SOC 2® Type 2: Preparing for Your First Audit

As a business leader, you know the stakes are high when it comes to data security. Whether you’re a SaaS company, a fintech startup, or a growing enterprise serving clients with stringent compliance requirements, achieving SOC 2® Type 2 certification is a critical step toward earning and maintaining your customers’ trust. But how do you prepare for such a rigorous audit, especially if it’s your first time?
Here’s everything you need to know to demystify the process, set yourself up for success, and avoid common pitfalls along the way.
Why SOC 2® Type 2 matters
Your clients trust you with their data, and SOC 2® Type 2 certification proves you’ve implemented robust controls to protect it. Unlike the SOC 2® Type 1 report, which only assesses your controls at a specific point in time, the SOC 2® Type 2 report evaluates how effectively those controls operate over a period (usually six months to a year).
The certification is often a prerequisite for doing business with enterprise clients, demonstrating your commitment to security, availability, processing integrity, confidentiality, and privacy — the five Trust Services Criteria.
How early should organizations engage an auditor?
Organizations should engage an auditor at least 3-6 months before the formal SOC 2® Type 2 audit period begins. Early engagement allows for initial discussions to clarify the scope of the audit, including which Trust Service Criteria will be assessed and what documentation and evidence will be required.
While auditors conducting the formal review avoid readiness work to maintain objectivity, they may recommend SOC 2® readiness tools or consultants to help your organization prepare. This proactive approach reduces surprises during the audit, ensures proper evidence collection, and sets the foundation for a successful certification process.
Want to see how ready your organization is for SOC 2®?

Let’s break down the steps for a successful SOC 2® Type 2 audit preparation.
Step 1: Understand the Trust Services Criteria
SOC 2® Type 2 audits focus on the Trust Services Criteria, which are essential for protecting and managing data responsibly. These criteria include:
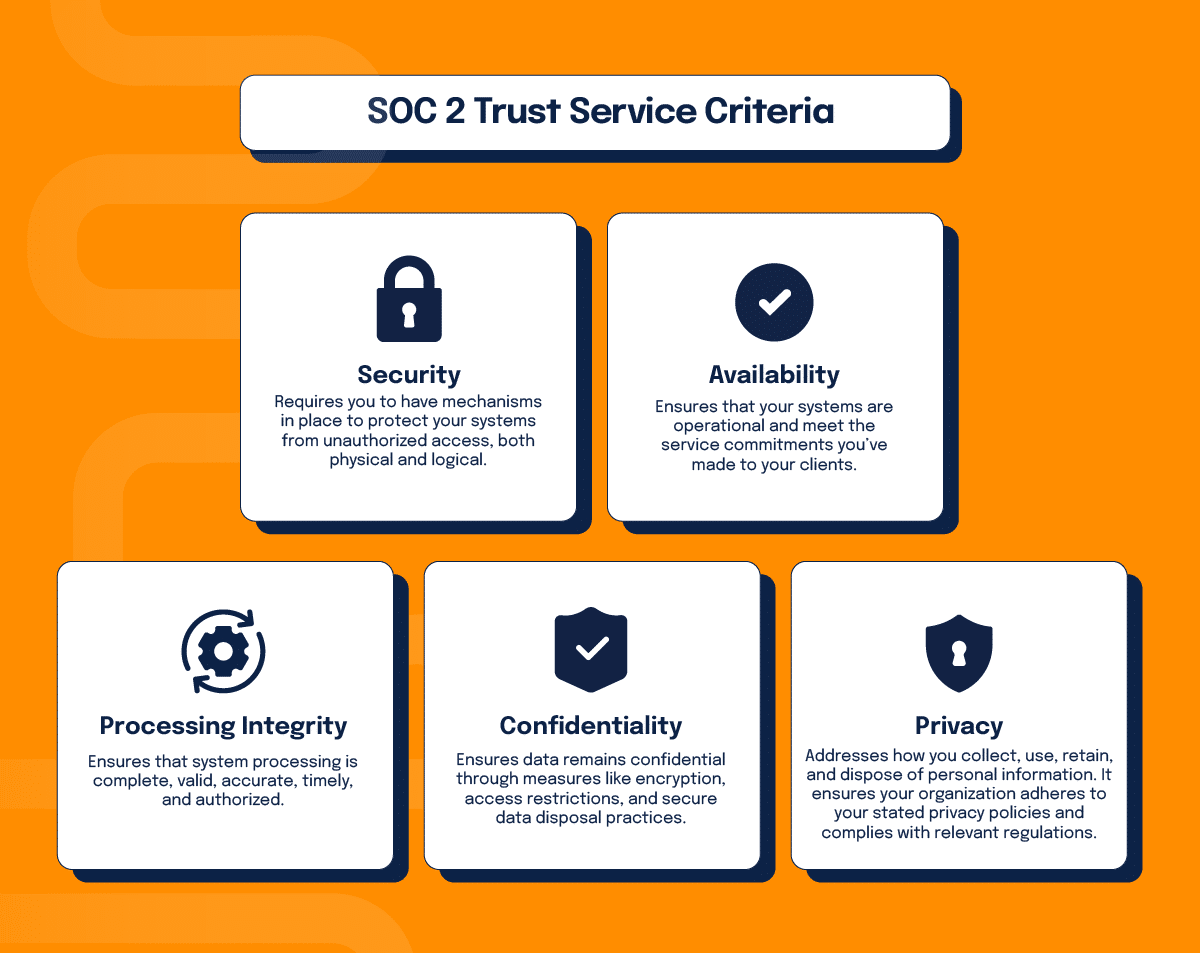
1. Security
This is the foundation of SOC 2®. It requires you to have mechanisms in place to protect your systems from unauthorized access, both physical and logical. This includes everything from firewalls and encryption to robust access control policies.
2. Availability
This criterion ensures that your systems are operational and meet the service commitments you’ve made to your clients. It involves maintaining system uptime, disaster recovery plans, and adequate resources to support service availability.
