The Ultimate Best Practices Guide
Essential Techniques for Evidence Collection and Preservation in Security Assurance
Years ago, collecting evidence was simpler. Today, it’s a tedious task and one fraught with risk if done inconsistently. This guide will help compliance and security assurance leaders understand the challenges in collecting evidence for modern data protection compliance and best practices for moving forward, and it will provide an understanding of the technology capabilities needed to collect and manage evidence more efficiently.
A big security assurance challenge: the generation and preservation of evidence
Evidence collection is hard because the demand for businesses to demonstrate compliance has risen dramatically in our modern, interconnected, data-intensive business environment. Businesses today reach more potential customers, rely on more vendors and suppliers, and collect huge troves of data, which has given rise to a seemingly endless parade of regulations around data privacy, process integrity, and security.
Each of those regulations brings its own demand for assurance that your business meets its compliance obligations. All those regulations have also led to the proliferation of assurance frameworks: ISO 27001, the NIST Cybersecurity Framework, PCI DSS, SOC 2, HITRUST, and many more. Each framework then requires the collection of evidence.
Gathering evidence can be challenging for a host of reasons. For one, many organizations don’t currently have control procedures that are implemented in ways that generate valid, time-stamped evidence. Let’s take a look at SOC2 Type 2 — a common security assurance report many companies must achieve these days — as an example.
A closer look at SOC 2® evidence collection
A System and Organization Control (SOC) 2® report documents the results of an auditor’s examination of the accuracy of the service organization’s description of its system, the design effectiveness of the internal controls, and the operating effectiveness of internal controls.
From the perspective of a SOC 2® assessor, a control operated effectively if, throughout the entire audit period, the control was consistently performed in accordance with the underlying procedures. To test operating effectiveness, your SOC 2 auditor will examine evidence that your organization produces when executing the control. In simple terms, if the evidence doesn’t exist, the control doesn’t exist. In fact, the auditor in a SOC 2® exam must fulfill evidentiary requirements documented in SSAE 18. (For more help, read our blog and find a helpful SOC 2® audit checklist.)
Keiter – a tax, audit, and consulting firm – provided the following example to highlight differences in documentation retained in an organization with a SOC 2® ready process.
Not SOC 2® ready
Prior to granting user access to the computer system, the user’s supervisor requests in person, over the phone, or via email the user’s access.
Evidence retained:
Sporadic evidence is retained in email only. If the employees that are party to the email leave the organization, the little evidence that exists may be destroyed.
SOC 2® ready
Prior to granting user access to the computer system, the user’s supervisor completes a digital form that indicates the specific roles to which the user requires access.
Evidence retained:
The digital form automatically documents approvals from the employee’s supervisor. The request is time-stamped, so the auditor can verify that access was not granted prior to being approved.
Other evidence collection challenges
- Evidence is not collected in a timely manner. Even when controls do exist and evidence can be generated, evidence often isn’t collected in a timely manner because people get busy or don’t realize why it’s important to submit evidence to their compliance team.
- An excess of time spent searching for evidence. In many organizations, evidence is poorly labeled, isn’t associated with specific compliance requirements, or is stored hazardously in disparate systems (e.g., hard drive, G-Drive, SharePoint, email threads) – making it nearly impossible to retrieve that evidence quickly or reuse it for multiple assessments.
- Lack of clarity around controls. Business unit teams might not understand what controls they’re assuring for and how to generate sufficient appropriate evidence, leading them to give incorrect or incomplete answers. This means more work for compliance professionals as they track down the correct evidence.
Since collecting evidence is rife with difficulties, many compliance professionals race against the clock in the days leading up to a scheduled audit gathering all the evidence their auditor has asked for. They end up gathering the last pieces of evidence during the audit itself. This is a hazardous move because if an external auditor finds that certain evidence is missing (or it’s not what they’d requested), they’re going to report the issue and it may be the cause for failing the audit.
