How to Customize a Risk Register Template for Your Needs
Cybersecurity threats are rising, posing significant challenges to organizations that strive to protect their assets and maintain compliance. As projects get more complicated, keeping track becomes difficult at best and dangerous at worst.
A risk register template is like a strategic checklist for your project. It helps your team identify, evaluate, and keep tabs on risks so you can still meet your deadlines and avoid potential risk scenarios. This article will explore the importance of a risk register and how to customize it to get the best outcomes for your company.
Why do I need a risk register template?
In an age where threats are increasingly more creative, targeted, and challenging, you must update your tools and methods to stay ahead. A risk register template empowers teams to refine risk assessment processes with a clear, structured roadmap for organization and ongoing management. This tool is particularly vital for large corporations facing a myriad of risks—cybersecurity, financial, legal, and operational—to address critical risks adequately.
Here are some powerful ways a risk register template can bolster your security and enhance your business operations.
Looking for a risk register template? We’ve got you covered.
A central hub for threat analysis
The risk register serves as a pivotal hub, equipping teams to effectively detect patterns in threats and system failures. This detection capability is essential for crafting focused strategies to mitigate risks and enhance cybersecurity defenses. By adopting a risk register, you initiate a collaborative effort among stakeholders, fostering a mutual understanding of risk exposure across various business units.
Improved collaboration and consistency
This collaborative endeavor creates a uniform scale for measuring risks, guaranteeing that all teams employ consistent criteria for risk evaluation. It also ensures senior leaders access standardized data, enabling them to make well-informed decisions and efficiently prioritize risk response activities.
Informed risk response choices
Armed with detailed risk data that aligns with the company’s goals and budgetary constraints, decision-makers can establish risk response strategies that are both strategically significant and relevant to the context. The risk register demands that risk owners provide precise responses, which encourages a thorough verification process to evaluate the effectiveness of existing policies and controls.
A comprehensive understanding of exposures
Such meticulousness affords a deep understanding of potential risks, aiding strategic operations, reporting, and compliance efforts. Moreover, maintaining a risk register facilitates the generation of vital enterprise-level risk disclosures, which are indispensable for meeting regulatory requirements and preparing for hearings or formal reports in case of significant incidents.
Transparency and accountability
Ultimately, the risk register enhances the organization’s transparency and accountability, improving its ability to navigate and communicate effectively in the face of unforeseen challenges. This increased clarity and responsibility protects the organization and positions it for successful risk management and compliance adherence.
When to use a risk register template
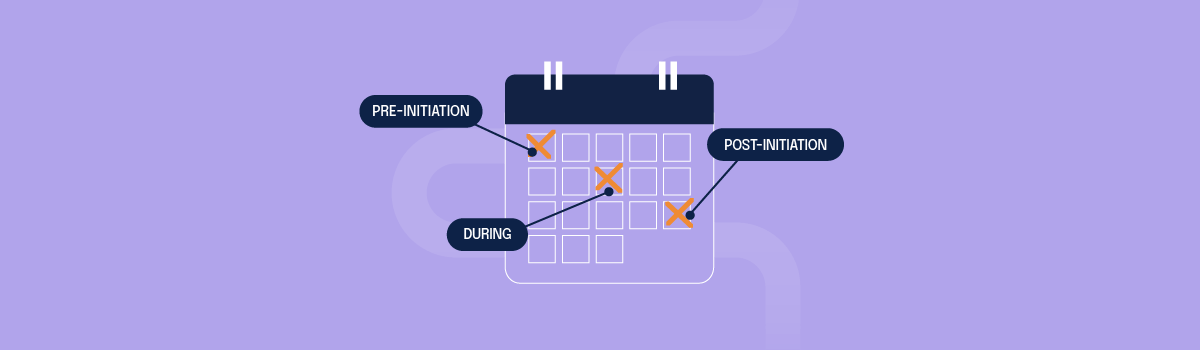
Project and risk managers find a risk register template invaluable for teams systematically identifying and organizing potential risks throughout distinct project stages—pre-, during, and post-initiation. This structured approach ensures a proactive risk management strategy, letting teams anticipate challenges in the pre-initiation phase, identify emerging risks during project execution, and assess potential issues related to project completion, handover, or ongoing maintenance in the post-initiation phase.
Here’s what that looks like across each of the phases mentioned above.