3. Processing Integrity
This is about ensuring that system processing is complete, valid, accurate, and authorized. If your systems handle transactions or data processing, this criterion ensures that these operations are executed as intended.
4. Confidentiality
Whether it’s customer data, intellectual property, or proprietary business information, this criterion ensures it remains confidential through measures like encryption, access restrictions, and secure data disposal practices.
5. Privacy
This criterion addresses how you collect, use, retain, and dispose of personal information. It ensures your organization adheres to your stated privacy policies and complies with relevant regulations like GDPR or CCPA.
Getting to know the Trust Services Criteria
You might be wondering, “How do I familiarize myself with the Trust Services Criteria?” Start by:
Mapping operations to the criteria
Determine which criteria are relevant to your business. For example, if you don’t handle personal data, the Privacy criterion may not apply. Tailor your scope to focus on what’s most pertinent to your operations.
Evaluating client contracts
Review client agreements and expectations to ensure you’re aligned with their requirements regarding security, availability, and other criteria.
Engaging key stakeholders
Involve department heads, IT leaders, and legal teams to ensure a comprehensive understanding of how your operations intersect with the Trust Services Criteria.
Step 2: Perform a readiness assessment
Before diving into the audit, conduct a readiness assessment to identify gaps in your current controls. Think of this as your diagnostic phase — you’re pinpointing areas where you need to improve before inviting an auditor to evaluate your systems.

Review existing controls
Take an inventory of all current controls, including both technical and administrative safeguards. This involves reviewing access controls, encryption protocols, incident response plans, and other measures you’ve implemented. Ensure they are aligned with the Trust Service Criteria, and document your findings. This baseline assessment provides clarity on where your organization stands.
Conduct a gap assessment
Once you’ve reviewed your controls, identify any shortcomings by conducting a gap assessment. For instance, check if your encryption protocols meet industry standards or if you have a formalized incident response plan. If not, consider the potential impact of these gaps on your security posture and ability to meet client expectations.
