Standardized), start by merging workflows where risk and compliance ask identical questions. Implement propagation rules so that control changes automatically update both views. Eliminate duplicate testing by ensuring evidence collected once satisfies multiple frameworks.
Level 4: Integrated
If you’re at Level 4 (Integrated), start by investing in continuous monitoring, predictive analytics, and automation to reduce manual touchpoints. Refine governance to operate seamlessly. Measure integration ROI and use metrics to justify continued investment in optimization.
Curious about where your company falls on the maturity spectrum?

Step 3: Measure progress and success
Track integration progress through operational metrics:
Track control testing and frequency to verify you’re testing once instead of separately for each framework
Track evidence reuse rates to find what percentage of evidence now satisfies multiple requirements without reformatting
Track reconciliation hours to find time spent manually aligning risk and compliance data, which should approach zero as integration matures.
Track duplicate control reduction to compare your pre-integration control inventory against your rationalized library.
Refine your architecture, workflows, or governance approach when numbers plateau or regress.
Purpose-built GRC platforms track these metrics automatically through integrated dashboards, eliminating the manual effort of measuring integration progress across disconnected systems.
How can Hyperproof help with risk and compliance integration?
Hyperproof provides purpose-built capabilities that address the practical challenges of implementing and maintaining integrated risk and compliance operations.
Pre-built framework crosswalks with customizable controls
Hyperproof includes illustrative controls for commonly used frameworks like NIST CSF, PCI-DSS, and ISO 27001, with requirements already linked within the Secure Controls Framework (SCF) model.
Organizations can start with these baseline controls and customize them, editing, adding, or archiving controls to match your environment. As controls are refined, the SCF-based crosswalks maintain linkage across frameworks automatically, significantly reducing the risk of creating duplicate controls when adapting to your specific needs.
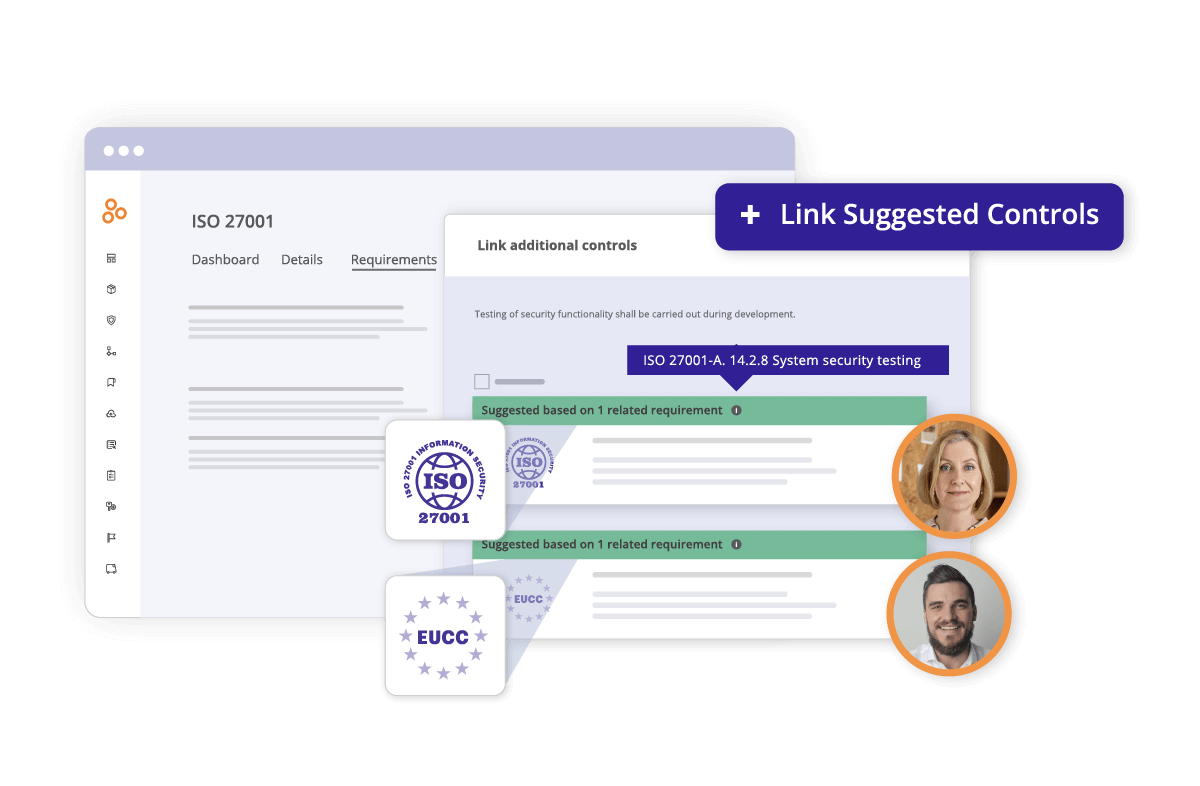
Jumpstart feature for framework expansion
When assessing new frameworks, Hyperproof’s Jumpstart feature provides immediate visibility into how your existing control environment already meets new requirements. This addresses the rationalization challenge by showing control coverage across frameworks before you start building, enabling you to extend existing controls rather than creating parallel structures.
The platform highlights which controls are linked to multiple program requirements, helping focus efforts on increasing control efficiency across your framework portfolio.