Pre-initiation
Anticipate potential risks during the project planning phase. Examples include stakeholder conflicts, resource availability, or uncertainties in project scope.
During project execution
Identify emerging risks as the project unfolds. This may include unforeseen challenges, changes in market conditions, or disruptions in the supply chain.
Post-initiation
Assess risks related to project completion, handover, or ongoing maintenance — for instance, potential issues with the project deliverables, client satisfaction, or long-term sustainability.
5 ways to customize your risk register template
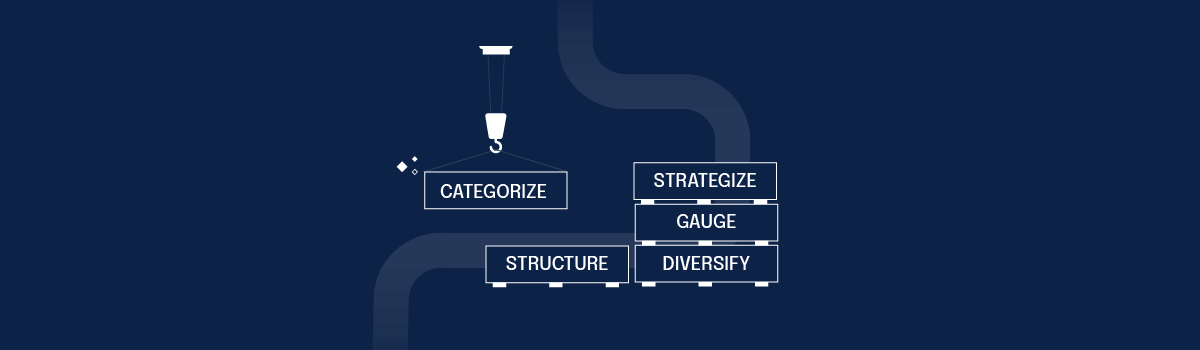
Risk register templates are not one-size-fits-all. While starting with a solid foundation is crucial, you must also invest the time to personalize it to address your specific project needs and risks. Here’s where to start.
1. Categorize your risk factors
Begin by categorizing the factors of uncertainty that could influence your project.
These categories, spanning technical, financial, legal, or environmental aspects, provide a framework for grouping and prioritizing risks while assigning responsibilities and resources. You can establish these categories using established guidelines or tailor them to align with your project’s unique characteristics and stakeholder expectations.
2. Employ diverse risk identification approaches
Use various techniques to uncover and describe potential project risks. You can employ qualitative, quantitative, or blended approaches depending on factors like project size, complexity, and data availability. These may encompass brainstorming sessions, interviews, checklists, surveys, scenario assessments, or historical data scrutiny.
3. Gauge risk implications using unique scales
Assess the likelihood and impact of identified risks using an array of measurement scales. Tailor these scales to fit the scope, quality, and precision requirements of your project and your business’ unique appetite for risk.
4. Devise risk mitigation strategies
Formulate comprehensive strategies for addressing and mitigating project risks. These strategies may involve risk reduction, avoidance, transfer, or acceptance, and their selection may hinge on risk severity, urgency, and feasibility. Common risk response strategies include mitigation (lowering risk probability or impact), contingency planning (preparing for risk occurrences), or escalation (referring risks to higher authorities).