Prioritize next steps by potential impact
Rank gaps based on their risk level, impact on your operations, and relevance to client commitments. High-priority items should be addressed first, such as vulnerabilities that could expose sensitive data or deficiencies that would fail an audit. Assign responsibility and deadlines for resolving each issue to keep your team on track.
Step 4: Build a strong governance framework
Your audit will scrutinize the governance practices underpinning your controls. A strong governance framework ensures you’re not only compliant but also resilient to evolving risks.
Policy management
Your policies should be comprehensive, clearly written, and easy for employees to understand. Policies must cover key areas like data protection, access controls, incident response, and employee responsibilities. Regularly review and update policies to keep them aligned with changing regulations and industry standards.
Employee training
Conduct regular training sessions to educate employees about your security and compliance requirements. Tailor the training to specific roles so that individuals understand how their actions contribute to the organization’s overall security posture. Include periodic refreshers and assessments to reinforce knowledge and identify ways to improve.
Documentation
Maintain detailed records of all processes, decisions, and incidents related to compliance and security. This includes meeting minutes, training logs, incident response activities, and access control changes. Use centralized tools or repositories to store and organize documentation, making it easy to retrieve during the audit.
Step 4: Implement and test controls
SOC 2® Type 2 isn’t just about having the right controls; it’s about proving they work. This involves:
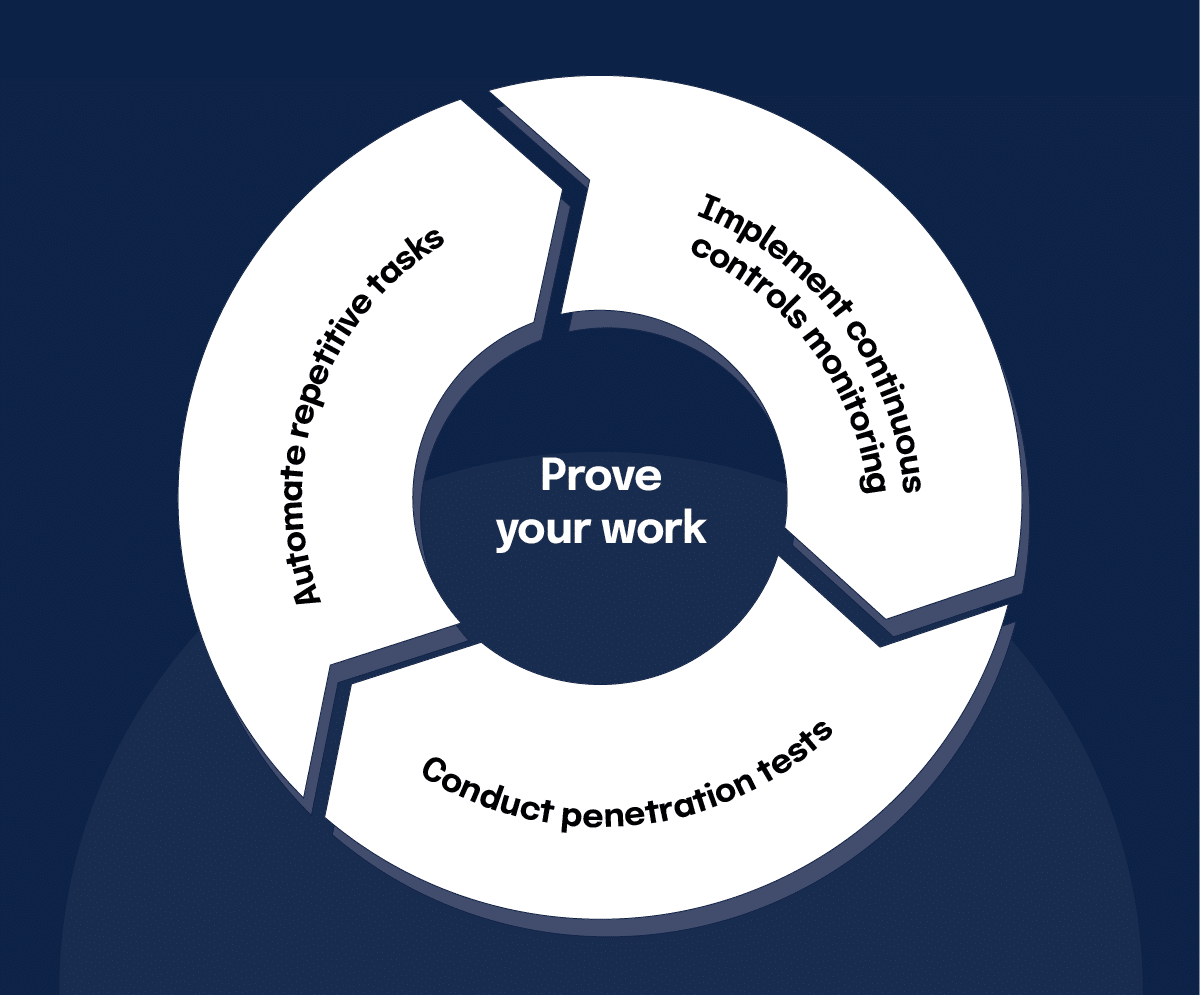
Automate repetitive tasks
Implement tools that can handle repetitive tasks like log monitoring, access reviews, and alerting for suspicious activities. For example, automated monitoring systems can flag unauthorized access attempts in real-time. Automation also simplifies reporting, making it easier to generate audit-ready evidence.
Implement continuous control monitoring
Continuous monitoring is the backbone of an effective control environment. Use advanced monitoring tools to track system activity, detect vulnerabilities, and log all relevant events. Monitoring tools should be configured to generate alerts for anomalies, such as unusual login patterns or unexpected changes to critical files. Establish clear processes for reviewing these alerts and escalating them as necessary.
Conduct penetration tests