Listen to Aaron Poulsen, Director of Information Security and Compliance at Hyperproof, talk about why waiting to collect evidence until an audit is starting is a highly risky and unreliable strategy:
Evidence collection challenges at a Fortune 500 Company
A data protection compliance director at one Fortune 500 company that sells communications products and services told Hyperproof that the need for her company to demonstrate compliance is pervasive. Her company’s customers are asking her team to produce evidence of compliance in three different ways:
1
Customers are asking the company to prove that the company’s products and operating environments are meeting specific assurance frameworks and have gone through third-party evaluations (e.g., SOC 2® reports, ISO 27000 series of certifications).
2
Customers frequently demand a response to one-off information security questionnaires.
3
Customers are asking the company to make contractual commitments to comply with different security and data privacy frameworks.
This data protection compliance team must collect a tremendous amount of evidence showing that all of their product lines and manufacturing sites are meeting specific assurance frameworks. If the compliance team couldn’t quickly pull up evidence to fulfill customers’ requests for assurance, the company would be at risk of damaging customer relationships and losing long-term customers as the trends listed above continue.
No way to reuse evidence
Because the compliance team didn’t have a central place to organize their evidence, the team had to start from ground zero and collect a whole new set of evidence each time an audit was scheduled.
Business unit operators had assessment fatigue
Product teams and other stakeholders spent a lot of time answering the same questions repeatedly for different data security and data privacy assessments. They were getting to a point of exhaustion with all the requests for evidence they had to respond to.
No central source of truth
Without a central source of truth for evidence and controls-related information, different product teams weren’t able to benefit from the security/compliance work other groups have already done.
Elevated legal risk
Because the compliance professionals didn’t have a tool that allowed them to “show their work” (i.e., map evidence of particular controls to requirements in data privacy regulations), they couldn’t do the work consistently. Not being able to show this type of work puts the organization at higher risk of violating certain data privacy laws.
Hear this compliance leader’s summary on the evidence management challenges her organization (a Fortune 500 company) is facing.
Challenges when gathering evidence to assess vendor risk
As you onboard more third parties, the workload involved in assessing each vendor’s risk profile also goes up. You’ll send more questionnaires to your vendors and suppliers, and if you do this manually, they might get lost, overlooked, or never retained. You might receive erroneous data or data in multiple formats that need an integration process to consolidate it into something meaningful. Hyperproof’s 2021 IT Compliance Benchmark Survey found that 1 in 2 IT risk management professionals have trouble understanding the true risk profile of their vendors.
What a better approach to evidence management looks like
The solution here is to move away from manual processes for evidence collection in favor of compliance operations software that brings efficiency, discipline, and consistency to the evidence management process.
Regardless of the specific solution you choose, it should have several important capabilities.
1. Ability to manage multiple assurance frameworks and crosswalk controls
Controls include policies, activities, processes, procedures, and technical solutions your business has committed to putting in place in order to meet compliance requirements and to mitigate risks.
The tool should be able to manage multiple assurance frameworks and should specifically empower control mapping (also called crosswalks) so you can see where two or more frameworks have overlapping requirements and all ask for the same information. This allows you to tailor your evidence request so one answer can satisfy several frameworks’ demands and so you don’t overwhelm control owners in the business operating units.
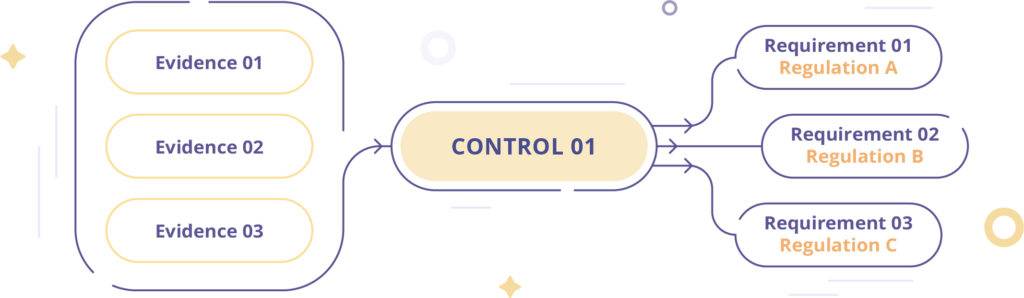
Listen to why this compliance leader believes that having a tool that allows evidence to be mapped to multiple controls and frameworks is essential for mitigating legal risks.
