The SEC approved new disclosure requirements. Here’s what you need to know.

Big news: after over a year of delays, the SEC has adopted its proposed cybersecurity disclosure requirements. Here’s a rundown of the key takeaways:
The new requirements go into effect on September 5, 2023

The final requirements will become effective 30 days after their publication in the Federal Register, meaning they go into effect on September 5, 2023. CISOs and Board members should start preparing now to ensure their companies are in compliance with the new rules.
The Form 10-K and Form 20-F disclosures will be due beginning with annual reports for fiscal years ending on or after December 15, 2023.
The Form 8-K and Form 6-K disclosures will be due on December 18, 2023. Smaller reporting companies will have an additional 180 days before they must begin providing the Form 8-K disclosure.
Companies have 4 days to disclose a breach

Companies must disclose a material cybersecurity breach within four days of recognizing its significant impact on investors via Item 1.05 on the Form 8-K. The timing here is important, as it doesn’t come into effect from the occurrence of the breach, but when a company’s legal team classifies it as material. This timeline allows for potential delays in reporting incidents, provided the company obtains written approval from the U.S. Attorney General under special circumstances related to public safety or national security.
A material cybersecurity incident is one that is likely to have a significant impact on the company’s business, financial condition, or operations. Breaches are on the rise, too: our 2023 IT Compliance and Risk Benchmark Report found that 1 in 2 companies managing risk ad-hoc or in siloed departments experienced a material breach in 2022.
Organizations have different ways of calculating what would be considered a material breach. If you’re looking for resources to help with this decision, we recommend checking out these data breach cost calculators.
Why 4 days?
Many are asking: why four days? The SEC believes this tighter deadline will help protect investors from the financial risks posed by cybersecurity incidents by giving them more timely data on the impact of material cybersecurity incidents.
In specific circumstances, the disclosure may be delayed for national security reasons or to safeguard police investigations. Additionally, companies won’t be penalized if they don’t report an incident and have a reasonable basis for believing that the incident is not material.
Public companies must disclose the following about an event:

- The nature of the incident
- The impact of the incident
- Steps the company has taken to address the incident
- The company’s policies and procedures for managing cyber risks
It must also detail the incident’s material impact or potential impact on the firm’s financial condition and operational results. The rules go beyond merely disclosing incidents. They also include Regulation S-K Item 106, which mandates entities to discuss their strategy for handling cybersecurity risks. This includes:
- Describing processes for assessing and managing material risks from digital threats
- Detailing the effects of previous cybersecurity incidents and potential future risks
- Discussing board oversight and management’s role and expertise in handling cybersecurity risks
Additionally, public companies must disclose information about how their board oversees cybersecurity risk, including information on how experienced the board is with understanding cybersecurity.
Companies must periodically describe their approaches to managing threats

This regulation builds upon an existing effort to safeguard the financial system against potential threats such as data theft, system failure, and cyber intrusions. It’s designed to enforce entities that experience a cybersecurity incident to ascertain its materiality, and if deemed material, report it. Item 106 will also require registrants to describe the board of directors’ oversight of risks from cybersecurity threats and management’s role and expertise in assessing and managing material risks from cybersecurity threats.
The regulations apply to both domestic and foreign private issuers, requiring similar disclosures on different forms for material cybersecurity incidents and for cybersecurity risk management.
What’s the overall impact for public companies?
Public companies will have to change a lot of their processes to adhere to these new rules. They’ll need to carefully evaluate the information they disclose about cybersecurity incidents, and those that don’t comply will potentially face investor lawsuits, SEC enforcement actions, and potential damage to their reputations.
Board members will have to get up-to-speed quickly on their understanding of cybersecurity risk. CISOs will likely lean on platforms like Hyperproof to help educate their boards about their risk postures and how risk is mitigated at their companies. They can also use Hyperproof to inventory their controls when describing how they’re managing threats and risks to better answer questions from the board.
CISOs will need fast and easy reporting solutions to quickly and effectively educate their board members on these topics. Ultimately, CISOs and board members will need to be in closer contact moving forward, and CISOs will now have a bigger seat at the table to showcase their work.
CISOs should be prepared to answer the following questions:
- What do you consider our biggest business risks?
- Which risks are most likely to occur?
- Which risks would result in the highest financial impact?
- What’s your recommendation for prioritizing our budget to mitigate risk?
- What’s our post-breach protocol?
How Hyperproof can help