Conduct penetration tests to identify security weaknesses, run disaster recovery drills to validate business continuity plans, and perform internal audits to assess compliance with policies. Document test outcomes and use the results to refine your controls. Testing should be an ongoing process—this ensures your systems remain robust against evolving threats and meet the audit’s consistency requirements.
Remember, the audit period requires consistent control operation. You can’t afford lapses or inconsistencies during this time.
Step 5: Streamline evidence collection
One of the most time-consuming aspects of a SOC 2® Type 2 audit is gathering evidence. From access logs to security policies, you’ll need to demonstrate compliance with your controls. Here’s how:

Centralized storage
Use a single platform to store and organize evidence. This reduces the risk of losing documents and ensures that all relevant data is easily accessible to auditors. A centralized repository also improves collaboration among teams by keeping everyone aligned on what’s already submitted and what’s still outstanding.
Real-time tracking
Implement a tracking system to monitor evidence requests and submissions in real time. This helps identify bottlenecks and ensures timely responses to auditor requests. A well-maintained tracking system can also highlight gaps in your evidence collection process, allowing you to address them proactively.
Collaboration
Involve all relevant teams, including IT, HR, and legal, in the evidence collection process. Assign specific responsibilities to team members to avoid duplication of effort and ensure accountability. Clear communication channels between teams can streamline the workflow and prevent delays in submitting evidence to auditors.
Leverage Hypersyncs
Hypersyncs are data connectors that automatically collect evidence from dozens of cloud-based apps and services on-demand or according to your schedule.
Reuse evidence across multiple frameworks
Reuse the same evidence across compliance frameworks so you don’t have to fetch the same piece of evidence multiple times.`
Step 6: Conduct a mock audit
A mock audit simulates the formal audit process and helps your organization identify gaps, weaknesses, or areas for improvement before the actual audit begins. Here’s how to stage an effective mock audit:
Select an experienced team
Assign internal or external experts to conduct the mock audit. Ensure they have a strong understanding of SOC 2® requirements and can objectively evaluate your controls.
Mimic the formal process
Structure the mock audit to mirror the real audit as closely as possible. This includes reviewing your policies, evidence, and control operations over the designated audit period. Simulate the types of questions and evidence requests you’ll face from an external auditor.