Common evidence requested across multiple data protection compliance frameworks

Access control
Data classification and retention policies
Change management tickets
Privacy policies

Security policies
Business continuity plan

Incident response plan/policy
2. Ability to assign owners and set review cadences for controls and evidence
You want a tool that allows you to designate individuals or teams as responsible for operating controls and collecting evidence. The ideal tool will allow you to set review cadences on controls and different types of evidence (e.g., weekly, monthly, quarterly, annually) and specify due dates so you don’t have to remind people to submit fresh evidence manually.
You should not wait until right before an audit starts to gather all needed evidence because if the auditor finds that certain evidence is missing (or it’s not what they requested) during the audit, they will report on it and may give you a qualified opinion.
3. Automated alerting and escalation for any remediation work that hasn’t been completed.
Having a tool that automatically alerts you when any evidence collection or remediation work hasn’t been completed can save a lot of time and ensure that your evidence stays current (and is acceptable to your auditor). For example, you might task a business unit leader with implementing a new policy or restructuring an approval process to make the controls more effective. You want a system that can send automated reminders to that unit leader about the work that they need to do or, if the work isn’t done by the deadline, to escalate that alert to you and the person’s supervisor.
Listen to this compliance leader at a Fortune500 company discuss the key capabilities she needs from an evidence management system:
4. Automated evidence collection
Evidence comes in different formats. Some may be policies (e.g., security policies, privacy policies, business continuity plans), and others will be snapshots capturing what happened within a particular system or process at a particular time. This type of evidence needs to be “fresh” for it to be considered valid by an auditor — that is, collected on a frequent basis (e.g., daily, weekly, monthly).
Evidence that needs to be fresh may include backup settings on your cloud databases, encryption settings on your applications that process high-risk data, access groups and lists of users for cloud databases, code change management evidence, etc. This information may come from cloud-based services such as AWS, Azure, GitHub, Google Cloud, or other established providers.
If your compliance management solution can automate the collection of such evidence, it goes a long way in reducing assessment fatigue. Any automatically collected evidence should come with metadata attached so you have visibility into exactly where the evidence came from and when it was collected. Including that metadata in your evidence is crucial to demonstrating to your auditors that the evidence you’re giving them is trustworthy.
5. Ability to categorize and tag evidence for easy retrieval
You want to be able to organize your evidence (e.g., within folders or categories) so you can easily find and retrieve relevant information and quickly answer questions you’re likely to get from your customers, auditors, regulatory examiners, or other stakeholders.
Listen to this compliance leader, who talks about why having a central repository
for evidence is “hugely helpful” to her organization:
6. Secure storage of evidence and the ability to customize roles and permissions
Ironically, even risk and compliance software companies don’t always have the strictest security controls over their environment and aren’t immune from data breaches. Risk and compliance software startup LogicGate confirmed a data breach in April 2021 in which the protected health information of 47,035 individuals were potentially compromised. LogicGate explained in breach notification letters that an unauthorized individual gained access to credentials in its Amazon Web Services cloud storage servers which are used to store backup files of customers that use its Risk Cloud platform.
When you use 3rd party compliance software to collect, manage, and store evidence, it’s important to understand the vendor’s security posture and ensure they have adequate security controls in place to keep your sensitive corporate/employee data safe.
Further, you also want to check that your compliance software provides the ability to restrict access to a need-to-know basis. For instance, you wouldn’t want an engineer submitting evidence of backup settings in your AWS databases to be able to see employee background check reports submitted by HR. You also wouldn’t want a third-party auditor to see all of the information you’ve stored in the compliance platform.