Unified evidence management with cross-framework reuse
Controls defined once in Hyperproof link to multiple framework requirements simultaneously. When you attach evidence or run control tests, that evidence automatically satisfies all linked requirements, eliminating duplicate evidence collection across frameworks. The platform connects recurring evidence tasks and lets you reuse artifacts like logs, screenshots, and tickets across multiple standards, operationalizing the integrated testing approach.

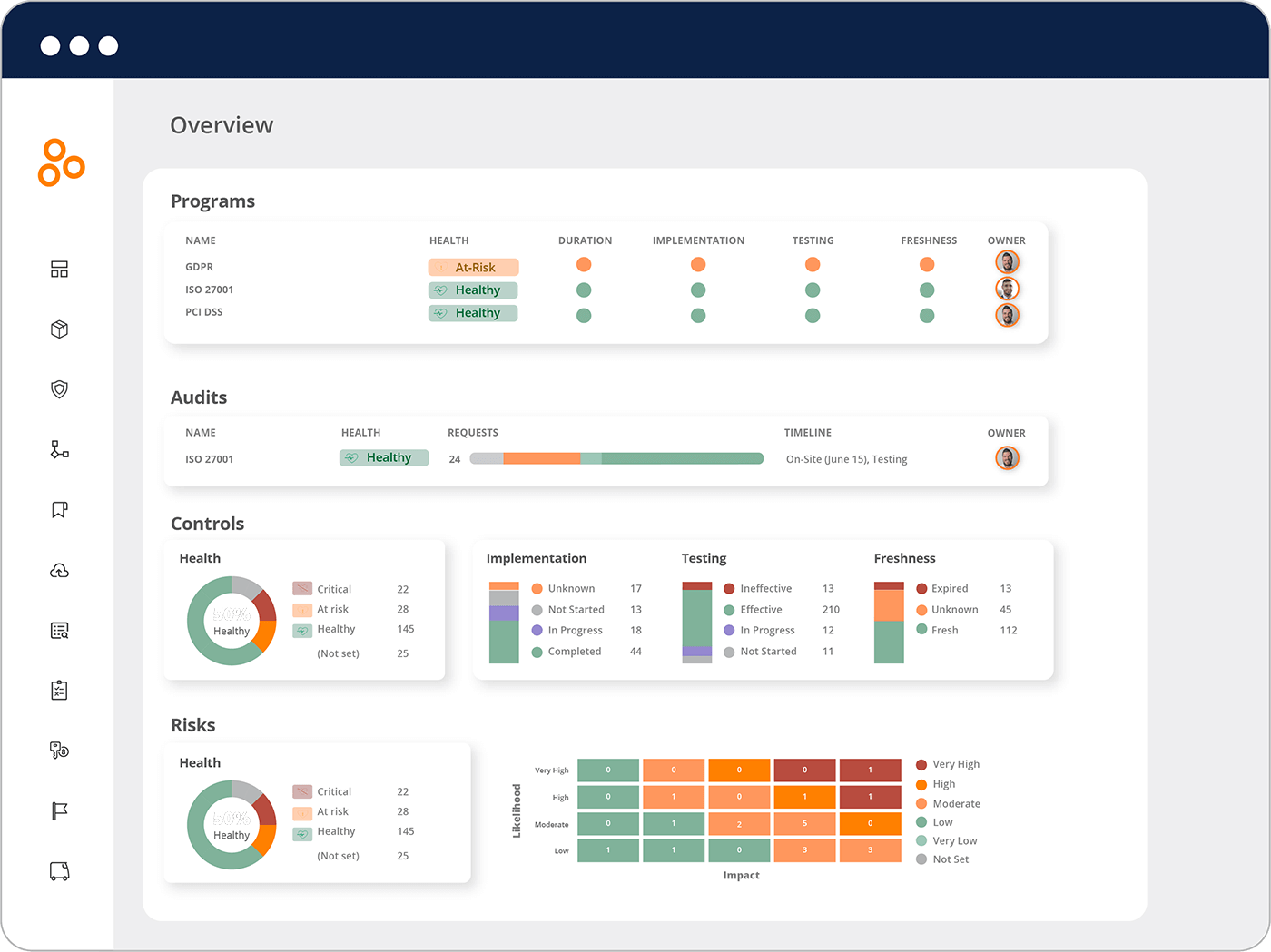
Dashboard visibility across frameworks and entities
Hyperproof’s dashboards show compliance status for individual frameworks and across all operationalized frameworks organization-wide. This provides the integrated view needed for governance decisions while maintaining framework-specific perspectives when auditors or regulators require them.
Organizations can monitor and control health, identify weak or overlapping controls, and see real-time status without manually consolidating data from separate risk and compliance systems.
Key takeaways: What should you consider when integrating risk and compliance operations?
Purpose-built platforms like Hyperproof operationalize these considerations through automated crosswalks, unified evidence management, and real-time dashboards.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