Implement improvements
Use the findings to refine your controls and processes. Address deficiencies systematically, assigning responsibility and setting deadlines for corrective actions. This ensures your organization is fully prepared when the actual audit begins.
A well-executed mock audit not only boosts your team’s confidence but also reduces the risk of surprises during the formal audit process.
Step 7: Communicate with Stakeholders
Your SOC 2® Type 2 journey doesn’t happen in a vacuum. Keep stakeholders informed and engaged throughout the process. This includes your board of directors, senior leadership, and clients who may be eagerly awaiting the results.
Provide regular updates
Provide progress updates at key milestones. This could include completing the readiness assessment, implementing key controls, and submitting evidence to auditors. Keeping stakeholders informed builds confidence and demonstrates your organization’s commitment to transparency and accountability.
Transparency
Be honest about challenges or delays. If there are unforeseen obstacles, communicate them promptly and provide a plan to address the issues. Transparency fosters trust among stakeholders and ensures they remain supportive throughout the audit process.
Celebrate your wins
Recognize team members’ contributions to building a culture of security and compliance. Highlighting successes, such as passing a mock audit or completing a significant milestone, boosts morale and reinforces the importance of everyone’s efforts in achieving SOC 2® certification.
Step 8: Conduct a post-audit review
Once the audit is complete and you’ve received your report, take time to reflect on the experience and plan for the future.
Analyze findings
Review any deficiencies or recommendations noted by the auditor. Analyze the root causes of any findings and develop a plan to address them. This may involve revising policies, enhancing training programs, or implementing additional controls to prevent future issues.
Continuous improvement
Use these insights to strengthen your controls and governance framework. Treat the audit findings as opportunities for growth rather than setbacks. Regularly revisit and refine your processes to ensure they remain effective and aligned with evolving industry standards.
Share that you’ve become compliant
Share the results with clients, prospects, and stakeholders to demonstrate your commitment to security and compliance. Highlighting your SOC 2® Type 2 certification can be a powerful marketing tool, showcasing your dedication to protecting customer data and meeting industry expectations.
Common pitfalls to avoid

Identifying and collecting documentation
Keeping track of compliance documents can be overwhelming. Hyperproof centralizes all audit documentation, making it easy to organize, retrieve, and track evidence.
Defining the audit scope
An unclear audit scope can lead to unnecessary work or missed compliance areas. Hyperproof helps define and manage the audit scope by aligning it with the relevant Trust Services Criteria.
Communicating with the auditor
Poor communication with your auditor can lead to delays or misunderstandings. Hyperproof streamlines communication by providing a collaborative platform where auditors can request and review evidence in real-time.
Ensuring data integrity
Inconsistent or incomplete data logs can raise red flags. Hyperproof automates data collection and integrity checks to ensure consistency across compliance records.
Not conducting an audit readiness assessment
Skipping a readiness assessment can result in unexpected gaps. Hyperproof offers automated self-assessments to identify and address compliance gaps before the formal audit.
Overestimating compliance
Assuming all controls are in place can be risky. Hyperproof continuously monitors compliance status, helping teams identify weaknesses early.
Confidentiality concerns
Mishandling sensitive audit-related data can expose your organization to risks. Hyperproof ensures access control, encryption, and role-based permissions to protect compliance-related data.
Managing a complex security infrastructure
Large or decentralized IT environments can create oversight challenges. Hyperproof integrates with existing security and compliance platforms, providing a unified view of compliance efforts.
Tracking change management
Untracked system and process changes can complicate compliance efforts. Hyperproof maintains an auditable history of changes, helping organizations stay compliant and prepared for audits.
How Hyperproof can help with SOC 2® Type 2 audits
Hyperproof eases the complexities of preparing for SOC 2® Type 2 audits, helping organizations reduce time and effort while maintaining accuracy and transparency. With a centralized platform, we enable you to manage evidence collection, track progress, and document compliance activities in real-time. Automation features simplify repetitive tasks like monitoring, reporting, and evidence submission, ensuring consistent control operation during the audit period.
