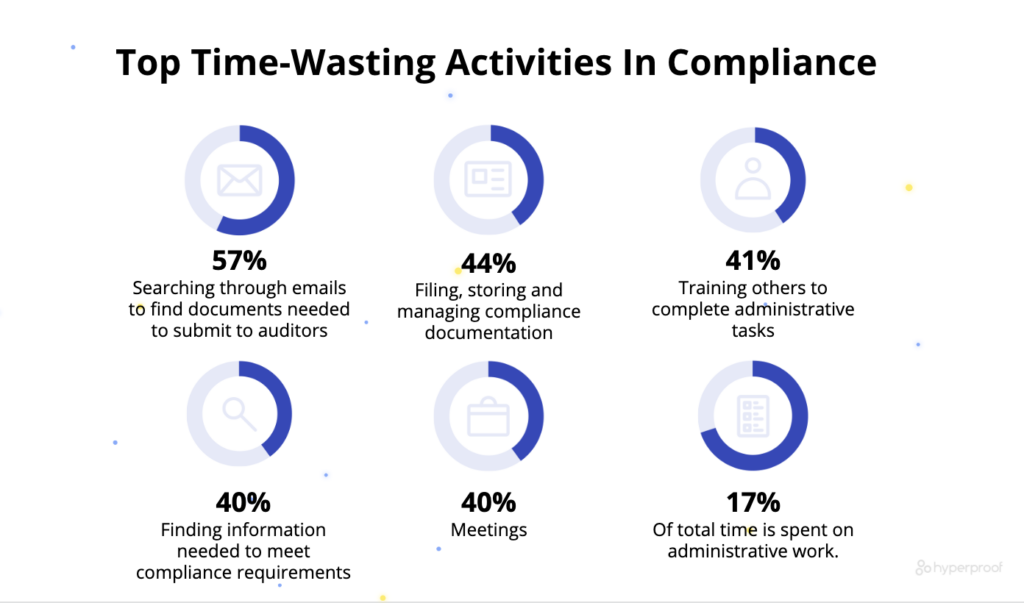
10 Most Common Information Security Program Pitfalls
Editor’s note: This is a guest post written by Peter vR Sternkopf, President and CEO of Vigilant Systems.
There’s a myriad of mistakes that can torpedo the most well-intentioned and carefully designed information security program. Our experience working with customers in the InfoSec field is consistent as to what mistakes have the biggest impact on their business. Below, we’ll examine the ten most common information security program pitfalls and provide some perspective to avoid them.
#1 pitfall – not understanding who the security program is meant to benefit
Understanding who the beneficiaries of the information security program really are is necessary for success. All of these should be considered customers of the company’s security program:
- Originators – ultimately, and most importantly, the purpose of information security is to protect the individual or originator that either owns or would be adversely affected by negative consequences resulting from the exposure of their information.
- Clients – the consumers of company products and/or services. Clients most always have entrusted their information to the company you work for; therefore, it is paramount in maintaining their trust by protecting their information. Additionally, and most often, meeting the requirements of a specific security framework is driven by clients.
- Shareholders – specifically individuals or organizations with a financial interest in the company. It goes without saying that information security breaches can have a severe and lasting monetary impact on shareholder interest.
- Stakeholders – individuals within the company, which may include board members, who have an interest in the company outcome. A breach of information in the company’s possession can have severe and lasting consequences to the health and viability of the company.
- Employees – arguably, the staff within the company are absolutely critical, not only to the success of the business but also are the lynchpin to the success of the information security program.
- Intellectual Property – not quite the same personal stake in the consequences of poorly protected information, but company intellectual property is no less important than an individual’s information. Protecting company information assets is absolutely paramount in maintaining a healthy business.
- Partners – partnering with other organizations to ensure a successful and enriching product or service experience, is essential to business success. Consequently, it’s vital to protect partner company information.
- Third-parties – including Cloud-hosting providers, integration partners, and third-party administrators, understanding the responsibilities of each party’s risks and controls and collaborating to ensure information protection are exercised, must be considered for a holistic information security program.
- Other Affected Parties – not to be overshadowed by the above beneficiaries, there are other consequential parties and departments that must be included that have significant operational and financial impacts to the business; these include, Legal, Compliance, Risk Management, Regulators, Insurance Carriers, and other industry-specific parties.
#2 pitfall – missed opportunity to endorse the security program
Promoting the value of a security program to Stakeholders and Participants is often overlooked or a nominal focus. Ensuring appropriate program beneficiary inclusion is essential because an organization cannot build a culture of compliance without stakeholder buy-in and support from all employees and partners with an interest in the outcome.
Buy-in from control owners that practice consistent and ongoing buy-in, and actively contribute to the program success, makes for vigorous security initiatives.
#3 pitfall – not understanding how the company mission aligns with security
If company goals and objectives are not aligned with the scope of the security program, it will eventually lose its way or fail altogether; e.g., if a new product or service is introduced to the marketplace but did not consider associated information security risks and controls.
Executive support will waiver if the security program does not support the company’s mission, goals, and objectives. Since companies often adjust their business model, it’s important to continuously evaluate security program alignment with where the company is heading.