Hear from Aaron Poulsen, Director of Information Security and Compliance on why compliance leaders must solve their evidence collection challenges now, and how this impacts an organization’s ability to pass an audit:
The business value of automating evidence collection and management
Having a compliance management software that allows you to streamline evidence management not only makes your compliance team’s lives easier, but also sharpens your compliance program’s performance so that it can be a better asset to the business. Here are the key benefits you can expect to reap when you take the time to set up a software platform to manage your evidence:
1. Save time
A more automated system of evidence collection and management will reduce the need for tedious, time-consuming tasks among your employees. This will let them devote valuable human brainpower to more sophisticated work. Among your own compliance team, this could include tasks such as developing new policies, improving control design, or running more sophisticated testing. Among the business units asked to provide evidence, they could go back to whatever their primary duties are.
2. Build a competitive advantage based on a superior security posture
Meanwhile, by collecting more precise and accurate evidence and doing so more quickly, you’ll be able to produce that evidence more efficiently for your customers or sales prospects when they ask for it. Your security team will be able to respond to security questionnaires more quickly and accurately. That makes you less of a third-party risk for your customers and a more attractive business partner compared to your competitors that don’t have their security compliance program under tight control. A stronger security compliance function truly is a competitive advantage in the marketplace.
According to Carl Lombardi, VP of Operations at Prime8, a preferred consulting firm to Fortune 50 tech, communications and health companies – having compliance software like Hyperproof gives him confidence in the assertions the company makes to customers and sets the firm apart as a trusted services provider.

With Hyperproof as the system of record of all of my work, I am ready for a regulatory body or customer to come in and do a spot audit at any time. I would feel comfortable showing an auditor what the company is doing, because the evidence is in the tool.
Carl Lombardi
VP of Operations // Prime 8 Consulting

3. Get a better forecast on how much effort is required to launch a new product or expand into a new market
When it’s easy to map evidence to multiple controls and assurance framework requirements, you can get a quick read on how much due diligence your team must do to meet a new privacy or security statute to be able to launch a new product in a new region.
4. Better reporting of compliance and security risks to senior management and the board
Further, better evidence collection also helps with reporting compliance and security risks to senior management and the board. You can state the organization’s overall compliance posture more confidently and drill down more easily into whatever topic might come up for discussion. That lets you fully participate in strategic discussions and keep security issues at the front of those conversations.
Hear from this senior compliance leader describe why great reporting is a meaningful feature of compliance software:
How does Hyperproof help organizations manage evidence collection at scale?
See below for a short description of how Hyperproof supports streamlined evidence management.
Re-use evidence to reduce assessment fatigue
With Hyperproof, all evidence can be centrally stored, categorized appropriately, labeled, mapped back to specific controls and regulatory requirements, and made accessible to stakeholders across all various corporate and product groups.
Automatically collect the latest policies
Security assessments always involve an auditor’s review of your company’s current security policies, incident response plan, business continuity plan, privacy policies, and other documents. Hyperproof integrates with many cloud-based file storage systems so the latest versions of important company policies and documents can be pulled into Hyperproof automatically.
Automatically collect fresh evidence from cloud services
With Hypersync, automatically collect proof from dozens of cloud-based apps and services on a cadence or on demand. Types of proof you can automate include: Backup settings, encryption settings, access groups, list of users, code change management evidence, and more. All proof comes with meta-data, such as where it comes from, timestamp, the user who set it up, etc., so auditors trust that the evidence is credible.
Reduce legal risks
Many data privacy laws require businesses to conduct due diligence to back up the compliance representations they make. In Hyperproof, evidence can be labeled as satisfying a particular type of control or legal requirement; this helps put due diligence in place much faster and minimizes legal risk.
Evidence refresh nudges
With Hyperproof, compliance pros don’t need to email or message colleagues on Slack to remind them to provide fresh evidence anymore. Automated reminder workflows can be set up — allowing compliance pros to spend their time on higher-level tasks.
Want to see Hyperproof evidence collection and management in action? Book a demo with our team or watch an overview of how evidence collection works in our platform.
Ready to see
Hyperproof in action?