5. Craft the structure of a risk register template
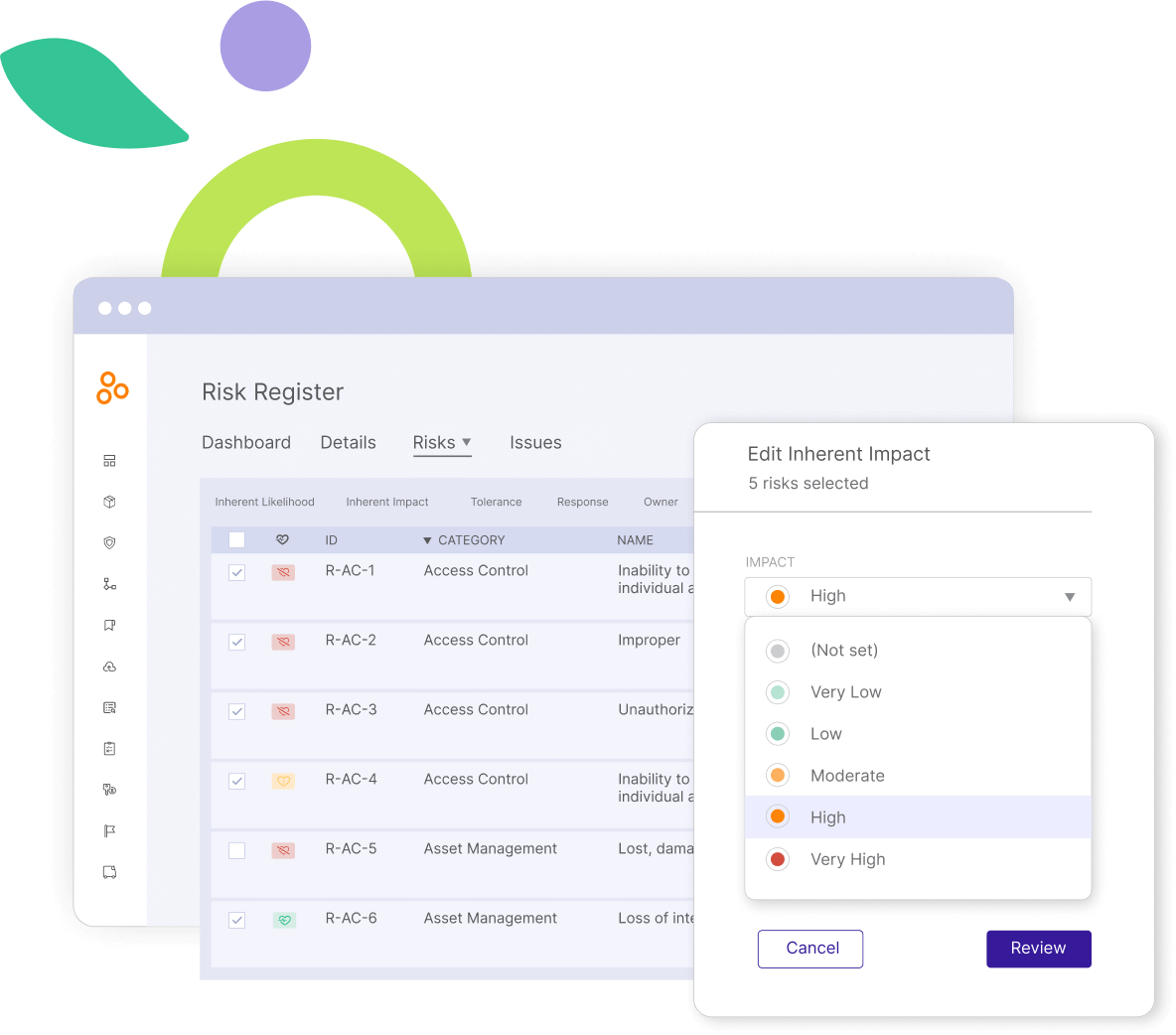
Design the layout and appearance of your risk register template, incorporating elements like columns, rows, headings, colors, fonts, and symbols. The choice of tools, such as tables, spreadsheets, databases, or specialized software, should align with your project’s size, complexity, and reporting requirements. Vital components frequently encompass risk ID, risk description, risk category, risk probability, risk impact, risk score, risk response, and risk owner.
You can adeptly navigate your project’s unique challenges and uncertainties by tailoring your risk register.
Empowering risk management with Hyperproof
Starting with an expert-designed risk register template is crucial to address the intricate challenges of today’s cybersecurity risks. As professionals who recognize this need, we’ve designed a comprehensive risk register template for large corporations to customize to fit their needs. While using this template, Hyperproof is your valuable ally, offering purpose-built risk register software that significantly enhances risk management, security assurance, and compliance efforts.
Hyperproof’s unique features, including the ability to set up multiple risk registers and customize scales for each, address the diverse needs of large corporations in sorting and prioritizing risks effectively. Beyond the template, the benefits of maintaining detailed cybersecurity risk data in Hyperproof extend past strategic risk management, providing a clear dashboard for tracking changes over time and facilitating effective communication with executives regarding potential exposures.
By embracing these innovative tools and methodologies, organizations can not only navigate the evolving threat landscape but also make informed decisions to safeguard their digital assets, ensuring resilience and success in an ever-changing cybersecurity environment.
Ready to take the first step towards organizing and modernizing your risk management?
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?