#4 pitfall – assigning the wrong resource as the business process owner
Assigning technical leadership that is responsible for the information security program is most often a huge mistake. Not only is there a significant conflict of interest with risk controls ownership, oversight, and evaluation, they are often not as adept at producing quality documentation for audit examination.
Information security is a business process function, not a technology function.
The most appropriate role for managing compliance would be a role that does not have any direct ownership in specific operational risks and controls. The most appropriate roles may include; Compliance Officer/Manager, Legal, InfoSec Officer, ISMS Manager, or Chief Operations Officer.
#5 pitfall – selecting an advisory committee and not an action council
Leadership through a committee without ownership and action responsibility is a recipe for inaction (ask me how I know). Ideally, forming a formally chartered information security council, where all members actually own the results and do the work is most effective. Here are a few things to keep in mind to create a functional information security council:
- You need a captain – an effective team needs a captain to cohesively lead the ‘players’ to achieve greatness. Typically the InfoSec Council ‘captain’ is also considered as the sponsor for InfoSec initiatives.
- Keep it small – including the following business functional areas is optimal; operations, engineering, human resources, legal, and compliance. Also, consider an external consultant that can provide advisory to the council and their security initiatives.
- Including an Executive – including a strategic and tactical executive (1-2 max) as part of the InfoSec Council creates a direct communication line to the rest of the executive team and stakeholders. It also adds perspective and alignment with the company mission, goals, and objectives.
#6 pitfall – hiring an advisory firm that won’t do the heavy-lifting
Selecting an Advisory firm, rather than a partner who does a lot of the heavy-lifting is classically a waste of information security budget dollars.
Advisory firms typically tell a company what needs to be done to meet the standard, reviews the work done by the company, tells them what’s wrong with the company’s work, and doesn’t actually do much or any of the actual documentation required to meet compliance requirements.
Professional Services firms, in contrast, will partner with the company, doing a significant part of the heavy-lifting, and may also manage information security initiatives from conception through audit(s), and beyond for continual improvement and compliance.

#7 pitfall – using search and replace document templates
At Vigilant Systems, we have seen organizations buying one-size-fits-all control document templates when they attempt to create their first information security compliance initiative. Buying one-size-fits-all control document templates is classically a simple and avoidable mistake: A simple search & replace approach to populating templates will not satisfy compliance requirements. It also takes more effort than merely customizing documentation to how the organization operates, rather a holistic approach to the information security program has to be woven throughout the required artifacts.
We’ve seen templates that cost ~$1,000 or more to license its use that is so poorly authored, that it takes more time and effort to correct them than it would have taken to craft it correctly in the first place.
There is a real-time and resource cost when the documentation does not meet the control standard and has to be re-done.
#8 pitfall – hosting audits without experienced support
Going it alone for audits almost always results in negative findings by the auditor. This is easily avoided by including an objective resource that is not only experienced with information security audits specific to a security framework, but is also extremely knowledgeable about the company’s information security management system.
Regardless of the type of information security audit and the framework compliance is measured against, there are ‘rules-of-engagement’ to consider and significant audit complexities that need to be navigated. Audits should not be navigated alone.
#9 pitfall – exclusion of security costs in budgets
Unrealistic ongoing cost expectations or budget exclusion of ongoing management and continual improvement costs to ensure continuous compliance, are often detrimental to the overall program success and often damages executive support.
Not including information security as an integral and funded aspect of company operations will torpedo the success of an information security program.
Additionally, by planning realistic costs into the budget for ongoing security management and improvement, an organization will be able to avoid incurring significant costs and potentially massive losses in the future due to applying ‘shortcuts’ in an underfunded program.
Related: The Business Case for Compliance, Even Now
#10 pitfall – treating security as a short-term goal, not as an ongoing program
Treating security initiatives as a sprint as opposed to a journey is not only shortchanging the security program, it actually puts the company’s information security at high risk. Implementing an information security program just to meet a customer requirement will shortchange long-term security.
With information security, there’s no destination, it’s a continuous and iterative cycle of improvement, not much different than running a software company.
Sitting on one’s hands throughout the review cycle and then scrambling in the eleventh hour when an audit date is looming does not serve the company, customers, and other entities that have a stake in the outcome of the information security program.
Understanding these pitfalls is the first step in avoiding them altogether. In future articles published on this blog site, we will examine strategic and tactical approaches to driving a successful information security program.
About Author
Peter VR Sternkopf, President and CEO of Vigilant Systems

Peter is a PMP and CEPA. His expertise includes inside-out security (IoS™) and successful completion of many information security compliance engagements within the following frameworks: ISO 27001/27002, AT101 SOC 2 Type 1 and Type 2, GLBA NIST 800-171, NIST 800-53, FedRAMP, and Privacy Shield, resulting in favorable audits and certifications. Other work he has done includes software development, internal investigations and forensic analysis, social sentiment analysis, mergers & acquisitions, information assets classification system design, eDiscovery process improvement, information systems migration, website design and build, Y2K remediation projects, and several others.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?