NIST CSF 2.0: Everything You Need to Know About the Update

In November of 2023, we published this handy guide covering all the proposed changes to NIST CSF for those anticipating the long-awaited updates to this flexible and ubiquitous framework. That day has finally arrived: NIST has finalized the first major update since the framework’s creation in 2014.
The update provides several improvements to the framework, but it’s important to note that most of the framework core has remained the same. This update is the outcome of a multi-year process of discussions and public comments aimed at making the framework more effective.
Here’s everything you should know about the changes:
NIST CSF 2.0 has a new Govern Function
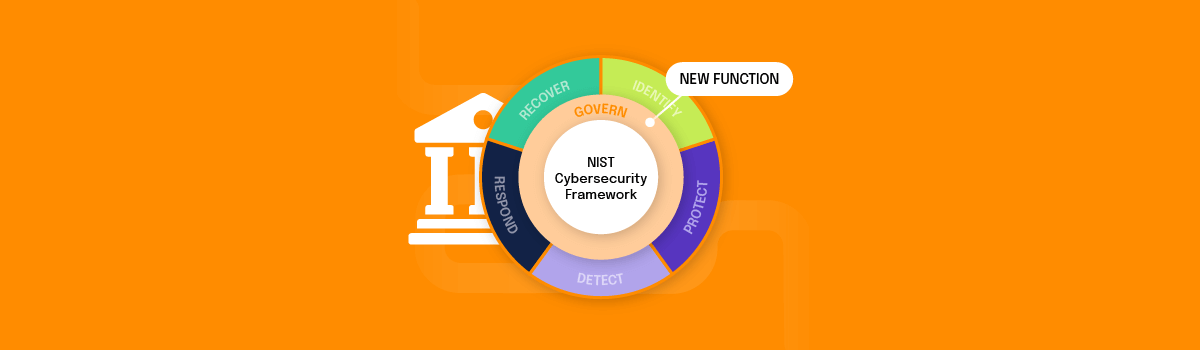
Perhaps the biggest change in NIST CSF 2.0 is that the framework now includes a new Govern Function to emphasize cybersecurity risk management governance outcomes. The Govern Function is now central to the rest of the pillars, as it informs how an organization will implement the other five Functions. The governance component emphasizes that cybersecurity is a major source of enterprise risk that senior leaders should consider alongside others such as finance and reputation.
With the addition of the Govern Function, the framework is now organized around six key functions:
- Govern: establish and monitor your company’s cybersecurity risk management strategy, expectations, and policy.
- Identify: determine the current cybersecurity risk to the business.
- Protect: support your ability to use safeguards to prevent or reduce cybersecurity risks.
- Detect: find and analyze possible cybersecurity attacks and compromises.
- Respond: take action regarding a detected cybersecurity incident.
- Recover: restore assets and operations impacted by a cybersecurity incident.
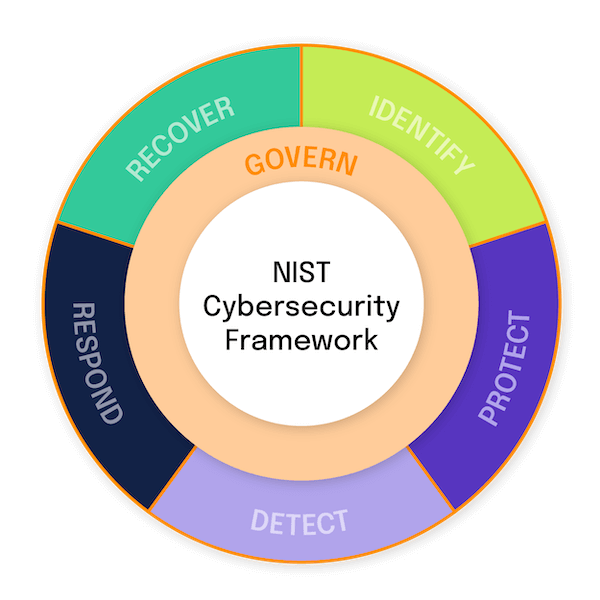
Additionally, the new Govern Function ensures that the implementation of the CSF 2.0 will be sustainable for organizations based on governance categories, including:
- Organizational Context (GV.OC), which addresses the organization’s risk management decisions
- Oversight (GV.OV), which allows for continuous improvements and adjustments to the organization’s risk management strategy
- Risk Management Strategy (GV.RM), which supports operational risk decisions based on the organization’s risk tolerance and appetite statements, assumptions, and other factors
- Roles, Responsibilities and Authorities (GV.RR), which establishes defined roles and responsibilities to encourage continuous improvement and consistent performance assessments
NIST CSF 2.0 now applies to all organizations, not just critical infrastructure