All of the questions above can be answered using a risk management platform like Hyperproof. Hyperproof’s risk register helps you track all of your risks, which risks are being mitigated, which are outstanding, which are most likely to occur, and which are the highest priority.
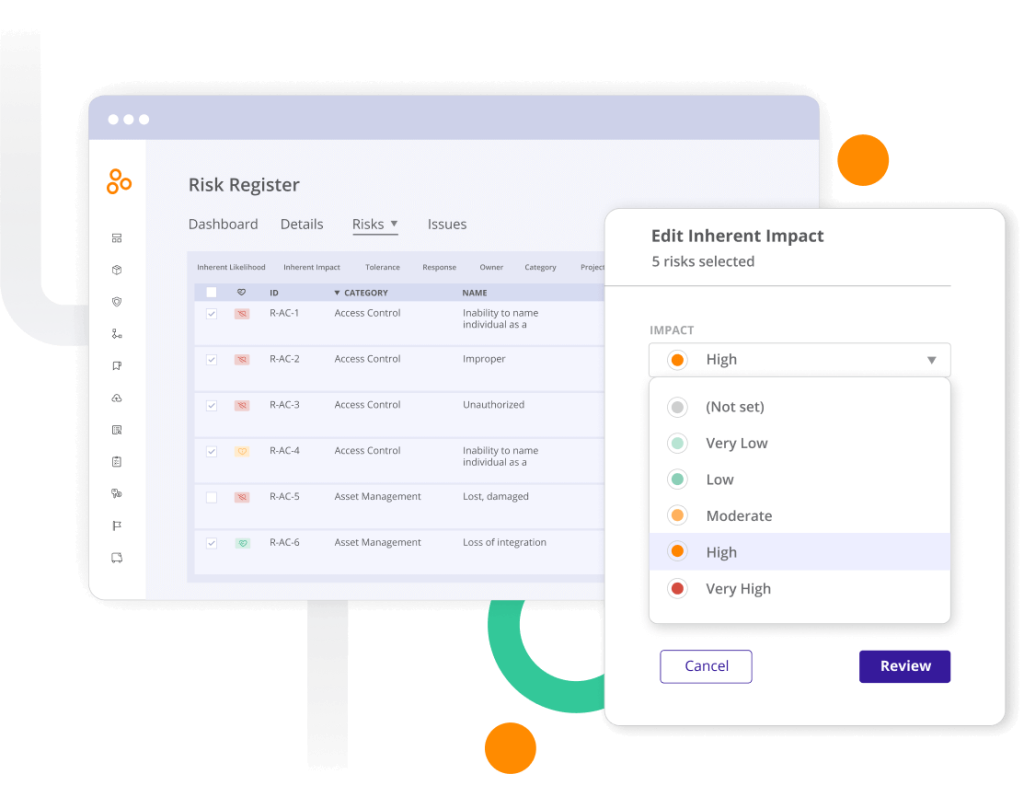
With Hyperproof’s in-depth, real-time analytics, you can understand your risk posture, strategically allocate your budget based on it, and get a full view into how your controls are tied to risks.
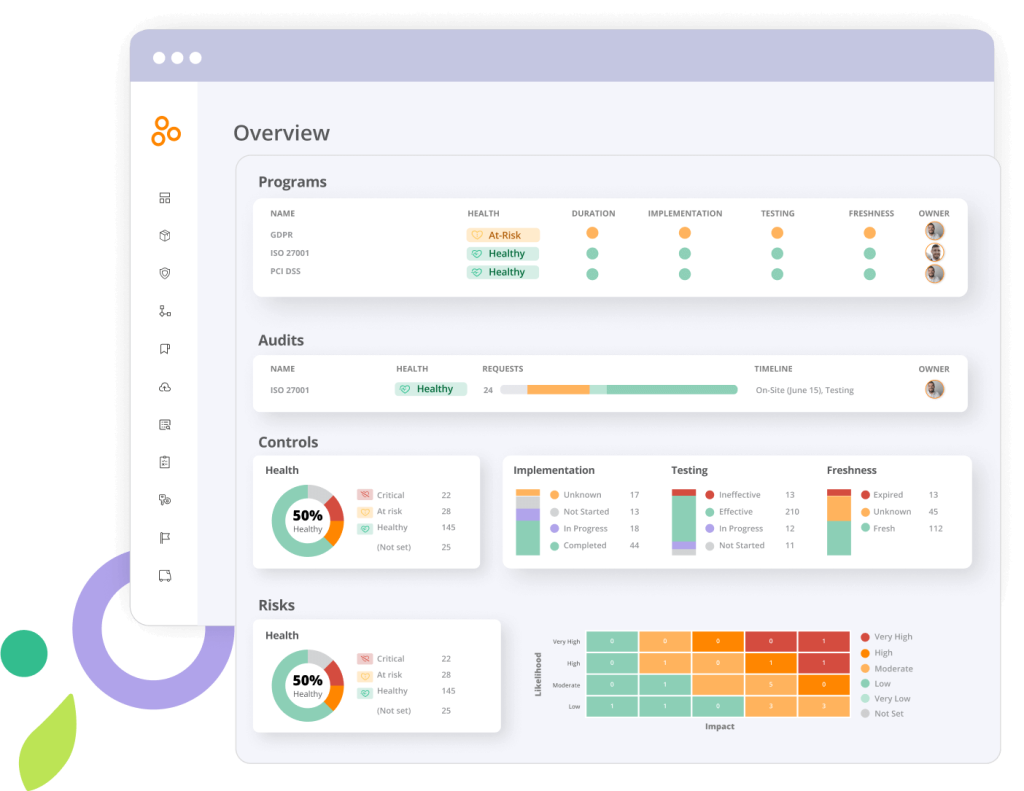
Interested in learning more?
Hyperproof can help relieve the burden of new processes the SEC disclosure rules will place on you and your board. Get in touch to see a demo!
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