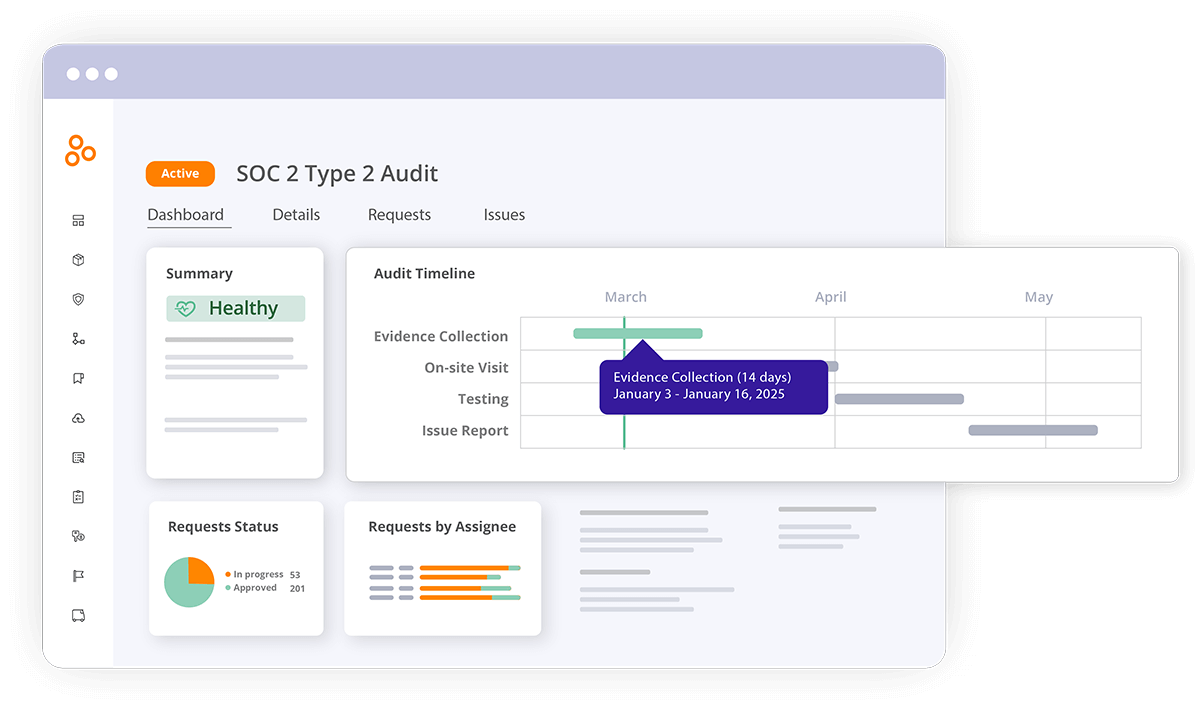
The Hyperproof platform enhances collaboration across teams, enabling IT, legal, HR departments—and auditors—to work seamlessly together. Built-in reminders and customizable workflows ensure nothing is overlooked, keeping your organization on track to meet auditor expectations. Hyperproof also provides comprehensive dashboards for stakeholders, making it easy to communicate progress and build confidence in your compliance efforts.
By simplifying the audit process, Hyperproof empowers organizations to focus on strengthening their security posture rather than navigating administrative hurdles. It sets the stage for successful SOC 2® Type 2 certification.
Preparing for your first SOC 2® Type 2 audit can feel overwhelming, but it’s also an opportunity to elevate your organization’s security posture and build trust with clients. By approaching the process methodically—from readiness assessments to post-audit reviews—you’ll not only earn your certification but also position your company for long-term success.
Remember, the audit isn’t the end of the road. It’s a milestone in your ongoing commitment to security and excellence. So roll up your sleeves, rally your team, and get ready to take your organization to the next level.
Ready to see how Hyperproof can help you with your SOC 2® type 2 audit?
Additional resources:
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