NIST CSF 2.0 now applies to all organizations across government, industry, and academia, including (but not limited to) critical infrastructure. The framework has been adapted to apply to any sector and encompasses a range of organizations varying in size and cybersecurity program maturity. Broadening the scope of NIST CSF 2.0 helps make the framework helpful to all organizations, regardless of sector, type, or size to address cybersecurity challenges of all magnitudes. CSF 2.0 now includes tiers as an appendix, which provides various breakdowns of an organization’s level of maturity of managing cybersecurity risks: Tier 1 (Partial), Tier 2 (Risk-Informed), Tier 3 (Repeatable) and Tier 4 (Adaptive).
A wealth of new NIST CSF 2.0 tools are now available
NIST has created a suite of resources to help all organizations achieve their cybersecurity goals, with added emphasis on governance and supply chains. These resources are designed to provide different audiences with tailored pathways and make the framework easier to leverage.
New searchable reference tool
NIST CSF’s new reference tool simplifies the way organizations can implement NIST CSF 2.0, allowing users to browse, search and export data and details from the core guidance in human-consumable and machine-readable formats.
Informative reference catalog with mappings
The CSF 2.0 offers a searchable catalog of informative references that allows organizations to cross-reference the CSF’s guidance to more than 50 other cybersecurity documents, like NIST 800-53. Tip: if you’re using a GRC platform like Hyperproof, you can automate this process with the click of a button. Hyperproof enables you to reuse controls across multiple frameworks to satisfy requirements from different standards.
Community profiles
NIST’s new community profiles help organizations understand how their peers are leveraging the framework. This flexible framework can be used in many ways, and these community profiles provide examples of how different verticals adapt the framework’s taxonomy to fit their specific use cases.
Implementation examples
A wide variety of organizations with different needs use this framework, and as a result, guidance around supporting NIST CSF 2.0 implementation has been piecemeal over time. NIST has provided detailed information like linkages and mappings to specific cybersecurity guidance from NIST and other organizations to assist with implementation guidance. These action-oriented steps help you understand outcomes of the subcategories and answer many of your questions on how to get started.
Quick start guides
NIST has developed these targeted guides, designed for small businesses, enterprise risk managers, and organizations seeking to secure their supply chains.
What to do if you’ve already implemented NIST CSF 1.1
If your organization has already adopted NIST CSF 1.1, we recommend that you review the Govern Function to determine if you have gaps to remediate based on your current and target profiles. Additionally, you should review the implementation guidance for all subcategories to determine if there is any new guidance you want to adopt.
You will also need to update your organizational profile document to align with the realignment and consolidation of the existing categories and subcategories.
Ready to see how Hyperproof can help you manage NIST CSF 2.0?

Hyperproof’s compliance operations software can help organizations implement NIST CSF 2.0 guidelines, support ongoing control evaluation efforts, and improve the security of an organization’s information systems. Hyperproof makes complying with NIST guidelines easier by helping you:
- Leverage a starter template with built-in NIST CSF 2.0 security controls
- Quickly collect evidence to verify the efficacy of various controls
- Get a complete view of all of your compliance efforts
- Use NIST CSF 2.0 controls to comply with other cybersecurity and data privacy standards
- Map controls to multiple standards/frameworks
- Track your progress towards compliance, assign tasks, and prioritize work streams
If you’re currently using NIST CSF 1.1 and looking for a platform to help you upgrade to 2.0 when the time is right, Hyperproof has you covered. To learn more, sign up for a personalized demo.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?











